The title of this month’s newsletter is a deep cut taken from the height of my favorite music genre, the admittedly awkwardly titled “Alternative Music.” What can I say, the 1990s in Seattle were wild, man - you had to be there.
Speaking of being there, last week was the Thanksgiving Holiday here in the United States. Normally my newsletter goes out on the last Tuesday of the month, but considering a lot of security professionals in the US got Thursday and likely Friday off, we decided to push publication by a week, so hopefully more of you can enjoy this edition instead of it getting buried under mashed potatoes and gravy!
The weather here in the Pacific NorthWest has firmly settled into “damp mode” (IYKYK), and the temperatures have started to creep below 40 degrees Fahrenheit (below 4 degrees Celsius for my international friends). I refuse to call it “The Big Dark” however - stop trying to make “The Big Dark” happen, Gretchen! Despite the cold, I’m happy to report that the intensity of DomainTools Investigations’ research output is only heating up.
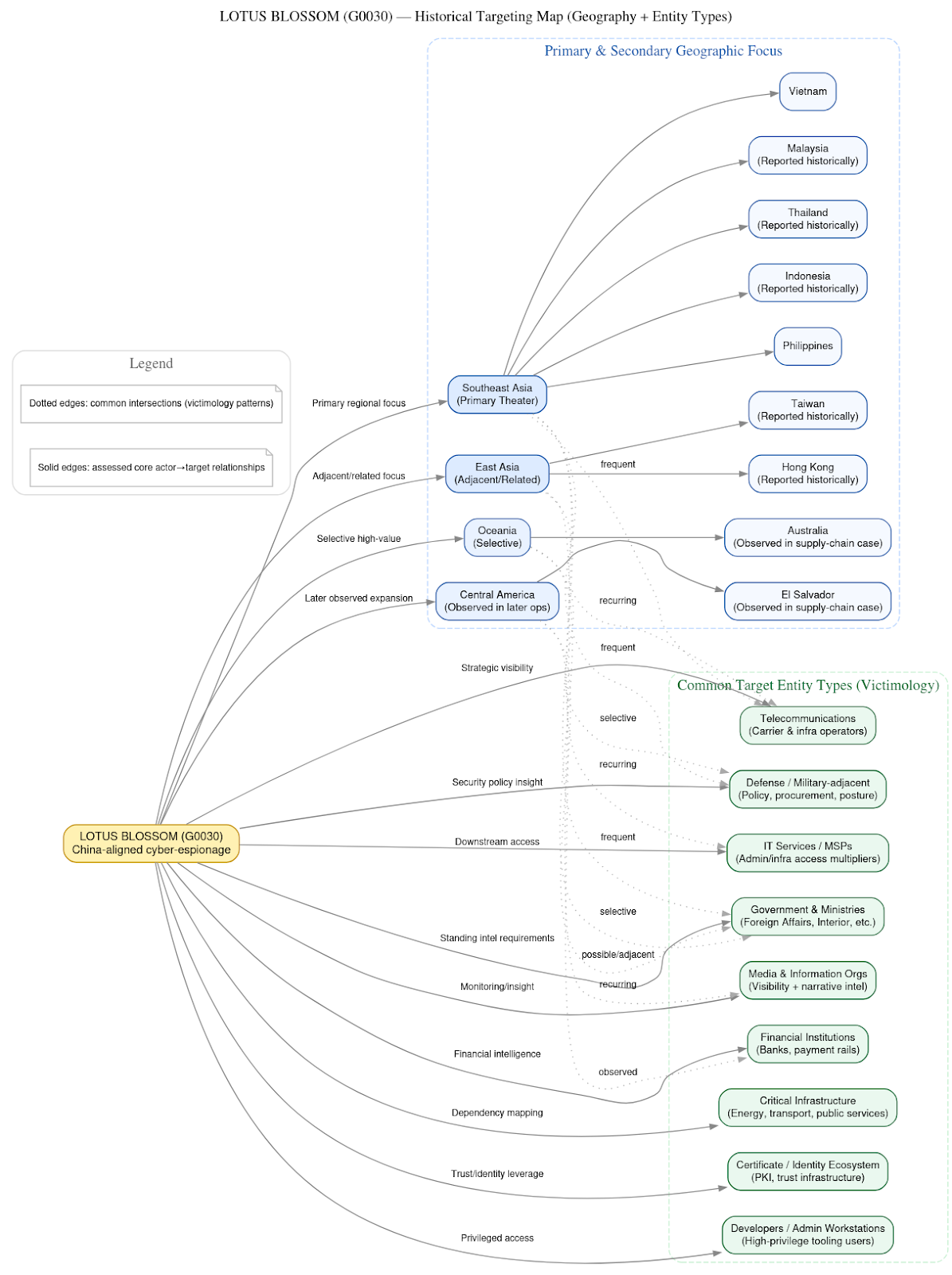
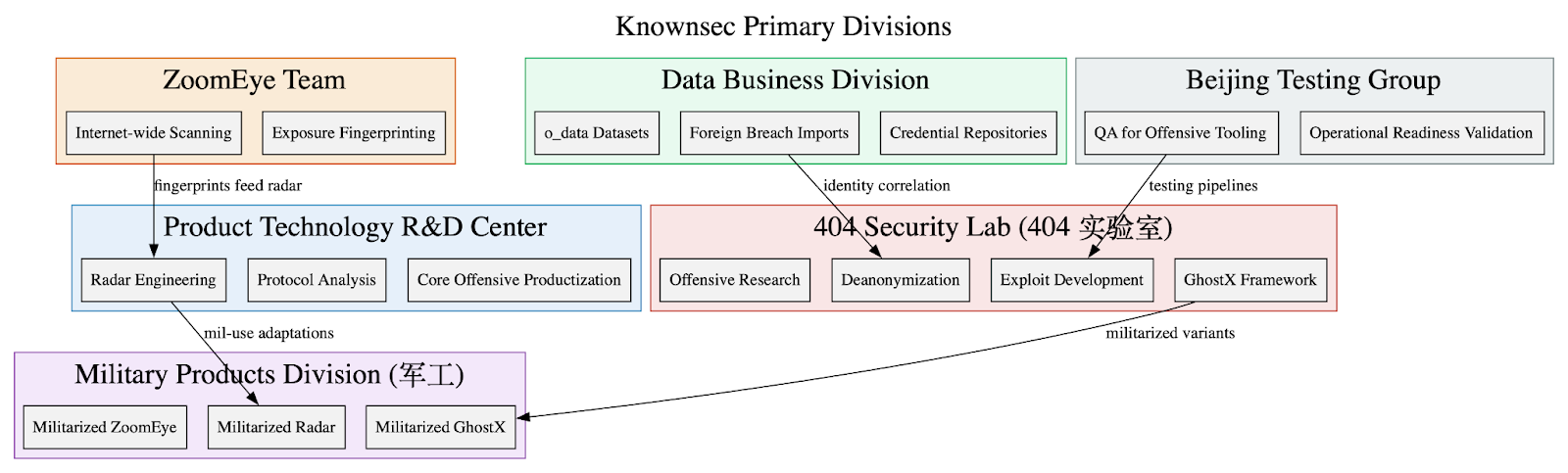
Our flagship research for November, “Inside the Great Firewall,” is a three-part series based on a recent dump of documents and technical details of China’s censorship infrastructure. This massive leak provided us with over 500 gigabytes of internal operational data. I had the pleasure of joining Dave Bittner on the Research Saturday podcast from N2K | CyberWire to discuss our team’s work.
In addition to this deep dive, we also published a threat intelligence report based on leaked internal documents from APT35 (Charming Kitten). This report maps the Iranian state-sponsored actor's organization, tool kit, and campaign strategies. It details their campaigns against Lebanon, Kuwait, Türkiye, Saudi Arabia, Korea, and domestic Iranian targets, with a focus on their use of Microsoft Exchange attack chains. As a former Exchange Admin, I took personal note of that detail and was glad those days were behind me!
