The APT35 Dump Episode 4: Leaking The Backstage Pass To An Iranian Intelligence Operation
Executive Summary
APT35, also known as Charming Kitten, has long occupied an odd niche in the hierarchy of Iranian cyber operations. They’re the loud ones, constantly deploying new credential-harvesting pages dressed in Western university or defense-contractor branding, yet always recycling the same code and lures. For years, analysts dismissed them as a politically motivated collective within the Revolutionary Guard’s orbit, dangerous mainly to journalists and dissidents, but rarely haunting MITRE’s nightmares.
Episode 4, the latest leak, changes that perception. What matters here isn’t the spectacle of intrusion but the machinery behind it. The files dissolve the myth of the hacker into the hum of administration: spreadsheets logging hosting providers and invoice numbers, crypto receipts processed through Cryptomus, and server rentals under a mosaic of false European identities. These aren’t exploits, they’re expense reports. The dump exposes how Iranian cyber units requisition, fund, and maintain infrastructure, revealing the bureaucratic metabolism that turns state intent into executable code.
Post-leak, APT35 failed to clean up after themselves, leaving operational infrastructure, live servers, and even hosting and service passwords accessible for weeks. The supposed guardians of Iran’s cyber doctrine simply walked away from their own compromised backend. This lack of operational hygiene underscores the paradox of Charming Kitten: a bureaucracy mimicking a hacker collective, running espionage operations with clerical precision, yet unable to follow basic OPSEC discipline when their paperwork leaked into the open.
Seen through this lens, APT35 functions as a government department more than a hacker crew. Someone drafts a VPS requisition; another logs the cost in euros; a supervisor approves the line item; and only then does a technician deploy the phishing kit or C2 beacon. It’s the banality of intrusion, the paperwork of digital