SecuritySnacks
Executive Summary:
- PRC cyber threat actors dubbed "Salt Typhoon" (as well as FamousSparrow and GhostEmperor) appear to be focused on infiltrating Internet Service Providers (ISPs) at this time.
- Why is this important? “If hackers gained access to service providers’ core routers, it would leave them in a powerful position to steal information, redirect internet traffic, install malicious software or pivot to new attacks.”
- Unlike similar threat actor groups that include the name "Typhoon," Salt Typhoon looks to be geared towards intelligence collection as opposed to creating backdoors for the purpose of being an Advanced Persistent Threat (APT.)
- Suggestions for network defense include
- Identify and mitigate living off the land techniques that could provide threat actors with an opportunity to infiltrate an enterprise network. (CISA resource)
- Locate and remove or isolate unused and/or unpatchable legacy systems.
- Potential link to “shadow C2 infrastructure”
- By having access to the Internet Service Provider of an enterprise network, a threat actor could manipulate the network from the inside.
Highlights:
- Binary Defense revealed details of how it uncovered PRC state-sponsored cyber actors inside a global aerospace engineering firm's network where they had been snooping around for four months.
- "I can't really comment on the connection between the incidents, but I can say that given the uptick in Chinese-linked attacks against critical infrastructure supply chains, ISPs, and core internet devices there is a clear strategy at play where attackers are aiming to identity and exploit logical choke points in our society to take control of the flow of information and supplies," Binary Defense Director of Security Research John Dwyer told The Register today when asked about a possible Salt Typhoon connection.
- As recently as August, another Typhoon gang — Volt Typhoon — was accused of hiding in American networks after exploiting a high-severity bug in Versa's SD-WAN software.
- WSJ article states Salt Typhoon threat actors attempt to gain critical data from broadband service providers, has been going on for months and has been linked to China by U.S. government investigators. The reason for targeting broadband providers, in particular, is to take control of those providers’ systems and, from there, access their data and possibly launch a separate cyberattack from within their networks.
- CISA Executive Assistant Director for Cybersecurity Jeff Greene told us the agency is aware of the report of the compromised ISPs, and said that China is known to be infiltrating all manner of critical targets, who have compromised the IT environments across multiple critical infrastructure sectors and organizations.
- China's Salt Typhoon cyber spies spotted deep inside US ISPs
Activity is confirmed, govt aid provided.
No advisory on mitigations for customers at this time
Resources:
Chinese spies spent months inside aerospace engineering firm's network via legacy IT
(The Register, 18 September 2024)
https://www.theregister.com/2024/09/18/chinese_spies_found_on_us_hq_firm_network
China's Salt Typhoon cyber spies are deep inside US ISPs
(The Register, 25 September 2024)
https://www.theregister.com/2024/09/25/chinas_salt_typhoon_cyber_spies
China-Linked Hackers Breach U.S. Internet Providers in New ‘Salt Typhoon’ Cyberattack
(The Wall Street Journal, 26 September 2024)
https://www.wsj.com/politics/national-security/china-cyberattack-internet-providers-260bd835
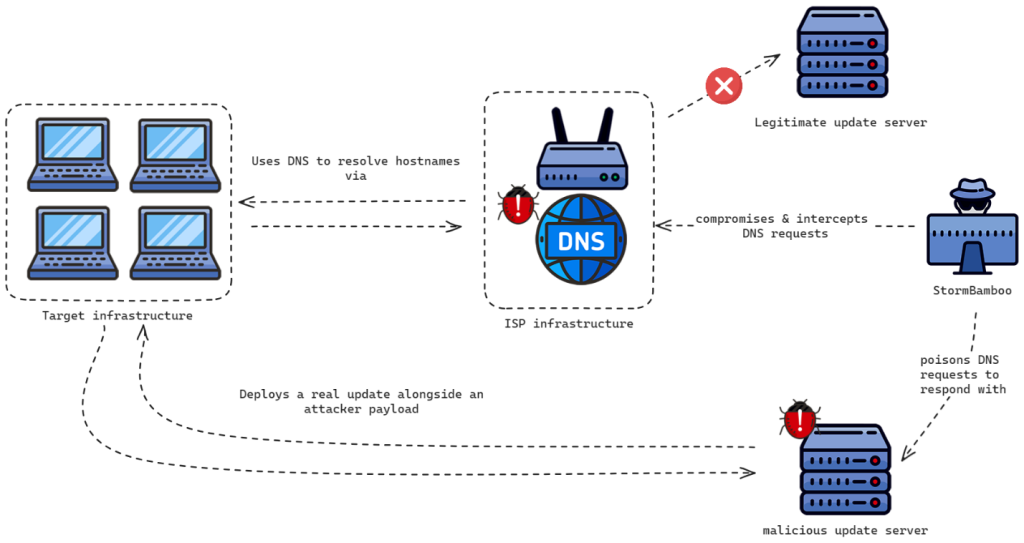
China-linked APT group Salt Typhoon compromised some U.S. internet service providers (ISPs)
(Security Affairs, 26 September 2024) – see graphic below
https://securityaffairs.com/168941/apt/salt-typhoon-china-linked-threat-actors-breached-us-isp.html
Salt Typhoon Cyberattack Targets U.S. Broadband Service Provider
(TeleCompetitor, 27 September 2024)
https://www.telecompetitor.com/salt-typhoon-cyberattack-targets-u-s-broadband-service-providers/

