
Greetings from Seattle, where “second false spring: has just arrived. It’s a thing, Google it! Returning readers will no doubt recognize that I’m a bit obsessed with the weather here. Even after thirty years in the Emerald City, and my induction as an honorary mossback, the weather and its 12-14 micro-seasons are frequently top of mind. During my first year as an undergrad at the University of Washington, I thought about becoming a meteorologist. I took several atmospheric sciences classes, but then the advanced math got me. Instead I got a degree more suited to my natural talents: Communications 😉
I teased this possibility last month, but now it’s official: The publication of this monthly newsletter has moved to the first Tuesday of the next month, as opposed to the last Tuesday of the month that the newsletter covers. We changed a few things up internally, and for practical reasons, this change is becoming permanent. The use of adapted song titles for each new edition is sticking around, though it might get harder if I keep up sequential numbering. I’d normally ask you to comment on this post if you recognized the song this one is based on, but GenAI kind of takes the fun out of it - Gemini for example got it on the first try 🙄
While February was a short month, the threat landscape was anything but quiet and my team was anything but bored. This edition of my newsletter focuses on a recurring phenomenon we observe in actor tradecraft: The weaponization of trust. Our headliner is a deep dive into Lotus Blossom (G0030) and their sophisticated supply chain attack targeting Notepad++. This wasn't a loud, "smash and grab" operation; it was a surgical infiltration of an update pipeline designed to stay under the radar of even the most diligent admins.
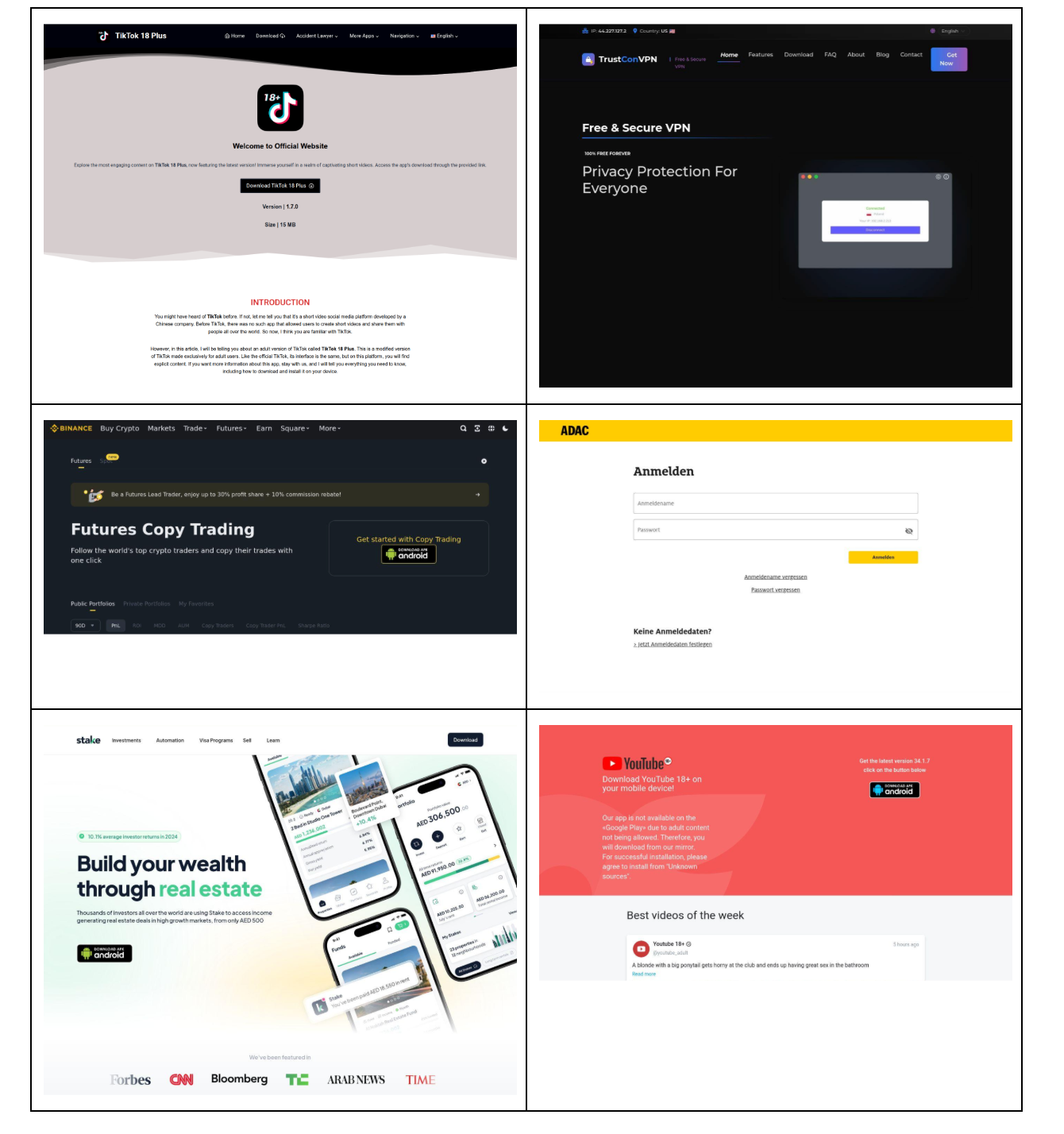
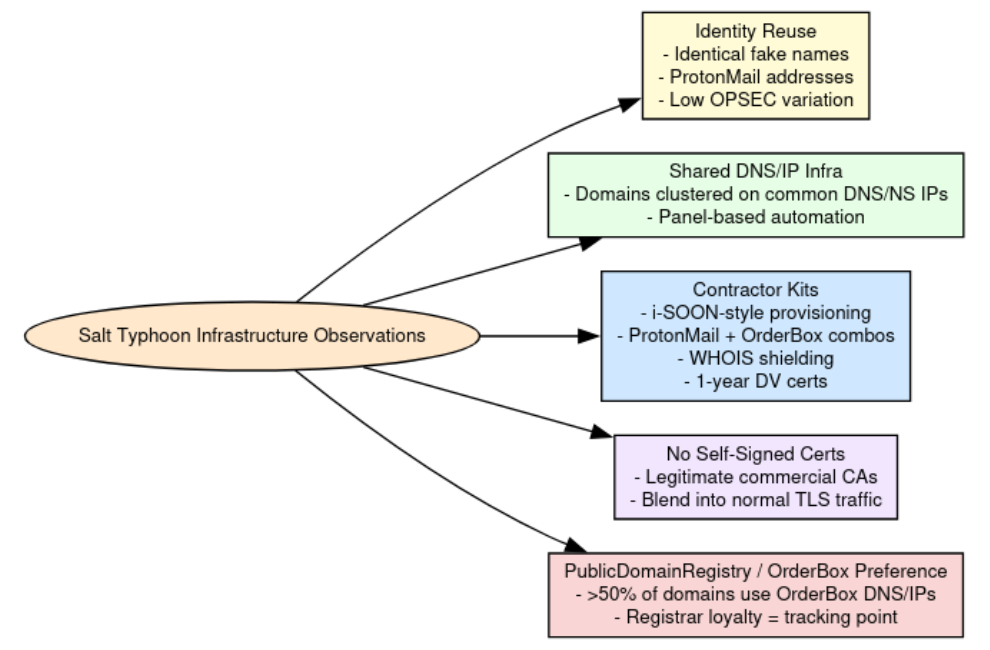
We’re also looking at the "human" side of the house with a new Security Snack on Idolized Crypto Scams. My team traced over 250 domains back to a single infrastructure cluster that uses celebrity personas and fraudulent presales to siphon assets across multiple blockchains.