espionage. Episode 4 strips away the glamour of zero-days and leaves the logistics in plain view: account creation, invoice reconciliation, crypto transaction IDs as bureaucratic stamps of approval. The same apparatus that once managed oil exports now manages data theft and influence operations. Behind every exploit sits a spreadsheet; behind every “state-sponsored attack,” a purchase order; behind every patriotic slogan, an accounts-payable clerk.
The Episode Four Files:
The leaked spreadsheets form the operational backbone of APT35’s infrastructure management system, a triptych of bureaucracy masquerading as tradecraft. Each file exposes a different layer of the machine: procurement, payment, and deployment. Together they illustrate how a state-sponsored threat actor runs its cyber operations not through shadowy improvisation but through clerical precision. The documents track every rented server, every registered domain, and every euro or satoshi spent, all with internal ticketing numbers and service IDs linking actions across datasets. What emerges is a portrait not of hackers but of administrators, a bureaucracy that treats intrusion as an accounting exercise and espionage as a workflow.
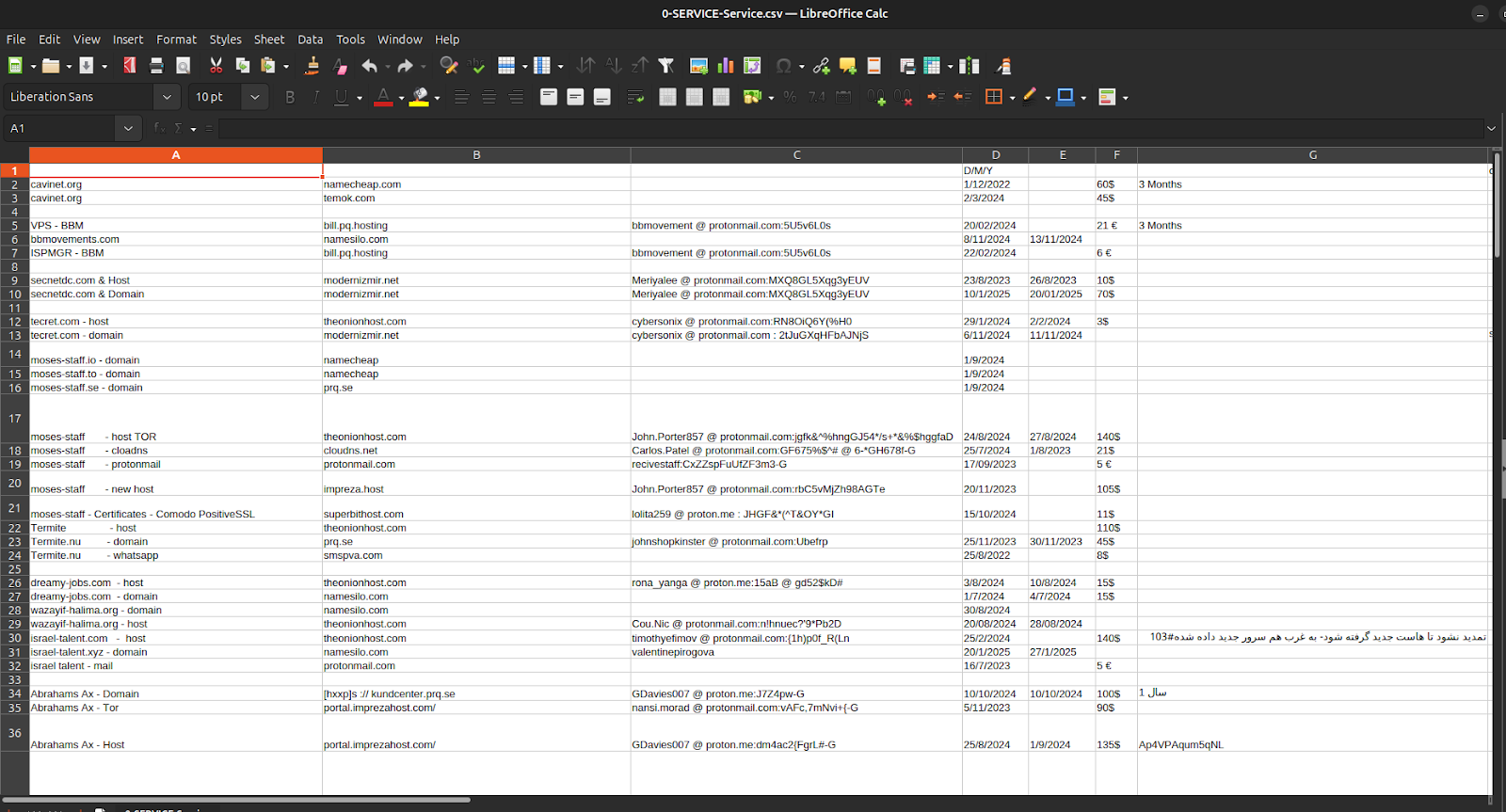
0-SERVICE-Service.csv
This sheet functions as the operational ledger. It contains roughly 170 populated rows tying domains to registrars and service notes, plus more than 50 distinct ProtonMail identities and over 80 cleartext credential pairs in email:password format. The entries include cadence markers like “3 Months / #2016,” lifecycle notes such as “SSL / no SSL,” and line-item prices in both dollars and euros. Provider references are recurrent and standardized rather than ad-hoc: EDIS (VPS) appears ~20 times, NameSilo (cheap domains) ~14, and Impreza (VPS) ~6, alongside sporadic mentions of Namecheap (domains) and Temok (Domains). The net effect is a normalized procurement sheet for intrusion, domains, tenancies, and accounts queued for operators, meticulous in bookkeeping but sloppy in OPSEC.