Last but not least, my team and I attended CYBERWARCON in Arlington, Virginia a couple of weeks ago. It was great to connect with the community, we had a small sponsorship booth and had many excellent conversations with fellow practitioners. I personally like the timing of this one-day conference, as it’s a nice bookend to its sister conference SLEUTHCON, which we attended earlier this year.
November was packed with research and tasty threat intelligence, so let's dive right in and get you up to speed!
Hot off the Presses
Inside the Great Firewall Part 1: The Dump
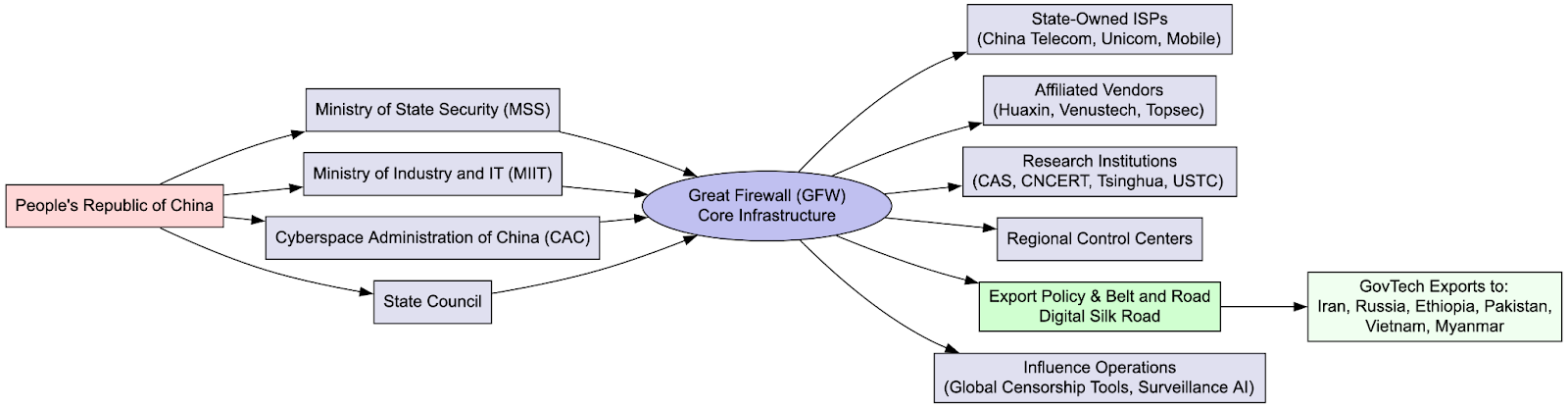
In September 2025, a historic breach of China’s censorship infrastructure leaked over 500 gigabytes of internal data detailing the infrastructure, design, and companies involved with the Great Firewall (GFW). DTI researchers analyzed more than 100,000 documents, internal source code, work logs, configuration files, emails, technical manuals, and operational runbooks.
Part 1 covers the human machinery behind the GFW and the consequences of the leak. This data links specific engineers and administrators to their roles across state-run ISPs (China Telecom, China Unicom, China Mobile), academic research institutions, and Ministry of State Security (MSS)-linked vendors.
Inside the Great Firewall Part 2: Technical Infrastructure
In Part 2, DTI analysts offer a forensic reconstruction of the Great Firewall’s technical infrastructure. From spreadsheets detailing app endpoint behavior, user monitoring intervals, and hardware configurations to blueprint files illustrating node relationships and control flows, the data illustrates a highly centralized yet distributed architecture, built on cooperation between state-run ISPs, telecom vendors, university research labs, and policy-design entities. Using this data, our researchers mapped the operational logic, software structure, and institutional alignment driving the digital surveillance regime.
