Rainy Day Newsletter #12 (but not 35)
Subscribe to the Newsletter here
Welcome to the New Year, I hope you all had a restful holiday season! Similarly to the November issue, we decided to hold this edition until the post-holiday inbox avalanche has (hopefully) subsided. I wouldn’t want you to miss your favorite newsletter!
It’s hard to believe that DTI turns one year old this coming Friday! In case you haven’t been a subscriber since “Day One”, allow me a brief recap: In September of 2024, at a DomainTools onsite meeting, serendipity brought together two individuals with deep security industry connections, and a passion for community. We hatched an idea, got a few more colleagues excited about this idea, and in late 2024, we pitched it to our bosses. A scrappy program on a shoestring budget, with an agreement to fail fast and pivot as necessary. We signed up for some KPIs (you better measure success if you want to spend other peoples’ money!), and we launched on January 9th, 2025.
As I sit here, drafting this message, I can’t help but look back with pride on everything we did this past year: The countless hours of collective hard work, the travel all over the world to meet with the community, and most importantly, all the great research we published. We positively crushed it, if I do say so myself!
Now it’s late December, and the future looks decidedly less certain. One half of the DTI Leadership team is no longer with the company. She would hate it if I called her out here by name, but IYKYK. Thank you for a crazy year of collaboration, planning, organizing, problem solving, and innovating. Myself and the remaining DTI Team miss you greatly!
I’m not sure yet what 2026 will bring, but I know it will be different. Different isn’t automatically bad of course, so time will tell! Stay tuned for updates!
Back to Business
For those of you keeping score, the weather here in the Pacific Northwest has officially transitioned from damp, dark, and cold to damper and colder but a little less dark. But luckily none of that has slowed down our researchers. Fueled by hot coffee and cold redbull, they’ve been burning the 4pm oil, and we have some fascinating, and frankly brazen, campaigns to share as we kick off the year.
Our featured research for this edition looks at a massive “super-cluster” of over 5,000 Chinese malware delivery domains. What makes this investigation particularly special is how we did it: our team utilized agentic AI systems to accelerate our analysis by 10x. If you’ve been wondering how AI actually changes the game for threat hunters, this is the blueprint.
We also pulled back the curtain on the bureaucratic side of state-sponsored espionage with our second deep dive into the APT35 leaks. It turns out that Iranian intelligence operators deal with the same mundane office headaches we do: Spreadsheets, expense reports, and ticketing systems.
Finally, we took a look at a B2B2C supply chain attack targeting the hospitality industry. By compromising hotel management accounts, attackers are reaching customers directly through official Booking[.]com channels. It’s a stark reminder that if the supply chain isn’t secure, neither is the trusted platform it supports.
Hot off the Presses
B2B2C Supply Chain Attack: Hotel’s Booking Accounts Compromised to Target Customer
DTI’s investigation reveals a sophisticated campaign targeting Booking[.]com customers by compromising hotel management accounts. Since May 2025, threat actors have generated nearly 1,000 spoofed domains to execute a “verify or cancel” phishing scheme. By hijacking official hotel messaging channels, attackers send urgent alerts that direct travelers to fraudulent sites. These pages are dynamically populated with the victim’s actual reservation details which have been stolen from the hotel’s own database to create a high-trust environment for stealing payment information.
Chinese Malware Delivery Domains Part IV
DTI’s latest investigation into massive Chinese malware delivery infrastructure reveals the addition of over 1,900 new malicious domains in the super cluster of over 5,000 domains we have been tracking since early 2025. This activity, which primarily targets Chinese-speaking users, has evolved from a consolidated infrastructure into a fragmented and localized network using domestic Chinese registrars to improve operational security. The attackers employ deceptive lures such as spoofed downloads for Chrome, VPNs, and office software to deliver an array of trojans and credential stealers.
To manage this massive influx of data, our researchers deployed agentic AI systems to analyze the malicious domains, increasing analysis speed by 10x. By utilizing a “task-based AI orchestrator” paired with specialized sub-agents, the team was able to bypass anti-automation hurdles and autonomously interact with and analyze thousands of sites per day.