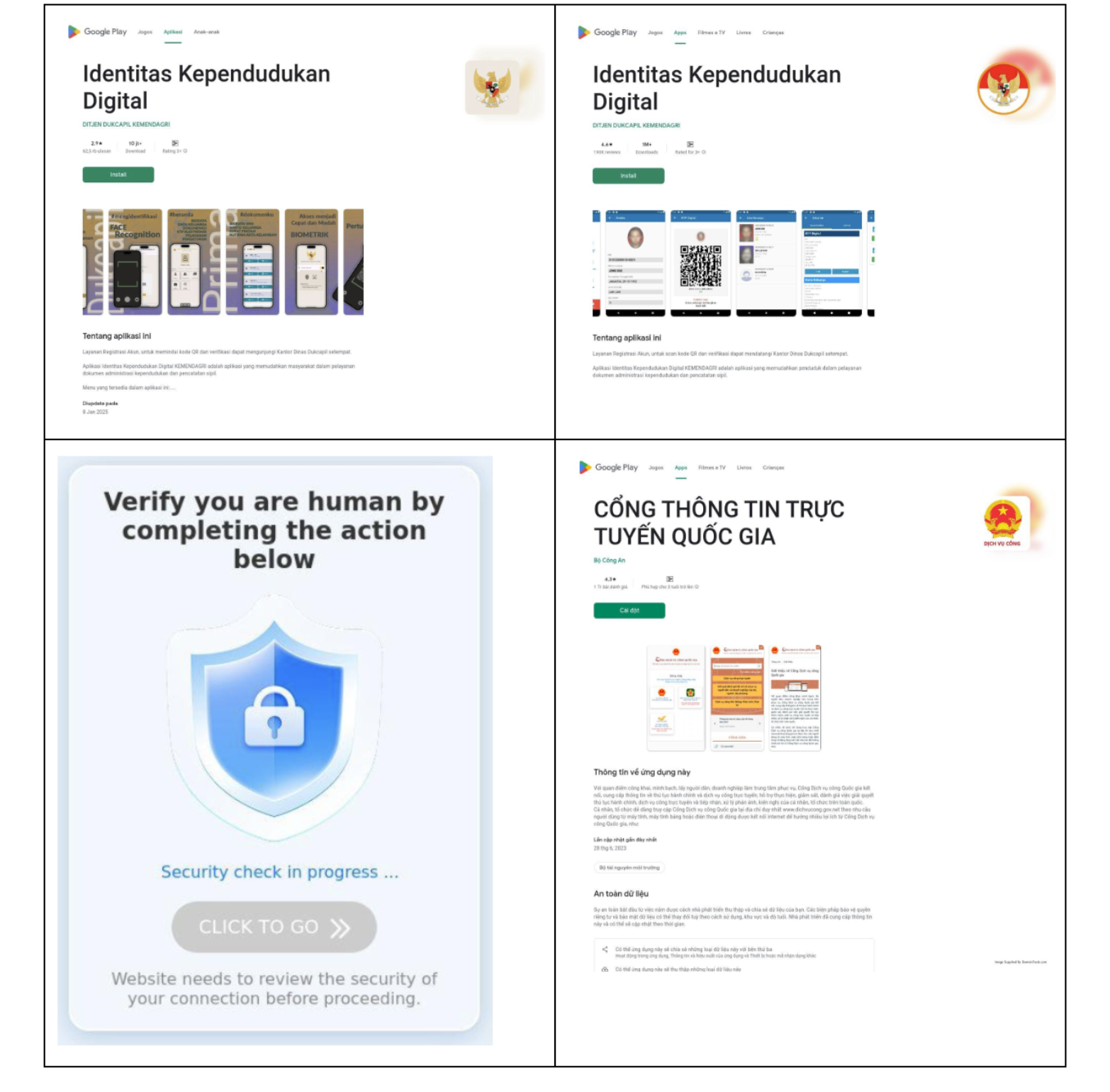
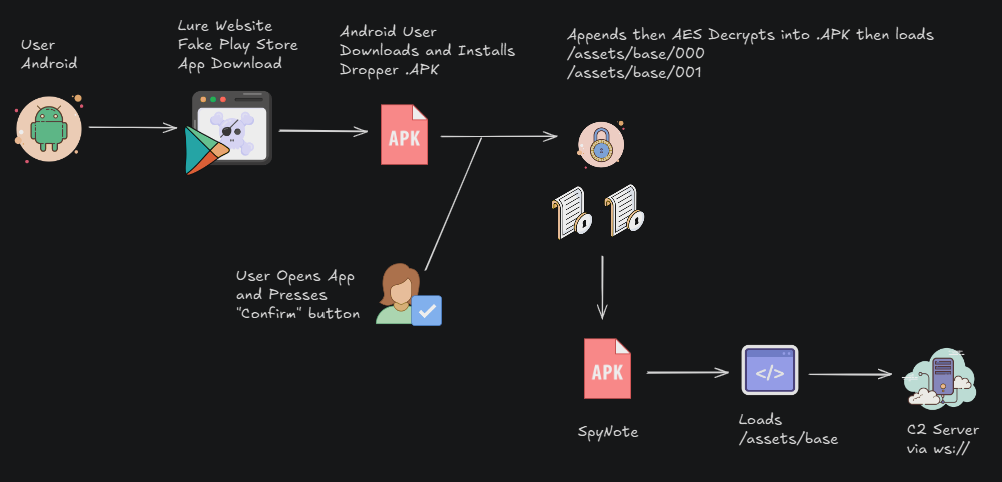
We closed out February with my talk at BSides Seattle, where I spoke about my team’s research on new domains delivering SpyNote Malware, which we covered extensively last year. If you weren’t able to catch me live, my team and I will be at BSides San Francisco near the end of March, where we have two presentations on the schedule - come find us and say hi! I will be in town for RSAC as well, and would be happy to host you in our space near Moscone.