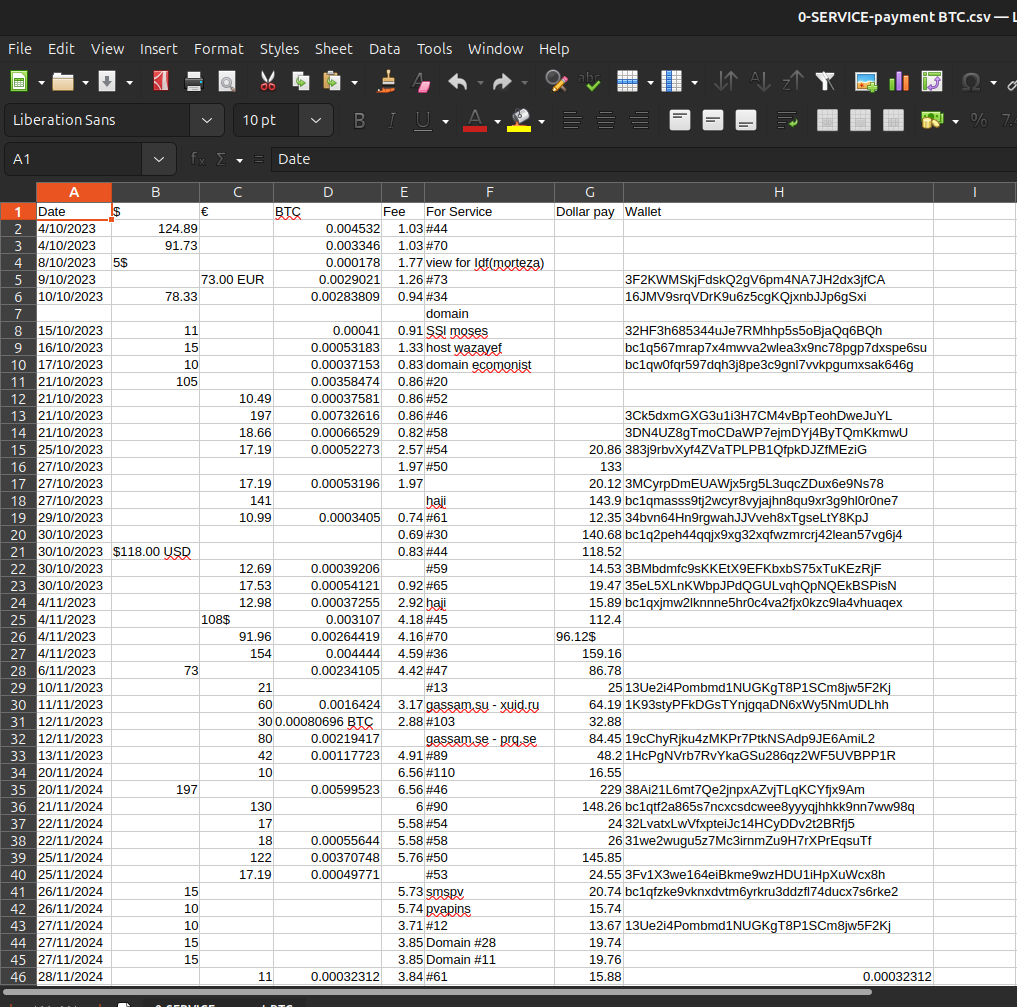
0-SERVICE-payment BTC.csv
This sheet contains financing data that stitches itself into a meticulous ledger of fifty-five entries spanning from October 4, 2023 through December 11, 2024. The totals form tight constellations around approximately $1,225, with average outlays of about $56 or 0.0019 BTC per transaction. At least thirty-two unique Bitcoin addresses populate the Wallet field. Many rows also reference internal service numbers, “#44,” “#70,” and others, that mirror entries in the companion service sheet (“#23,” “#30,” “#103”). Together they form a verifiable connection between request, payment, and activation. A closed accountability loop meant to satisfy internal auditors while preserving outward anonymity. Each crypto receipt aligns neatly with a ticket number and an allocated cost, revealing an ecosystem of deliberate, ledger-bound order beneath the façade of decentralization.