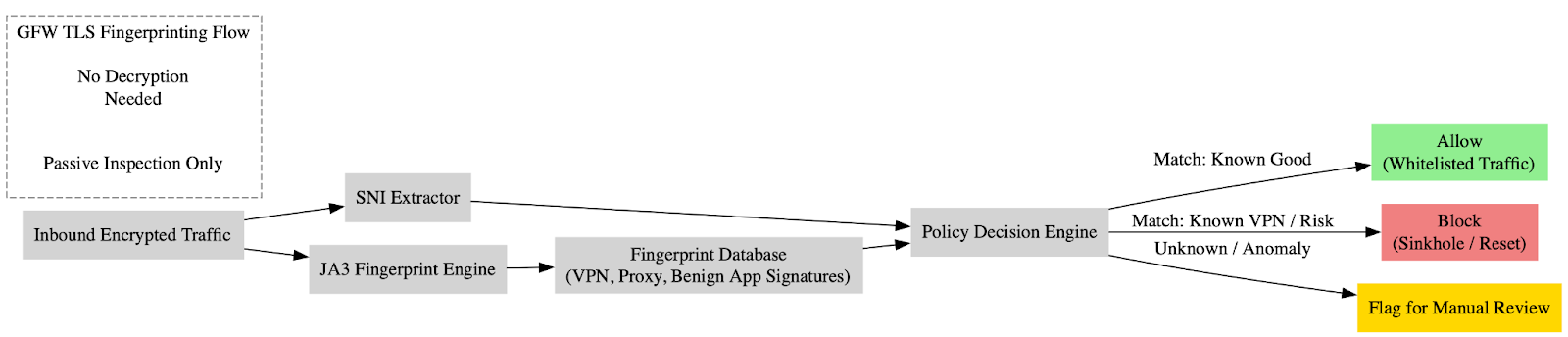
🔍Read the full technical deep dive here
Inside the Great Firewall Part 3: Geopolitical and Societal Ramifications
In the final part of the series, our team analyzes the strategic doctrine behind the Great Firewall. This analysis reveals the GFW as a cornerstone of China’s broader governance model, extending internal social control mechanisms into the digital realm while also projecting power abroad. The regime serves a dual purpose of insulating the domestic population from undesired narratives and foreign influence, while exporting technologies, protocols, and ideological models of digital sovereignty to other authoritarian or aspiring technocratic regimes.
Threat Intelligence Report: APT35 Internal Leak of Hacking Campaigns Against Lebanon, Kuwait, Turkey, Saudi Arabia, Korea, and Domestic Iranian Targets
In October, internal documents from APT35, also referred to as Charming Kitten, were leaked on Github. Our researchers reviewed and analyzed the leaked documents to form a tightly linked forensic trail that maps both technique and organization. In this report, we broke down APT35’s tool kit which covers reconnaissance, initial access, and post-exploitation tooling optimized for large-scale, quota-driven compromise operations. Our team analyzed the actor’s operational profile and campaign strategies, identifying an emphasis on weaponizing exchange attack chains (ProxyShell, Autodiscover, EWS enumeration, and PowerShell driven tasks) to extract mailbox contents and Global Address Lists, maintain mailbox-level persistence, HUMINT extraction, and iterative phishing loops based on harvested address books.

What We’re Reading
In case you’re behind on your cybersecurity reading homework, DTI team member Ian Campbell’s monthly recommended reading list will get you up to speed!
- The top article for the month: GreyNoise Intelligence – When Bulletproof Hosting Proves Bulletproof: The Stark Industries Shell Game
- The top research for the month: arXiv – Adversarial Poetry as a Universal Single-Turn Jailbreak Mechanism in Large Language Models
📚Checkout the full reading list here📚
Where We’ll Be
- SANS Cyber Threat Summit 2025, London, UK, 3-4 December
Final Thoughts
As always, thank you to my returning readers! If you’re new, I hope you found this newsletter informational, helpful, and worthy of sharing with your peers. And of course I hope you will be coming back to read future editions!
We share this newsletter via email as well - if you’d prefer to get it to your inbox, sign up here.