Image Source: China-linked APT group Salt Typhoon compromised some U.S. internet service providers (ISPs) Security Affairs, 26 September 2024

Continues To Use Credential Phishing Infrastructure to Target Individuals Perceived as a Threat to the Iranian Regime
Since June 2024, the Iran-nexus actor CHARMING KITTEN (APT42, Mint Sandstorm, TA453) continues to create new network infrastructure consistent with what the Mandiant intelligence team identifies as Cluster B. Mandiant previously reported on this CHARMING KITTEN infrastructure cluster using credential phishing pages to target individuals perceived as a threat to the Iranian regime, including researchers, journalists, NGO leaders, and human rights activists. There are no confirmed targets of the new infrastructure; however, it is likely that the actor’s target scope remains focused on entities deemed a threat to the Iranian regime.
Details
Newly Identified Domains:
- growing-prices-advanced[.]top
- competitive-searchvolume-considered[.]top
- software-selection-features[.]buzz
- app-engage-station[.]help
- Horse-improve-department[.]top
- click-manage-room[.]cfd
- flow-exulltation-uplift[.]top
- house-server-digital[.]xyz
- interconnected-equipment-buildings[.]buzz
- nail-forward-valid[.]lol
- request-human-received[.]xyz
- paper-blue-hero[.]top
These domains were all registered since the publication of Mandiant’s blog with some registered as recently as September 2024. The domains listed above share many similarities with domains previously attributed to Cluster B including:
- Similar TLDs: The new domains use TLDs such as ".top," ".buzz," and ".help," “.cfd,” “.xyz,” and “.lol” all of which were reported by Mandiant.
- Hyphenated Naming Conventions: The new domains continue to contain several words separated by hyphens.
- IP Overlap: All listed domains resolve to 135.181.203[.]1, an IP address assigned to the hosting provider, Hetzner, and used to host multiple Cluster B domains publicly reported by Mandiant.
Targeting
Specific targeting for these newly-identified domains is not known. However, public reporting indicates that Cluster B infrastructure commonly masquerades as login pages for Google, YouTube, and other file hosting services. The actor typically disseminates these credential harvesting pages through spear phishing emails that often pose as invitations to conferences or links to legitimate documents hosted on cloud infrastructure.
The most recent specific targeting information for Cluster B includes multiple entities impacted during March 2024. This includes Cluster B infrastructure to target a news editor working for a Persian-language news television channel using a fake Gmail login page and to target Google, Microsoft, and Yahoo credentials from individuals in the research and academic sectors in the U.S., Israel, and Europe.
Conclusion
The newly identified domains indicate that the CHARMING KITTEN actor continues to be active in the wake of public reporting. It is likely that this new infrastructure is being used in a manner consistent with previously reported activity: targeted spear phishing used to direct intended victims to credential phishing pages. The actor’s target set likely continues to be focused on entities deemed a threat to the Iranian regime.
IOCs on GitHub
Find all IOCs on our GitHub.
Crypto News relayed widespread social media reports of Web3-related domain takeovers of Squarespace-held domains.
Domain takeovers of Squarespace-held domains
Crypto News relayed widespread social media reports of Web3-related domain takeovers of Squarespace-held domains. Using 0xngmi’s list as a guidepost, we are releasing passive DNS records for the listed sites observed since 2024-07-01 to allow for further analysis (please note two sets of data, one in epoch time, one set in a subfolder with human-readable time). Inclusion in this list does NOT necessarily indicate compromise.
Crypto News link: https://crypto.news/defi-protocols-compromised-as-many-domains-under-dns-siege/
0xngmi link: https://gist.github.com/0xngmi/789e297f3107d3c28c56da7acf11828d
Passive DNS records: https://github.com/DomainTools/SecuritySnacks/tree/main/2024/DeFiDNS


