Newsletter 11 Could Take Forever
The title of this month’s newsletter is a deep cut taken from the height of my favorite music genre, the admittedly awkwardly titled “Alternative Music.” What can I say, the 1990s in Seattle were wild, man - you had to be there.
Speaking of being there, last week was the Thanksgiving Holiday here in the United States. Normally my newsletter goes out on the last Tuesday of the month, but considering a lot of security professionals in the US got Thursday and likely Friday off, we decided to push publication by a week, so hopefully more of you can enjoy this edition instead of it getting buried under mashed potatoes and gravy!
The weather here in the Pacific NorthWest has firmly settled into “damp mode” (IYKYK), and the temperatures have started to creep below 40 degrees Fahrenheit (below 4 degrees Celsius for my international friends). I refuse to call it “The Big Dark” however - stop trying to make “The Big Dark” happen, Gretchen! Despite the cold, I’m happy to report that the intensity of DomainTools Investigations’ research output is only heating up.
Our flagship research for November, “Inside the Great Firewall,” is a three-part series based on a recent dump of documents and technical details of China’s censorship infrastructure. This massive leak provided us with over 500 gigabytes of internal operational data. I had the pleasure of joining Dave Bittner on the Research Saturday podcast from N2K | CyberWire to discuss our team’s work.
In addition to this deep dive, we also published a threat intelligence report based on leaked internal documents from APT35 (Charming Kitten). This report maps the Iranian state-sponsored actor's organization, tool kit, and campaign strategies. It details their campaigns against Lebanon, Kuwait, Türkiye, Saudi Arabia, Korea, and domestic Iranian targets, with a focus on their use of Microsoft Exchange attack chains. As a former Exchange Admin, I took personal note of that detail and was glad those days were behind me!
Last but not least, my team and I attended CYBERWARCON in Arlington, Virginia a couple of weeks ago. It was great to connect with the community, we had a small sponsorship booth and had many excellent conversations with fellow practitioners. I personally like the timing of this one-day conference, as it’s a nice bookend to its sister conference SLEUTHCON, which we attended earlier this year.
November was packed with research and tasty threat intelligence, so let's dive right in and get you up to speed!
Hot off the Presses
Inside the Great Firewall Part 1: The Dump
In September 2025, a historic breach of China’s censorship infrastructure leaked over 500 gigabytes of internal data detailing the infrastructure, design, and companies involved with the Great Firewall (GFW). DTI researchers analyzed more than 100,000 documents, internal source code, work logs, configuration files, emails, technical manuals, and operational runbooks.
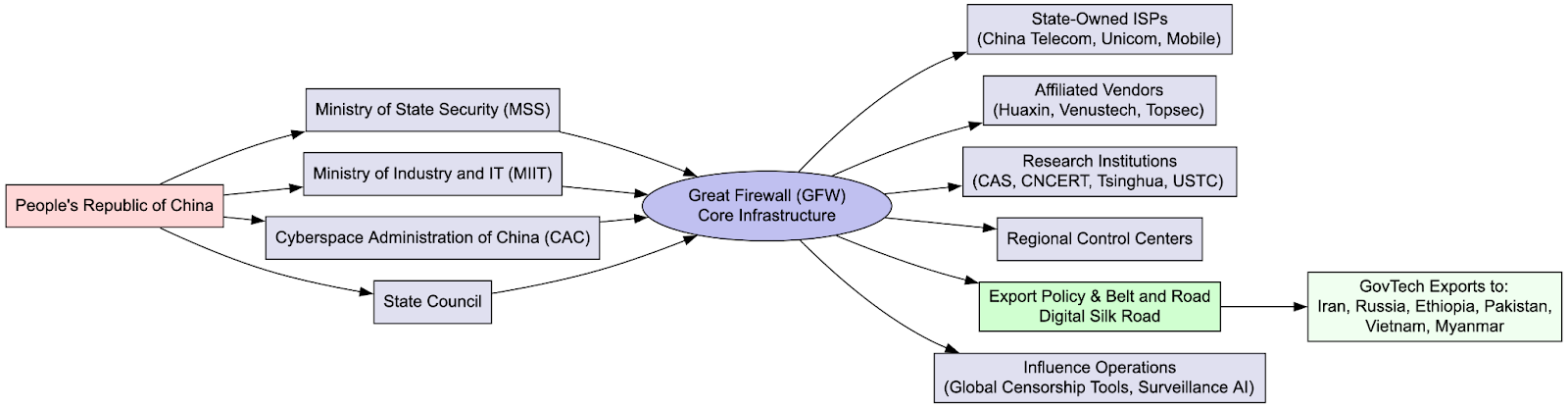
Part 1 covers the human machinery behind the GFW and the consequences of the leak. This data links specific engineers and administrators to their roles across state-run ISPs (China Telecom, China Unicom, China Mobile), academic research institutions, and Ministry of State Security (MSS)-linked vendors.
Inside the Great Firewall Part 2: Technical Infrastructure
In Part 2, DTI analysts offer a forensic reconstruction of the Great Firewall’s technical infrastructure. From spreadsheets detailing app endpoint behavior, user monitoring intervals, and hardware configurations to blueprint files illustrating node relationships and control flows, the data illustrates a highly centralized yet distributed architecture, built on cooperation between state-run ISPs, telecom vendors, university research labs, and policy-design entities. Using this data, our researchers mapped the operational logic, software structure, and institutional alignment driving the digital surveillance regime.
