SecuritySnacks

Commentary followed by links to cybersecurity articles and resources that caught our interest internally.
This OWASP guide popped up on my radar this week and, yes, it’s about AI. And yes, it’s entirely predictable. But what appeals to me at the moment is its predictability amidst the nondeterminism of LLM rakestepping. Catastrophic outcomes in these complex systems are foreseeable not just from today, or the day this Adversa post was published, but at least from 1984. It was in 1984 that sociologist Charles Perrow published “Normal Accidents: Living With High-Risk Technologies.” Normal Accidents had nothing to do with artificial intelligence, yet seeing how it’s being deployed today, the book now has everything to do with it. Perrow studied major industrial accidents across much of the twentieth century and isolated some important insights on unexpected catastrophic failures inevitable enough to be called Normal Accidents:
- The system is complex.
- The system is tightly coupled.
- The system has catastrophic potential.
In the agentic systems we see proposed and being implemented before us, certainly complexity plays an integral role - the dirty little secret of LLMs is that to make one useful, especially for a specialized expert task, you’re dealing with multiple layers of LLMs with varying levels of autonomy. It’s the sausage being made behind that single pane of glass most AI products pretend to be.
We then turn to tight coupling - essentially, complex systems producing outputs that must occur in a specific order, such as a multi-stage chemical treatment process. It is the anticipated sequence - in Perrow’s words, the invariant sequence - where B must follow A, because that is the only way to make the product - that defines tight coupling. Think about the sub-tasks each Agent is charged with; pre-prompt hardening against injection attacks, shifting tone and scope of the LLM response, providing expectations to shape system output. Above that and the primary agent doing the task, you have multiple other systems working to evaluate, validate, and re-shape output before it’s pushed to the surface agent, who relays it to you. Should those multiple subsystems interact in varied ways or orders, the output is necessarily - perhaps catastrophically - affected.
Catastrophic potential is mostly self-evident, but let us take a specific example: the modern Security Operations Center, or SOC. Perrow’s book provides multiple corollary environments - think a Nuclear Power operations center full of sensors, monitors, and potential alerts. Or the cockpit of a commercial airplane, which had seen much more automation in the decades prior to 1984 and provided starkly relevant examples of alert and attention issues at critical moments. Indeed, we see SOC failures in some of the biggest hacks on record, where alerts are missed or disregarded, leading to major systemic damage.
So in the SOC we have a complex, tightly-coupled system with catastrophic potential. “The essence of the Normal Accident,” Perrow wrote, is “the interaction of multiple failures that are not in a direct operational sequence.” That is, system components interacting in sequences and ways not only unexpected, but “incomprehensible” during the incident, often leading to much worse outcomes.
And what do we do, 42 years after Normal Accidents’ release? We add a complex, relatively tightly-coupled system of agents to a complex, certainly tightly-coupled system with catastrophic potential called the Security Operations Center. And not only that, but a system of agents fundamentally empowered by their own nondeterministic nature.
“What distinguishes these [system component] interactions,” Perrow wrote, “is that they were not designed into the system by anybody; no one intended them to be linked. They baffle us because we acted in terms of our own designs of a world that we expected to exist - but the world was different.”
In the rush to the AI/Agentic SOC, expect many Normal Accidents.
Podcasts
- ChinaTalk - Richard Danzig on AI and Cyber - Danzig’s published “Artificial Intelligence, Cybersecurity, and National Security: The Fierce Urgency of Now” over at RAND, and sat down for a good interview with the ChinaTalk folks. I may not agree with all points raised, but the conversation is a very well-informed and thoughtful one.
Articles
- CERT Polska - Energy Sector Incident Report - If you’re reading this list, you’ve probably already seen this, but linking in case that’s untrue. Probably the best of the recent resources around the Polish energy grid incident, and worth becoming familiar with. Also good writeups by Kim Zetter here, here, and here.
- UK Defence Journal - Iranian-linked Scottish accounts fall silent again - Social media accounts that posed as supporters of Scottish Independence once again fell silent amidst the Iranian internet blackout. Fun little detection, if not necessarily a fine one.
- TechCrunch - Fintech firm Marquis blames hack at firewall provider SonicWall for its data breach - I expect this to go nowhere, but it’s certainly an interesting push that the likes of Ivanti, Fortinet, and Palo Alto will also be eyeing nervously.
- Greynoise - -f Around and Find Out: 18 Hours of Unsolicited Telnet Houseguests - Telnet? What year is it?!?! All kidding aside, Greynoise is making some fascinating moves lately, and as much of an AI skeptic as I am, hrbmstr’s experiments with AI analysis show some real value there.
- APNIC - What we learned from 63,000 attacks in 12 days on APNIC Honeynet sensors at University of Dhaka - “In just twelve days, our sensor was hit 63,247 times by 4,262 unique source IPs, including five unique IP addresses from Bangladesh. Fourteen of those led to malware download attempts. The time to first attack was less than one hour, and we averaged ~5,270 attacks every single day!” - Not groundbreaking, but another eye-opening bit of research showing with data just how dangerous the internet can be, packet-wise. Good work and writeup on their part.
- Resecurity - Cyber Counterintelligence: When “Shiny Objects” Trick “Shiny Hunters” - Resecurity published some great coups between December and January, and have gone on my must-read feeds list as a result.
Research Papers and Reports
- GTIG - No Place Like Home Network: Disrupting the World's Largest Residential Proxy Network - Good work by Google taking down the IPIDEA proxy networks, but a lot remains to be done.

