Can you believe August is almost over? Here in the Pacific Northwest, Summer is making its last stand. If the weather professionals are right, we will have another 10 days or so of temperatures in the low 80s (that’s high 20s in Celsius for my international readers), before Fall settles in. As every Seattleite knows, there is that one day in September, when the temperature drops suddenly, and the rain returns, and then it’s another 9 months before the best time of the year comes back. Not that we’re bitter or anything, those 3 months of summer are glorious and make all the rain worth it.
You know where it rarely rains though? Las Vegas! And that’s where the DTI team spent 8 days at the beginning of August for Hacker Summer Camp. Some people will argue that 8 days in Vegas is about 6.5 days too long. And the heat also did not disappoint, every day peaked north
of 105F, or 40+ in Celsius. But luckily, it’s a dry heat they say 🙄

Our brilliant Marketing team had a great solution to keep us out of the heat: We chartered several shuttle buses that drove back and forth between Black Hat and the hotel where the larger DomainTools contingent stayed. Great advertising and we got to ride in style!

My other van is the DNS express!
Even if you didn’t work for DomainTools, you could catch a free ride. All for the price of being a captive audience and having to watch our demo reel 😎:

Come take a ride in my windowless black van!
The team had a packed schedule, and lots of community events to support! The Diana Initiative, BSides Las Vegas, Sober in Cyber, Black Hat, DEF CON, as well as a handful of other community events and cons that I cannot name publicly - IYKYK.
At the end of the week, I had the pleasure to present at DEF CON 33 in the Recon Village. I talked about how to use passive DNS to enumerate subdomains and how to effectively identify deep wildcards:
At the end of the week, I had the pleasure to present at DEF CON 33 in the Recon Village. I talked about how to use passive DNS to enumerate subdomains and how to effectively identify deep wildcards:

Did I mention it was hot? Shorts and T-shirt to the rescue!

My colleagues Ian Campbell and Malachi Walker also presented at DEF CON, together in the Malware Village and Malachi gave a second talk in the BIC Village
While the days were long and hot, and the nights were short and fueled by energy drinks, we loved every minute of it. Hacker Summer Camp is where “our people” meet, and we wouldn't miss it for anything!
If you are a returning reader, welcome back! If you are a new reader, what you are about to read is news from our group of researchers and analysts, where they provide their expertise in investigating, mitigating, and preventing Domain and DNS based attacks.
So without further ado, here’s what our incredible team has been up to for the rest of August:
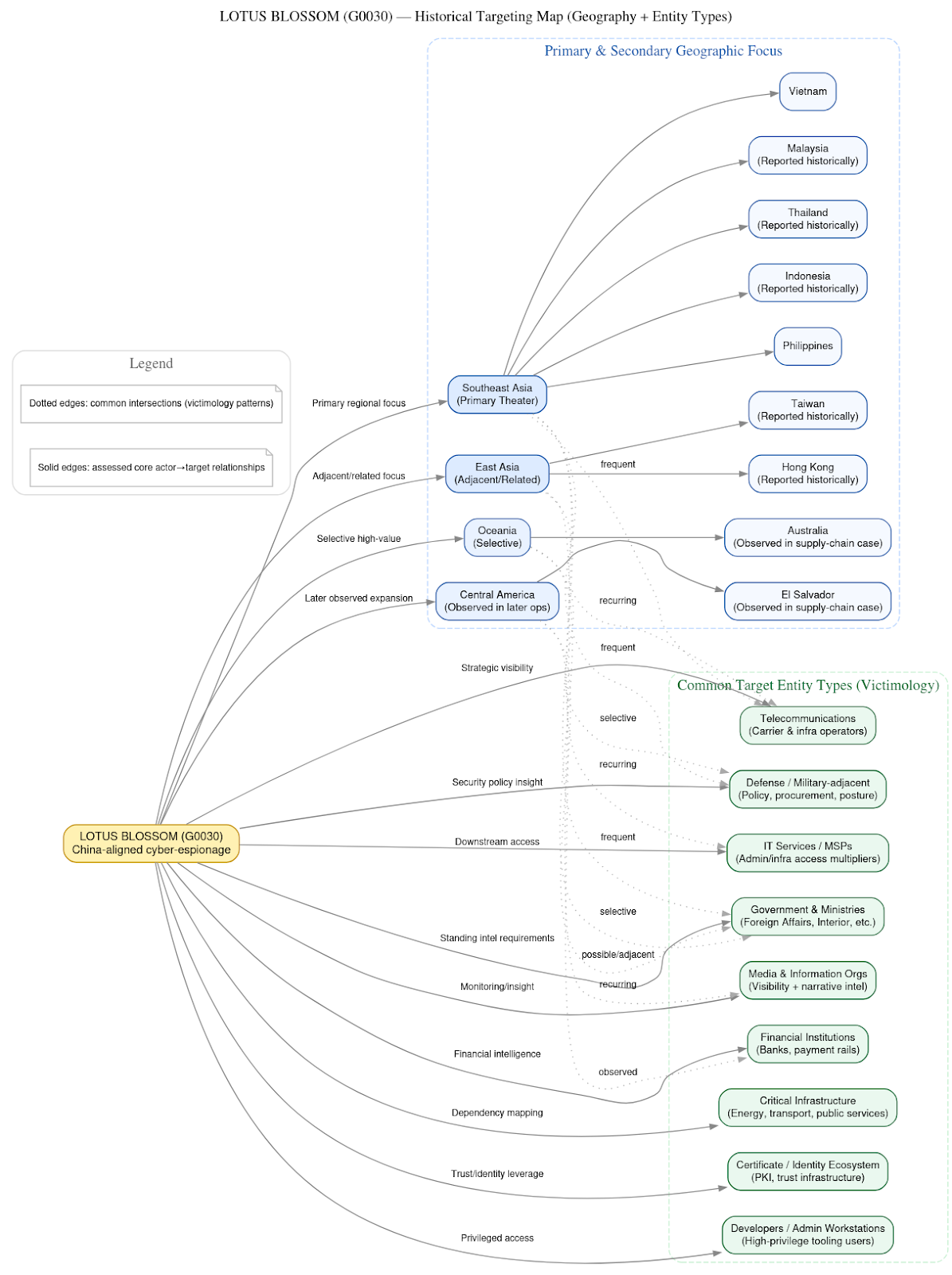
From Laptops to Laundromats: How DPRK IT Workers Infiltrated the Global Remote Economy
In this post we discuss how the Reconnaissance General Bureau (RGB) of the DPRK orchestrated an operation that used stolen or forged identities to secure tech jobs for their operatives for the purpose of gaining access to intellectual property, and to receive salaries in cryptocurrency.
The article covers key actors like Song Kum Hyok, an officer in the Andariel subgroup, to facilitators who run "laptop farms" to create the illusion that the workers are U.S.-based. The money laundering process is also detailed, showing how funds are routed through front companies and crypto brokers in various countries to convert the fraudulently obtained wages into usable capital for North Korea's strategic programs, including weapons development.