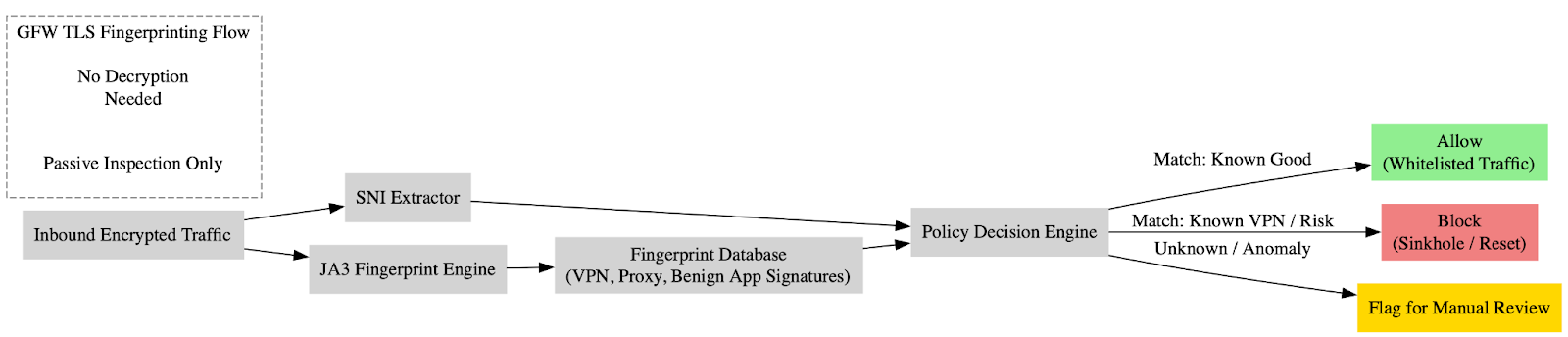
🔍Read the full technical deep dive here
Inside the Great Firewall Part 3: Geopolitical and Societal Ramifications
In the final part of the series, our team analyzes the strategic doctrine behind the Great Firewall. This analysis reveals the GFW as a cornerstone of China’s broader governance model, extending internal social control mechanisms into the digital realm while also projecting power abroad. The regime serves a dual purpose of insulating the domestic population from undesired narratives and foreign influence, while exporting technologies, protocols, and ideological models of digital sovereignty to other authoritarian or aspiring technocratic regimes.
Threat Intelligence Report: APT35 Internal Leak of Hacking Campaigns Against Lebanon, Kuwait, Turkey, Saudi Arabia, Korea, and Domestic Iranian Targets
In October, internal documents from APT35, also referred to as Charming Kitten, were leaked on Github. Our researchers reviewed and analyzed the leaked documents to form a tightly linked forensic trail that maps both technique and organization. In this report, we broke down APT35’s tool kit which covers reconnaissance, initial access, and post-exploitation tooling optimized for large-scale, quota-driven compromise operations. Our team analyzed the actor’s operational profile and campaign strategies, identifying an emphasis on weaponizing exchange attack chains (ProxyShell, Autodiscover, EWS enumeration, and PowerShell driven tasks) to extract mailbox contents and Global Address Lists, maintain mailbox-level persistence, HUMINT extraction, and iterative phishing loops based on harvested address books.

What We’re Reading
In case you’re behind on your cybersecurity reading homework, DTI team member Ian Campbell’s monthly recommended reading list will get you up to speed!
- The top article for the month: GreyNoise Intelligence – When Bulletproof Hosting Proves Bulletproof: The Stark Industries Shell Game
- The top research for the month: arXiv – Adversarial Poetry as a Universal Single-Turn Jailbreak Mechanism in Large Language Models
📚Checkout the full reading list here📚
Where We’ll Be
- SANS Cyber Threat Summit 2025, London, UK, 3-4 December
Final Thoughts
As always, thank you to my returning readers! If you’re new, I hope you found this newsletter informational, helpful, and worthy of sharing with your peers. And of course I hope you will be coming back to read future editions!
We share this newsletter via email as well - if you’d prefer to get it to your inbox, sign up here.
If you missed last month's content, here are some quick links:
- DomainTools Investigations BSides NoVa Recap
- Repo the Repo - NPM Phishing
- Inside a Crypto Scam Nexus
- 18+ E-Crime
Thanks for reading - see you next month!
-Daniel
https://www.linkedin.com/in/schwalbe
https://infosec.exchange/@danonsecurity
https://www.linkedin.com/in/schwalbe
https://infosec.exchange/@danonsecurity
Related Content
DomainTools Investigations kicks off 2026 with deep dives into the KnownSec leak exposing China's cyberespionage ecosystem, predatory online gambling apps, and a phishing campaign weaponizing fake job interviews.
A new year, a new cover image! We recently went through another rebranding exercise, which brought new collateral templates. Most noticeably, it changed our corporate website. Some of you noticed, and let us know exactly how you felt about it! The DomainTools Investigations site (https://dti.domaintools.com) also got a make-over, and I think the main website compliments our DTI site nicely!
Regular readers will notice that once again the newsletter is a week “late” - but once again, there were good reasons for it. So I’m considering releasing it on the first Tuesday of the Month, instead of the last one. If you feel strongly one way or the other, please let me know in the comments (or email me). The use of song titles with numbers that correspond to the current edition for the newsletter title is sticking around for now. My friend @Kali Fencl started that when she helped me launch this newsletter over a year ago, and while it’s getting more difficult, I’m committed.