Phishing campaign targets job seekers with fake career portals and interview invites, stealing ID.me credentials and deploying malware since August 2025.
A malicious actor has created several domain masquerades of small companies posing as job boards, interview themes, and login pages since approximately August 2025. The activity appears to have two distinct objectives. The first is a credential harvesting scheme targeting ID.me accounts — the official identity provider for US government services like the IRS and SSA — which may then be exploited to facilitate financial fraud, including tax refund theft and fraudulent unemployment benefits. The second cluster focuses on malware delivery, tricking job seekers via fake Microsoft Teams meeting invites to download a malicious, unsigned variant of the remote access tool Connectwise. This gives the attacker access to the victim’s machine where they may conduct follow-on attacks.
Registration Commonalities
- Nameserver: namecheaphosting.com
- IP ISP: Namecheap Inc.
- Mail Server Domain
- privateemail.com
- jellyfish.systems
- SSL Issuer: Sectigo
- Registrar: NameCheap Inc.
- Server Type: Microsoft
ID.me Credential Harvesting
clock-towerrealty[.]org
apply-untide[.]rentals
The site purports to be a United Rentals Careers portal and uses legitimate links and site content loaded from the real site, jobs.unitedrentals[.]com.
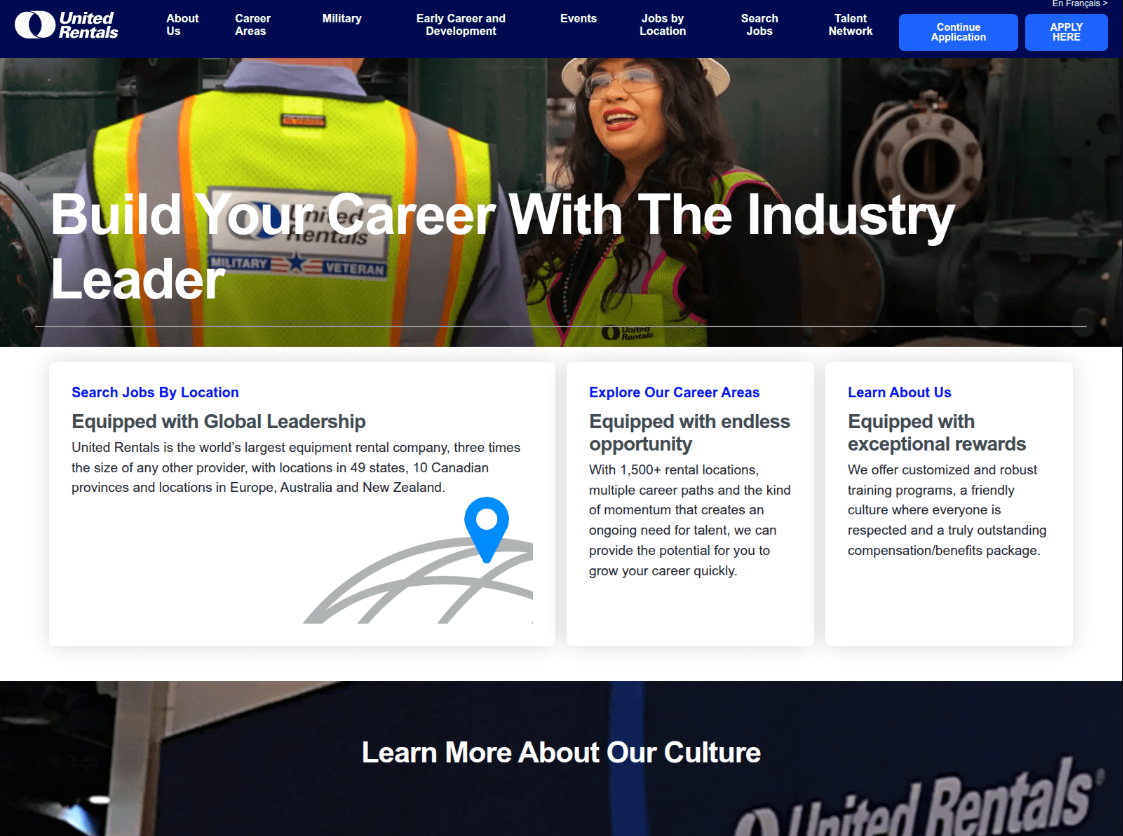
The two buttons on the top right for “Continue Application” and “APPLY HERE” direct to another actor owned domain, clock-towerrealty[.]org.
http[:]//clock-towerrealty[.]org/APPLY/?ff_landing=13 Continue Application
https[:]//clock-towerrealty[.]org/APPLY/?ff_landing=10 APPLY HERE
The code for clock-towerrealty[.]org contains a credential harvester designed to look like a legitimate corporate portal. This appears to be a brand spoof but not a website spoof of the real entity, Clock Tower Realty in Florida, USA.
The malicious domain is using a cheaply registered WordPress site to trick job seekers into providing their email and password. Credentials being targeted are ID.me. If a scammer gets ID.me credentials, they could potentially perform unauthorized logins to steal tax refunds, apply for fraudulent unemployment benefits, or take over Social Security accounts.
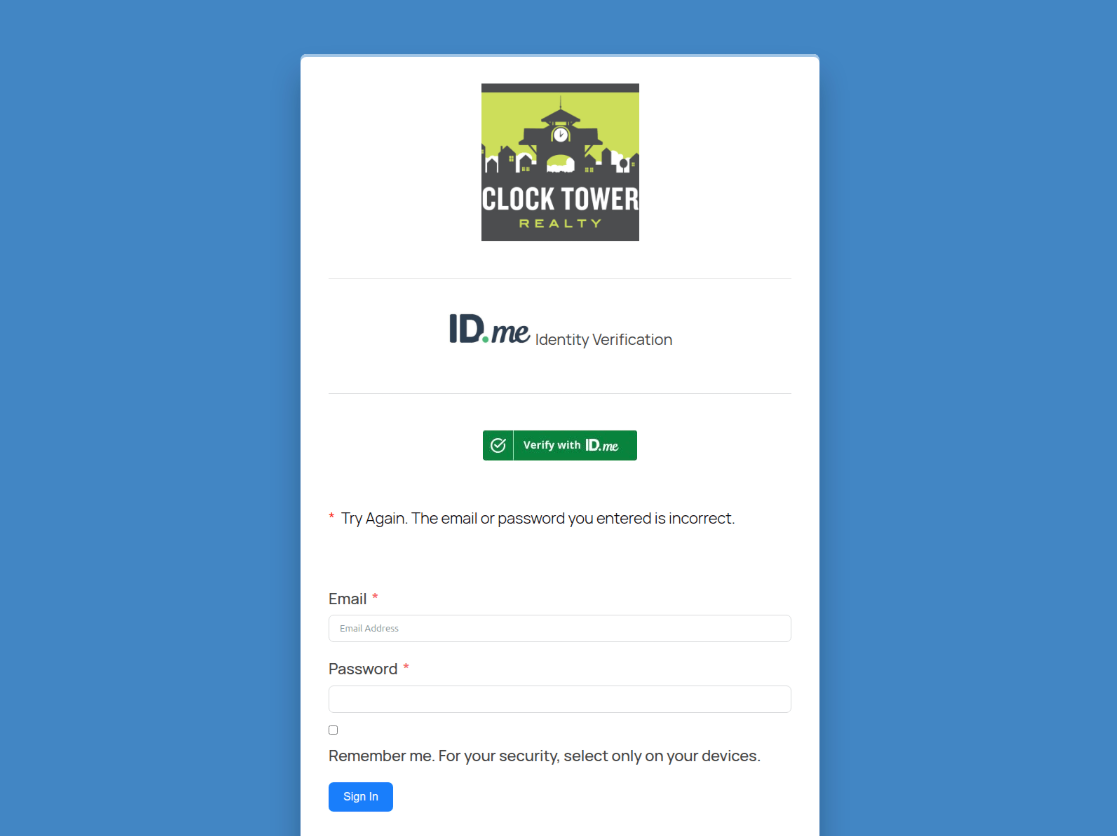
When a user clicks the "Sign In" button after entering their information, the data is sent to admin-ajax.php, suggesting the stolen credentials are being stored in the WordPress SQL database.
https[:]//clock-towerrealty[.]org/APPLY/wp-admin/admin-ajax.php
The site also has a preloaded error message loaded initially - a basic deception to trick users into entering credentials.
```
<p class="alert alert-error" role="alert">
<span style="color: #ff0000">* <span style="color: #000000">Try Again. </span></span>
<span style="color: #ff0000"><span style="color: #000000">The email or password you entered is incorrect.</span></span>
</p>
```This site, strangely, uses images with the following filenames:
- WhatsApp-Image-2026-01-16-at-12.23.50-PM-300x117.jpeg
- WhatsApp-Image-2026-01-16-at-12.25.04-PM.jpeg
These scammers may have taken screenshots of legitimate company logos and sent them via WhatsApp during the development of the scam, hence the file names “WhatsApp-Image”. Seeing "WhatsApp-Image" in a site's source code is a strong indicator that the site is fraudulent. Legitimate companies like United Rentals have dedicated IT departments.
The site is instrumented for marketing and behavior tracking using the Google Tag Manager (GTM) ID “GTM-T75PDC7R”,which appears on multiple other actor-controlled sites created between 2025-08 and 2026-01 that feature the same type of scam.
Website Title: Careers | United Rentals
GTM-T75PDC7R
clock-towerrealty[.]org
apply-untide[.]rentals
from-unietd[.]rentals
frosm-unitde[.]rentals
from-united[.]rentals
forms-unitde[.]rentals
froms-united[.]rentals
Malware Delivery
Other domains suspected of being in an associated cluster of activity were also identified masquerading as legitimate small company brands with job interview meeting invites. However, these domains do not simply attempt to steal credentials through fake logon pages. Instead, they deliver a malicious Windows installation file that provides remote access to the compromised machine.
Initial phishing domain: mlcrsoftedge[.]com. The site itself purports to be and links to https[:]//lsxconstructions[.]com/, a seemingly legitimate construction company website, which was created 2025-02-01 and redirects to lsxconstruction[.]com.
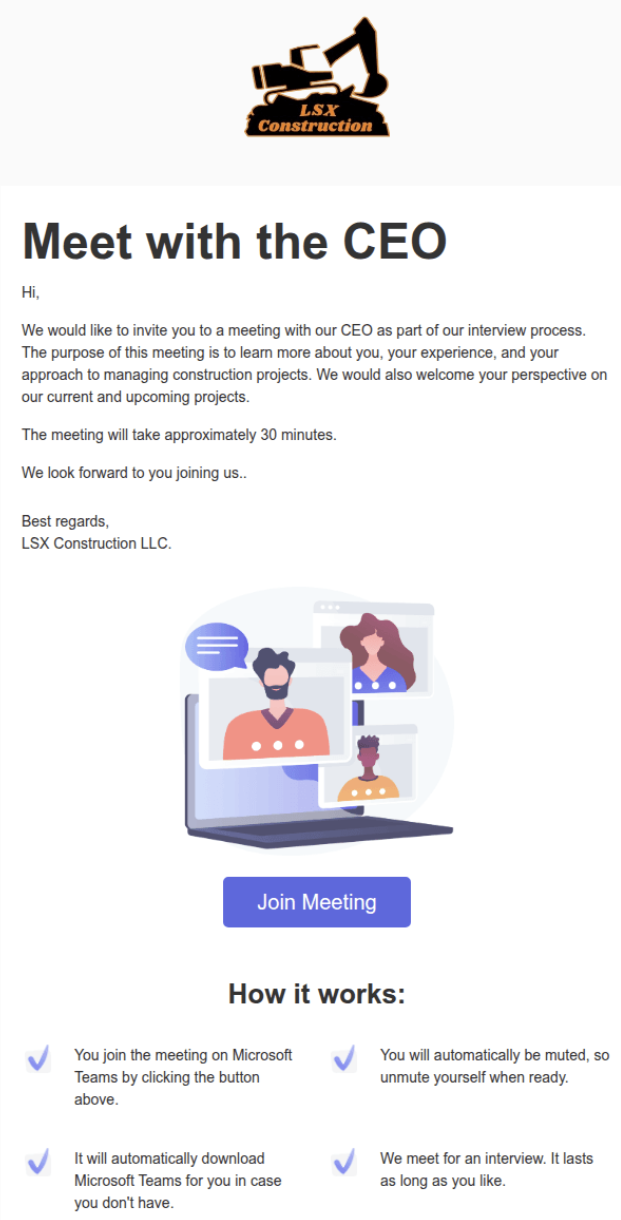
When users receive the meeting invite and click the "Join Meeting" button, they unknowingly initiate a download of a modified, unsigned installation file for Connectwise, a remote access tool.
https[:]//mlcrsoftedge[.]com/downloads/LSXCMeets.msi
LSXCMeets.msi
4107f8e0d6597866d4beb7c30718935353782dc7e199d3956fd10c8456383feb
Bundled files such as 7027b69ab6ebc9f3f7d2f6c800793fde2a057b76010d8cfd831cf440371b2b23 are linked to multiple reports of impersonation attacks and Connectwise phishing campaigns going back to 2025-04-23. The majority of the recent activity appears to have started around 2025-11.
Conclusion
The identified phishing activities use domain masquerades with a job theme and consist of two distinct attack types. One focuses on harvesting ID.me credentials, which are used to access government services (IRS, SSA, VA) and facilitate financial fraud. The second delivers a malicious, unsigned remote access tool (Connectwise) disguised as a Microsoft Teams link, resulting in system compromise. While there’s no definitive evidence the two clusters are linked to the same actor, the registration patterns, themes – specifically, masquerading as small companies – and timeframe appear highly correlative.
IOCs
mlcrsoftedge[.]com
clock-towerrealty[.]org
apply-untide[.]rentals
from-unietd[.]rentals
frosm-unitde[.]rentals
from-united[.]rentals
forms-unitde[.]rentals
froms-united[.]rentals
Sha256: 4107f8e0d6597866d4beb7c30718935353782dc7e199d3956fd10c8456383feb
Google Tag Manager: GTM-T75PDC7R
Be wary of "real money" games this New Year. This report uncovers hundreds of fake Android gambling apps using spoofed reviews, fake win declarations, and "waistcoat" shells to trick users into sideloading unregulated, predatory gambling software.
Before trying out your new year luck, be wary of online gambling apps and real money games. This report details an investigation into multiple clusters of dubious Android applications created in the past few weeks that are engaged in predatory gambling and real money gaming apps. Notably, these are not registered apps. They are intentionally misleading users into thinking they are legitimate and reputable through multiple tactics like spoofing the Google Play Store, creating fake reviews, generating fake public win declarations, and creating entire brands with marketing campaigns and broad distribution tactics. These clusters also attempt to evade detection and analysis by having post install code and configuration retrievals from actor controlled sites, which serve a dual purpose of distributing region specific content to users post installation.
The report is segmented into three distinct infrastructure clusters. Each cluster appears to target a general set of countries including Nigeria, India, Pakistan, and the Philippines. They also appear to have non-region specific user base targeting, including English, Portuguese, and Bengali speaking users. Despite the wide range of targets, the clusters share a common theme of mobile-focused gaming or gamified gambling apps to attract users for financial gain.
Details
The three clusters spoof the Google Play Store with fake app reviews and downloadable Android applications. Clusters 1 and 2 involve Android application delivery campaigns that utilize the Cocos2d game engine to obfuscate code setup,load external code and configuration details, and send device and user telemetry to actor controlled domains. These applications are distributed via hundreds of websites spoofing as Google Play Store installation pages with fake reviews. Search Engine Optimization (SEO) manipulation techniques are used to drive traffic to these sites.
Cluster 1: AA Game: Aviator
Approximately 180 domains since March, 2025,170 of which were first seen on 2025-12-14. They host nearly identical websites and serve primarily the same APK file with a few exceptions in older versions. The apps appear to feature crash-gambling mechanics, a style of game where users attempt to collect as much money as possible before the game crashes.
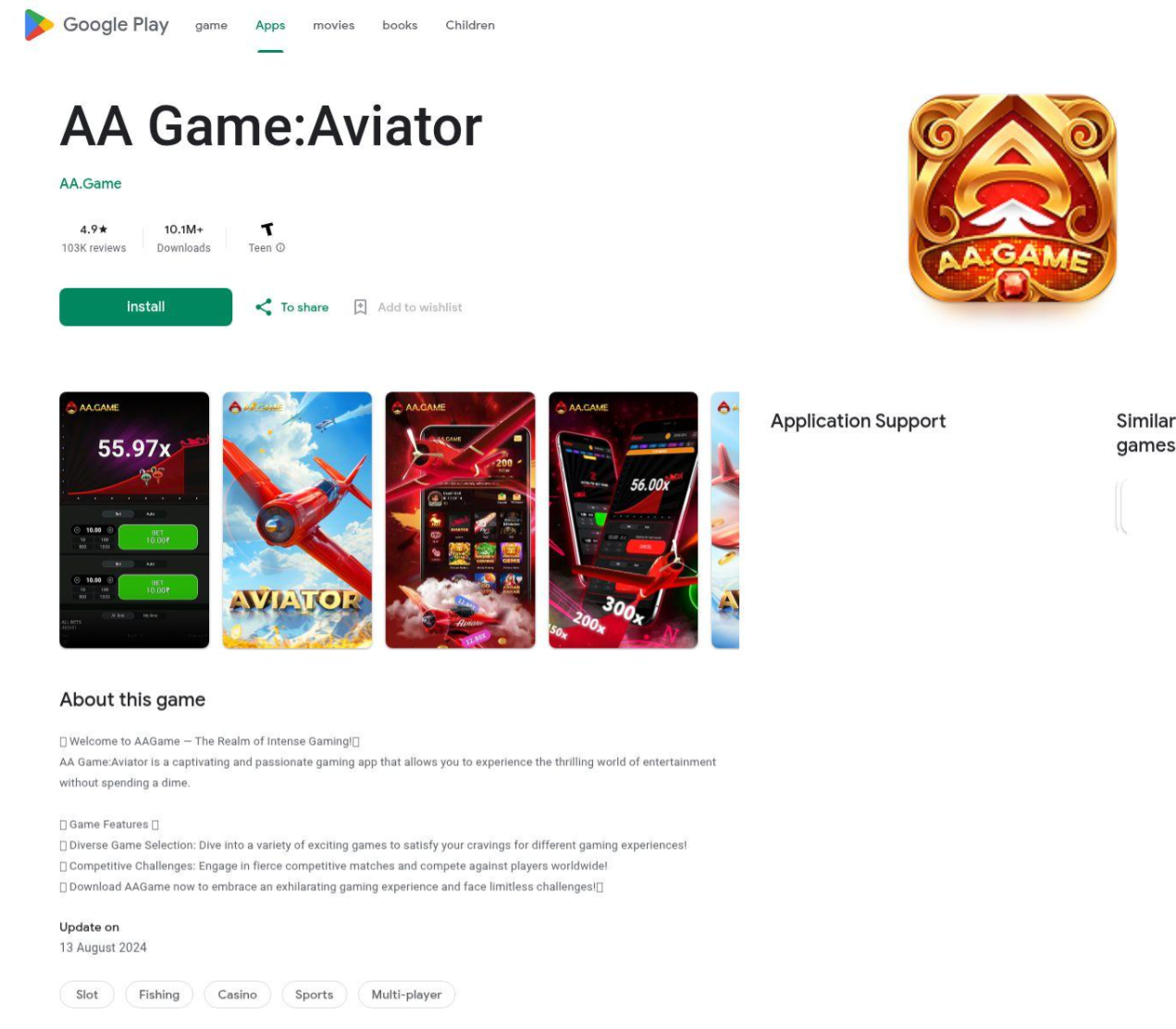
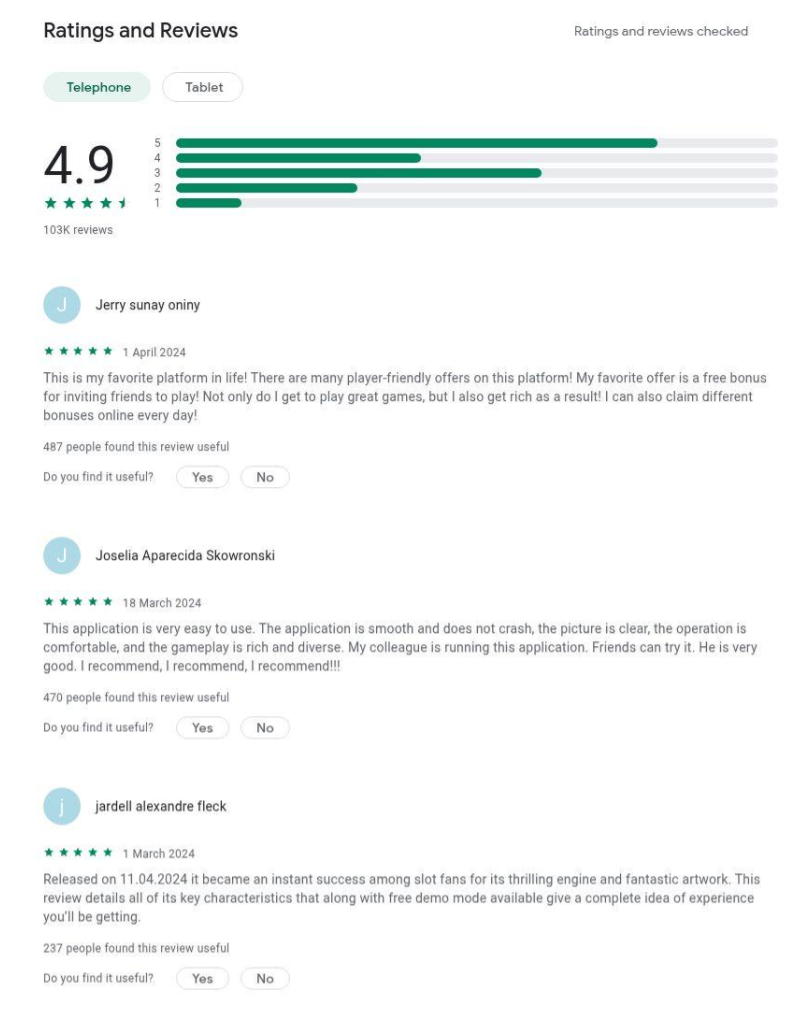
The reviews are clearly fake. They are hardcoded into the HTML, there are multiple identical reviews under different names, and they all share the exact same review id such as “data-review-id="13dc2fa2-4acc-4923-8a55-be2f20d1841a". In a real database, every review has a unique ID. Here, the scammers just copied and pasted the same HTML template.
“Aviator” games are also commonly used themes for unregulated, illegal gambling crash style games. The example app above uses terms like “Get Rich”, and has fake reviews like “I also get rich as a result!” and “Because I made more money than you can imagine!". Legitimate apps on the Play Store are strictly regulated; Google does not allow apps to promise that you will "get rich." These are social engineering tactics used to play on people's desire for easy money.
Brief details of connective tissue
Baidu Tracking ID: 49521a05cd400ce694691ca2cfd38453
IP ISP: Defender Cloud International LLC
Registrar:
- Metaregistrar BV
- Bangning Digital Technology Co.,Ltd
Name Server Domain: share-dns[.]net, share-dns[.]com
Server Type: nginx
SSL Hashes
- bc1f466a2c1c4b885adac674e39e8fe22d26d4a5
- b9e8c8b5ddba6935c82fd5e192e4171d005b0d8c
- 134a16bfde5eb4d3908a53aa9a18a50c7b129c29
Website Title: AA Game:Aviator - Apps on Google Play
AA: Aviator Application
AAGame-new523y.apk
3860ffaa621b26c742dcfce52b916ddad6f7f4056045a0fadaf3434fc978c9ad
6da17544754706b86042b1646b6ae7101b549f539b69c5be5b68594cd9cfa969
83332d680ed84f222a5b9f2085b4fa9523e98c80d65eeecde6d4cb65d3075110
32a7c4a4dc4b14988adfa65a1c5d55df2ca39852c5e7aa61187df306436f58d7
india-aagame-7000003.apk
9a7495bb56e05389c00e4702a53eed6d946d265b20be766c92ef15e00d69ca6b
A defining characteristic of these applications is the use of the Cocos2d framework. In this model, the Android Java layer (DEX) acts as a minimal host for a native C++ engine (libcocos.so), which in turn executes encrypted, compiled JavaScript code.
Although some of the analyzed application’s code paths and text suggested they were targeting Nigerian based users, there were also samples focused on the Indian rupee (INR). Though remnants of what could be past regional targeting were observed, it's unclear if a specific user base is currently being targeted in this cluster.
Analysis of an older development variant of the Android application revealed a module called hall_marqueen. This module is hard-coded to generate fake withdrawal notifications, creating the illusion of a highly active and profitable user base:
code JavaScript
downloadcontent_copy
expand_less
setHallLabelText() {
let e = "";
// 5% chance of a "realistic" name, 95% chance of a generic "UserXXXXX"
if (p.instance.getIntRandom(0, 20) > 19)
e = p.instance.getRandomName();
else {
let t = p.instance.getIntRandom(0, 3e5).toString();
while (t.length < 5) t = "0" + t;
e = "User" + t;
}
// Randomized fake withdrawal amounts
let t = ["100", "200", "500", "1000", "5000", "10000", "20000"];
const n = Math.floor(Math.random() * t.length);
return e + " successfully withdraws ₹" + t[n];
}Cluster 2: DK777
Cluster 2 is a more generalized gambling Android app delivery. Sixteen domains registered on the same day host similar websites spoofing the Google Play store to deliver the same APK file. The application "DK777" features slots and multi-game halls, with visual assets emphasizing "big wins" and "jackpots”. The application also uses a Cocos2d framework with a more complex range of obfuscation techniques, including over 1,000 obfuscated files within the application’s classes dex file and 50+ encrypted JSC files. Multiple presumably actor-controlled sites with backups were identified that are used to send device telemetry and retrieve additional configuration and code for execution. Some of the configurations were set to use the Pakistani rupee. Languages in the apps included English, Portuguese, and Bengali.
Initial delivery domains spoof the Google Play Store for DK777 Android app delivery, including the following:
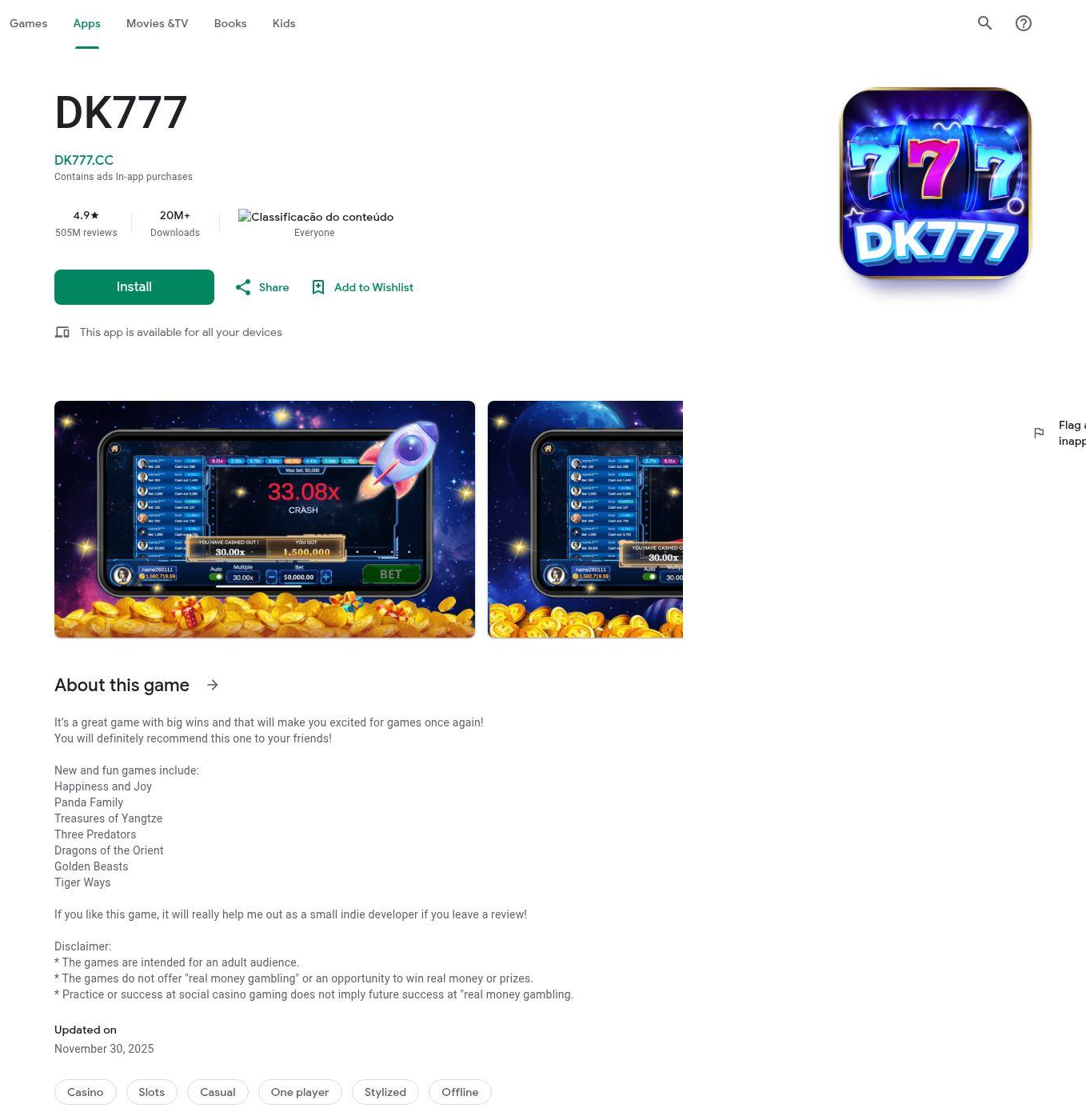
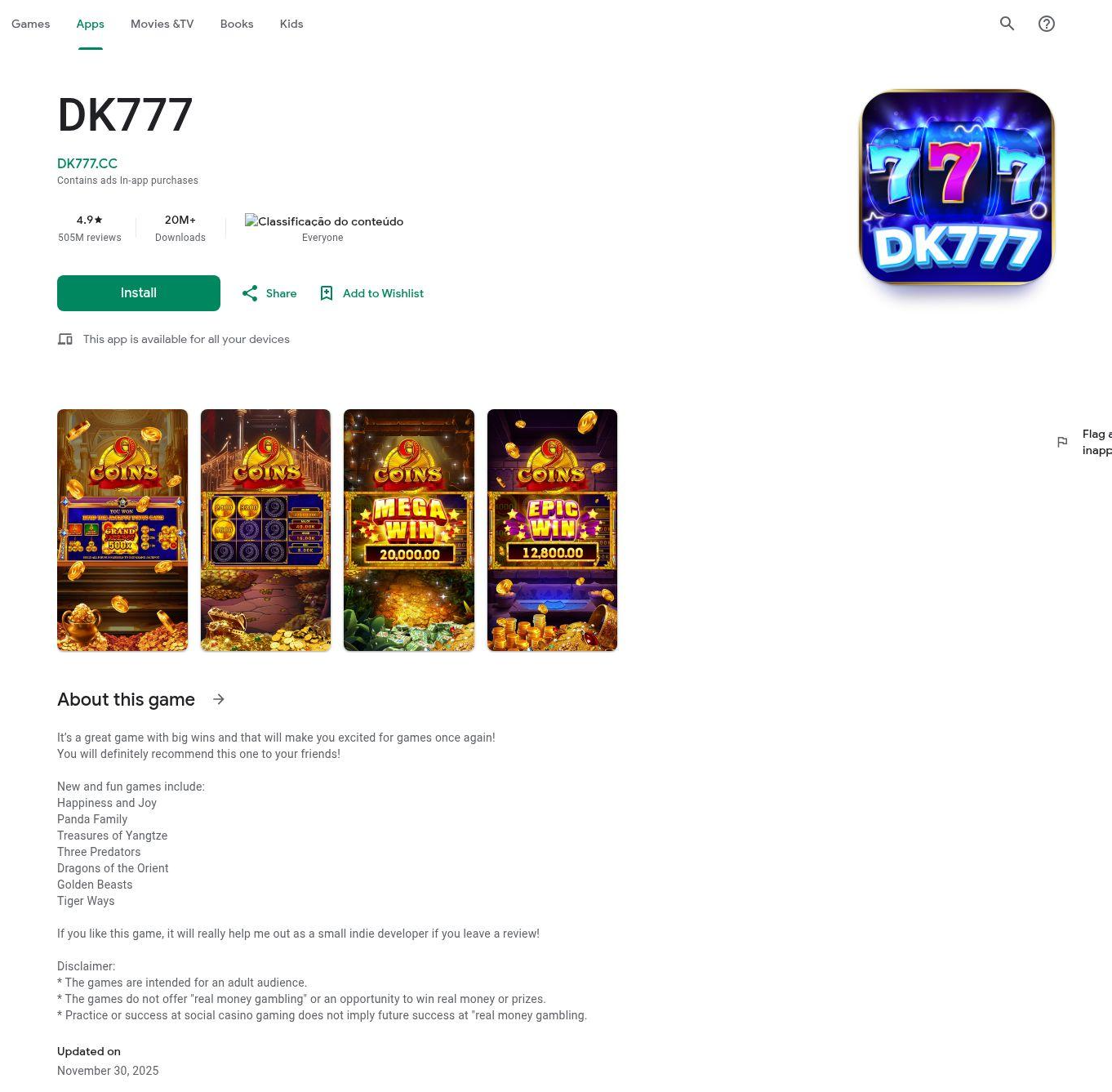
Brief details of connective tissue
ISP: CloudFlare Inc.
Registrar:
- Metaregistrar BV
- Gname[.]com Pte. Ltd.
Name Server Domain: cloudflare[.]com
Website Title: DK777 – Apps on Google Play
All the initial delivery domains download the same APK.
DK777_1000.apk
7da0e56d4c0669647aec7ea3645b882b793d4de20ab14718d4d6698fe9b3b8a2
The app retrieves external code and configuration details from actor-controlled domains.
All six domains were registered the same day (2025-12-08) with similar registration and hosting configurations. Pivoting on these configurations revealed over 120 other domains dating back to as early as 2022-01 with similar gambling themes, including "192bet[.]com" and "pak111[.]com".
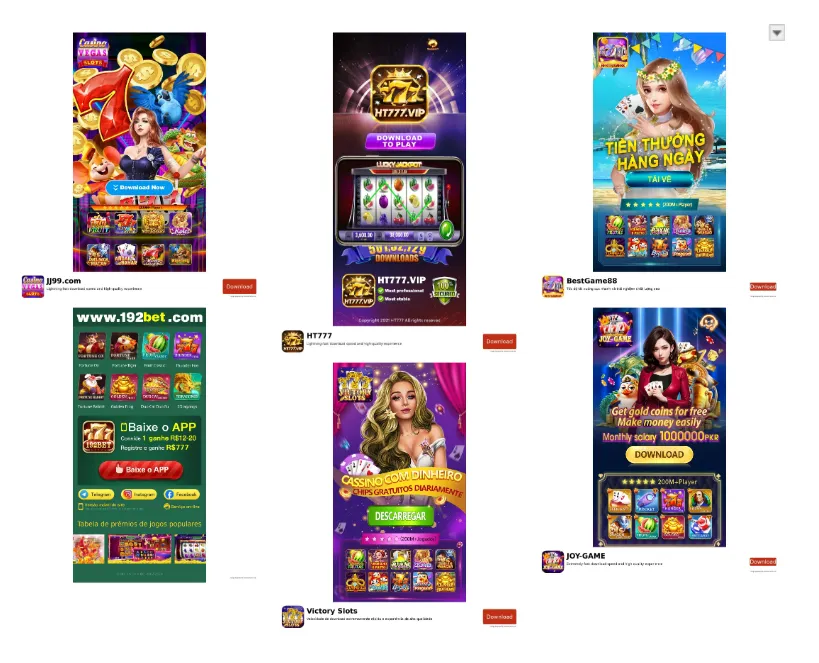