Crypto transfers and money laundering
https://dti.domaintools.com/from-laptops-to-laundromats-how-dprk-it-workers-infiltrated-the-global-remote-economy/?utm_source=LinkedIn&utm_medium=Social&utm_campaign=DTI-Newsletter-August
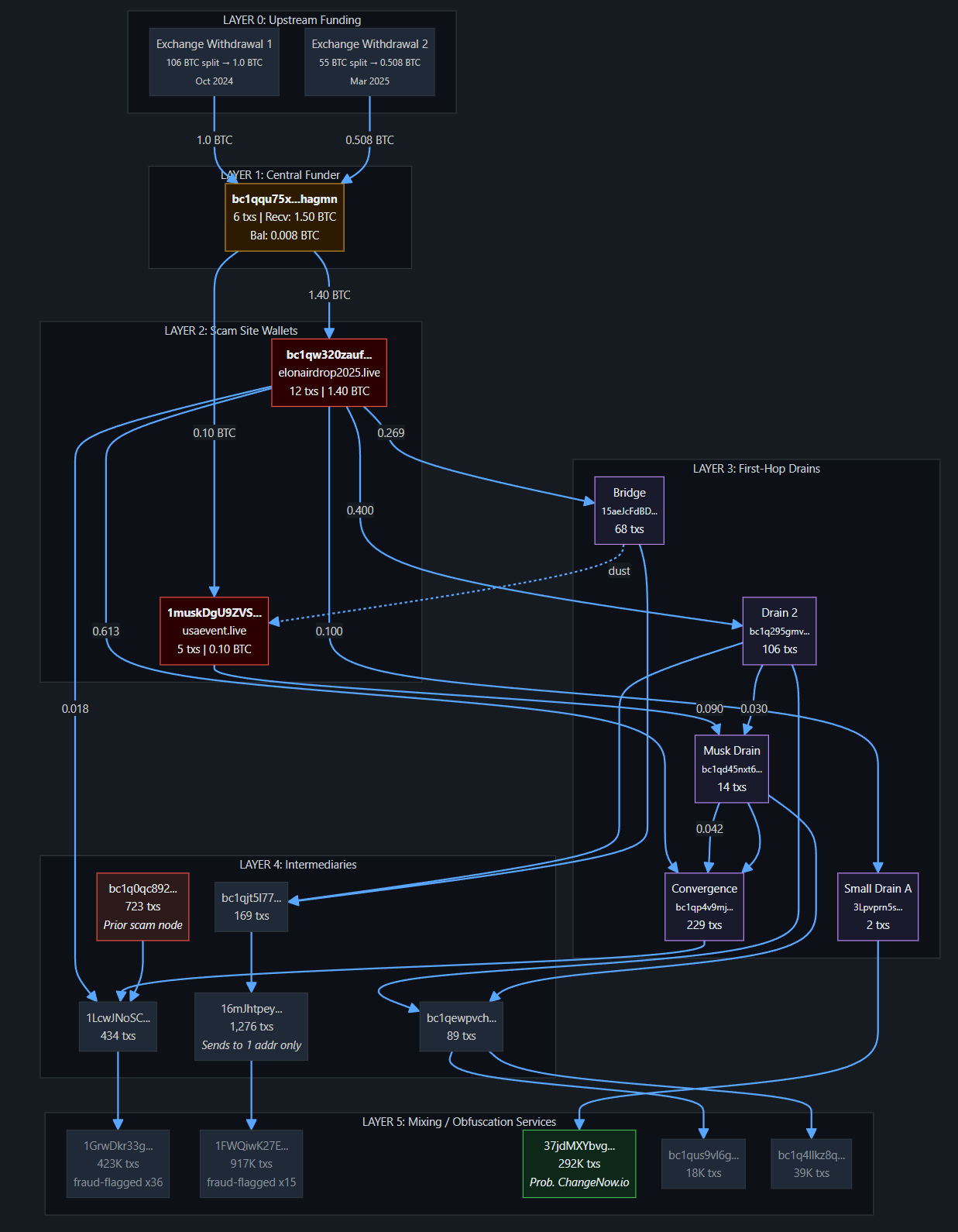
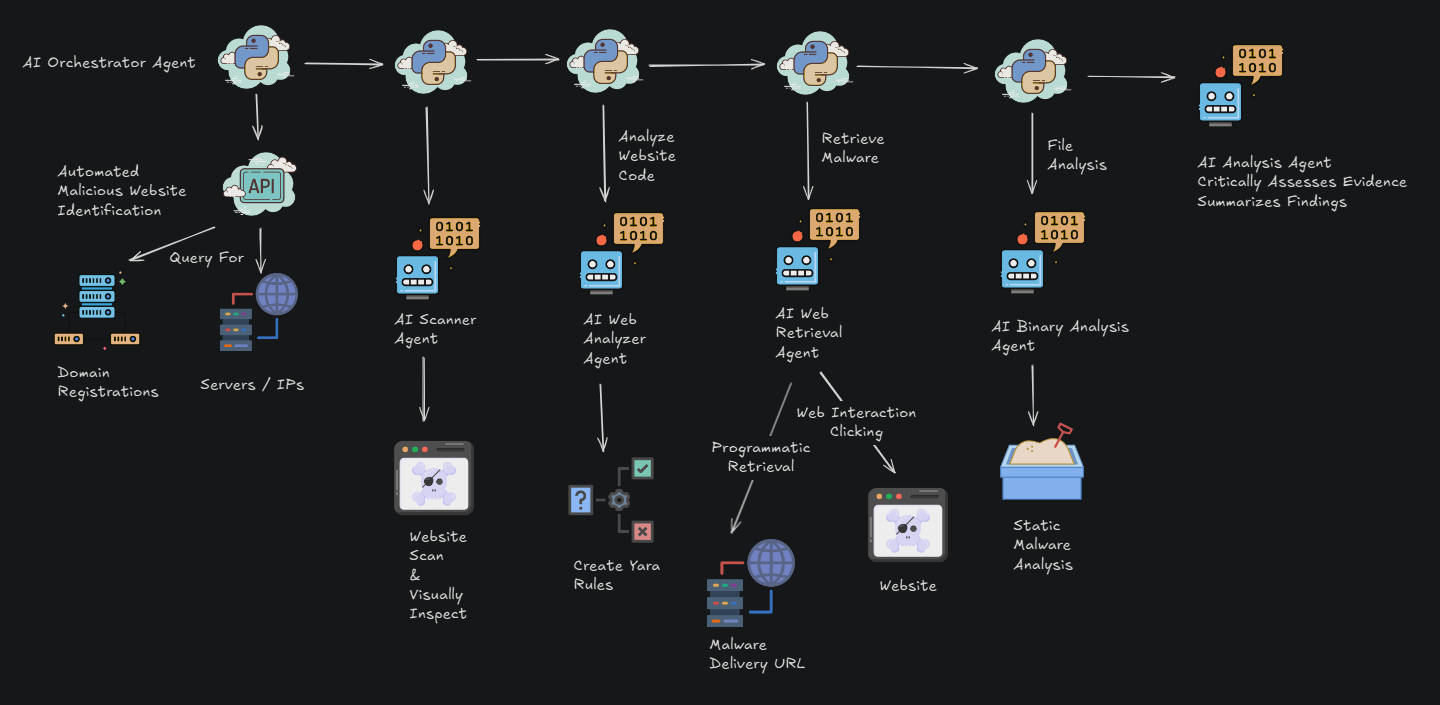
Hunting for Malware Networks
For this investigation, we took a look at recently active malware-as-a-service (MaaS) operations. We analyzed their use of web-hosted PowerShell scripts as an effective initial-stage payload delivery mechanism. This technique serves to compartmentalize the attack chain, reducing the exposure of core command and control (C2) infrastructure and complicating forensic investigations.
One example detailed in this article centers around a script that connects to a commonly used C2 domain, and was observed distributing over 60 different malicious files in the past 2 months. It included multiple stealer malware families such as Amadey, Lumma, Luca, DeerStealer, and RedLine as well as other malware families like Rugmi, BlackBasta and DarkGate.
The investigation into the broader infrastructure revealed a significant concentration of malicious activity originating from a small number of IP addresses, all associated with the same ASN. It seems likely that this ASN is part of a bulletproof hosting operation.
Additionally, threat actors appear to increasingly be leveraging legitimate distributed services like Amazon CloudFront and GitHub to host and deliver malware. This makes proactive network-based blocking more difficult.