Another thing that’s probably staying are mentions of the local weather! Returning readers know I live in Seattle, and the weather here is always a topic of conversation! For example, many of you think the rain never stops in Seattle. Movies depict torrential downpours, but we Seattleites don’t mind: Keep believing that. But in reality, fellow PNW-er Scott Losse explains it best. Check him out and follow him, he’s funny!
Unlike the East Coast (sorry friends!), we just had a brief, miraculous week of mild weather and sunshine. But as it is customary, "The Gray" has returned like clockwork. It’s that part of winter here, where blue sky quickly begins to feel like a distant memory, and dampness is king. Don’t worry, only three to four months of that!
Speaking of winter, while most of the world was recovering from New Year's Eve and shovelling their driveways, my team here at DomainTools Investigations was busy dissecting a fresh mountain of data. If you thought the i-Soon leak from a while back was a one-off, think again. We’ve been heads-down on the KnownSec leak, a fascinating look at one of the supposed "white hat" companies that turned out to be part of the backbone of China’s cyberespionage ecosystem.
Beyond the geopolitical chess match, we’re also tracking some more "down-to-earth" (read: predatory) threats. Our analysts have been playing a high-stakes game of whack-a-mole with a series of dubious online gambling apps that are currently targeting users across the globe with some surprisingly sophisticated evasion tactics.
And for those of you who appreciate a shorter read with your morning coffee, we have a new SecuritySnack focused on "Phishing Interviews." This investigation highlights a particularly cold-hearted campaign that weaponizes the job hunt, exploiting the trust of applicants to harvest government credentials and to drop remote access tools.
We’ve got a lot to cover to kick off the year, so let’s dive right in, and get you all caught up!
Hot off the Presses
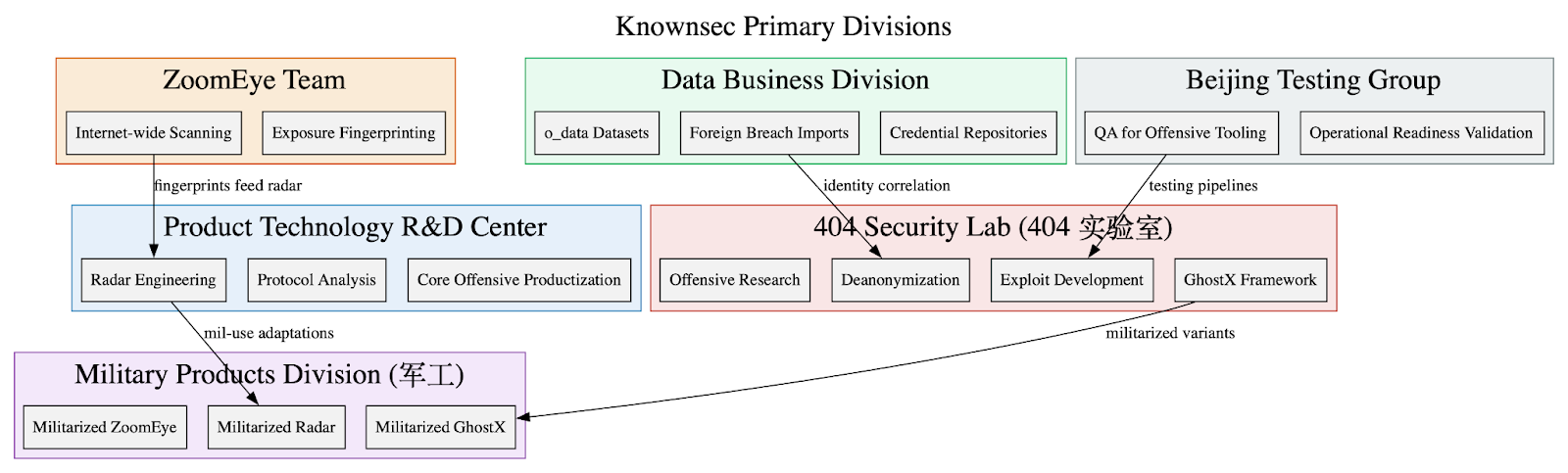
THE KNOWNSEC LEAK: Yet Another Leak of China’s Contractor-Driven Cyberespionage Ecosystem
In November of 2025, an allegedly massive leak of data from Chinese company “KnownSec” was posted to a github account. The leak has since been pulled off of Github and downloaded by very few, and of those few who gained access, only one uploaded 65 documents as a primer to the leak elsewhere for others to see. DTI was able to get the 65 document images and this initial investigation is derived from this slice of a much larger leak that is out there but not available.
While Knownsec advertises itself as a “white hat” pillar in China’s cybersecurity landscape, the leak revealed the company operates a vertically integrated espionage stack for reconnaissance, exploitation, collection, and persistence, designed for both domestic surveillance and foreign intelligence operations in support of China’s security state.
Its internal documents, product manuals, and data repositories show a company engineered to support Chinese national security, intelligence, and military objectives. Tools like ZoomEye and the Critical Infrastructure Target Library give China a global reconnaissance system that catalogs millions of foreign IPs, domains, and organizations mapped by sector, geography, and strategic value. Massive datasets containing real names, ID numbers, mobile phones, emails, and credentials allow Knownsec and its government clients to correlate infrastructure with people, enabling rapid deanonymization, targeting, and social engineering. On top of this data foundation, Knownsec’s offensive products – GhostX, Un-Mail, and Passive Radar – purport to provide a full intrusion and surveillance pipeline.