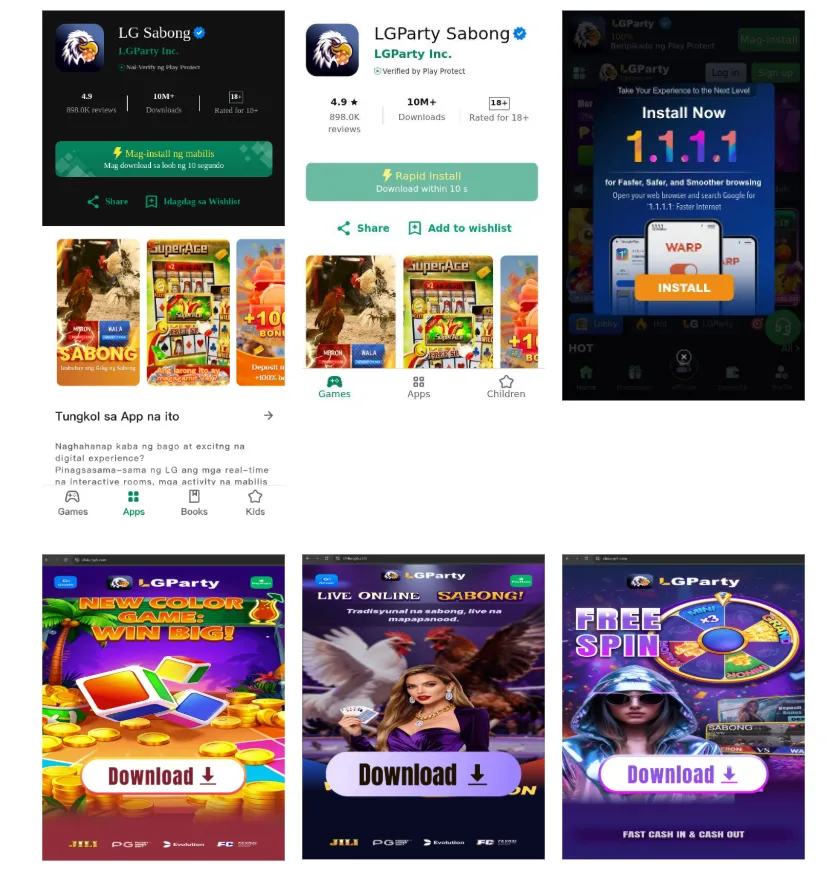
Cluster 3: LG Sabong
This cluster has approximately 196 domains. The bulk of registrations occurred between November and 2025-12 with related domains observed as early as 2025-05. The websites have aspects suggesting some localization for Filipino-speaking users. The nomenclature "Sabong" (cockfighting) suggests a focus on a culturally specific gambling market in the Philippines, while some variations of the randomized display images use the Filipino language.
Brief details of connective tissue
Google Tag Manager: GTM-M899ZXM
ISP: CloudFlare Inc.
Registrar: Dynadot Inc
Name Server Domain: cloudflare[.]com
Server Type: AliyunOSS
Website Title:
- LG - Apps
- LGParty - Apps
- LGParty - Apps on Google Play
The sites use a "Cloaking" or "Bridge Page" system typically used in the gambling industry to bypass ad platform restrictions (like Facebook or Google Ads).
The code does not build a real functional website with buttons and text. Instead, it renders a hardcoded "lgpartyShareLand" component, which are PNG images displayed as the site content. These images are randomly selected during page load from two arrays stored on an Aliyun (Alibaba Cloud) server. There are 12 different sets of images for "LGParty" and 9 sets for "LG111". This is likely done so that ad reviewers see different "innocent" versions of the page, making it harder for automated bots to flag the site as a gambling portal.Deceptive Asset URLs
- https[:]//static.lg1313abcwsx[.]com/googleInstall/lgparty_shareland_[1-12].png
- https[:]//static.lg1313abcwsx[.]com/site/ind/shareLand/page_[1-9].png
The images display download or install buttons, but the entire site is set up as an onClick event wrapper, which triggers a jumpHander function. The jumpHander does three things:
- Generates or retrieves a fbFingerId (Facebook Fingerprint ID) and stores it in the user’s localStorage
- Runs a Facebook Pixel event (PageView and ClickLand) to track that a "lead" clicked the ad.
- Redirects the user’s browser to a new URL, often to open a "Google Play" style link or an "intent" (to force open the browser on Android) to a subdomain like: https://pllay-godgle.{actor domain}.com
In the redirect action, the system uses "Jump Links" to move the user from the "Bridge Page" (the fake UI) to the actual malicious payload.
var o = "https://pllay-godgle.".concat(location.hostname).concat(location.search);return "intent://".concat(e.replace(/^https?:\/\//, ""), "#Intent;scheme=").concat(a, ";package=com.android.chrome;end")The final goal is to force the installation of a "Waistcoat" APK. The script contains a utility function to trigger a silent download and communicates with a backend API at /x2/lg-waistcoat/delivery/. The term "waistcoat" (马甲包) is a Chinese industry term for "shell apps" or "wrapper apps" — fake apps used to hide gambling content inside an innocent-looking shell to get past Apple/Google app store reviewers.
APK Filename: Dynamically generated as LGParty.apk or LG111.apk depending on the site configuration.
Download URL Pattern: https://apk-[current-domain]/apks/[siteName].apk?_ts=[timestamp]
Execution Logic: The code creates a hidden anchor element (__apk_dl_anchor__), sets the download attribute, and programmatically clicks it:
function c() {
var e = "".concat(o.Z.siteName, ".apk"); // "LGParty.apk"
var a = "https://apk-".concat(location.host, "/apks/").concat(o.Z.siteName, ".apk");
var n = document.createElement("a");
n.id = "__apk_dl_anchor__";
n.href = a;
n.download = e;
n.click(); // Triggers immediate browser download
}The goal is likely application side-loading. Google Play Store policy is quite clear on gambling and real money apps. They must have licenses to operate and complete an application process to be approved among other requirements. Because Google Play Store bans or prevents unlicensed or fraudulent real-money and gambling apps, groups may use "Waistcoat" (shell) pages, images, and fake Play Store UIs to trick the user into downloading a "verified" file from the real Play Store while trying to avoid detection. Once the .apk is installed, the app likely shows an innocent game (like a flight sim or puzzle) until it connects to its server, which can then flip a switch to load in and show the actual illegal gambling interface. In the case of these clusters, the external code update functionality suggests they were or could be used in this manner but there were no identified apps currently in the legitimate Google Play Store.
Broader Outlook and Trend Analysis
The architecture observed here, specifically the Cocos2d native bridge combined with bytecode encryption, is a hallmark of "Shell" applications used in financial fraud. By separating the distribution (spoofed websites) from the logic (encrypted JavaScript), threat actors can pivot regional themes (India vs. Philippines) with minimal changes to the underlying technical framework. With Clusters 1 and 2, this appeared to be the case as the applications sent device telemetry to external servers, then retrieved and loaded configuration and code from those external actor-controlled domains at runtime. It is suspected that both clusters operated with regional and device profile-based configurations. These configurations also enable the actor to change the behavior of the application at any time to load in malicious code after installation.
While there is no direct attribution identified thus far, this pattern has previously been associated with professional syndicates operating out of Southeast Asia that manage high-volume gambling and investment scams.
The core strategy relies on delivering illegitimate applications that deceive users into trusting them. This is accomplished through various deceptive tactics, including the spoofing of the Google Play Store, the fabrication of social proof such as reviews and win declarations, and the establishment of dedicated brand identities with widespread distribution. A key feature of these operations is the attempt to evade analysis by utilizing post-installation code and configuration fetched from actor-controlled domains.
While the applications do not appear to be overtly malicious in nature, as with typical malware granting remote access to user’s devices or stealing credentials, these applications pose as gambling and real money games with no regulation, oversight, or legitimacy. They can and likely do manipulate the gambling app behaviors such as having rigged results or non randomized outcomes.
Security Advice and Conclusion
This campaign highlights the critical role of managed app stores in the mobile ecosystem.
- Sideloading Risks: The primary defense against these campaigns is avoiding APK installations from non-standard sources. These apps require sideloading specifically because their core logic — such as the fake marquee module — would be flagged by the automated and manual review processes of legitimate stores such as Google Play Store.
- Fabricated Social Proof: Users should be informed that download counts, ratings, and reviews on spoofed websites are cosmetic HTML elements and do not reflect the application's actual standing or security.
- Managed Environments: Organizations should leverage Managed Google Play or Mobile Device Management (MDM) solutions to restrict the installation of apps from untrusted sources, as the "hot-update" capabilities of these frameworks allow an app to change its behavior entirely after it has been installed.
IOCs
Cluster 1: AA Aviator Game
Cluster 2: DK777 Related Apps
Cluster 3: LG Sabong App