Now, without further ado, from supply chain evolution to high-velocity fraud, we’ve got plenty to get you up to speed. Let’s dive in!
Hot off the Presses
Lotus Blossom (G0030) and the NotePad++ Supply Chain Espionage Campaign
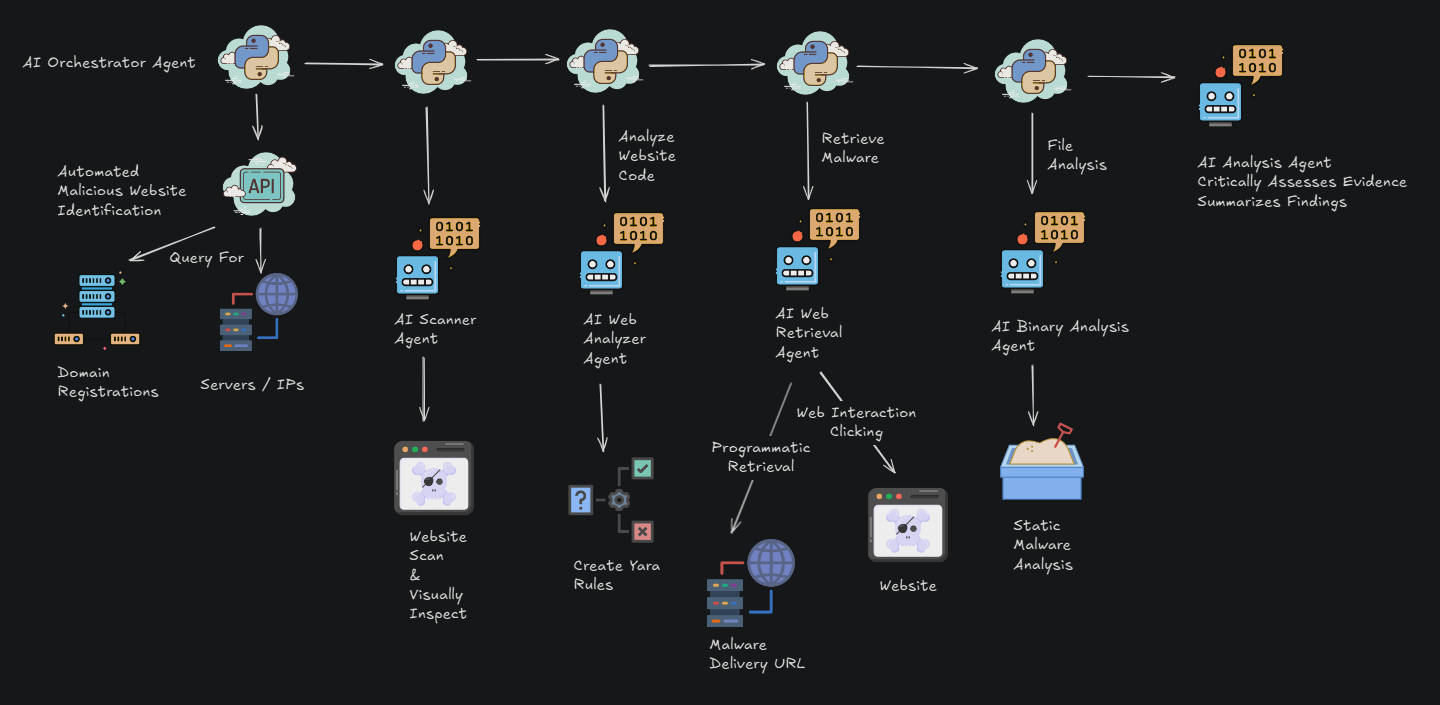
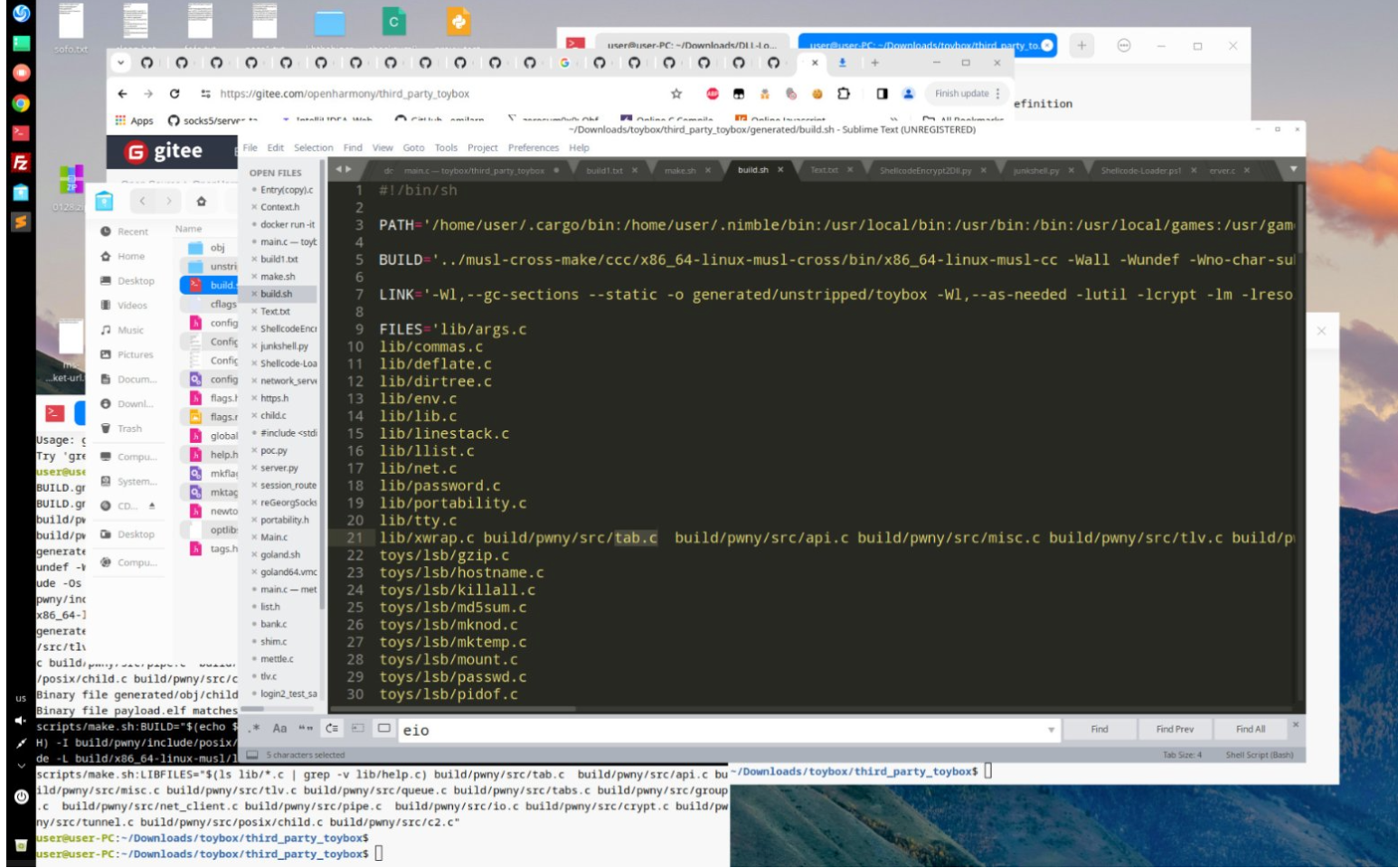
DTI researchers analyzed the sustained compromise of the Notepad++ update pipeline from late 2025 into early 2026. Rather than modifying the open-source codebase, attackers infiltrated upstream distribution infrastructure and selectively redirected update traffic for a small group of targets. This allowed them to deliver customized installers and low-noise implants to be delivered while most users continued receiving legitimate updates.Taken together, the operational choices, tooling, and victim profile support attribution, with moderate to high confidence, to the China-aligned espionage actor commonly tracked as Lotus Blossom (G0030) in concurrence with other organizations assessment.