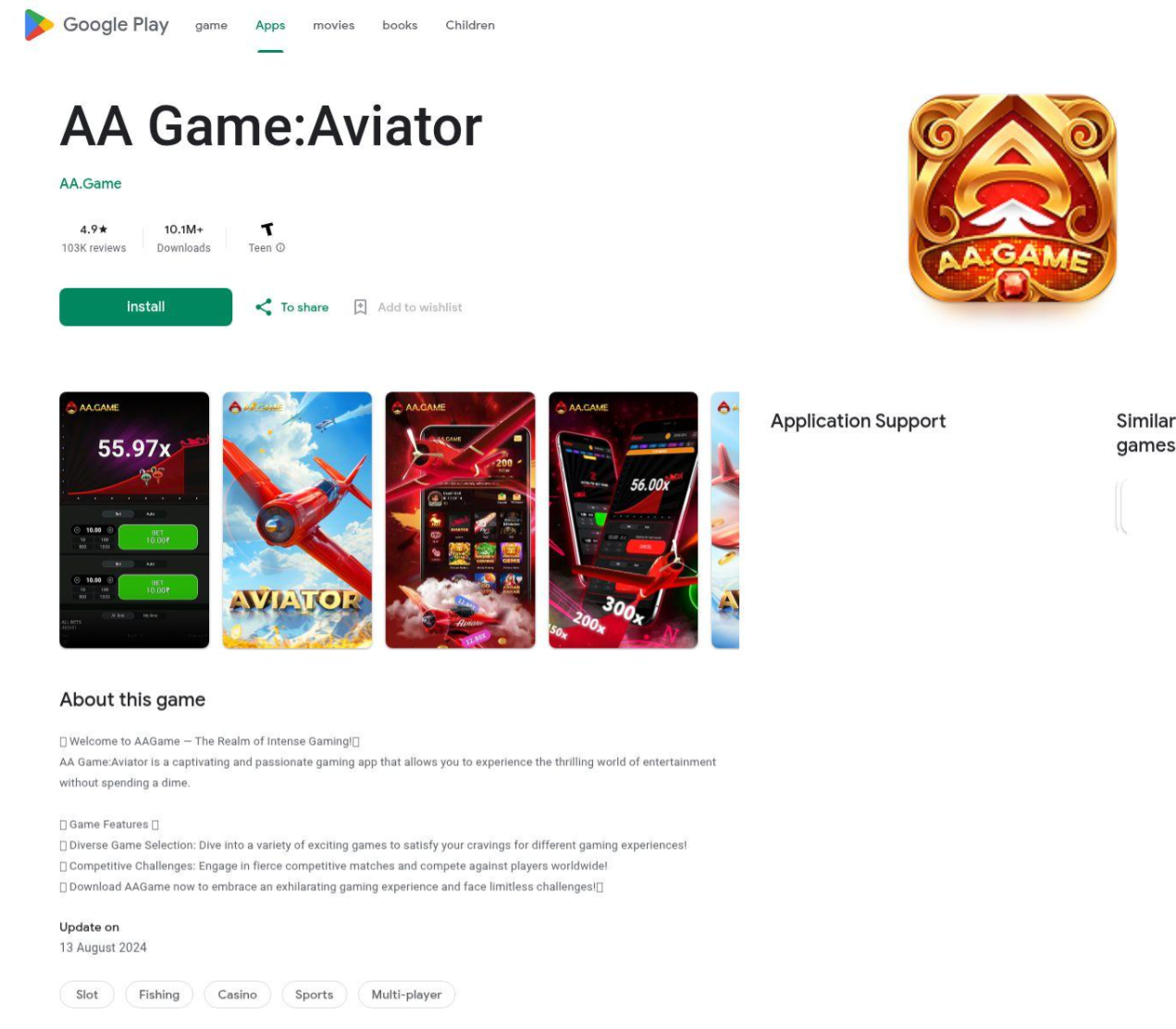
Pay to Lose: Dubious Online Gambling Games
DTI analysts identified multiple clusters of dubious Android applications created in the past few weeks that are engaged in predatory gambling and real money gaming apps. Notably, these are not registered apps. They are intentionally misleading users into thinking they are legitimate and reputable through multiple tactics like spoofing the Google Play Store, creating fake reviews, generating fake public win declarations, and creating entire brands with marketing campaigns and broad distribution tactics. These clusters also attempt to evade detection and analysis by having post install code and configuration retrievals from actor controlled sites, which serve a dual purpose of distributing region specific content to users post installation.
The investigation is segmented into three distinct infrastructure clusters. Each cluster appears to target a general set of countries including Nigeria, India, Pakistan, and the Philippines. They also appear to have non-region specific user base targeting, including English, Portuguese, and Bengali speaking users. Despite the wide range of targets, the clusters share a common theme of mobile-focused gaming or gamified gambling apps to attract users for financial gain
Security Snack: Phishing Interviews
My team uncovered a malicious actor that has created several domain masquerades of small companies posing as job boards, interview themes, and login pages since approximately August 2025.
The investigation revealed two distinct objectives. The first is a credential harvesting scheme targeting ID.me accounts — the official identity provider for US government services like the IRS and SSA — which can then be exploited to facilitate financial fraud, including tax refund theft and fraudulent unemployment benefits.