Commentary followed by links to cybersecurity articles that caught our interest internally.
I know I’m not the only one that flinched when a Log4j vulnerability dropped on the Thursday before Christmas. That it’s only a 6.3 allowed me to breathe again, but only shallowly.
Long before security, I spent my days in a 911 dispatch room soloing emergency calls and coordinating the response. The overlaps between that and cyber incident response are many, but two are worth calling out today. The first is that both types of response require forming an elaborate mental map of the emergency. And the second is that both types of response aren’t embodied; you’re at a workstation, processing and integrating in real time, but without the ability to physically release the tension involved.
The lack of physical embodiment is one of the reasons 911 calls can stick with you. Recall down to the waver in someone’s voice or something you think you heard in the background can be excruciatingly intimate and precise; the slosh of water in a tub, or the bark of an unrelated dog. And anchored to the desk as you are, there is no way to work the tension out of your body at the time. You learn to sit with it, and in turn the memories sit with you.
Some cyber incident response scenarios play out similarly. We can thrive on the tension, we can perform in near-superhuman ways across parallel tasks of critical importance for an extended period of time, we can love the thrill of pressure and the satisfied exhaustion of knowing how we handled it. But it all takes a toll, and that toll can stick with you.
We ignored it for a long time in Emergency Services, and in some ways still do. But it also resulted in the establishment of mechanisms like Critical Incident Stress Debriefing, mutually supportive ways to blow off steam while acknowledging the incident, and more. Many of us working remote, though, struggle more because the work desk hangs around our neck like an albatross, and we toss it as far as possible once the work day ends. But the stress of those incidents isn’t dealt with, and the mental and physical fatigue make after-hours efforts seem impossible.
Gauge how you and your team handle incidents. Figure out if you leave the stress in your body, or if you can find a way to work it out. It’s even more critical maintenance than replacing spinning disks – because when your stress response systems start throwing errors, they’re much harder to resolve.
Take care of yourselves out there. Take care of each other. We are all we’ve got.
Podcasts
Cyberwire – Root access to the great firewall – DomainTools Head of Investigations Daniel Schwalbe interviewed on our Great Firewall series. Definitely worth a listen – just editing these pieces kept me up at night, given the impact of realizations about the technologies behind the Great Firewall.
Articles
Intezer – Tracing a Paper Werewolf campaign through AI-generated decoys and Excel XLLs – Excellent find by Intezer, accompanied by a good writeup from Reuters. Only read after your coffee and when you’re prepared for statements like “An XLL is a native Windows DLL that Excel loads as an add-in, allowing it to execute arbitrary code” because I was not ready.
Infoblox – Parked Domains Become Weapons with Direct Search Advertising – More great work with an accompanying writeup by Brian Krebs. Parked Domains continue to be one of the most common threats I see in day-to-day hunting, so it’s good to see research in this area.
DomainTools Investigations – The APT35 Dump Episode 4: Leaking The Backstage Pass To An Iranian Intelligence Operation – The next in our APT35/Charming Kitten series, with some of the strongest writing I’ve seen from our team yet. Several phrases are going to stick with me for a while, but especially “the banality of intrusion.” The depth and breadth of bureaucracy involved is sort of amazing compared to other models.
Greynoise Intelligence – React2Shell research – Greynoise has assembled a boatload of supplemental data on their github for folks defending against the React2Shell vulnerability, or those looking to hunt for exploiters. C2 IPs and domains, full payloads, hashes, and more. Lots of credit goes to Greynoise for providing this to the community.
Research Papers and Reports
GA Tech et al – From Concealment to Exposure – Understanding the Lifecycle and Infrastructure of APT domains – Some incredibly important points here as far as domains being aged, IP/DNS changes prior to public disclosure causing defender issues, a need for much longer log retention than most organizations consider, and more.
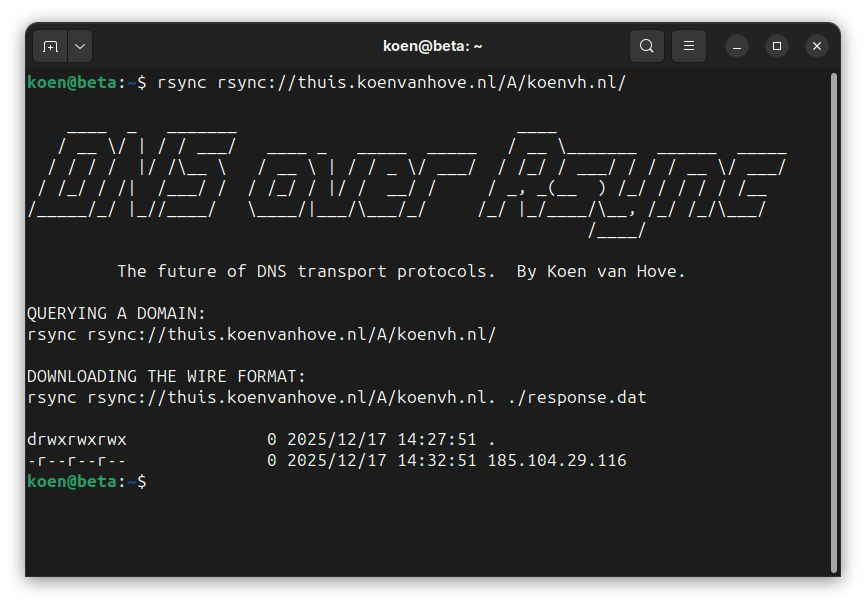
koenvh – DNS over rsync – Yes, you read that right. No, I won’t take it back, and you can’t make me. I saw it so you have to see it too, I don’t make the rules. It’s not the most cursed protocol I’ve ever seen, but it’s close.
Entertainment
The Onion – Study Finds 80% Of Americans Lack Social Connections To Pull Off Heist – Something tells me the readership for this list probably skews much further toward being able to crew a heist with their network, but that’s just a guess.
New B2B2C supply chain attack targets Booking.com customers. Attackers are compromising hotel accounts to send & "verify or cancel" phishing messages with dynamic booking data. Learn how to spot these fake domains and protect your payment info.
Since May 2025, an attacker targeting Booking[.]com customers has generated nearly 1,000 spoofed booking and hotel reservation domains. The attackers appear to be compromising hotel booking management accounts to target Booking[.]com customers directly through the platform’s official messaging channels. By sending urgent “verify or cancel” notifications, they direct victims to external phishing sites that dynamically load the traveler’s actual reservation details to steal payment information.
Details
Attack Breakdown
The attack began by compromising hotel booking accounts. Though the specifics are as of yet unknown, it is likely this activity is a tied to attacks reported in November 2025 by Sekoia.io, dubbed the “I Paid Twice” phishing campaign. Sekoia labs suspected the attacker targeted hotel staff to steal credentials for booking platforms. A question remains if the attacker targeting hotels is the same one operating the phishing kits to target the hotel’s customers. Sekoia noted that such stolen hotel booking credentials are sold on Russian-language forums for under $5,000 each. Furthermore, while we found no direct links, a Microsoft STORM-1865 report shares many of the same characteristics with exception of an identified malware delivery component.
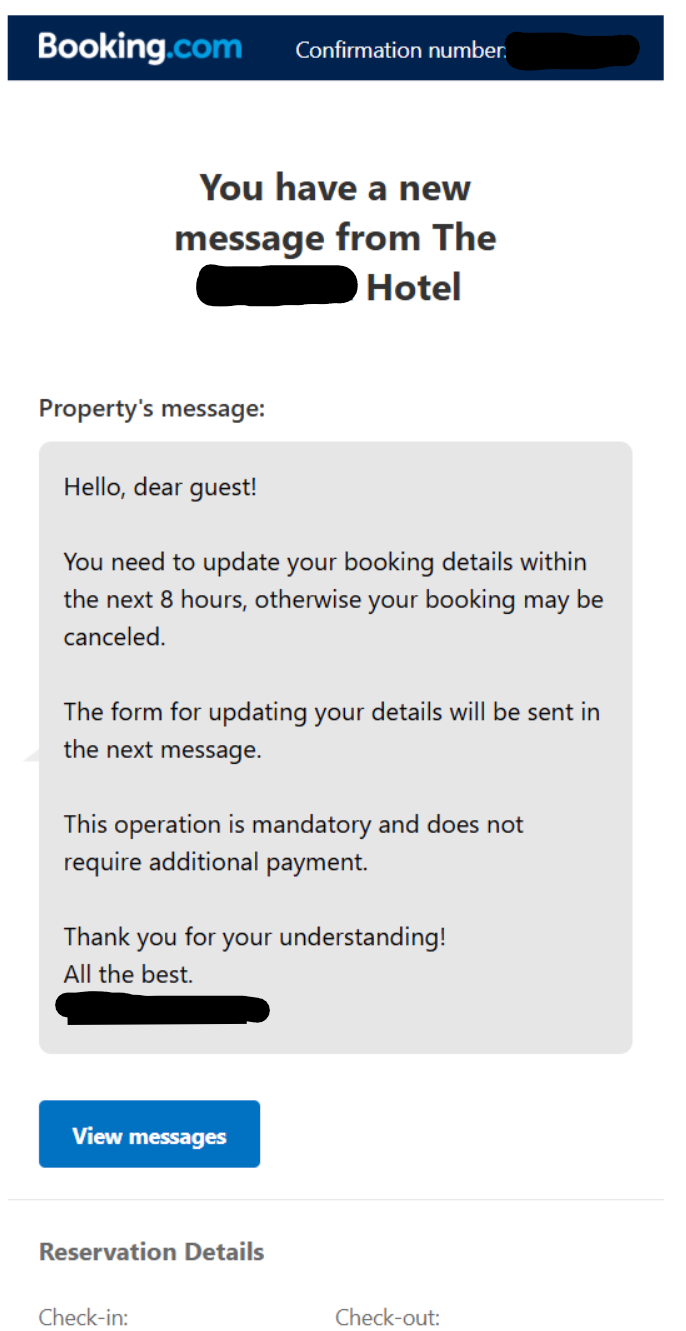
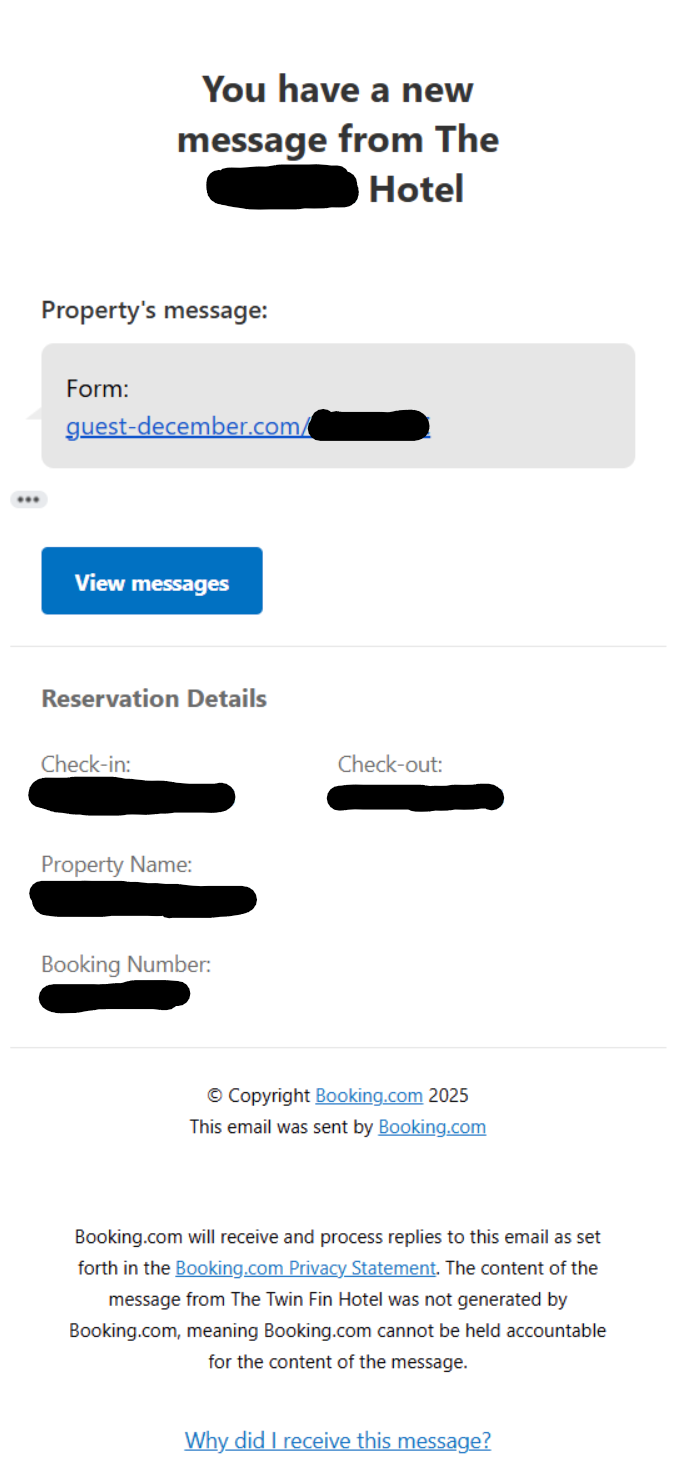
Once the attacker obtained these credentials, they then used that access to send lures to the hotel’s customers through Booking[.]com’s services. The victim receives a Booking app message and email from Booking[.]com with a message that they need to update their booking information within 8 hours or risk having their booking cancelled. If the user responds to the message, the attacker sends a URL to an attacker-owned domain with a customer-specific tracker ID.
On the attacker’s website it first presents a fake CloudFlare “Confirm that you are human” checkbox.
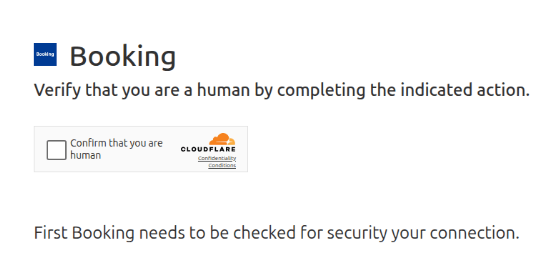
In fact, the main page loads an iframe containing the fake button and starts a timer to ask the server if the user has clicked yet.
Upon clicking the fake verification button, the site reloads, taking the customer’s booking ID from the URL and matching it against the data they stole from the hotel. The phishing page is dynamically generated to look like Booking[.]com hotel booking forms. The page is populated with the reservation hotel details and check in date. The victim is lured into re-entering their personal contact details including name, email and phone number.