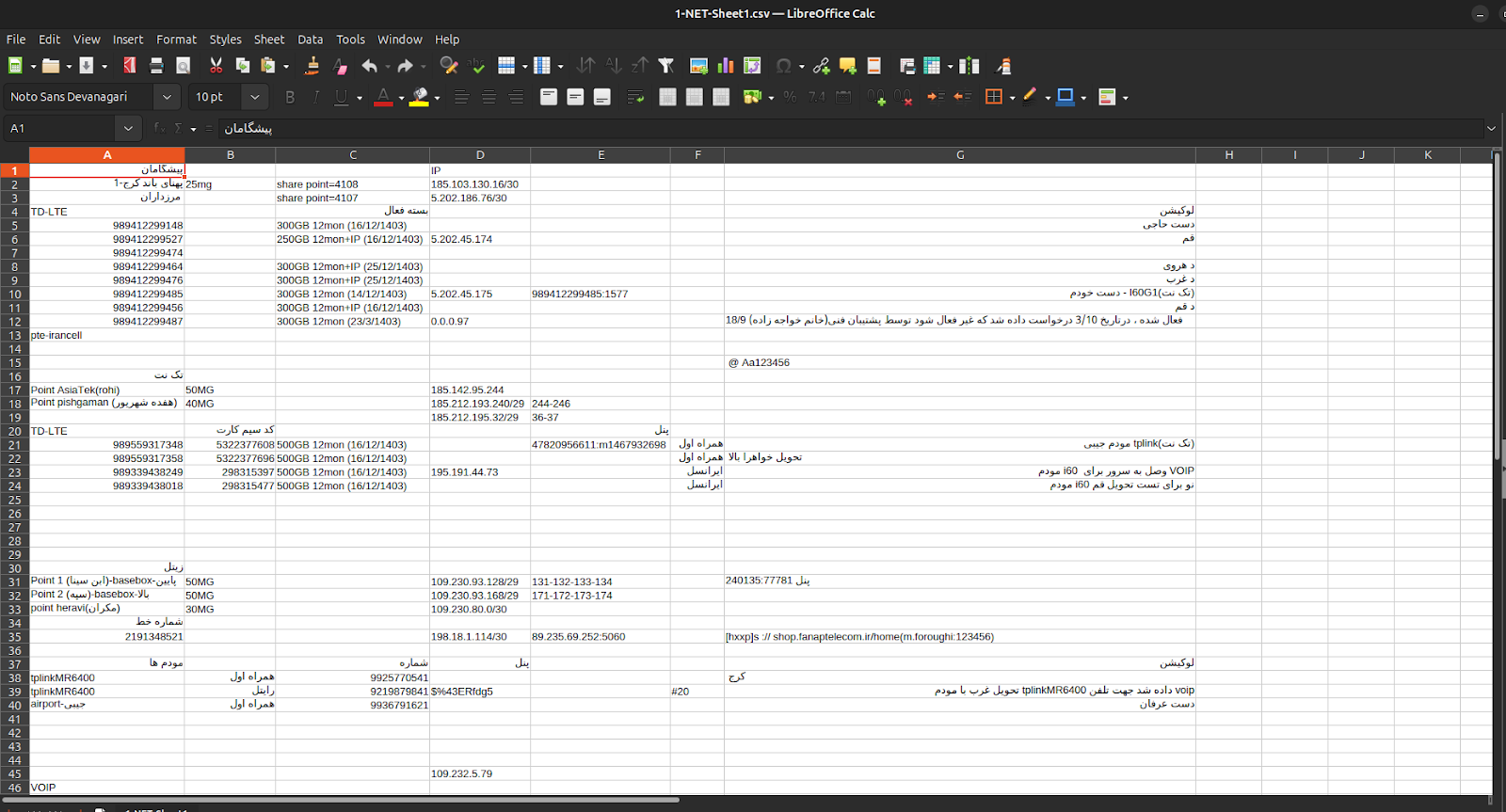
1-NET-Sheet1.csv
This sheet closes the loop with network addresses: IPs and /29–/30 allocations (e.g., 185.103.130[.]16/30, 185.212.193[.]240/29, 109.230.93[.]128/29, 195.191.44[.]73) with Persian-annotated connectivity and location notes (TD-LTE, service tiers, city markers). These rows correspond to live infrastructure observed in provider dashboards (EDIS, Impreza), matching the same pseudonymous customer identities and service SKUs seen in the invoices. In aggregate, the three files describe an industrial relay: the service sheet assigns and tracks assets, the BTC register funds and reconciles them (with ticket-level joins), and the network sheet manifests them as routable hosts. The tradecraft here isn’t improvisation; it’s administration, an evidentiary chain that converts hierarchy into infrastructure, with the very spreadsheets that ensure renewals also exposing credentials, wallets, and IPs.