The second cluster focuses on malware delivery, tricking job seekers via fake Microsoft Teams meeting invites to download a malicious, unsigned variant of the remote access tool Connectwise. This gives the attacker access to the victim’s machine where they may conduct follow-on attacks.
What We’re Reading
In case you’re behind on your cybersecurity reading homework, DTI team member Ian Campbell’s monthly recommended reading list will get you up to speed!
- The top podcast for the month: ChinaTalk - Richard Danzig on AI and Cyber
- The top article for the month: CERT Polska - Energy Sector Incident Report
- The top research for the month: GTIG - No Place Like Home Network: Disrupting the World's Largest Residential Proxy Network
📚Checkout the full reading list here📚
Where We’ll Be
- AFCEA West 2026, San Diego, CA, 10-12 February
- BSides Seattle, Redmond, WA, 27-28 February
- NICAR 2026, Indianapolis, IN, 5-6 March
- BSides SF, San Francisco, CA, 21-22 March
Final Thoughts
As always, thank you to my returning readers! If you’re new, I hope you found this newsletter informational, helpful, and worthy of sharing with your peers. And of course I hope you will be coming back to read future editions!
We share this newsletter via email as well - if you’d prefer to get it to your inbox, sign up here.
If you missed last month's content, here are some quick links:
- Chinese Malware Delivery Domains Part IV
- The APT35 Dump Episode 4: Leaking The Backstage Pass To An Iranian Intelligence Operation
- B2B2C Supply Chain Attack: Hotel’s Booking Accounts Compromised to Target Customers
Thanks for reading - see you next month!
-Daniel

Welcome to the New Year, I hope you all had a restful holiday season! Similarly to the November issue, we decided to hold this edition until the post-holiday inbox avalanche has (hopefully) subsided. I wouldn’t want you to miss your favorite newsletter!
It’s hard to believe that DTI turns one year old this coming Friday! In case you haven’t been a subscriber since “Day One”, allow me a brief recap: In September of 2024, at a DomainTools onsite meeting, serendipity brought together two individuals with deep security industry connections, and a passion for community. We hatched an idea, got a few more colleagues excited about this idea, and in late 2024, we pitched it to our bosses. A scrappy program on a shoestring budget, with an agreement to fail fast and pivot as necessary. We signed up for some KPIs (you better measure success if you want to spend other peoples’ money!), and we launched on January 9th, 2025.
As I sit here, drafting this message, I can’t help but look back with pride on everything we did this past year: The countless hours of collective hard work, the travel all over the world to meet with the community, and most importantly, all the great research we published. We positively crushed it, if I do say so myself!
Now it’s late December, and the future looks decidedly less certain. One half of the DTI Leadership team is no longer with the company. She would hate it if I called her out here by name, but IYKYK. Thank you for a crazy year of collaboration, planning, organizing, problem solving, and innovating. Myself and the remaining DTI Team miss you greatly!
I’m not sure yet what 2026 will bring, but I know it will be different. Different isn’t automatically bad of course, so time will tell! Stay tuned for updates!
Back to Business
For those of you keeping score, the weather here in the Pacific Northwest has officially transitioned from damp, dark, and cold to damper and colder but a little less dark. But luckily none of that has slowed down our researchers. Fueled by hot coffee and cold redbull, they’ve been burning the 4pm oil, and we have some fascinating, and frankly brazen, campaigns to share as we kick off the year.
Our featured research for this edition looks at a massive “super-cluster” of over 5,000 Chinese malware delivery domains. What makes this investigation particularly special is how we did it: our team utilized agentic AI systems to accelerate our analysis by 10x. If you’ve been wondering how AI actually changes the game for threat hunters, this is the blueprint.
We also pulled back the curtain on the bureaucratic side of state-sponsored espionage with our second deep dive into the APT35 leaks. It turns out that Iranian intelligence operators deal with the same mundane office headaches we do: Spreadsheets, expense reports, and ticketing systems.