Subsequently they are asked to re-enter their payment information for the hotel booking.
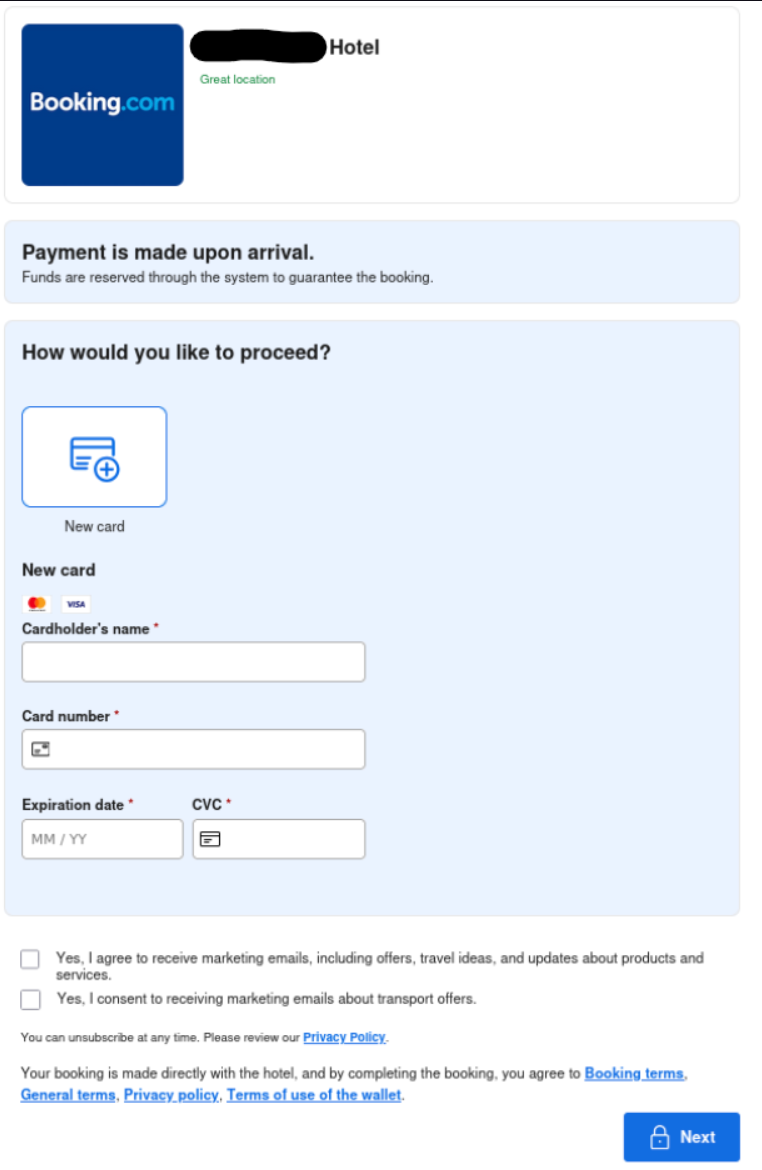
This appears to be the end goal of the attack, to retrieve contact info and payment information. Normally, we might expect this level of effort and ability to leverage trusted business relationships to attempt to distribute malware such as NetSupport RAT, but as of writing this investigation, the goal of the attack appeared limited to payment information harvesting.
Phishing Web Kit
The filepaths and scripts suggested the attack may involve Scraper/Interceptor kits, which are used almost exclusively for Booking[.]com and Airbnb scams. Such kits are often associated with the Telekopye toolkit or the “U-Admin” ecosystem (Russian-origin phishing-as-a-service).
Common filepaths for the webkit:
- /dist/sites/ALL/booking/favicon.ico
- /dist/booking/booking/styles-new4.css
- /dist/booking/booking/submit-new8.js
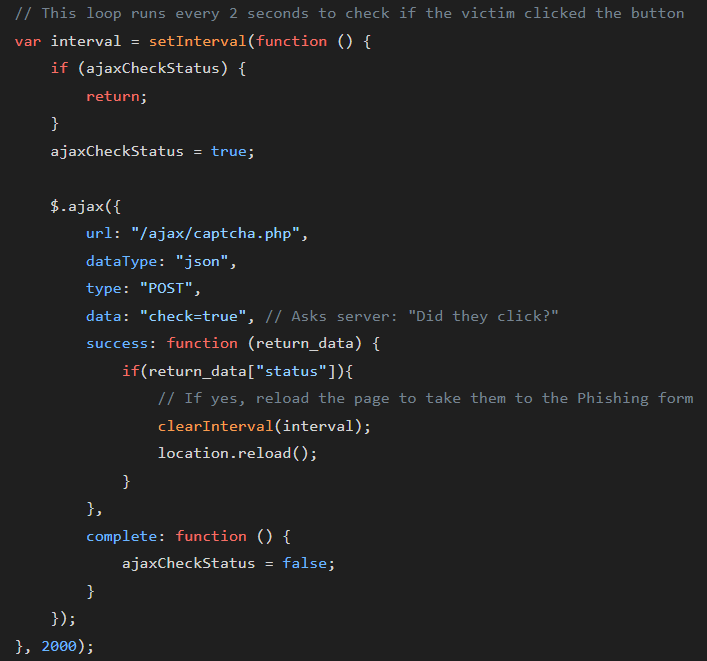
It also uses a polling Ajax endpoint with a specific set of PHP files to synchronize the victim’s browser with the attacker’s control panel:
- /ajax/captcha.php (The “Check” stage)
- /ajax/payment_card_status.php (The “Redirect” controller)
- /ajax/user_send_status.php (The “Progress” tracker)
- /ajax/change_language.php
This specific naming convention(payment_card_status.php) is a known signature of the “Drainer” or “InfoStealer” variants of the Booking[.]com phishing kit.
However, the sites investigated appeared to use a database of stolen booking information from Booking[.]com and used it to dynamically populate pages for each victim. These factors suggest the attacker is using frankenstein code partially from a common Booking web kit to dynamically load victim specific information.
Domain Infrastructure
One of the domains resolved to “80.64.19[.]92”, which has several overlaps with “77.83.207[.]34” including the following:
- host TLS fingerprint host.services.tls.fingerprint_sha256
- Ac410155847201fd764f6c56a40c7e2de7c632e22dc97a5a3dffdd7894d69c69
- host.services.ssh.server_host_key.fingerprint_sha256
- b27da9759a8f931abb34cf1a4b04aeb7979d89504f791afc28e7116288b38728
Both of the IP addresses above are based in Moscow, Russia and are seen hosting the same services from Debian Linux operating systems: Proftpd Project Proftpd, Exim, Isc Bind, F5 Nginx, Dovecot
The strong link between both IP addresses is notable as the “77.83.207[.]34” has resolved over 370 domains since May 2025 that spoof hotel and confirmation related themes, and those domains have unique emails and registrant names exposed in the registration details.
The registrant email addresses link additional IP addresses resolving large numbers of similar domain name patterns in the same timeframe including “91.92.46[.]181” with another 358 domains and “172.86.75[.]75” with 41 domains.
In a few cases domains were previously seen spoofing as Booking[.]com in December 2024 including the following two now reused in 2025 for similar purposes:
- fastchek-by-booking[.]com
- check-via-booking[.]com
Dominant Themes by Frequency (Themes May Overlap)
Primary Spoofed Entity: Booking[.]com
Specific Properties Being Impersonated
Conclusion
This campaign abuses trust relationships within the hospitality supply chain. By leveraging compromised hotel credentials to send messages through authenticated Booking[.]com channels, threat actors bypass standard email security gateways and user vigilance.
For defenders, the primary detection opportunities may lie in the distinct infrastructure patterns rather than the delivery mechanism. While the current objective appears limited to financial fraud, the actors’ established foothold within hotel administrative portals presents a significant latent risk for lateral movement or the deployment of persistent malware (e.g., NetSupport RAT) in future campaigns. The apparent theft of customer booking information also presents a latent risk to customers for follow on phishing attacks.
A question remains, why have Booking[.]com and affected Hotel chains been silent? The answer may be that Booking[.]com legally positions itself as an intermediary and may argue that the hotel is responsible for their own poor security.
What Victims Should Do
If you have received a suspicious message or believe you may have been compromised:
- Contact the Hotel Directly: Call the hotel using a number from Google Maps (not the one in the suspicious message) to verify if the request is legitimate.
- Check the URL: Genuine Booking[.]com payments occur only on Booking[.]com. Any other URL (e.g., booking-secure-verify.com or hotel-reservation-check.com) is a scam.
- Initiate a Chargeback: If you paid, immediately call your bank. Report the transaction as “fraud due to a compromised merchant account,” not just a billing dispute.
- Secure Your Accounts: Change your Booking[.]com password and enable Two-Factor Authentication (2FA). If you reused that password elsewhere, change it there too.
- Ignore “Recovery” Scams: Be wary of third-party services or random social media accounts claiming they can “recover” your lost funds; these are often secondary scams targeting already vulnerable victims.
Third-Party Platform Risks & Mitigation
This campaign highlights an architectural weakness in the hospitality sector: the operational dependency on third-party platforms (like Booking[.]com) that may not provide enterprise-grade security controls. Hotels are effectively granting “trusted insider” status to external vendors without the ability to enforce internal security policies on those platforms such as the following:
- Session Kill Switches: The inability for admins to monitor and force-terminate sessions.
- Granular Outbound Filtering: The lack of controls to block sessions from sending unapproved URLs to guests.
- Strict Access Control: The absence of IP-allowlisting to restrict login access solely to the hotel’s physical network.
Since hotels cannot force third parties like Booking[.]com to change its architecture or take on specific security liabilities or guarantees for the hotel’s use of their services, the best strategy may be to treat them as an untrusted environment. The most practical defense may be to abstract the user interface away from the staff through your Property Management System (PMS) where more granular controls may be implemented.
IOCs
A full list of IOCs can be found on our GitHub.
Domain Name Regexp Patterns
confirmation-id\d+\.(com|world|click)verif(y)?gu[ea]st\d+-booking\.comcard(verif(y)?|id)\d*-booking\.(cconfirmation-id\d+\.(com|world|click)
verif(y)?gu[ea]st\d+-booking\.com
card(verif(y)?|id)\d*-booking\.(com|world)
[a-z]+-[a-z]+-[a-z]+\.(icu|click)
.*-booking\.com$
confirmation-id081277[.]com
confirmation-id081273[.]com
confirmation-id081299[.]com
confirmation-id155632[.]com
confirmation-id755632[.]com
confirmation-id897923[.]com
confirmation-id196632[.]com
confirmation-id78443[.]com
confirm-reserve[.]com
confirmation-one[.]click
verifyguets3438-booking[.]com
verify-details574[.]world
bookedehotelle2025[.]com
verifyguets25148-booking[.]com
verifyguets24111-booking[.]com
verifyguets84511-booking[.]com
verifyguets71561-booking[.]com
confirmation-id871234[.]com
verifyguets74341-booking[.]com
confirmation-id72694[.]com
verifyguets67841-booking[.]com
verifyguets12410-booking[.]com
confirmation-id784417[.]com
….