The Notepad++ compromise represents a clear evolution in Lotus Blossom’s tradecraft. Earlier campaigns relied heavily on spear-phishing and bespoke backdoors delivered directly to victims. Rather than compromising end-user systems through conventional infrastructure attacks, such as opportunistic abuse of widely trusted software updates, the actors shifted the locus of trust toward the developer ecosystem itself. By abusing a legitimate update mechanism relied upon specifically by developers and administrators, they transformed routine maintenance into a covert entry point for high-value access.The incident highlights how trusted software update systems can be quietly weaponized for long-term intelligence collection without causing widespread disruption.
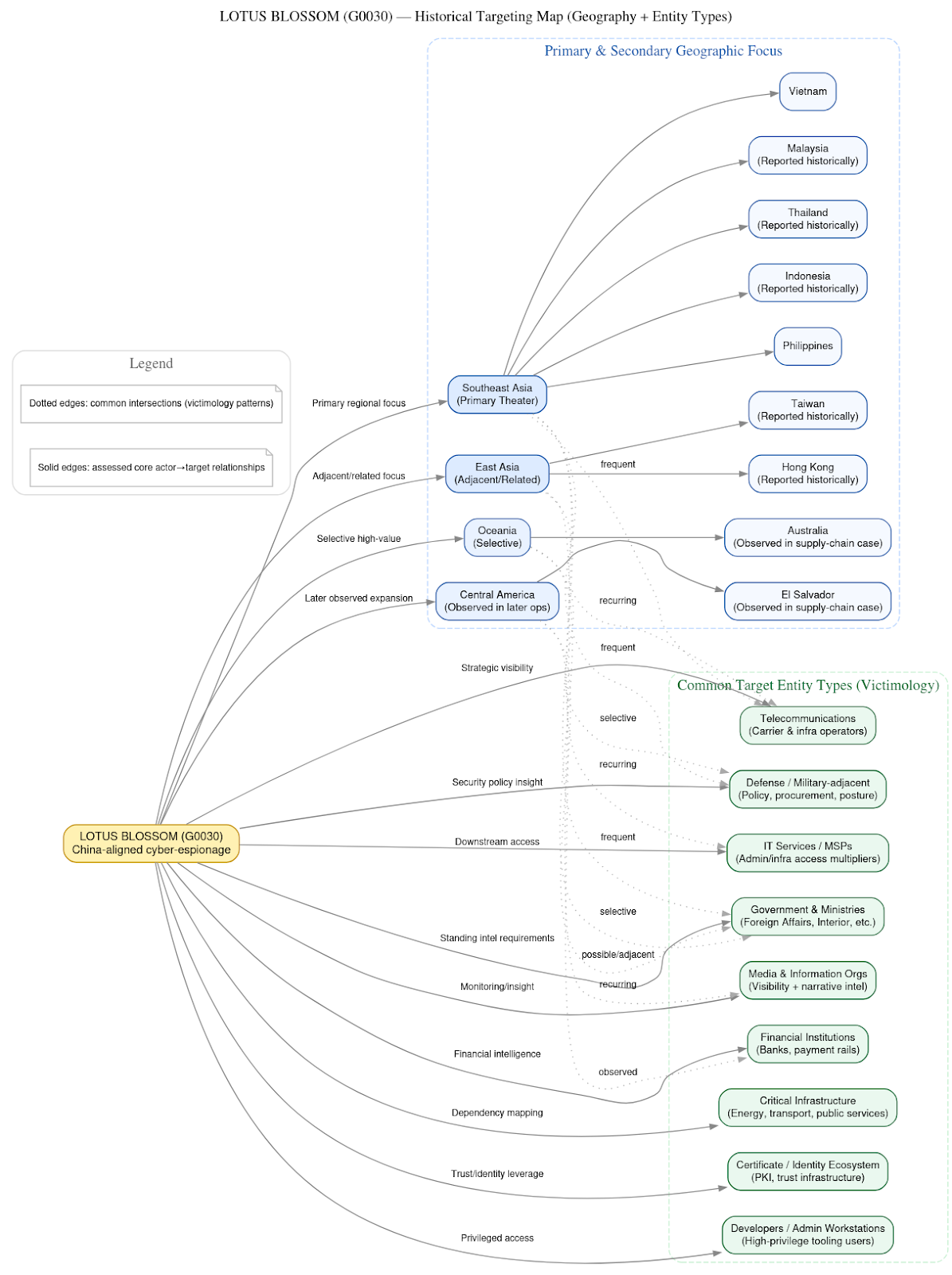
🔍Read the full investigation here
SecuritySnack: Idolized Crypto Scams
A cryptocurrency scam operation spanning roughly 250 domains was identified across multiple themes, including fake celebrity giveaways and fraudulent token presales. The investigation began with a cluster of suspected scam domains sharing the same Google analytics tag ID and expanded through blockchain tracing, wallet analysis, and domain registration overlaps. This process revealed activity across BTC, ETH, and XRP and included impersonation of public figures, platforms, and crypto projects.