Screenshots from DNSDB Scout of two services that indicated attempted or successful compromise.
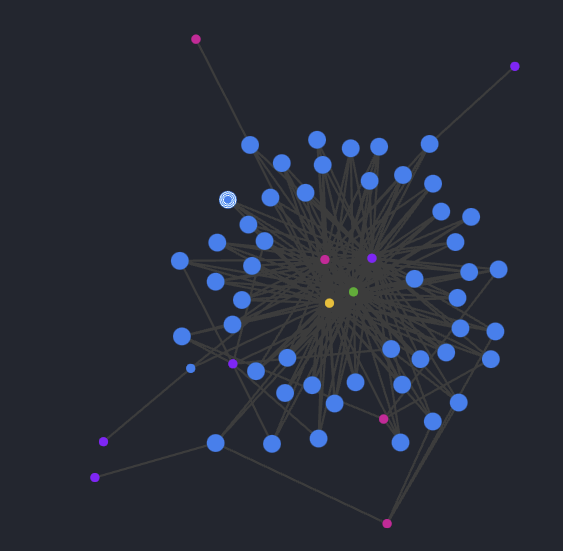
Wester European targeted SMS campaigns that are phishing for credentials and banking information.
Western European targeted SMS campaigns that are phishing for credentials and banking information
We have been following a threat actor since at least November targeting western European countries with SMS campaigns, leading to the phishing of account credentials and banking information. Targets thus far include government benefits agencies, e-commerce giants, and video-on-demand services. This actor favors Russian-based Prospero hosting, and has now been detected using Squarespace as a registrar.
This actor often uses phrases like ‘facturacion’ (which translates into ‘billing’ or ‘invoice in several European languages) as well as ‘service,’ moncompte (my account), ‘suscripcion,’ and similar generic terms combined with specific brands or agencies to lure targets in for account takeover or bank fraud. Previously targeted countries include Norway, Sweden, Finland, and Austria; the Squarespace-registered batch appears to be targeting Germany, France, and Spain as well.
Recent domain examples below:
suscripcionfacturacion[.]com
facturacion-suscripcionvod[.]com
retrasofacturacion[.]com
facturacion-retraso[.]com
connect-accnfix[.]com
navgov-hu[.]com
ntflx-serviceup[.]com
ntlx-accuntmanage[.]com
serviceup-ntlx[.]com
ups-myserviceup[.]com
We advise network administrators consider blocking Prospero’s IPspace in its entirety and allow-listing elements on a case-by-case basis, if possible.
End-users should be wary of SMS-related banking alerts, and only input their banking credentials into known or verified websites and application. We advise users to never download banking applications from third-party app stores, and to always navigate to their bank’s website manually in order to avoid unknowingly entering credentials into cloned or fraudulent banking websites.

Visualization of 49 likely associated domains first seen or newly active from 2024-06-01 forward utilizing Squarespace registration and Prospero hosting, also showing commonalities among server type and risk score.

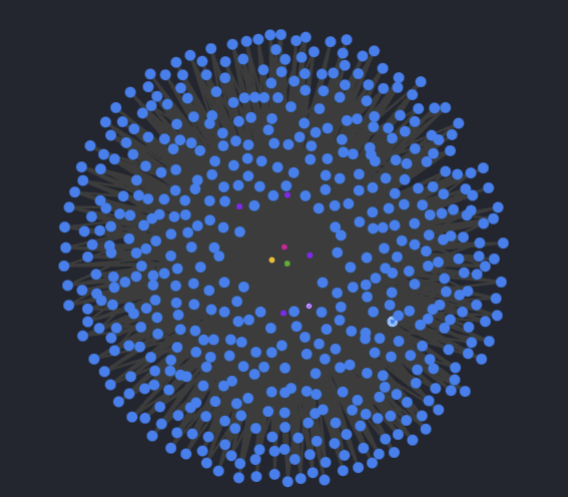
1600+ were registered between 2024-06-19 and 2024-06-20.
1600+ were registered between 2024-06-19 and 2024-06-20
We observed a massive bloom of newly active domain registrations including the word “airdrop” between 2024-06-19 and 2024-06-20. Instead of the usual 40-60 domains per day, 1600+ were registered. 1549 of those domains appear to be by a single actor, with a common profile across MX, registrar, registrant, TLD, and more. The 1549 domains have an average risk score of 90, on a 0-100 scale of increasing risk.
Passive DNS (see screenshot from DNSDB Scout) shows an example domain moving from Dynadot to Onamae nameservers prior to expiration, and then moving to parked NS, possibly indicative of enforcement action, but not necessarily. Whois shows registrar moving from Dynadot to Onamae at the same time.
While not declarative of malicious activity, this massive renewal of activity in the number of “airdrop” domains is notable due to the regularity of airdrop scams in the cryptocurrency space – scams which often involve leading targets to malicious websites.
We encourage all cryptocurrency users and services to warn others of the possibility of a wave of airdrop scams.
Domain profile:
First Seen/newly-active and re-registered: 2024-06-19 or 2024-06-20
Registrar: GMO Internet Group, Inc. d/b/a Onamae[.]com
MX domain: h-email[.]net
ISP: Team Internet AG (ASN206834)
IPs: 104.247.81.50, 104.247.81.51, 104.247.81.52, 104.247.81.53, 104.247.81.54
TLD: xyz