If you missed last month's content, here are some quick links:
- DomainTools Investigations BSides NoVa Recap
- Repo the Repo - NPM Phishing
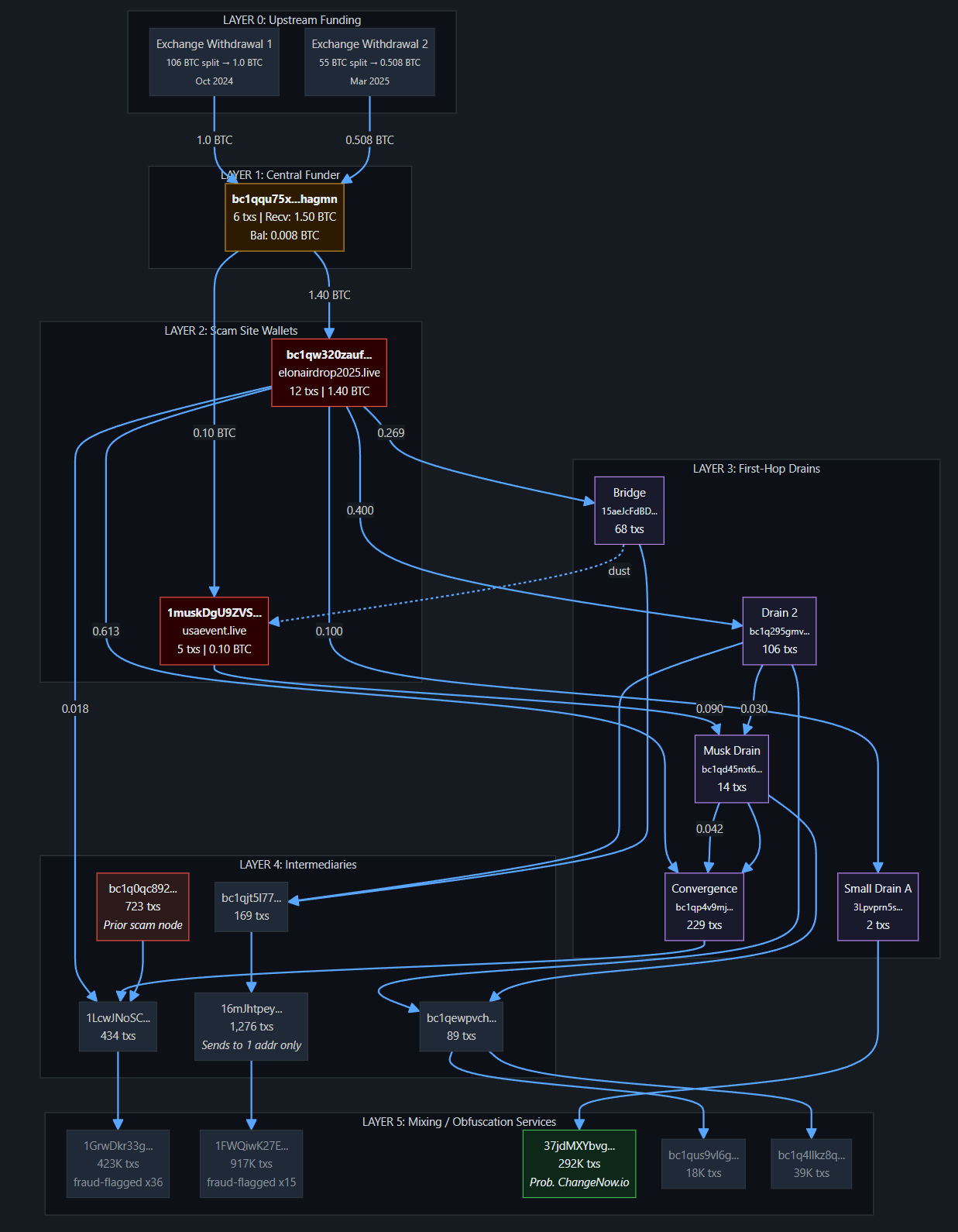
- Inside a Crypto Scam Nexus
- 18+ E-Crime
Thanks for reading - see you next month!
-Daniel
https://www.linkedin.com/in/schwalbe
https://infosec.exchange/@danonsecurity
https://www.linkedin.com/in/schwalbe
https://infosec.exchange/@danonsecurity