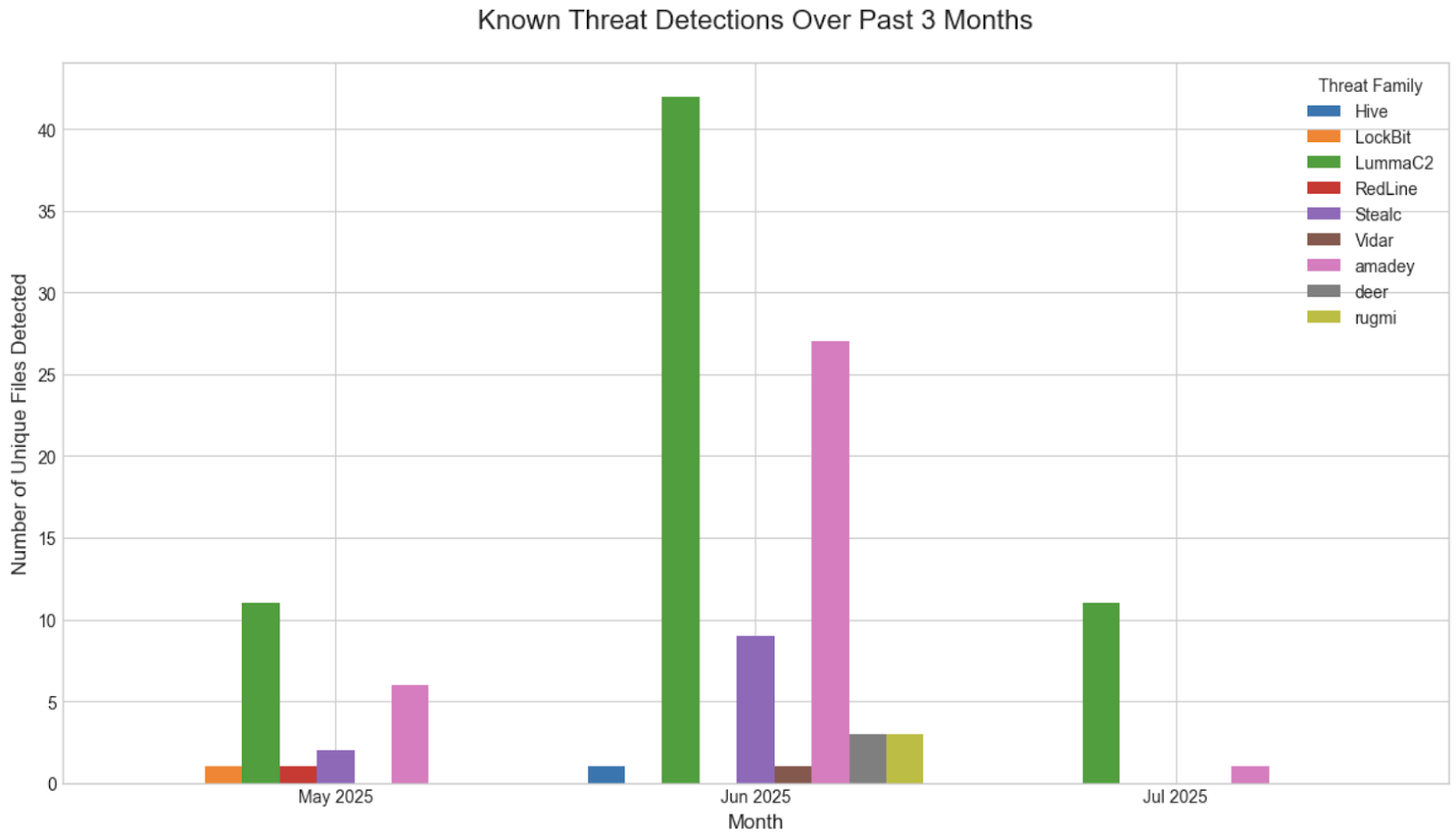
Analysis of 200 binaries in VirusTotal over the past 3 months show that there appears to be an overrepresentative share of LummaC2 and Amadey.
