I can’t believe it, but we have made it to the 5th iteration of my DomainTools Investigations (DTI) newsletter! If you’re a returning reader, I’m glad you keep coming back! If you’re a new reader, what you’re about to read is top secret. Anything you say can and will be used against you without express written consent of Major League Baseball. That’s the saying, right?
But seriously, if you’re a new reader, welcome! What you’re really about to read is not top secret; it’s news from our group of researchers and analysts providing their expertise in investigating, mitigating, and preventing Domain and DNS based attacks.
Community is incredibly important to me, and I believe that the only way we’ll make progress in fighting threat actors is coming together to share what we know. So take a look around, and if you have information to collaborate with us to get further in our analyses, please let us know.
So without further ado, here’s what we’ve been up to in May:
🔥HOT OFF THE PRESSES
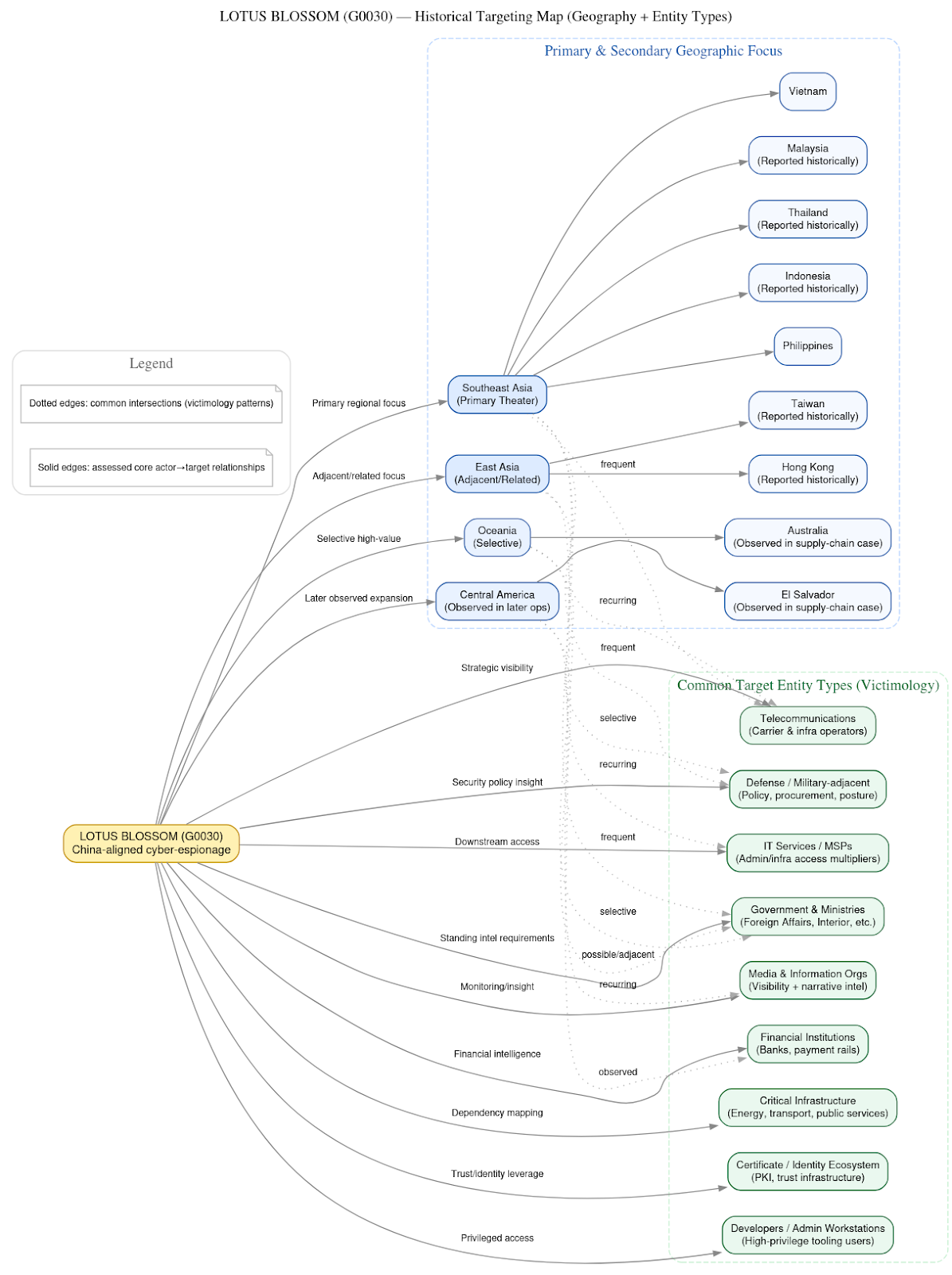
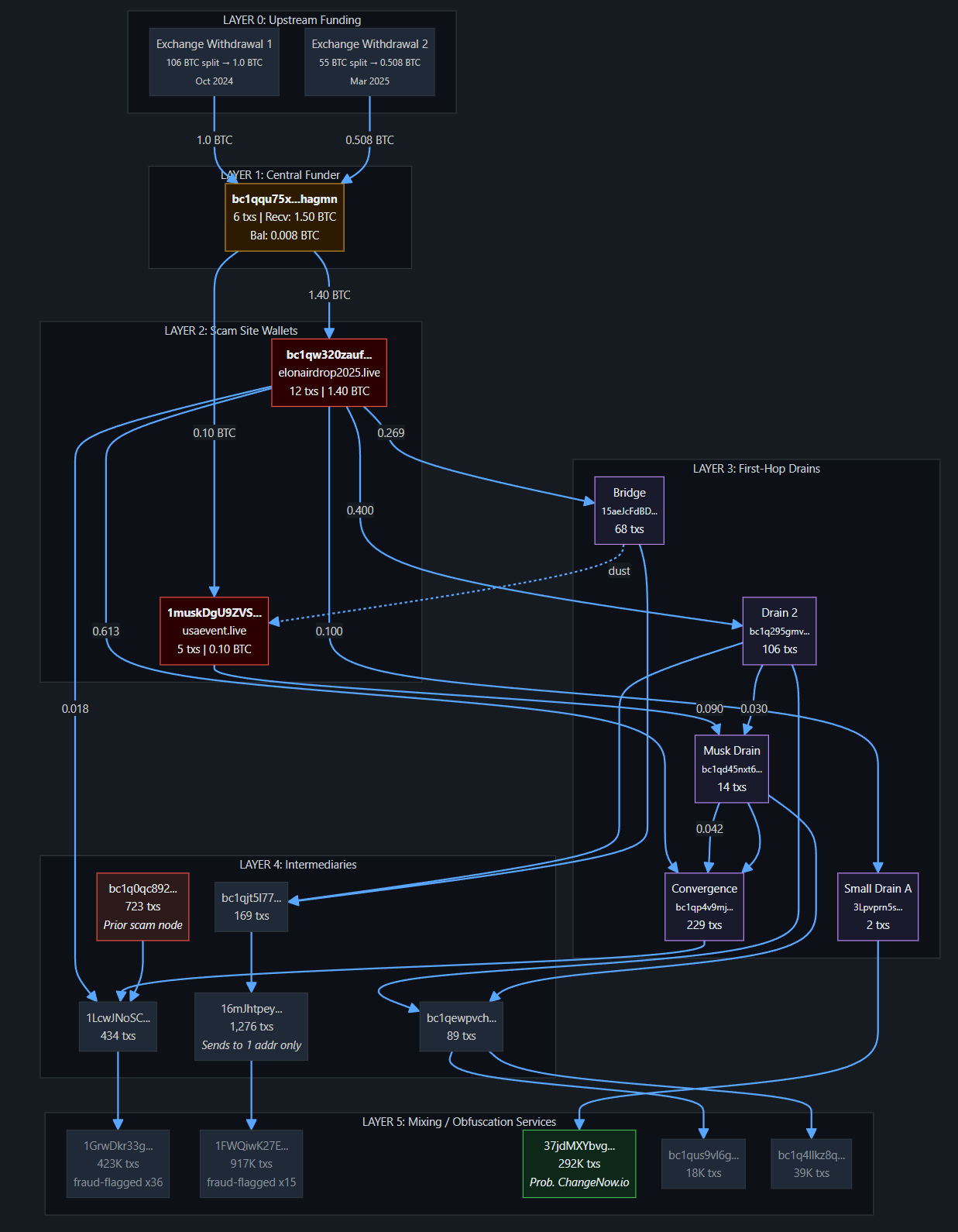
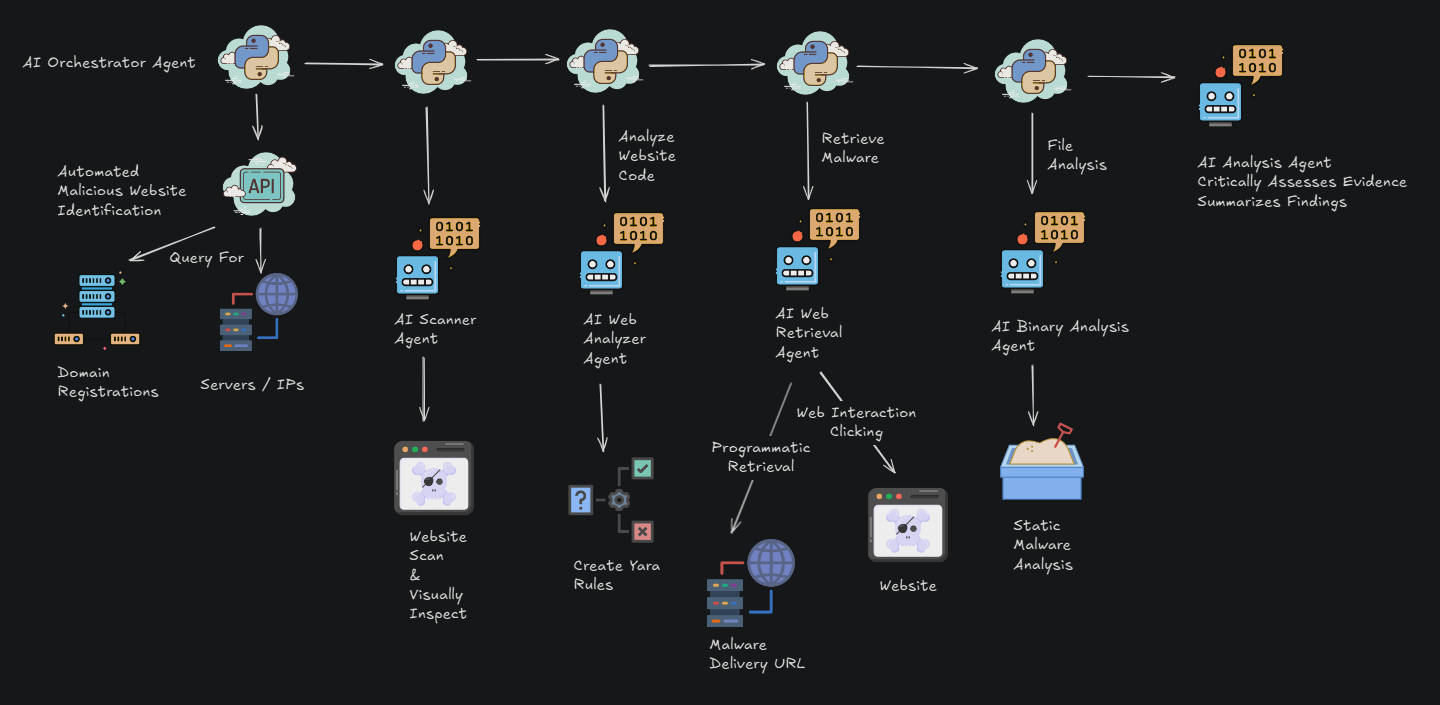
Published this week (May 28), DTI shared its latest analysis on a malicious campaign using a fake website to spread VenomRAT, a Remote Access Trojan. The research examines attackers’ methods, such as deceptive websites and command infrastructure, indicating a clear intent to target individuals for financial gain by compromising their credentials, crypto wallets, and potentially selling access to their systems.

Why is This Important? This campaign highlights a growing trend: attackers crafting modular, open-source-based malware that’s stealthy, flexible, and easy to deploy. This DIY malware model helps them move fast and stay hidden.