Commentary followed by links to cybersecurity articles that caught our interest internally.

Infosec, know thyself.
It’s no surprise that I’m an advocate for deeply introspective paths. My autism positions me for rumination (and much overthinking), but also self-examination and self-evaluation in order to identify strengths to capitalize on and inefficiencies to drum out. In talks I give on autism in cybersecurity with my good friend and work partner from the TechOps side, we emphasize engaging in substantive evaluation of your own thinking, reactions, and sensitivities in relation to your work and environment.
At the right dose, self-reflection can be a superpower all its own, as well as enable more superpowers in its wake.
When cybersecurity professionals become vulnerable enough to engage in metacognitive and other reflection in public, it makes us all better defenders. One good example can often be found amidst Tricia Howard’s work over at Akamai - whether she’s writing on resilience, toxicity and mental health, and more.
The recent example I want to really amplify here, though, is a great piece from the folks at SpyCloud published on Halloween: It All Counts: From Small Wins to Global Takedowns, How Being Mission-Driven and Curious Influences Cybersecurity Investigations for Good.
You had me at “mission-driven”; after all, the RAND study quote on neurodivergents being essential for national security due to “missions that are too important and too difficult to be left to those who use their brains only in typical ways” is deeply resonant with me. You also had me at “curious” - every investigation I approach, I do so with a natural sense of curiosity that makes it all the richer. But SpyCloud’s piece revolving around their investigators sitting down to talk brains and wins provides even more insight.
From connecting threat actor motivation to behavior and likely evolution, to being able to influence threat actor decision-making in impactful ways, and motivating the team itself by empowering curiosity and impacting justice in the wider world, the conversation speaks deeply to me about critical lessons for our profession, and our industry.
To quote the piece, “iron sharpens iron, and together we get better.”
Let’s work together to form and maintain the sharpening blocks we need to make 2026 the worst year for threat actors on record.
Let’s go.
Articles
GreyNoise Intelligence - When Bulletproof Hosting Proves Bulletproof: The Stark Industries Shell Game - Excellent, brief article from Greynoise’ boB Rudis with clear technical observations to evaluate sanctions on Stark. We need more of this, and we need to prioritize review of our current enforcement methods. More on this to come…
KrebsOnSecurity - Aisuru Botnet Shifts from DDoS to Residential Proxies - Aisuru’s power boggles the mind, as seen in this recent BleepingComputer article, but its evolution is even more interesting. Some of its roots appear to spring from Minecraft disputes, others to embarrass the Chinese Communist party. And the move to offer residential proxy access is not a welcome development.
BBC - A Chinese firm bought an insurer for CIA agents - part of Beijing's trillion dollar spending spree - This should perhaps precipitate a much wider review of PRC-owned assets with deep data insights on critical American sectors. Data is now national security-critical infrastructure.
DomainTools Investigations - APT35 Internal Leak of Hacking Campaigns Against Lebanon, Kuwait, Turkey, Saudi Arabia, Korea, and Domestic Iranian Targets - From us last week, another natsec deep dive. I’m always fascinated by structural differences between threat actor groups, especially nation-state ones. In this case, it’s the regimented and almost rigid structure, contrasted with more flexible APT schemas.
CISA - Bulletproof Defense: Mitigating Risks From Bulletproof Hosting Providers - Overdue, but a good starting reference on BPH. Necessary to highlight CISA’s advice here on ASN blocking, an absolutely critical feature that many commercial products lack. Looking at you here, Palo.
NYT - Cryptographers Held an Election. They Can’t Decrypt the Results. - Turns out someone lost the key. Ironic but relatable - there but for the grace of Shamir go I.
TechCrunch - CrowdStrike fires ‘suspicious insider’ who passed information to hackers - Going to be interesting to see if charges are filed - opening Crowdstrike up to discovery there. If I was a betting man…
Mandiant - Frontline Intelligence: Analysis of UNC1549 TTPs, Custom Tools, and Malware Targeting the Aerospace and Defense Ecosystem - Iran-nexus actor with a pretty complicated portfolio compared to some of their pals.
Politico - Cybersecurity breach at Congressional Budget Office remains a live threat - At least it’s not the State Department this time? Smells faintly like Chinese trade espionage, but that’s entirely speculation.
SpyCloud - October Cybercrime Update: LummaC2’s Decline, Data Theft Extortion & Hacktivist Leaks - Good roundup on a few fronts, but especially the LummaC2 update. Someone’s got Lumma in their sights, or perhaps multiple someones.
Research Papers and Reports
Anthropic - Disrupting the first reported AI-orchestrated cyber espionage campaign - There is some ongoing controversy about this report, and understandably so. Anthropic’s reports tend to be higher-quality than the other AI firms out there, and in a narrative sense they explain their analysis well - operational tempo, request volumes, and activity patterns seem the right way to do it. But we need IOCs, TTPs, and other technical indicators as narratives are not enough. It’s worth noting that it took a while to convince any industry to share those, so here’s hoping Anthropic blazes the trail with this as well.
arXiv - Adversarial Poetry as a Universal Single-Turn Jailbreak Mechanism in Large Language Models - This may be my favorite paper ever on LLMs. There’s something incredibly funny in the Humanities coming back to haunt a technology industry and educational system that systematically defunded and deprioritized them.