SpyNote Malware Part 2
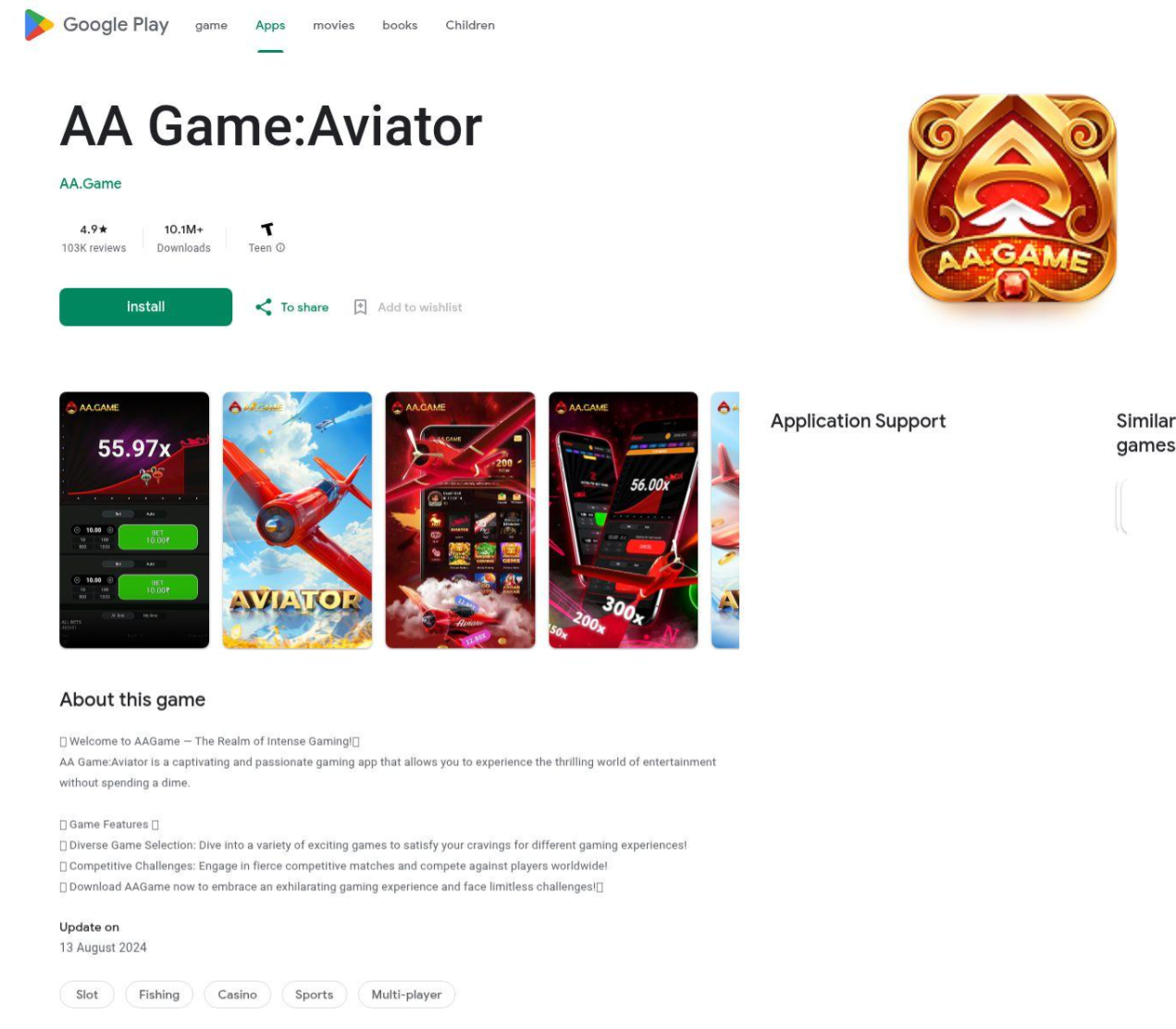
The SpyNote malware campaign has resurfaced, and the threat actors are employing deceptive websites that mimic the Google Play Store to trick users into downloading an Android RAT (Remote Access Trojan).
SpyNote is designed for surveillance, data exfiltration, and remote control of a victim's device. Its capabilities include keylogging, stealing 2FA codes, capturing audio and video, and remotely wiping data. This new campaign incorporates minor changes in the actor's tactics, such as slight IP resolution changes and the addition of anti-analysis techniques in the APK dropper to protect the payload from detection.
The malicious websites use JavaScript to initiate the download of a dropper APK. This dropper conceals its functions using DEX Element Injection and decrypts a second-stage SpyNote payload. The payload then loads the command-and-control (C2) logic from a separate file, using obfuscation to hinder static analysis.