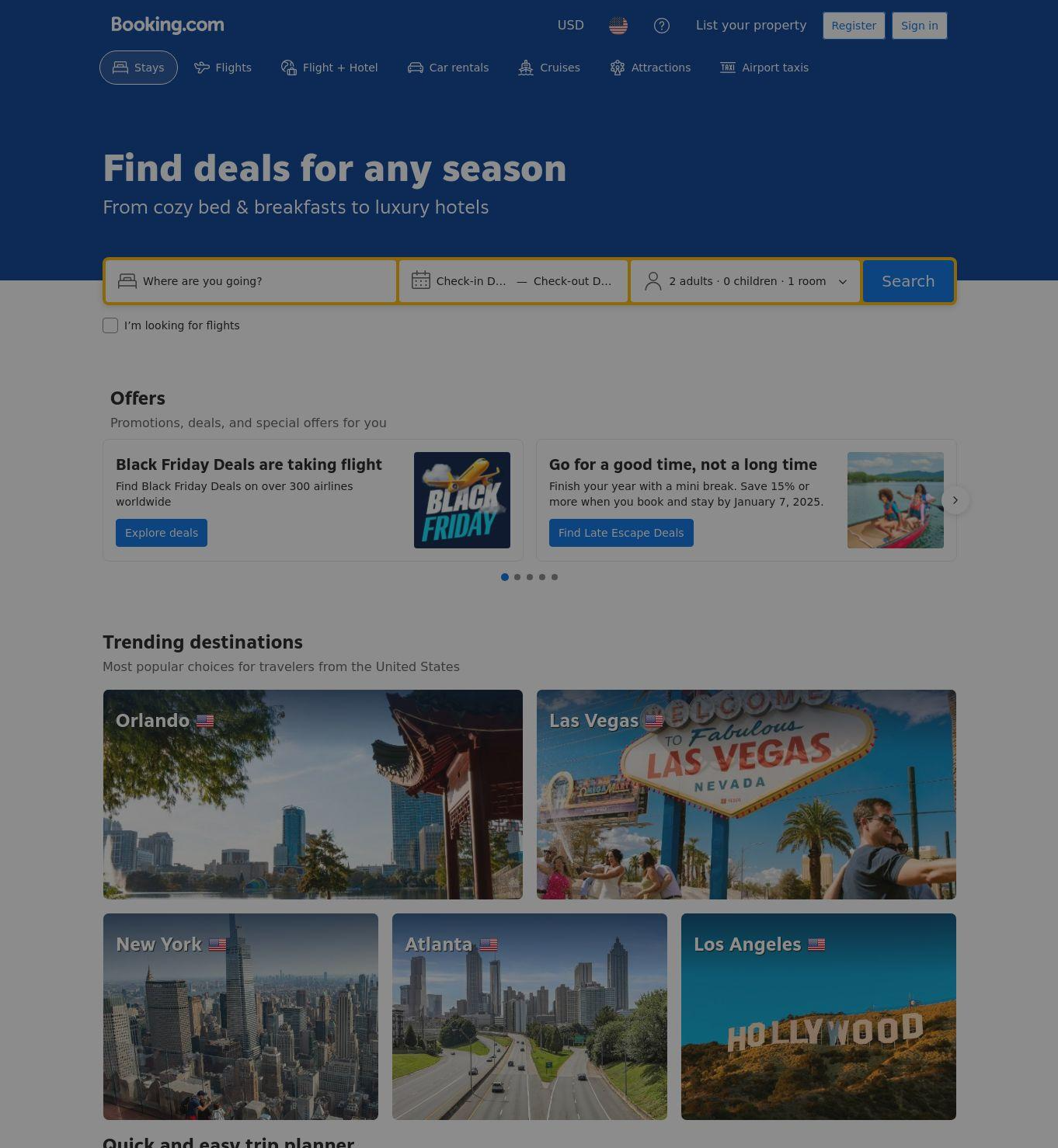
Finally, we took a look at a B2B2C supply chain attack targeting the hospitality industry. By compromising hotel management accounts, attackers are reaching customers directly through official Booking[.]com channels. It’s a stark reminder that if the supply chain isn’t secure, neither is the trusted platform it supports.
Hot off the Presses
B2B2C Supply Chain Attack: Hotel’s Booking Accounts Compromised to Target Customer
DTI’s investigation reveals a sophisticated campaign targeting Booking[.]com customers by compromising hotel management accounts. Since May 2025, threat actors have generated nearly 1,000 spoofed domains to execute a “verify or cancel” phishing scheme. By hijacking official hotel messaging channels, attackers send urgent alerts that direct travelers to fraudulent sites. These pages are dynamically populated with the victim’s actual reservation details which have been stolen from the hotel’s own database to create a high-trust environment for stealing payment information.
Chinese Malware Delivery Domains Part IV
DTI’s latest investigation into massive Chinese malware delivery infrastructure reveals the addition of over 1,900 new malicious domains in the super cluster of over 5,000 domains we have been tracking since early 2025. This activity, which primarily targets Chinese-speaking users, has evolved from a consolidated infrastructure into a fragmented and localized network using domestic Chinese registrars to improve operational security. The attackers employ deceptive lures such as spoofed downloads for Chrome, VPNs, and office software to deliver an array of trojans and credential stealers.
To manage this massive influx of data, our researchers deployed agentic AI systems to analyze the malicious domains, increasing analysis speed by 10x. By utilizing a “task-based AI orchestrator” paired with specialized sub-agents, the team was able to bypass anti-automation hurdles and autonomously interact with and analyze thousands of sites per day.