Commentary followed by links to cybersecurity articles that caught our interest internally.
It’s almost November, and I’m behind on my reading.
Which isn’t anything new - I’ve been behind on my reading since about sixth grade. But the uptick in infosec-related news and activity definitely feels substantial, a crescendo building towards the end of the year, or next year’s spring offensives, or whatever’s looming over the Taiwan Strait.
De-escalation feels like a quaint notion. The cosmic microwave background of China-nexus actor persistence and ever-present staccato of Russian organized crime and nation-state operations vie for different forms of our attention, but never our rest.
F5 network dwell time has been reported as nearly two years; nearly two years from initial compromise to detection, making coffee every day, going through life events, picking the kids up from soccer practice, two sets of holiday parties.
One of the things I’m stuck thinking about as the days get longer in multiple ways is time. F5 is not the only one that’s had a dwell time like that, and it’s certainly a difference from short-duration actors with more traditional criminal motives. But we’re also seeing the landscape change as Large Language Model-assisted cyber operations begin surfacing. Most uses there are in their infancy, similar to the defender usage of LLMs - still in the “horseless carriage” phase of technology, to steal a concept from Douglas Rushkoff. But they’re maturing - slow, fast, and otherwise.
Looking back to some earlier artificial intelligence work, Google’s AlphaGo took several years to gain mastery level in the game Go, across thirty million games. AlphaZero reached mastery in 4.9 million games, and learned how to beat AlphaGo in 3 days when pitted against it adversarially. OpenAI’s DOTA2 bot amassed 45,000 years of experience in ten months’ time. This was all years ago.
I am left wondering, if AI-based cyber threat offense reaches a more mature level, what happens when you take a system that can learn centuries’ worth of lessons in days, and connect it with strategic actors whose focus is sometimes across decades.
What does that do to time?
And in the interests of time, let’s move on to the news and chatter.
Several of us from DomainTools Investigations will be at CYBERWARCON in Arlington, VA on November 19th. If you’re there as well, don’t hesitate to say hello. Or tell us your secrets.
We’re good at secrets.
Podcasts
Three Buddy Problem - JAGS LABScon 2025 keynote: Steps to an ecology of cyber - Like last month, also from LABScon; in this case, Juan Andres Guerrero-Saade’s keynote presentation on the state of cybersecurity, how to navigate it, and what to look for next. Thirty minutes of some of the best cross-disciplinary exploration I’ve heard.
China Talk - PLA Purges and How Xi Rules with Jon Czin - Background and practical implementation of thinking and planning that informs the Chinese government’s operational stances.
Lawfare - CYBERCOM Legal Conference: The Role of the Private Sector in Conflict - Reposted episode from April but a good panel on public/private work in cyber, specifically in the context of conflict.
Articles
Bloomberg - Hackers Had Been Lurking in Cyber Firm F5 Systems Since 2023 - This has been a bit of a sleeper story so far, but most of the watershed compromises haven’t been declared yet. Spent a night or three tracking possible DNS threads that roughly indicated the same time fence, but you never know until it’s out in print.
GTIG - Pro-Russia Information Operations Leverage Russian Drone Incursions into Polish Airspace - Rare (I think?) and very well-done Google Threat Intelligence piece on opportunistic hybridity in a real-world information campaign. All the notional borders we build fade into the background once feedback loops between cyber, info, and kinetic blend natively like the rest of the world.
Infoblox - Vault Viper: High Stakes, Hidden Threats - The ubiquity of gambling alongside fraud in cyber threat intelligence is no surprise to analysts, but the interconnections and scale often astound. Infoblox doing one of those things they do so well: sketch the outline of the badness, isolate and connect clusters, and lay it all out at micro- and macro-levels.
RecordedFuture - Dark Covenant 3.0: Controlled Impunity and Russia’s Cybercriminals - “Cybercrime in this environment cannot be understood solely as a commercial enterprise; it is also a tool of influence, a means of information acquisition, and a liability when it threatens domestic stability or undermines Russian interests.” - Fascinating deep-dive that paints a much more complex and ambiguous picture of Russian state interaction with cybercrime groups than we’re used to.
Trail of Bits - Prompt injection to RCE in AI agents - Great writeup centering around mapping and exploiting commands marked as “safe” in AI agents and thus allowed to circumvent human review.
Ars Technica - New image-generating AIs are being used for fake expense reports - Well that’s creative. Admittedly, as a teen I pulled a dot matrix printer and Tandy out of the attic to forge my report cards (which worked great in the short term, not so much in the long term, but that’s a story for another time).
Research Papers and Reports
arXiv - Living Off the LLM: How LLMs Will Change Adversary Tactics - Speculative paper on translating LLM proficiencies into living-off-the-land techniques for adversaries. Read, and start planning.
Dartmouth ISTS - From Chaos To Capability: Building the US Market for Offensive Cyber - Novel research specifically around private-sector circumstances supporting government cyber operations, including current state of play, gaps, and opportunities in this largely gray area. Feels substantially different from the separate hybrid models we’re used to reading about in China and Russia, among other places.

Ian Campbell's recap of DTI's participation at BSides NoVa
As one part of the broader infosec community, it’s one of our pillars within DomainTools Investigations to contribute meaningfully to collective knowledge as well as common good. We believe that doing so reinforces the fact that cybersecurity is a living ecosystem - an ecosystem of ecosystems, in fact - and thrives or withers accordingly. From Head of Investigations Daniel Schwalbe down through the ranks, we want to see a thriving ecosystem, and there’s no other way to do it than to put our money and time where our mouths are.
You’ve got to have some skin in the game.
One great example of security community activity is BSides NoVa, which happened October 10 & 11. We stepped up as a Gold sponsor alongside other great organizations to bring together a diverse group, from folks looking to enter the industry to those retired from decades in it. In addition, we submitted two talks that were accepted: my colleague Malachi Walker’s talk on cyber threats in F1 racing, and my talk on DNS and domain intelligence in investigative journalism.
BSides is more than just a professional opportunity for me - it’s a deeply personal part of my path into and within infosec. While information security and cybersecurity have always been special interests of mine, the first conference I attended where I really felt the passionate burn to be an integral part of it all was a Security BSides conference, BSides Boston 2016. I sat in Microsoft’s NERD facility (not kidding about the name!) and felt the first undeniable yearning to be doing the cool work that speakers presented, even though I could only half-follow most of it at the time.
From the smallest BSides in a local meeting hall to major events like BSides CHARM, Las Vegas, or NoVa, both the model and the reality represent some of the best our community has to offer. It fills me with pride to be part of an organization that could sponsor this event.
For my part, I was honored to speak to a full room about DomainTools’ history of enabling investigative journalists and security researchers in the community through our Grant access program. We’ve been presenting at the NICAR journalism conference for nearly a decade now, grateful that interest drives not one but two NICAR sessions. In addition to access, we’ve been providing training and investigative support and review to help journalists identify objective truths in data that inform their investigations.
Earlier this year we provided a technical writeup on one such investigation over on our corporate blog, and the details there formed the backbone of this presentation as we demonstrated the value of both DNS records and Whois/RDAP data in unraveling layers of truths. We were also able to highlight several other places where either our data proved helpful or we collaborated with journalists and investigators directly this year alone, including CitizenLab, Reuters, and the prolific Brian Krebs.
Slides for my presentation can be found here on Google Drive (contact me if you need them placed for download elsewhere).
In addition to the slides, I’d like to reiterate my answer to one of the Q&A questions at the end. The session participants were awesome and engaged, across all levels of familiarity with DNS and domain data, and asked excellent questions. One of the better questions was “Where do I learn how to do this kind of work?”
As my introduction slide notes, I’ve got no degrees and no certifications. I cannot speak to higher education or training programs. What I can say is that learning from the folks actually doing the work is key. There are very few areas in which I have so much knowledge that I can claim to be a subject matter expert (which troubles me sometimes as far as both impact and career go). But where I excel is identifying work that I want to be doing, finding the people already doing it, and reverse-engineering their processes to build my own. In practice, this looks like not just reading investigations from Brian Krebs, Shelby Grossman, Renee Diresta, CitizenLab, or Infoblox’ Threat Intel team, but actually writing down and analyzing each step of their investigation to learn where and how they pivot from one piece of data to another, as well as areas they focus on as often fruitful investigatory avenues.
Another great source is journalist Craig Silverman, who devotes his time to teaching other journalists how to dive deep digitally. In addition, pay attention to the various places where Yael Grauer pops up, from Consumer Reports and the Associated Press to DEF CON, especially around privacy or public interest/technology & integrity issues.
Learn from folks doing the work - and then change, adapt, iterate, and customize it. Make it your own.
And go make a splash.
My thanks to BSides NoVa, its sponsors, and everyone who came to my talk or that I talked with on Saturday. We are the ecosystem. Let’s dig, share, and thrive.

A deep dive into the 4-stage NPM phishing attack flow that led to high-profile repository account takeover. Protect your development security.
Recently, a series of high profile supply chain compromises were caused by malicious code written to NPM repositories managed by stolen developer credentials. While developers of prominent NPM repositories have been targeted for many years, these events prompted CISA to release an alert due to their widespread nature. Attackers stole developer accounts through a phishing campaign involving fake NPM management and login pages. This tactic enabled them to take over accounts for malicious activity and remains one of the most common and effective methods of credential theft.
Details
NPJMS is the largest JavaScript repository, with two official domains: npmjs.com is the main site and npmjs.org is also an official NPM domain. Phishers have historically used variations of this domain to deceive users, leveraging common tactics such as typo-squatting through domains like “npnjs[.]com”, which are particularly easy to overlook when presented in lower case characters.
Examining a recently spoofed NPM login page configuration with the domain “npmjs[.]pro” demonstrates how the attack progresses through three distinct stages, each designed to capture a piece of information or deceive the user into the next step.
Stage 1: Homepage Lure
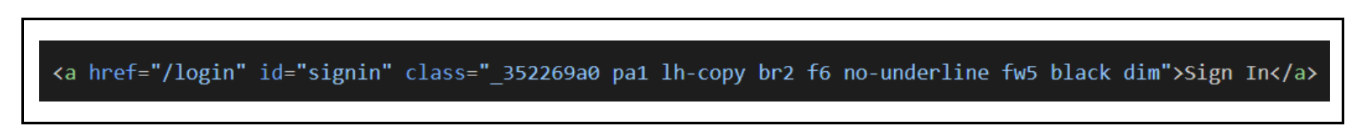
This is the initial landing page of the phishing site, designed to build trust and initiate the login flow.

This is a relative sign-in link. On the malicious domain, clicking "Sign In" sends the user to the /login path on the attacker's server, not the legitimate npmjs[.]com. The attacker's server logs the request and serves the fake login page (Stage 2) in response.
Stage 2: Initial Credential Capture
After being funneled from the fake homepage, the user is presented with the fake login form.

The form's action="/login/" sends the submitted username and password to a script on the attacker's server. The attacker's server captures and logs the credentials. It then uses them to initiate a login attempt on the real npmjs[.]com, triggering a legitimate email OTP to be sent to the victim. At this point, the user's primary npm credentials (username and password) are compromised,and the next stage is to retrieve their MFA/OTP code.

Stage 3: MFA / OTP Code Interception
The attacker's server immediately presents a page to intercept the second-factor authentication code.
This form captures the value from the name="otp" field and sends it to the /login/email-otp endpoint on the attacker's server. The user receives a real OTP via email (triggered by the attacker), which reinforces their belief that the process is secure. The attacker's server receives the valid OTP and now possesses all information required to hijack the account.

Stage 4: Session Hijack and Evasion
This final stage is a server-side action to complete the attack.
The attacker uses the captured credentials and OTP to establish their own authenticated session on the real npmjs[.]com, then redirects the victim to avoid suspicion. The attacker now has full, authenticated access to the victim's npm account. The victim remains unaware that their account and session have been compromised. Their browser redirects them to the real npm sign-in page, making them believe the process did not complete.


Conclusion
This detailed attack flow for credential theft and account takeover shows that classic credential harvesting tactics remain highly effective. As our reliance on shared software supply chains grows, developer vigilance has never been more important. While multi-factor authentication (MFA) is an essential defense, this example shows that OTP codes are only as secure as the domain they are entered into. Always verify the URL in your address bar before entering credentials, and consider adopting phishing-resistant MFA, like hardware security keys, to truly secure your accounts.
IOCs
The provided IOCs are recently registered typosquatted domains of NPMJS.
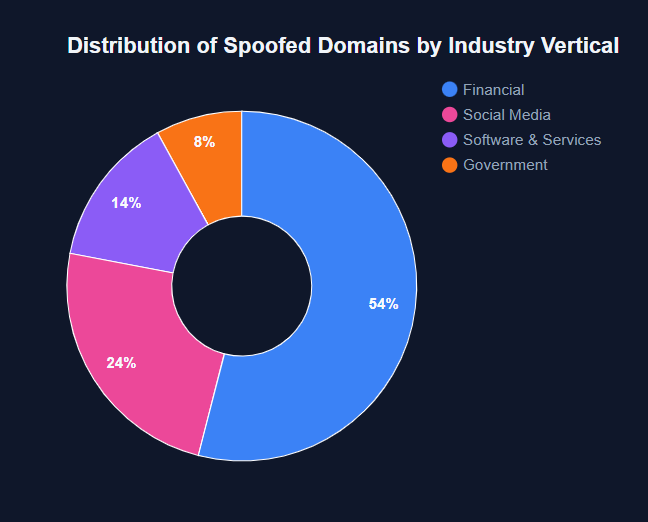
Starting in September 2024, a financially motivated cluster of more than 80 spoofed domain names and lure websites began targeting users with fake applications and websites themed as government tax sites, consumer banking, age 18+ social media content, and Windows assistant applications. The actor used these spoofed domains to deliver Android and Windows trojans likely for the purpose of stealing credentials or more overtly through the use of fake login pages.
Starting in September 2024, a financially motivated cluster of more than 80 spoofed domain names and lure websites began targeting users with fake applications and websites themed as government tax sites, consumer banking, age 18+ social media content, and Windows assistant applications. The actor used these spoofed domains to deliver Android and Windows trojans likely for the purpose of stealing credentials or more overtly through the use of fake login pages.
Details
Windows Installation Assistant download themed websites such as the following were used to deliver Windows trojans.
ms32-download[.]pro
corp-ms32-download[.]pro