The Economics of Access
For Tehran’s cyber apparatus, access isn’t stolen, it’s procured, budgeted, and renewed. Episode 4 makes unmistakably clear that intrusion has an economy. Each Virtual Private Server (VPS) payment, logged in euros, is a link in a chain of Iran’s information operations. All paid through Cryptomus, each transaction is small enough to slip under every compliance radar. There are no lump sums, no visible treasury trails, only the steady drip of crypto micro-payments routed through resellers in Cyprus, the Netherlands, and Central Europe. Each one buys continuity, not capability: another month of hosting for a phishing kit, another quarter of uptime for a command-and-control node, another renewal for a cover domain. This is cyber operations as a subscription service.
Charming Kitten’s internal operators follow a logic refined not in cyberspace, but in decades of sanctions survival. The same micro-smuggling economy that keeps Iranian goods moving across closed borders now underpins their digital operations. Instead of hiding budgets behind complex front companies, they fragment everything: dozens of disposable aliases, each spinning up a low-cost VPS, each paying through anonymous crypto gateways, each leaving behind a receipt that looks indistinguishable from civilian freelance infrastructure work. To an external reviewer, the activity resembles a swarm of hobbyists tinkering with side projects. Inside the apparatus, every alias corresponds to a tasking order, a performance measure, and a supervisory check.