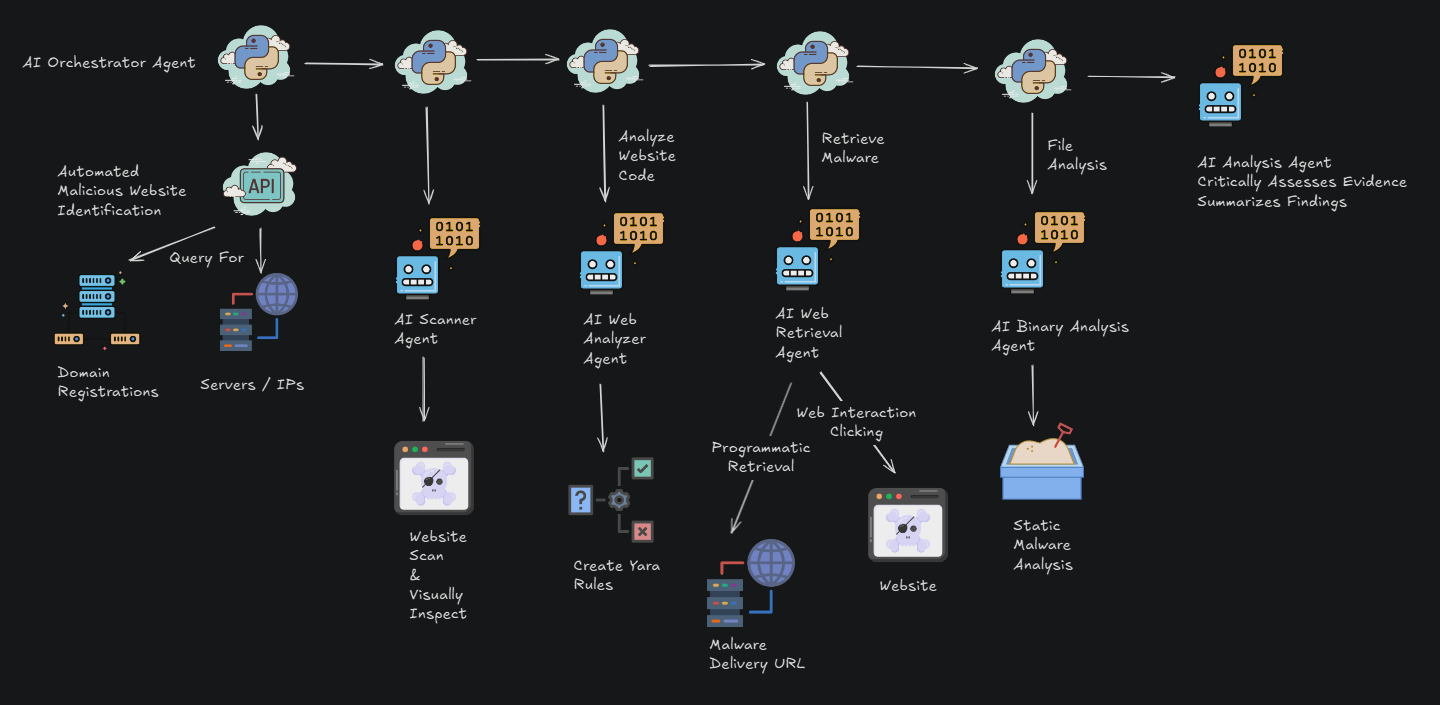
Agent Orchestration Flow Diagram
📖Read the latest research here
The APT35 Dump Episode 4: Leaking The Backstage Pass To An Iranian Intelligence Operation
DTI’s latest deep dive into the four-part leak of internal documents from APT35 (Charming Kitten) reveals the financial administration powering Iranian state-sponsored espionage. The leaked files, ranging from payment spreadsheets to internal ticketing systems, show how the group has financed and managed their operations in spite of international sanctions. These documents track everything from server procurement and crypto-payment receipts to operator attendance logs and performance metrics, illustrating a “bureaucratic metabolism” where cyberattacks are treated as standard administrative workflows.
Despite this clerical precision, the investigation highlights a glaring lack of operational hygiene. The group failed to secure their backend infrastructure and cleartext credentials even after the internal documents were leaked, allowing researchers to map the financial and administrative connections between APT35/Charming Kitten and the Iranian “Moses Staff” threat actor. By stripping away the mystery of their technical exploits, this research exposes the administration, including budgeting, invoice reconciliation, and supervisor approvals, that sustains Iran’s strategic information operations across the Middle East and beyond.