Download URL: https[:]//cozzystaysemarang[.]com/temp/winsetup-stable-windows_x86_x64_software_package_revision_final.exe
Filename: winsetup-stable-windows_x86_x64_software_package_revision_final.exe
Sha256: 3767140145cef85204ddec1285f5dc8544bfcf8ff22318c11073baaa476385fc
The same delivery domain was previously observed delivering APK files in June 2025.
APK Sha256: a83a442f930fea310d391f852385e3673d8c7128e5bbdc2b68217838c78381fa
More recent versions used a different domain with a long URL likely to hide the filename from automated security tools and, to a lesser extent, human review. The excessive spaces (%20 in URL encoding) and length may bypass some detection rules or regular expressions to match malicious patterns..
Download URL:
https[:]//fleetfedx[.]com/Installer%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20em_OtvJCxP1_installer_Win7-Win11_x86_x64.msi
SHA256: 71cd466073bf23b43111dbc68ccaf1064e737f3f9ffebfec9a6f5146af6a34b9
The download links also contain a Tracking Pixel in the on-click event: onclick="fbq('track', 'Lead');" This indicates that the attacker is running this as a campaign. They are likely using Facebook ads or other methods to drive traffic to this fake page and are tracking their "conversion rate", a metric of how many people they successfully trick into clicking the malicious download link.
Facebook Tracker Ids:
- 1354988235984551
- 690114973584418
- 1327164645166821
Additionally, a Yandex tracker was also identified in use: 97105740
Connective Tissue
Registrar
- PDR Ltd. d/b/a PublicDomainRegistry.com
- GMO Internet, Inc.
IP ISP
- BL Networks
- H2nexus Ltd
- H2.nexus Frankfurt Network
Name Server Domain
- regway[.]com
Top Level Domains
- Pro, Shop, Com, Icu, Top
Registrant Email Domains
- fviainboxes[.]com
- dropjar[.]com
- replyloop[.]com
- yopmail[.]com
- robot-mail[.]com
- protonmail[.]com
Trackers
- Facebook: 690114973584418
- Facebook: 1327164645166821
- Facebook: 1354988235984551
- Yandex: 97105740
The majority of the cluster’s domains targeted users with age 18+ themed TikTok, YouTube, and online Gambling Android applications. Other themes specifically involved several prominent consumer banks and cryptocurrency exchanges including USAA, PMC, Bloomberg, and Binance. A subset of the domains resolve fake Windows 11 Installation Assistant and TrustCon VPN application downloads.
A breakdown of the cluster’s domain and websites by spoofed industries shows the majority are directly financially related, including the Government tax sites.
Sample screenshots of spoofed websites for malware delivery and credential harvesting:

Conclusion
This report highlights a persistent and financially motivated cybercrime operation employing common techniques, including spoofed domains and lure websites to distribute malware and harvest credentials.
The most common lures preyed on curiosity and desire, which can override a user's normal caution. The promise of forbidden or exclusive content is a powerful social engineering tool. Subsequently, victims are often embarrassed to admit how their device was infected. They are less likely to report the malicious app to authorities, security vendors, or even their IT department, allowing the malware to persist longer and the campaign to remain undetected.
They operate with the mindset of a malicious marketing firm, prioritizing scale and conversion rates over high-level technical sophistication. The use of template-based website builders indicates a focus on rapid deployment and disposability of their infrastructure, allowing them to quickly pivot and evade takedowns, browser-based warnings, and blocklisting mechanisms.
Users are advised to exercise extreme caution when encountering unfamiliar links or download prompts, particularly those related to banking, social media, or system utilities.
IOCs
Emails
Domains

Commentary followed by links to cybersecurity articles that caught our interest internally.
The days are getting shorter, and so is the news cycle.
It’s A Lot.
Bright spots emerge from the pattern, and one of the brightest in a while occurred last week for me - LABScon. SentinelOne and various sponsors manage to gather nearly two hundred of the top cybersecurity folks every year to talk and listen to each other, and I was honored to be admitted this year. The agenda itself is public and tells you enough to know just what kind of impact speakers can have: human rights investigators, harassment fighters, nation-state espionage mitigators, and more.
While a lot of it was TLP:RED, one thing I’m confident in sharing is the week showed me a community of folks intent and determined on doing good for the world. Many are positioned to follow through on that in some way and are excited to talk about it to a full room or one-on-one with a complete stranger.
It’s a posture I’m trying hard to carry back from con and out into the world.
On another note, something I’m seeing more of that I want to flag for folks: RecordedFuture published a great report on Stark Industries workarounds to deal with EU sanctions, and Brian Krebs expanded upon it with a great post as well.
One of the common themes in conversation alongside harder research lately has been the intermediate and long-term ineffectiveness of many of our interventions targeting malicious actors, groups, and campaigns. Takedowns are momentarily gratifying - as I’ve said before, we need to celebrate the wins where we can - but do not seem to provide longitudinal benefits. What does effective long term disruption look like, and is it feasible? What are the models, and what are the realities?
For my part, I’ve been looking at bad actors’ activities before and after US OFAC and UK OFSI sanctions to understand both preparation and reaction. Emerging from technical observables like DNS and BGP is an opaque but solid understanding that bad actors are much better at reliability engineering and disaster recovery than we want to admit, from domain mirroring all the way up to anticipatory Autonomous System takeover. I’ve submitted a talk to CYBERWARCON on the topic (and hopefully it’s accepted!), but if folks reading this know of work around long-term disruption, cybersecurity-related sanctions research, or adjacent topics, I’d love to hear from you. Please shoot me an email at CSRL at domaintools[.]com.
Podcasts
Microsoft Threat Intelligence - Stopping Domain Impersonation with AI - I know, I know, I’m tired of AI all the time too. But it’s timely and important to stay on top of. Good conversation, especially around how the problem is one of scale rather than sophistication.
Three Buddy Problem - I can’t choose between them, so you get all three Live from LABScon episodes.
- Lindsay Freeman on tracking Wagner Group war crimes - Hearing Freeman talk about this was heartbreaking, but the work her group does around this topic is inspiring. Deep, dark OSINT
- Visi Stark shares memories of creating the APT1 report - If nothing else listen for the excellent and hilarious dynamic between the hosts and Stark, but also, the interview carries some great insights on the history and current state of affairs of analysis and threat intelligence.
- Aurora Johnson and Trevor Hilligoss on China's 'internet toilets' - Great interview on toxic online communities in China. Also, I second Juan on “Spycloud is ****ing awesome.”
Articles
The Record - Ransomware gang takedowns causing explosion of new, smaller groups - Immediately thought of research we conducted with Analyst1 and Scylla Intel and presented at SLEUTHCON earlier this year. Of particular interest is the finding that disruption tends to result in smaller groups reconstituting around critical trust relationships.
Infoblox - Deniability by Design: DNS-Driven Insights into a Malicious Ad Network - Incredibly good work by Infoblox weaving deep technical details and deep narrative into a systematic understanding of not just malicious adtech but the behavior behind it and thorough methods to fingerprint and track it.
Morningstar - Unit 221B Raises $5M in Seed Funding To Convert Threat Intelligence into Real World Arrests - You love to see it. Congratulations to our friends at Unit 221B, who should have people throwing large piles of cash at them all the time, given how excellent their work is.
Google TIG - Another BRICKSTORM: Stealthy Backdoor Enabling Espionage into Tech and Legal Sectors - Targeting profile prioritized “legal services, Software as a Service (SaaS) providers, Business Process Outsourcers (BPOs), and Technology.” Excellent writeup by TIG, as always.
Schneier - Surveying the Global Spyware Market - Schneier highlights two important points: that investment in spyware companies has risen lately, and the role of brokers and resellers that often go unnoticed in the chain.
Koi Security - First Malicious MCP in the Wild - Thousands of downloads a week and it’s copying every email to the dev’s personal server. Because the S in MCP stands for Security!
CSO - Why domain-based attacks will continue to wreak havoc - The dangerousness of these attacks long predated AI, including at scale, but this is a pretty good review of some domain attacks to take note of and ensure you’ve worked into your defenses and simulations.
Group-IB - Mapping the Infrastructure and Malware Ecosystem of MuddyWater - Not always the biggest fan of Group-IB, but indicators are indicators, and there’s some good work here about how Muddy Water’s tradecraft is evolving.
Microsoft - Microsoft seizes 338 websites to disrupt rapidly growing ‘RaccoonO365’ phishing service - Joint work between Microsoft DCU and Health-ISAC, highlighting the role RaccoonO365 has adopted in targeting the healthcare sector.
Research Papers and Reports
arXiv - Large Language Models for Security Operations Centers: A Comprehensive Survey - Not ground-breaking, but some valuable LLM/SOC fundamentals covered here.
Entertainment
GadgetReview - Massive Attack Turns Concert Into Facial Recognition Surveillance Experiment - Massive Attack hasn’t commented on data retention from the event, laying bare the ambiguity and lack of agency that goes unseen in all the other applications. A+

A group has been targeting Indonesian and Vietnamese Android users with banking trojans disguised as legitimate payment and government identity applications. The operators exhibit distinct domain registration patterns, often reusing TLS certificates and grouping domains to resolve to the same IP addresses, with a strong operational focus during Eastern Asia's daytime hours.
Since approximately August 2024, a group has been targeting Indonesian and Vietnamese Android users with banking trojans disguised as legitimate payment and government identity applications. The operators exhibit distinct domain registration patterns, often reusing TLS certificates and grouping domains to resolve to the same IP addresses, with a strong operational focus during Eastern Asia's daytime hours.
Details
The pattern was initially identified through the monitoring of suspicious site elements such as those associated to Google Play Store http.html:"VfPpkd-jY41G-V67aGc" that may suggest spoofed Play store websites for malware delivery.
icrossingappxyz[.]com
The page contains fake buttons for Google Play Store and App Store application downloads. Clicking the Google Play starts an on-page download progression bar and then prompts for a file store download location on device. The Apple App Store link was nonfunctional.
The site uses an obfuscation wrapper with Socket.IO library, which enables real-time, bidirectional communication with a server. This is highly abnormal for a download page. Instead of linking directly to a file download, when a user clicks the Android button, it initiates a WebSocket connection: socket.emit('startDownload', ...). The server responds by sending the .apk file back to the browser in many small chunks. The browser listens for these with “socket.on('chunk', (chunk) => { chunks.push(chunk); });”. As the server sends data, it also sends progress messages (downloadProgress). The script uses these to update the on-screen progress bar, making the user believe a normal download is occurring. When the server sends the “downloadComplete” message, the script combines all the chunks in memory and sets the type to 'application/vnd.android.package-archive', the MIME type for an APK file. It then creates a temporary local URL for the file and creates an invisible <a> link, pointing to the temporary file URL and programmatically clicks it. This initiates a user download prompt from the browser.
The malicious site operators likely attempted to evade detection and hide their malware store through the elaborate download method. Network security and firewalls might be configured to block direct downloads of .apk files. However, by hiding the file transfer inside WebSocket traffic, it can often slip through undetected. Since there is no static URL pointing to the malicious file, automated security scanners that crawl websites looking for malicious links will not find it.
It is worth noting that some browsers correctly flagged these downloads as suspicious with download warning prompts such as the following:
IdentitasKependudukanDigital.apk
1f9253092c5a2abdb7bc3d93fccad85f23ce5bfde38377c792a242f045afcdb5
The file was detected as BankBot.Remo.1.origin, a previously closed source banking trojan that had its source code leaked on Russian-language forums in 2016. This has resulted in many variants.
Other much more commonplace malware delivery sites were also used such as the following spoof of M-Pajak, a tax payment app. It simply spoofs the Google App Store page and has a direct download URL to the malicious file stored on the server. Notably, the site used a mix of Thai, Vietnamese, Portuguese, and Indonesian language in the HTML code instead of dynamically inserting the correct language strings based on the visitor's Accept-Language header or GeoIP. This suggests these are template files used by unsophisticated operators.
twmlwcs[.]cc
Download URL: https[:]//twmlwcs[.]cc/tax-app/M-Pajak.apk
M-Pajak.apk
SHA256 Hash: e9d3f6211d4ebbe0c5c564b234903fbf5a0dd3f531b518e13ef0dcc8bedc4a6d
The downloaded file is also a loader for BankBot and is configured with the following C2 domains:
saping.ynhqhu[.]com
aaping.ynhqhu[.]com
admin.congdichvucongdancuquocgia[.]cc
admin.outdoormovietheaters[.]com
Of the over 100 domains identified in this activity for malware distribution, there were a very limited number of variations in the spoofed content used for delivery. There were slight variations as can be seen from the following sample screenshots in addition to following the fake verification trends that have become commonplace over the past year.

The group also has a nice habit of keeping their malware in open web directories such as the following:
Open Index of dgpyynxzb[.]com
Open Index of ykkadm[.]icu
indiemusicacademi[.]com
Domain Registration Patterns
Over the past 12 months, the actor was observed using distinct domain registration patterns. This often included the reuse of TLS certificates on two domains and grouping multiple domains to resolve to the same IP addresses.
- ISP:
- Alibaba
- Scloud
- CloudFlare
- IP Country: SG, ID
- Common Website title and page:
- Identitas Kependudukan Digital- Apps on Google Play
- Server Type: nginx
- Nameserver:
- share-dns[.]net
- cloudflare[.]com
- SSL Issuer: R10, R11, WE1
- Registrar:
- Gname.com Pte. Ltd.
The most prolific registration patterns were the use of Alibaba ISP, Gname Registrar, and share-dns[.]net nameservers.
Heatmaps showing the domain registration (left) and first seen DNS requests (right) with the time of day (UTC) over the year.
With the heatmaps for both domain registration and first seen DNS resolutions showing a visually similar grouping, it can also be observed that the delta relative to the domain registrations and first seen DNS requests averaged 10.5 hours over the year. This suggests the domains may be consistently operationalized quickly after registration though not nearly as rapidly as other more prominent cyber crime groups.
The time data shows a strong grouping around eastern Asia's daytime hours, as is expected with the likely focus on targeting Indonesian and Vietnamese mobile users. It may also suggest the operators are working during the same times, if not also located in the same region.
Conclusion
The malicious operators employed some methodologies to bypass network security that might block direct downloads and prevent static URL-based security scanners from detecting the malicious files. However, it is worth noting that some browsers correctly flag these downloads as suspicious, displaying warning prompts to users and serving as a crucial line of defense for end users. Additionally, several commonplace methodologies employed prominently by less sophisticated financially-motivated groups such as spoofing Google Play Store allow for the identification of these spoofed malware delivery sites. The consistent use of Alibaba ISP, Gname Registrar, and share-dns[.]net nameservers across their operations provides a clear footprint of their infrastructure. While some spoofed sites, like twmlwcs[.]cc, show mixed language code possibly indicating template use by less sophisticated elements, the overall campaign exhibits a coordinated approach to malware delivery. Overall it is likely financially motivated and suspected of being operated by a group in the same region.
IOCs
Domains (see them on our Github as well)
Sha256 Hashes