On-chain findings were mixed but revealed a well-developed supporting infrastructure. In several cases, blockchain tracing showed actor-controlled wallets funding themselves and cycling assets through multi-layer laundering pipelines. The broader infrastructure includes cross-chain scam tooling, distributed hosting across multiple jurisdictions, and hundreds of related domains. Evidence from shared wallets, infrastructure overlaps, and Russian-language artifacts indicates a single actor likely responsible for both campaigns.
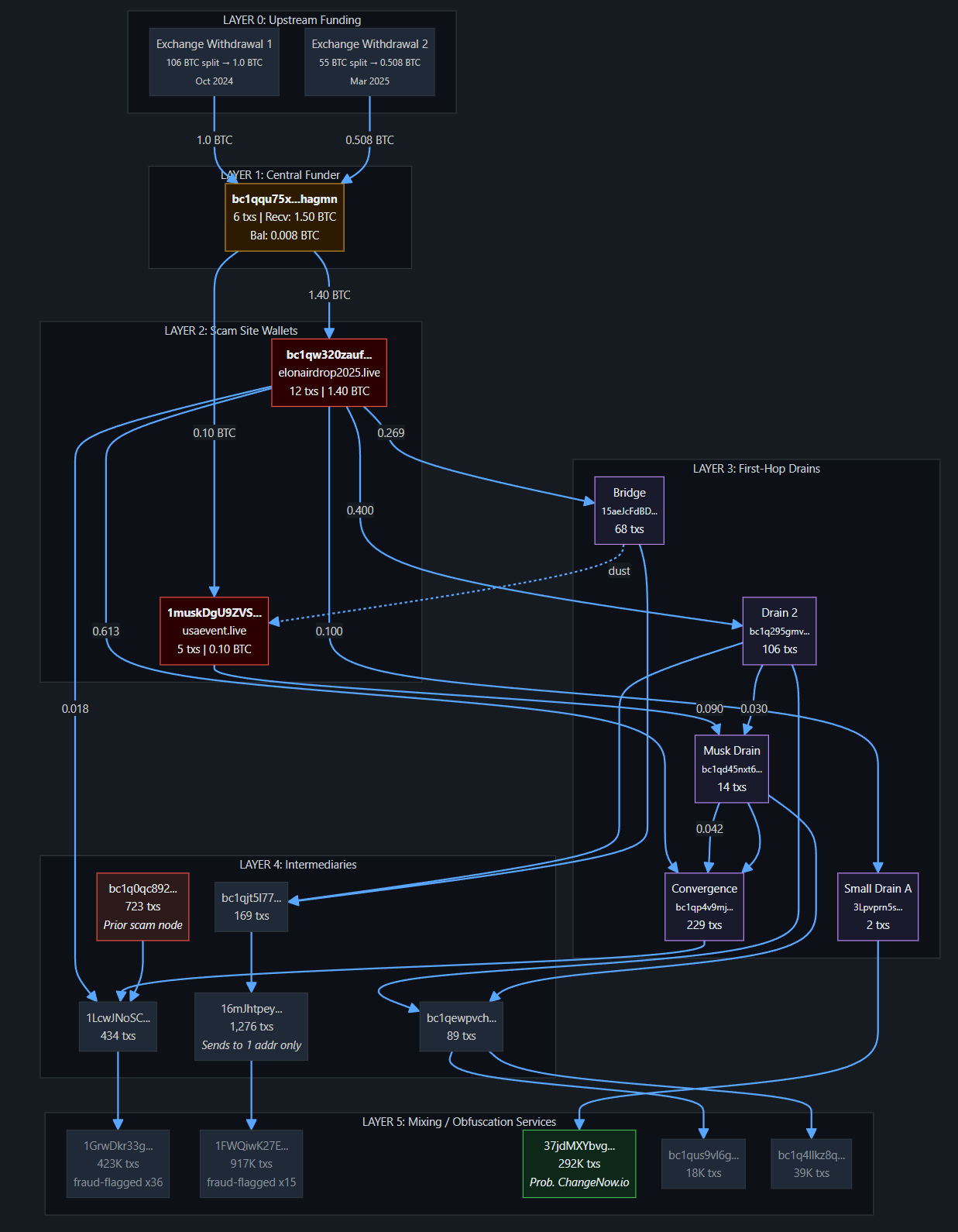
What We’re Reading
In case you’re behind on your cybersecurity reading homework, DTI team member Ian Campbell’s monthly recommended reading list will get you up to speed!
