On 18 November 2024, BlackBerry’s threat research team reported on a cyber espionage campaign targeting the Pakistan Navy. This campaign used malicious documents to collect credentials and distribute malware. While BlackBerry did not attribute this activity to a specific actor, subsequent analysis by DomainTools revealed significant overlaps in tactics, techniques, procedures (TTPs), and targeting scope with the cyber-espionage group known as SloppyLemming.
Review of BlackBerry Report
Recent activity from this campaign involved the deployment of a malicious PDF document in early September 2024. The document resembles an internal IT memo, instructing recipients on integrating Axigen Thunderbird for secure email communications. The document contained a link to a malicious website (paknavy.rf[.]gd) mimicking the legitimate Pakistan Navy domain.
Upon visiting the fraudulent site, users were prompted to download a ZIP file, “Axigen_Thunderbird.zip,” which included a malicious Thunderbird extension. Once installed, the extension requested credentials for “@paknavy.gov.pk” email addresses. Entered credentials were transmitted to an actor-controlled domain (updateschedulers[.]com), and the extension downloaded a malware payload hosted on the same domain. BlackBerry researchers identified the malware as a variant of Sync-Scheduler. Public reporting from March 2024 first identified this malware family and its use of the domain packageupdates[.]net for command and control (C2). BlackBerry also identified related activity in the May/June 2024 time frame using the C2 domain extension.webmailmigration[.]com.
Further analysis by DomainTools uncovered an additional likely associated domain: diplomaticservices[.]link. Whois data from this domain shows a registrant organization of “National Telecom Corporation” likely referencing the Pakistani government’s telecommunications provider. The only other domain using this registrant organization since 2010 is the webmailmigration[.]com domain from the BlackBerry report.
Overlap with SloppyLemming Actor