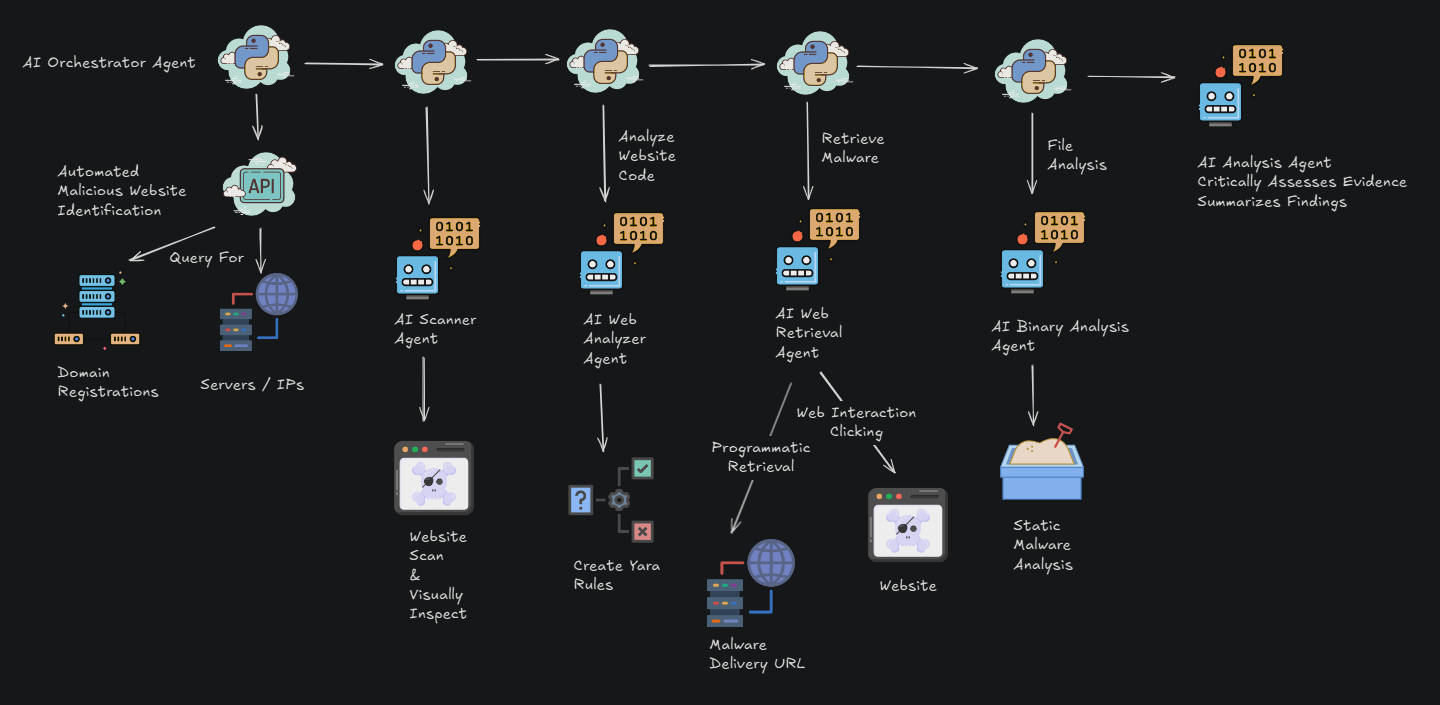
Agent Orchestration Flow Diagram
The APT35 Dump Episode 4: Leaking The Backstage Pass To An Iranian Intelligence Operation
DTI’s latest deep dive into the four-part leak of internal documents from APT35 (Charming Kitten) reveals the financial administration powering Iranian state-sponsored espionage. The leaked files, ranging from payment spreadsheets to internal ticketing systems, show how the group has financed and managed their operations in spite of international sanctions. These documents track everything from server procurement and crypto-payment receipts to operator attendance logs and performance metrics, illustrating a “bureaucratic metabolism” where cyberattacks are treated as standard administrative workflows.
Despite this clerical precision, the investigation highlights a glaring lack of operational hygiene. The group failed to secure their backend infrastructure and cleartext credentials even after the internal documents were leaked, allowing researchers to map the financial and administrative connections between APT35/Charming Kitten and the Iranian “Moses Staff” threat actor. By stripping away the mystery of their technical exploits, this research exposes the administration, including budgeting, invoice reconciliation, and supervisor approvals, that sustains Iran’s strategic information operations across the Middle East and beyond.
Screenshot of moses-staff[.]io homepage
What We’re Reading
In case you’re behind on your cybersecurity reading homework, DTI team member Ian Campbell’s monthly recommended reading list will get you up to speed!
- The top podcast for the month: Cyberwire – Root Access to the Great Firewall
- The top article for the month: Infoblox – Parked Domains Become Weapons with Direct Search Advertising
- The top research for the month: GA Tech et al – From Concealment to Exposure – Understanding the Lifecycle and Infrastructure of APT domains
Checkout the full reading list here
Where We’ll Be
- The DTI Travel Squad is staying local in January, but we will keep you updated on future travel once schedules get finalized!
Final Thoughts
As always, thank you to my returning readers! If you’re new, I hope you found this newsletter informational, helpful, and worthy of sharing with your peers. And of course I hope you will be coming back to read future editions!
We share this newsletter via email as well – if you’d prefer to get it to your inbox, sign up here.
If you missed last month’s content, here are some quick links:
- Threat Intelligence Report: APT35 Internal Leak of Hacking Campaigns Against Lebanon, Kuwait, Turkey, Saudi Arabia, Korea, and Domestic Iranian Targets
- Inside the Great Firewall Part 3: Geopolitical and Societal Ramifications
- Inside the Great Firewall Part 2: Technical Infrastructure
- Inside the Great Firewall Part 1: The Dump
Thanks for reading – see you next month!
-Daniel
https://www.linkedin.com/in/schwalbe
https://infosec.exchange/@danonsecurity

Dive into DomainTools Investigations' latest threat intel! Read our 3-part series on China's Great Firewall leak and an analysis of APT35 (Charming Kitten) campaigns targeting the Middle East and Korea, focusing on Exchange attacks. Get the intelligence you need!
The title of this month’s newsletter is a deep cut taken from the height of my favorite music genre, the admittedly awkwardly titled “Alternative Music.” What can I say, the 1990s in Seattle were wild, man - you had to be there.
Speaking of being there, last week was the Thanksgiving Holiday here in the United States. Normally my newsletter goes out on the last Tuesday of the month, but considering a lot of security professionals in the US got Thursday and likely Friday off, we decided to push publication by a week, so hopefully more of you can enjoy this edition instead of it getting buried under mashed potatoes and gravy!