200+ registrations in concert with financial or credential phishing
We see over 200+ billing-oriented TEPCO domains created in the last month with the same host. We suspect it’s a mass domain registration in concert with financial or credential phishing.
The domains and historical passive DNS records for the two IPs involved can be found in the GitHub link below. The pDNS may or may not include uninvolved domains, but many appear to be part of the same cluster or campaign.
If the community has any additional input, please let us know.
https://github.com/DomainTools/SecuritySnacks/tree/main/2024/TEPCO

195 domains registered and used for credential phishing pulled from a phish impersonating DocuSign using a click thru URL obfuscator.
195 domains registered and used for credential phishing
We spotted 195 domains registered and used for credential phishing pulled from a phish impersonating DocuSign using a click thru URL obfuscator.
The initial domain was qi6kd[.]com which showed a google workspace login, off a DocuSign-impersonating email with a link to a malicious site.

Potential phishing on reregistering old, inactive vmware-related domains.
Potential phishing on reregistering old, inactive vmware-related domains
Using some monitors, @neurovagrant observed an actor creating or reregistering old, inactive vmware-related domains and spinning them up for likely phishing purposes.
vmware-shop[.]store
Registrar: Gname
Host: Alibaba
First seen: 2023-03-11 (today)
Screenshot of landing page below taken today, appears to be directly impersonating vmware/Broadcom, probably phishing for creds.
vmwareshop[.]com also reregistered today, Gname registration and NS but no hosting yet.
Suspicious campaigns registering thousands of domains across cheaper TLDs
We observed multiple suspicious campaigns recently auto-registering thousands of domains across cheaper TLDs such as .cfd and .bond. While their purpose is not yet apparent, and the two sets of events appear unconnected, here's what we've observed so far:
More than 10k domains in 3 days across .cfd registered through Aceville Pte. Ltd. with higher-than-average Iris risk scores fitting several pseudorandom-looking/DGA patterns. Examples:
388aqo001[.]cfd
4qwljn001[.]cfd
8hgsxe001[.]cfd
adix348002[.]cfd
adpzfsn002[.]cfd
aerx7v9002[.]cfd
91-yongjiudizhi-f19q4x8j-dpq[.]cfd
91-yongjiudizhi-q8hkazxp-sij[.]cfd
And several thousand .bond domains newly registered through Key-Systems fitting one of the following patterns:
security-jobs-#####
cyber-security-degree-#####
cyber-security-jobs-#####
homeland-security-jobs-#####
cyber-security-#####
security-surveillance-cameras-#####
home-security-#####
password-manager-#####

Barbie & Barbenheimer domains list
While fans are still flocking to Barbie for the second week in a row, bad actors are flocking to register barbie and barbenheimer domains. See the full list here:
https://github.com/DomainTools/SecuritySnacks/blob/main/2023/Barbie/barbie-domains.txt

79 newly registered domains to "help"
CISOs - worried about getting an SEC notice? Looking for an attorney? 79 domains were recently registered to "help" you find one no matter where you are in the US. (we're kidding, of course, you probably want to avoid all of these)

Down to only a few thousand
We continue to monitor the drop of active .GA domains as part of their move away from FreeNom. Since late March we saw a drop from ~9M to ~1.5M domains, and now down to a few thousand.