In September 2024, Cloudflare’s threat research team reported on an India-nexus cyber espionage actor it dubbed SloppyLemming (aka OUTRIDER TIGER). This actor primarily targets Pakistan, with a focus on government and defense. SloppyLemming frequently leverages its custom CloudPhish credential logging tool on Cloudflare Worker domains to compromise email credentials from targeted individuals. One of the mail clients CloudPhish specifically targeted was Axigen, which was the mail client referenced in the malicious activity covered in the BlackBerry report. SloppyLemming also employed PDF documents for credential collection and malware delivery.
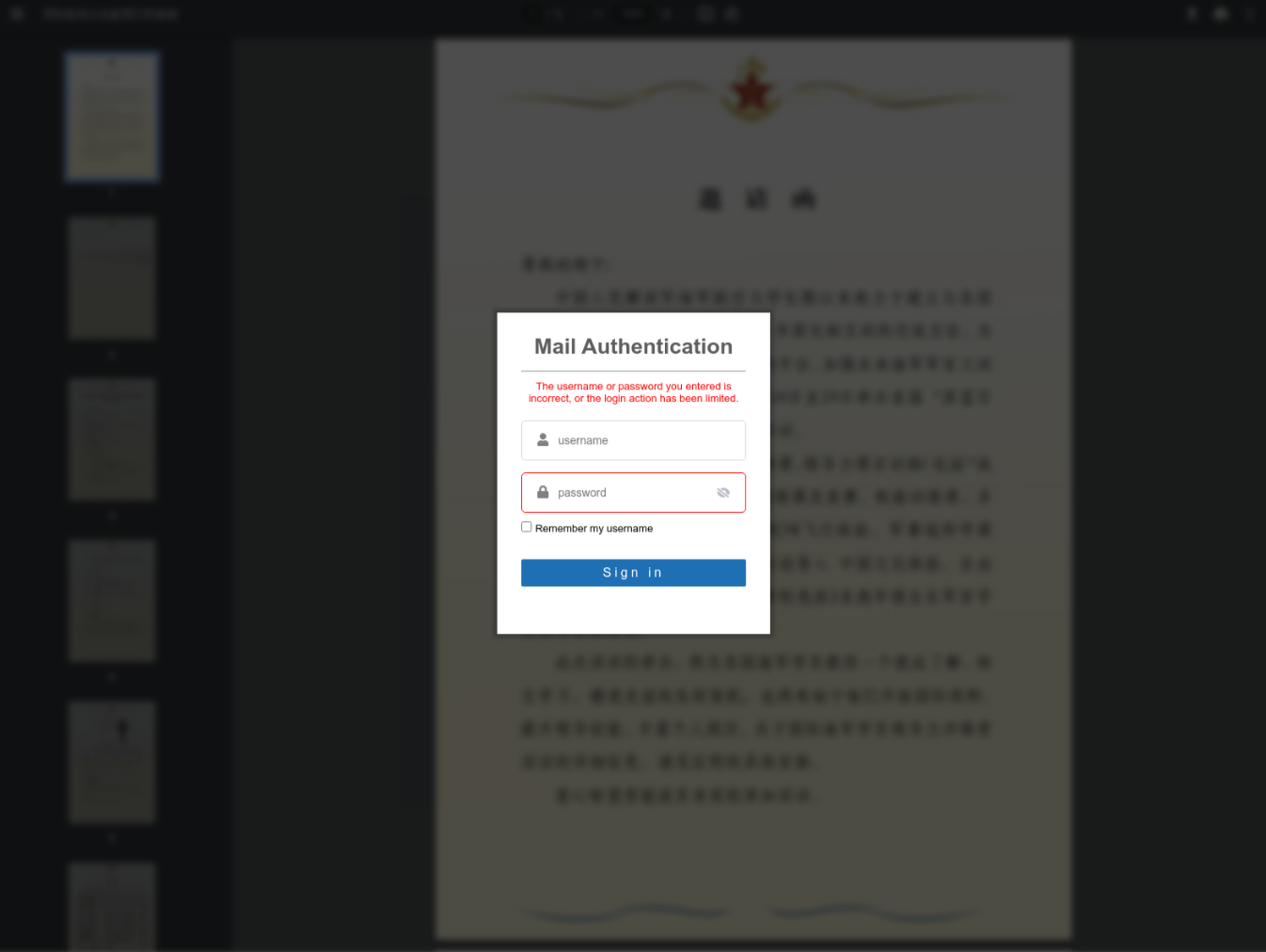
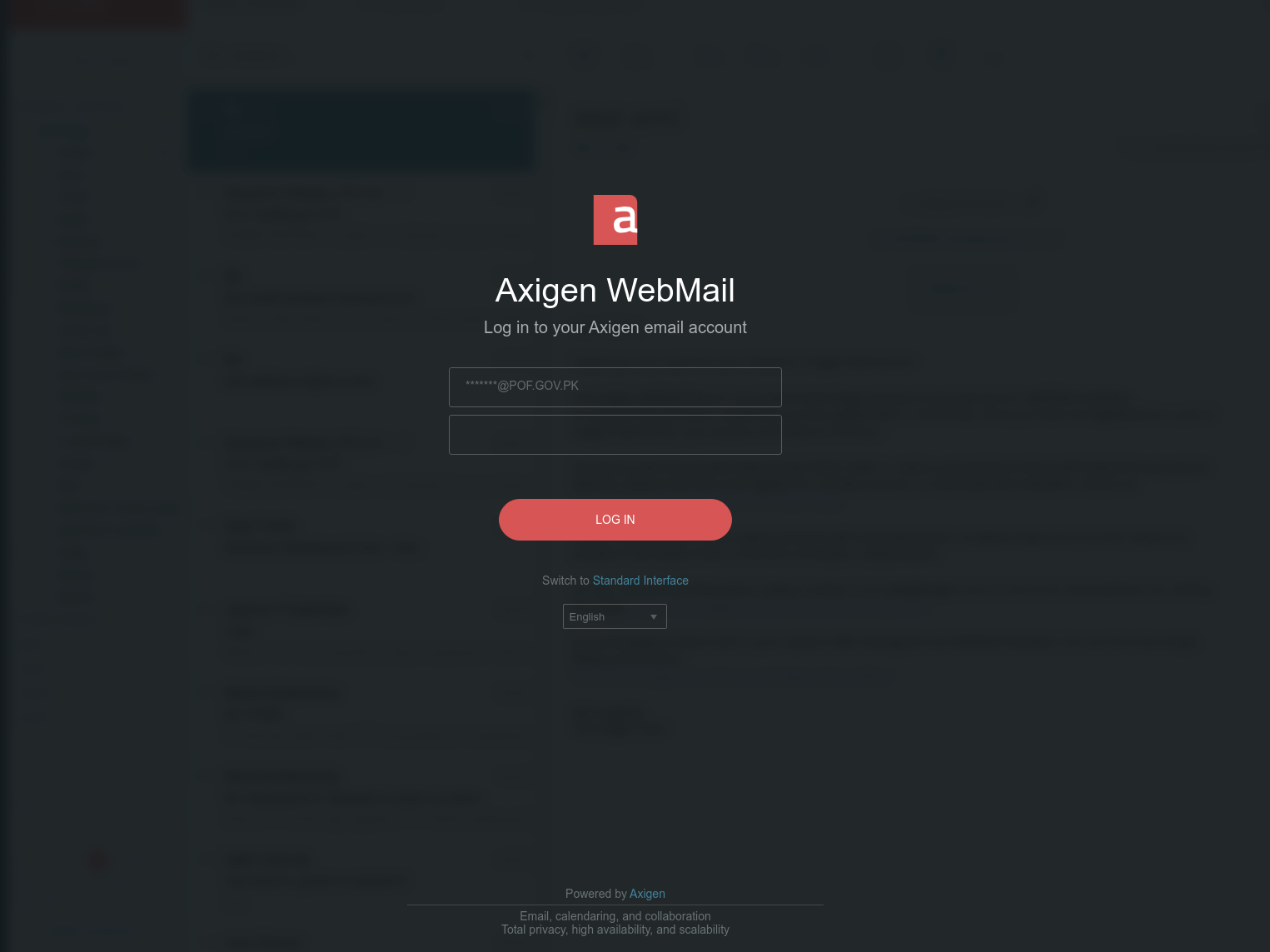
Data from the urlscan.io scanning service shows an Axigen webmail credential phishing page present on www.login.webmailmigration[.]com in April 2024. Similar Axigen phishing pages present on the following domains between February and July 2024:
- mail-pakchinainvest-com.niancao010.workers[.]dev
- webmail.cybar-net-pk.workers[.]dev
- mail.pof-gov-pk.workers[.]dev
These domains use a similar domain naming convention to that detailed in the SloppyLemming report.
Figure 1. Screenshot of credential phishing pages present on www.login.webmailmigration[.]com in April 2024 (left) and mail.pof-gov-pk.workers[.]dev in August 2024 (right)
Additional similarities between the recent BlackBerry and Cloudflare’s reports include the actor’s use of malicious PDFs malware delivery and a Pakistan-centric target scope.
Conclusion
It is likely that SloppyLemming is the actor responsible for the malicious activity described in BlackBerry’s recent report. This assessment is made with low confidence based on similar credential phishing and malware delivery TTPs, as well a Pakistan-focused target scope. However, it is plausible that the BlackBerry report discusses a separate actor from SloppyLemming that is employing similar TTPs.
IOCs
paknavy[.]rf[.]gd
updateschedulers[.]com
packageupdates[.]net
finance-gov-pk[.]rf[.]gd
extension[.]webmailmigration[.]com
diplomaticservices[.]link