- The top article for the month: Infoblox Threat Intel - Compromised Routers, DNS, and a TDS Hidden in Aeza Networks
- The top research for the month: Crowdstrike - 2026 Global Threat Report
📚Check out the full reading list here
Where We’ll Be
- NICAR 2026, Indianapolis, IN - 04-06 March
- BSides San Francisco, San Francisco, CA - 21-22 March
Come see me speak on Saturday 21 March at 1:05pm, AMC Theater 13
- FIRST CTI Conference, Munich, Germany - 21-23 April
Final Thoughts
As always, thank you to my returning readers! If you’re new, I hope you found this newsletter informational, helpful, and worthy of sharing with your peers. And of course I hope you will be coming back to read future editions!
We share this newsletter via email as well - if you’d prefer to get it to your inbox, sign up here.
If you missed last month's content, here are some quick links:
- Security Snack: Phishing Interviews
- Pay to Lose: Dubious Online Gambling Games
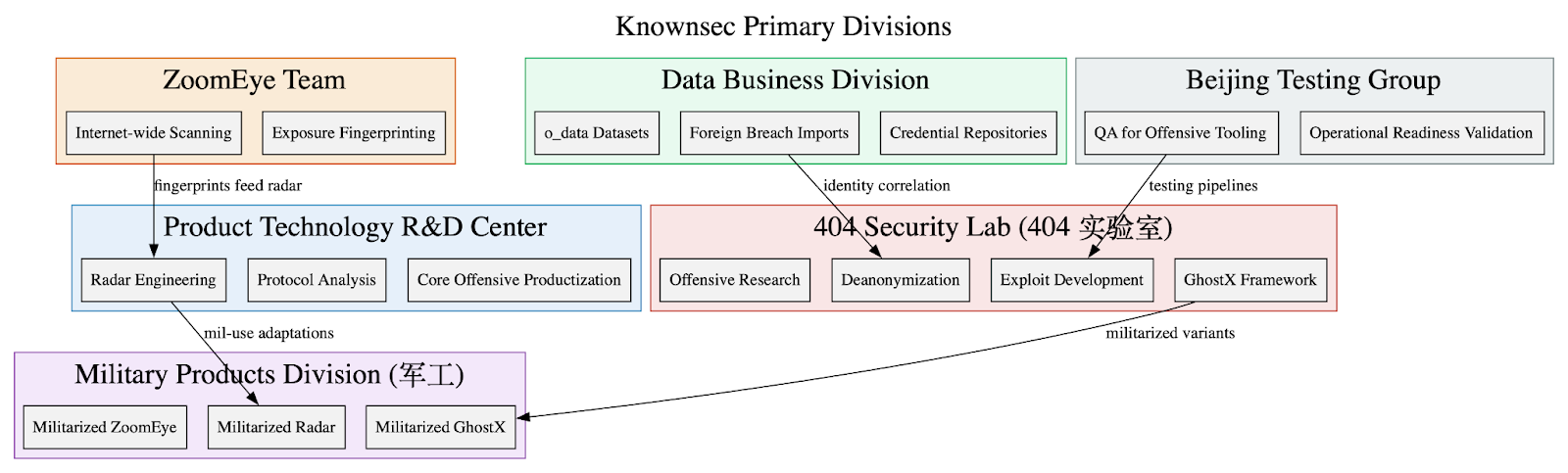
- THE KNOWNSEC LEAK: Yet Another Leak of China’s Contractor-Driven Cyberespionage Ecosystem
Thanks for reading & see you next month!
-Daniel
https://www.linkedin.com/in/schwalbe/
https://infosec.exchange/@danonsecurity



























![A screenshot of a fake cybersecurity website, cybersecureprotect[.]com, masquerading as a legitimate antivirus service](https://cdn.prod.website-files.com/6941445776ba1afe6af83186/6941445876ba1afe6af8477a_693c851d2848ceb668595d8a_april-newsletter-image-5.png)