While open-source tools can aid defenders in detection, the real victims are everyday users—targeted with fake login pages and malware disguised as trusted software, all aimed at draining bank accounts and crypto wallets.
Objects May Be More Malicious Than They Appear
DTI observed an unknown actor continuously creating malicious Chrome Browser extensions since February, 2024. The websites masqueraded as legitimate services, productivity tools, ad and media creation or analysis assistants, and more to direct users to install corresponding malicious extensions on Google’s Chrome Web Store. The extensions had a dual functionality, where they appeared to function as intended, but also connected to malicious servers to send user data, receive commands, and execute arbitrary code.

Why is This Important? The actor’s persistence and the time lag in detection and removal pose a threat to users seeking productivity tools and browser enhancements. All users should protect themselves by exercising caution when installing extensions. Stick to the Chrome Web Store and verified developers, carefully review requested permissions, read reviews, and be wary of lookalike extensions.
Threat Actors Love a Good Viral Event
Viral media events capture global attention. Everything from natural disasters to geopolitical shifts to cultural phenomena can dominate headlines and online conversations – and bad actors pay attention and look to capitalize on the public’s interest.
We undertook a project to analyze scam and malicious domains that emerge in the wake of high-profile viral media events. Leveraging AI-driven research capabilities, we aimed to understand how threat actors exploit these moments for financial gain and other nefarious purposes.