The weather here in the Pacific NorthWest has firmly settled into “damp mode” (IYKYK), and the temperatures have started to creep below 40 degrees Fahrenheit (below 4 degrees Celsius for my international friends). I refuse to call it “The Big Dark” however - stop trying to make “The Big Dark” happen, Gretchen! Despite the cold, I’m happy to report that the intensity of DomainTools Investigations’ research output is only heating up.
Our flagship research for November, “Inside the Great Firewall,” is a three-part series based on a recent dump of documents and technical details of China’s censorship infrastructure. This massive leak provided us with over 500 gigabytes of internal operational data. I had the pleasure of joining Dave Bittner on the Research Saturday podcast from N2K | CyberWire to discuss our team’s work.
In addition to this deep dive, we also published a threat intelligence report based on leaked internal documents from APT35 (Charming Kitten). This report maps the Iranian state-sponsored actor's organization, tool kit, and campaign strategies. It details their campaigns against Lebanon, Kuwait, Türkiye, Saudi Arabia, Korea, and domestic Iranian targets, with a focus on their use of Microsoft Exchange attack chains. As a former Exchange Admin, I took personal note of that detail and was glad those days were behind me!
Last but not least, my team and I attended CYBERWARCON in Arlington, Virginia a couple of weeks ago. It was great to connect with the community, we had a small sponsorship booth and had many excellent conversations with fellow practitioners. I personally like the timing of this one-day conference, as it’s a nice bookend to its sister conference SLEUTHCON, which we attended earlier this year.
November was packed with research and tasty threat intelligence, so let's dive right in and get you up to speed!
Hot off the Presses
Inside the Great Firewall Part 1: The Dump
In September 2025, a historic breach of China’s censorship infrastructure leaked over 500 gigabytes of internal data detailing the infrastructure, design, and companies involved with the Great Firewall (GFW). DTI researchers analyzed more than 100,000 documents, internal source code, work logs, configuration files, emails, technical manuals, and operational runbooks.
Part 1 covers the human machinery behind the GFW and the consequences of the leak. This data links specific engineers and administrators to their roles across state-run ISPs (China Telecom, China Unicom, China Mobile), academic research institutions, and Ministry of State Security (MSS)-linked vendors.

Inside the Great Firewall Part 2: Technical Infrastructure
In Part 2, DTI analysts offer a forensic reconstruction of the Great Firewall’s technical infrastructure. From spreadsheets detailing app endpoint behavior, user monitoring intervals, and hardware configurations to blueprint files illustrating node relationships and control flows, the data illustrates a highly centralized yet distributed architecture, built on cooperation between state-run ISPs, telecom vendors, university research labs, and policy-design entities. Using this data, our researchers mapped the operational logic, software structure, and institutional alignment driving the digital surveillance regime.

🔍Read the full technical deep dive here
Inside the Great Firewall Part 3: Geopolitical and Societal Ramifications
In the final part of the series, our team analyzes the strategic doctrine behind the Great Firewall. This analysis reveals the GFW as a cornerstone of China’s broader governance model, extending internal social control mechanisms into the digital realm while also projecting power abroad. The regime serves a dual purpose of insulating the domestic population from undesired narratives and foreign influence, while exporting technologies, protocols, and ideological models of digital sovereignty to other authoritarian or aspiring technocratic regimes.

Threat Intelligence Report: APT35 Internal Leak of Hacking Campaigns Against Lebanon, Kuwait, Turkey, Saudi Arabia, Korea, and Domestic Iranian Targets
In October, internal documents from APT35, also referred to as Charming Kitten, were leaked on Github. Our researchers reviewed and analyzed the leaked documents to form a tightly linked forensic trail that maps both technique and organization. In this report, we broke down APT35’s tool kit which covers reconnaissance, initial access, and post-exploitation tooling optimized for large-scale, quota-driven compromise operations. Our team analyzed the actor’s operational profile and campaign strategies, identifying an emphasis on weaponizing exchange attack chains (ProxyShell, Autodiscover, EWS enumeration, and PowerShell driven tasks) to extract mailbox contents and Global Address Lists, maintain mailbox-level persistence, HUMINT extraction, and iterative phishing loops based on harvested address books.

What We’re Reading
In case you’re behind on your cybersecurity reading homework, DTI team member Ian Campbell’s monthly recommended reading list will get you up to speed!
- The top article for the month: GreyNoise Intelligence – When Bulletproof Hosting Proves Bulletproof: The Stark Industries Shell Game
- The top research for the month: arXiv – Adversarial Poetry as a Universal Single-Turn Jailbreak Mechanism in Large Language Models
📚Checkout the full reading list here📚
Where We’ll Be
- SANS Cyber Threat Summit 2025, London, UK, 3-4 December
Final Thoughts
As always, thank you to my returning readers! If you’re new, I hope you found this newsletter informational, helpful, and worthy of sharing with your peers. And of course I hope you will be coming back to read future editions!
We share this newsletter via email as well - if you’d prefer to get it to your inbox, sign up here.
If you missed last month's content, here are some quick links:
- DomainTools Investigations BSides NoVa Recap
- Repo the Repo - NPM Phishing
- Inside a Crypto Scam Nexus
- 18+ E-Crime
Thanks for reading - see you next month!
-Daniel
https://www.linkedin.com/in/schwalbe
https://infosec.exchange/@danonsecurity
https://www.linkedin.com/in/schwalbe
https://infosec.exchange/@danonsecurity


