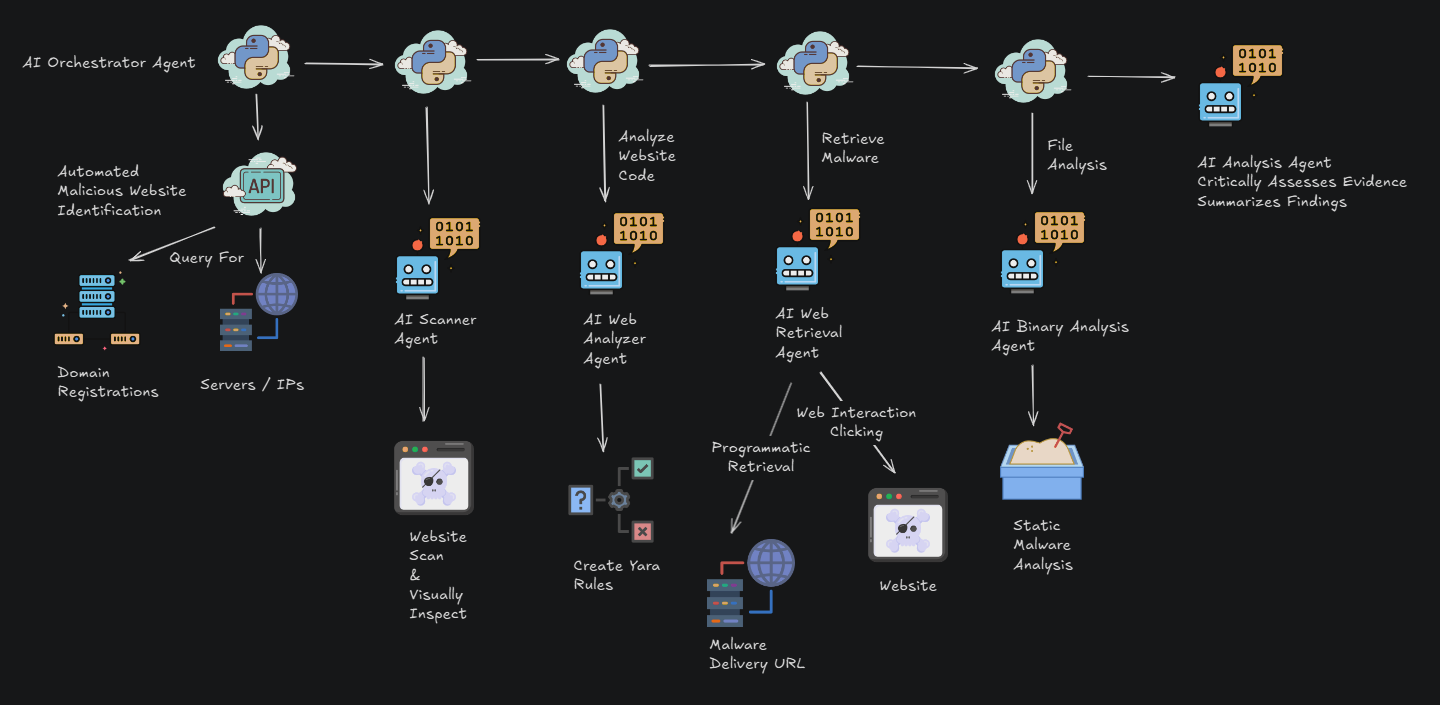
Credential Phishing Pages Mimicking Legitimate Webmail Login Portals
Since 1 August 2024, a likely India-nexus targeted intrusion actor has targeted entities in China and South Asia using credential phishing pages mimicking legitimate webmail login portals. Domain naming conventions as well as observed phishing pages reveal likely targeting of entities in the government and defense sectors. Observed tactics, techniques, and procedures and target scope are consistent with public reporting on Indian targeted intrusion actors.
Details
Identified domains share the following similarities:
- Registration via 1api registrar service
- Use of Royalhost nameservers
- Resolving to the IP address 65.21.85[.]206
- Domain naming convention using webmail login or file download themes often combined with references to specific, likely targeted entities
The 65.21.85[.]206 IP address is a shared host resolving numerous domains likely unrelated to the India-nexus targeted intrusion activity. However, historical data from this host indicates the India-nexus actor has used 65.21.85[.]206 since at least April 2024 to host phishing domains.

Figure 1. Example Credential Phishing Page from nepal-mofa[.]com
Analysis of this activity also shows one of the actor-registered domains (never-giveup.mail-downloadfiles[.]com) redirecting to a credential phishing page hosted on the cloud service Netlify (large-files-d0wnl0ad-session-expired.netlify[.]app). These domains are likely being used to target Chinese entities.

Figure 2. Chinese-language Credential Phishing Page Hosted on Netlify
IOCs
Conclusion
This activity is consistent with targeted intrusion activity identified in previous public reporting. Naming conventions are generally consistent with activity from the group known as Sidewinder with domains spoofing webmail login portals and the targeting of entities in China and South Asia. The India-nexus targeted intrusion group known as Patchwork also historically exhibited a similar target scope.
Related Content
APT35/Charming Kitten's leaked documents expose the financial machinery behind state-sponsored hacking. Learn how bureaucracy, crypto micro-payments, and administrative ledgers sustain Iranian cyber operations and link them to Moses Staff.