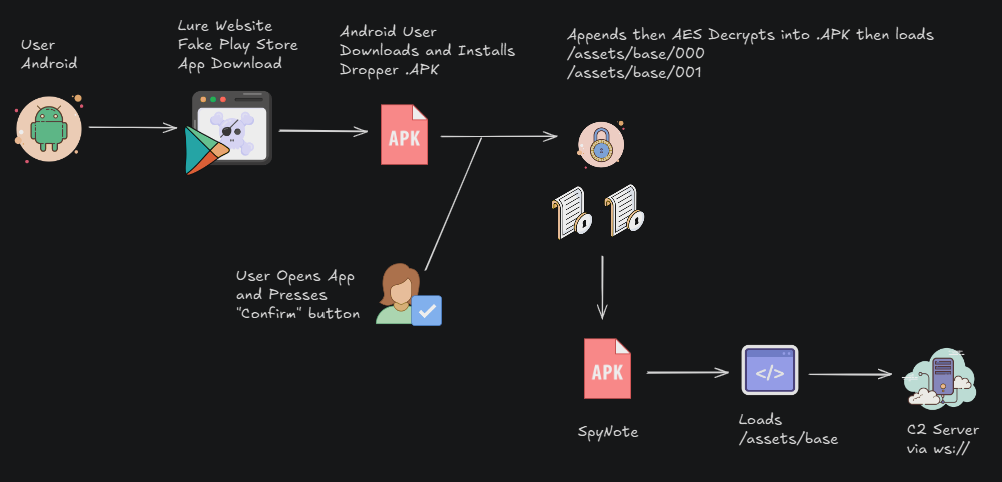
Malware execution flowchart
Cybersecurity Reading List - Week of 2025-08-25
In this latest installment of his reading list, my colleague Ian Campbell highlights a recent influx of new research and publications in the cybersecurity field. As always, he covers several different types of media, something for everybody:
- Podcasts: "Adversary Universe from Crowdstrike" for a perspective on AI, "CyberWire Research Saturday" for a deep dive into the VexTrio cybercriminal group, and "Prompt||GTFO" for demonstrations on how practitioners are using AI.
- Articles: An interview with a Kaseya hacker, and a piece on data exfiltration via DNS.
- Research Papers and Reports: Greynoise Intelligence study on how attack spikes can precede new CVEs, a RecordedFuture report on cloud threat hunting, and a CAIDA paper on early-stage traffic discovery.
- Tools and Resources: Learn about CISA's new open-source malware analysis platform, Thorium
- Entertaining Reading: "The Berners Street Hoax"
Customer Webinar: Exclusive Recap of the DTI Team DEF CON 33 Talks
For those who couldn't make it to Las Vegas, we're bringing these talks directly to you.
Here's what we'll cover:
- Malware in DNS: A look at how attackers hide malicious code in DNS TXT records.
- Pre-Identifying DNS Wildcards: Learn new techniques for subdomain enumeration and attack surface management.
- DNS Scavenger Hunt: An interactive session where you can put your skills to the test.
Webinar Details:
- Date: Tuesday, September 30th
- Time: 10:00 AM PT / 1:00 PM ET
- Duration: 1.5 hours
Where We’ll Be
- Underground Economy, France, 1-4 September
- Back to Las Vegas for private event, September 8-12
- If you find yourself in the area that week, let us know and we’d be happy to meet up over a refreshing beverage
- DC Closed Door Session, National Harbor, MD, 17 September
- TLP:RED research, please note “DFS Newsletter” in the “Referred By” section: https://dti.domaintools.com/request-an-invite/
- Intelligence & National Security Summit, National Harbor, MD, 18-19 September
- LABScon, Scottsdale, AZ, 17-20 September
Final Thoughts
As always, thank you to my returning readers! If you’re new, I hope you found this newsletter informational, helpful, and worthy of sharing with your peers. And of course I hope you will keep coming back to read future editions!
We share this newsletter via email as well - if you’d prefer to get it to your inbox, sign up here.
If you missed last month's content, here are some quick links:
- Malware in DNS: A Covert Delivery Mechanism
- Chinese Malware Delivery Domains: Part III - The "SilverFox" Campaign
- Where Everybody Knows Your Name: Observing Malice-Complicit Nameservers
- Iran's Intelligence Group 13: A Profile of a Covert Cyber Strike Unit
Thanks for reading - see you next month!
Daniel