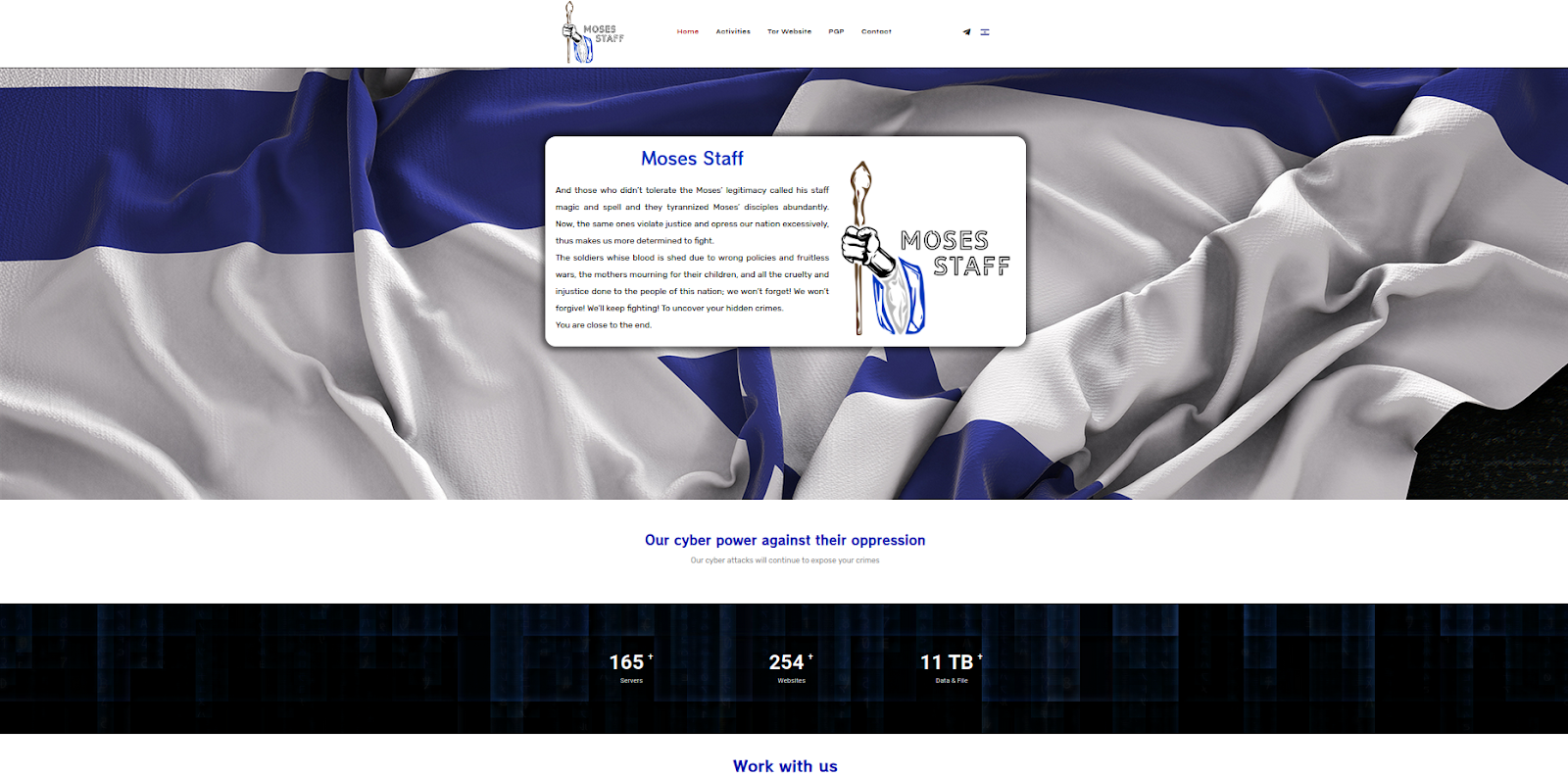
Screenshot of moses-staff[.]io homepage
What We’re Reading
In case you’re behind on your cybersecurity reading homework, DTI team member Ian Campbell’s monthly recommended reading list will get you up to speed!
- The top podcast for the month: Cyberwire – Root Access to the Great Firewall
- The top article for the month: Infoblox – Parked Domains Become Weapons with Direct Search Advertising
- The top research for the month: GA Tech et al – From Concealment to Exposure – Understanding the Lifecycle and Infrastructure of APT domains
📚Checkout the full reading list here📚
Where We’ll Be
- The DTI Travel Squad is staying local in January, but we will keep you updated on future travel once schedules get finalized!
Final Thoughts
As always, thank you to my returning readers! If you’re new, I hope you found this newsletter informational, helpful, and worthy of sharing with your peers. And of course I hope you will be coming back to read future editions!
We share this newsletter via email as well – if you’d prefer to get it to your inbox, sign up here.
If you missed last month’s content, here are some quick links:
- Threat Intelligence Report: APT35 Internal Leak of Hacking Campaigns Against Lebanon, Kuwait, Turkey, Saudi Arabia, Korea, and Domestic Iranian Targets
- Inside the Great Firewall Part 3: Geopolitical and Societal Ramifications
- Inside the Great Firewall Part 2: Technical Infrastructure
- Inside the Great Firewall Part 1: The Dump
Thanks for reading – see you next month!
-Daniel