Why is This Important? The speed at which these events unfold provides a fertile ground for scammers to deploy a variety of schemes primarily focused on financial exploitation through fake donations, merchandise sales, and cryptocurrency scams. Staying vigilant and critically evaluating any website or domain seeking engagement related to a viral event is crucial
Cybersecurity Scholastic Book Fair
Wouldn’t that be awesome if one of the conferences decided to do a 90s-style Scholastic book fair for cybersecurity and infosec books? One can dream, but until then, here are some of the topics from Ian Campbell’s May Recommended Reading digest:
- Salt Typhoon hacks to influence final round of DARPA’s AI-cyber competition – NextGov
- Uyghur Language Software Hijacked to Deliver Malware – Citizen Lab
- The Human Element Podcast – hosted by my friend and CTO of Maltego, Ben April
Be sure to check out the reading list for Ian’s full recommendations!
Final Thoughts
Again, if you’re a returning reader from last month, I thank you. If you’re new, I hope you found this newsletter informational, helpful, and worthy of sharing with your peers.
We share this newsletter via email as well – if you’d prefer to get it to your inbox, sign up here.
If you missed last month’s content, here are some quick links:
- Deceptive Browser Extensions within the Google Store: A Study in AI Slop
- Newly Registered Domains Distributing SpyNote Malware
- Where to Find Aspiring Hackers – or listen to this episode of the Breaking Badness Cybersecurity Podcast to learn more about Proton66 and the threat actor known as Coquettte (yes, with three T’s).
Thanks for reading – see you next month!
Daniel