Moses Staff: APT 35’s Hidden Hand
If the first half of Episode 4 exposed the clerical machinery that sustains Iran’s cyber-espionage bureaucracy, then the next revelation shows what that bureaucracy actually builds: the operational scaffolding behind Moses Staff, the regime’s most theatrical and destructive façade.
For years, Moses Staff appeared to the outside world as a self-contained hacktivist brand, a militant cyber-propaganda unit releasing stolen Israeli data, encrypting servers, and posting defiant manifestos instead of ransom notes. Security vendors catalogued their campaigns from 2021 onward: the destructive intrusions against Israeli logistics firms, public data dumps, the sudden appearance of custom toolsets like PyDcrypt, DCSrv, and the later StrifeWater RAT. Analysts saw ideology and chaos; what they lacked, until this dump, was administration.
The artifacts contained in Episode 4, spreadsheets, invoices, and hosting dashboards, bridge that gap. Buried in the 0-SERVICE-Service.csv ledger, among the usual lists of domains and ProtonMail credentials, sits a quiet entry: moses-staff[.]io.
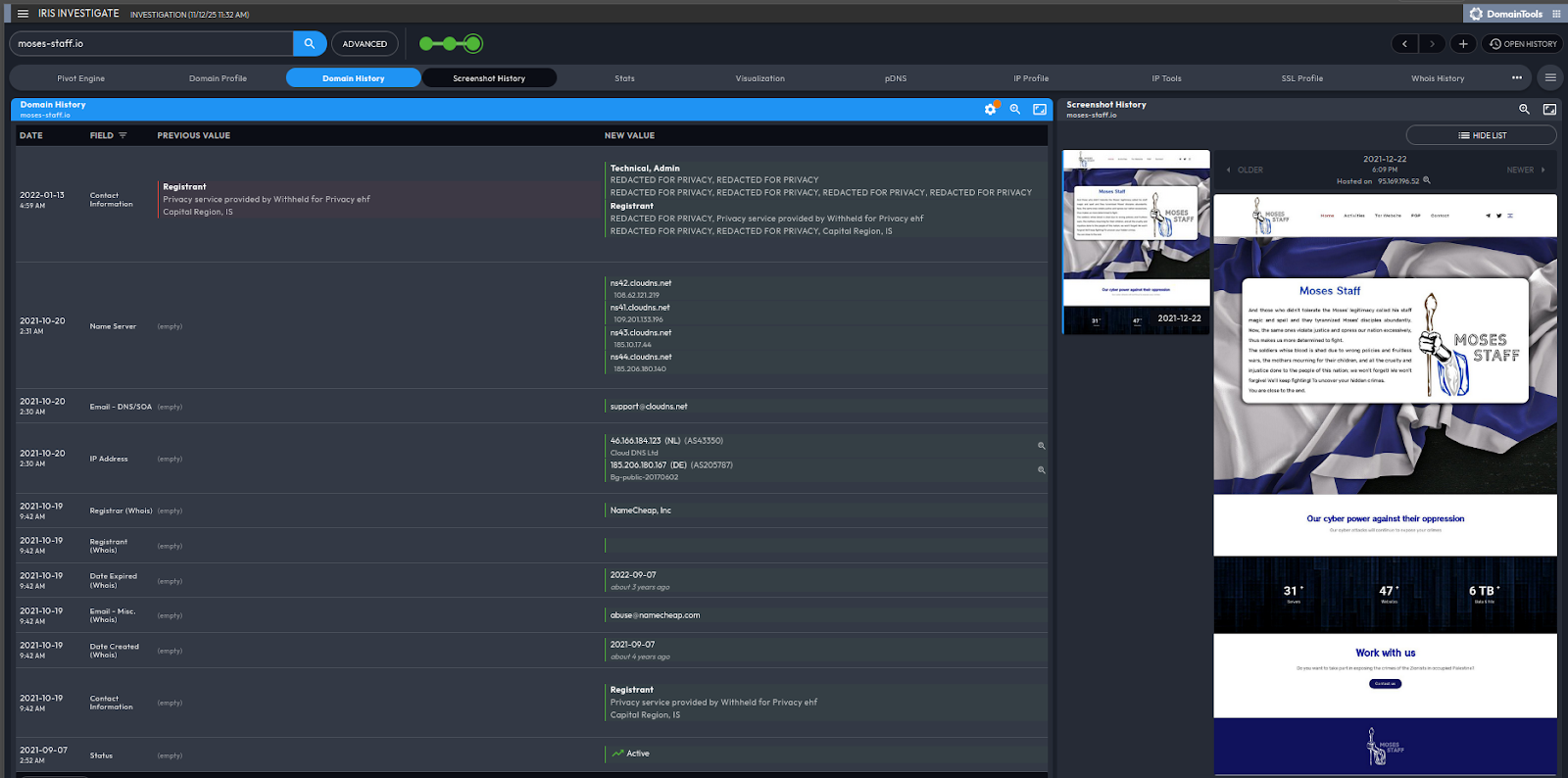
Moses-Staff[.]io Domain WHOIS History 2021-25
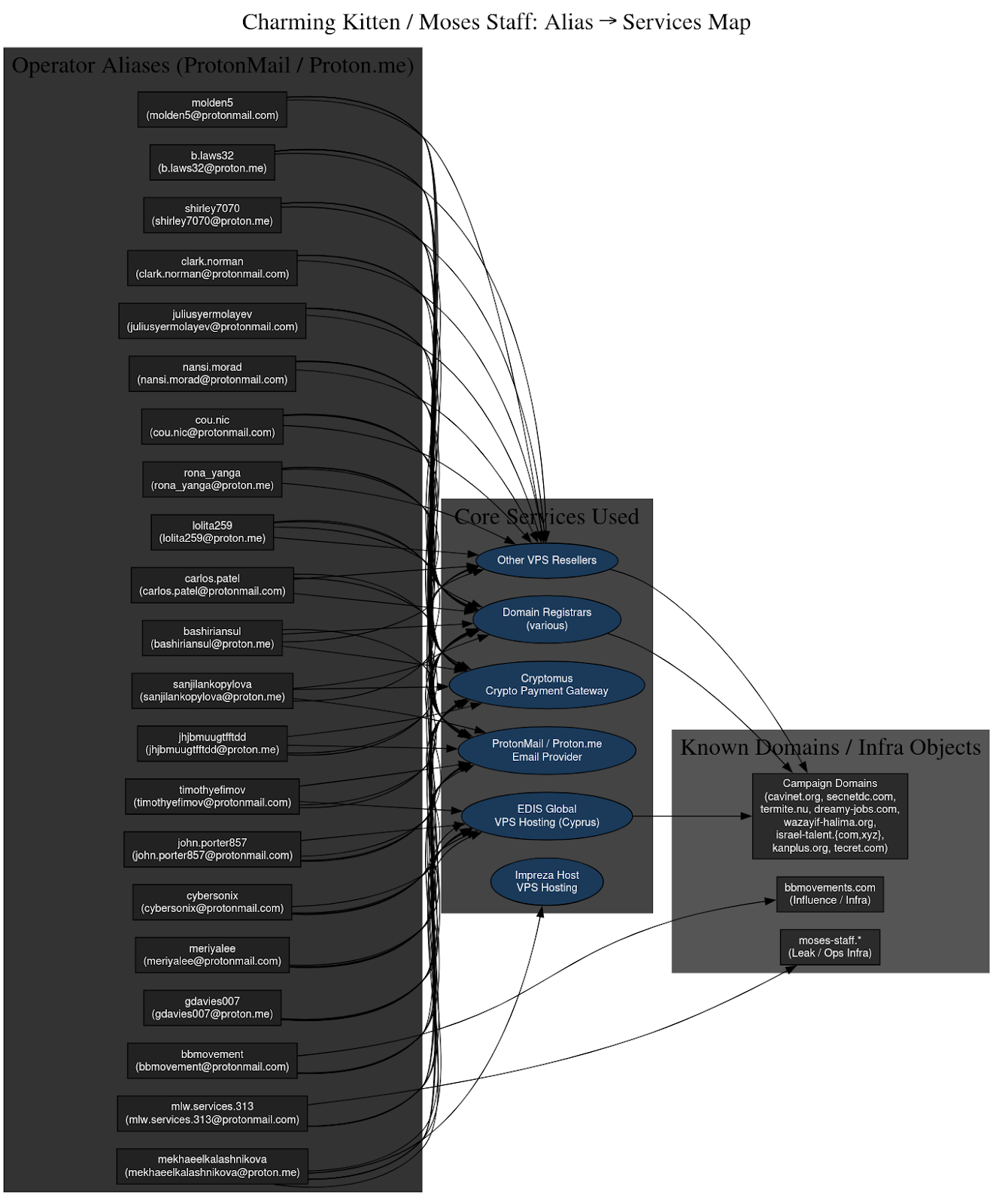
The artifacts are clear, APT 35, the same administrative machine that runs Tehran’s long-term credential-phishing operations, also ran the logistics that powered Moses Staff’s ransomware theatre. The overlap is not merely stylistic , it is infrastructural. The same ProtonMail accounts (bbmovement@protonmail[.]com, meriyalee@protonmail[.]com, cybersonix@protonmail[.]com) appear both in Charming Kitten correspondence and in the hosting ledgers that birthed Moses Staff domains. The same registrars recur, modernizmir.net, TheOnionHost, Namecheap. The same payment conduit repeats, crypto micropayments through Cryptomus routed via Cyprus.
Through these documents, the ideological mask of Moses Staff collapses into the administrative skeleton of APT 35. The supposed hacktivists and the government cyber-unit share not only tooling and targets but also the same accounts-payable system. The propaganda arm and the espionage arm are two products of a single workflow: different “projects” under the same internal ticketing regime.
The campaign record matches the timestamps perfectly. When public vendors documented Moses Staff’s early destructive wave in late 2021, the first lines of the ledger began appearing. As new RAT variants (like StrifeWater) surface in 2023 reports, the invoices show new server rentals across Europe. Each operational evolution leaves a paper trail, a cost code, an invoice number, and a renewal date. The bureaucracy of intrusion is also its audit log.
What these artifacts ultimately reveal is that Iran’s cyber strategy is not improvised, it is administered. Moses Staff is not a rogue collective or an ideological outgrowth; it is the production wing of a well-organized ministry of access. Its campaigns are budgeted, scheduled, and logged with the same diligence as a government infrastructure project. Behind every public defacement sits a clerk who approved the invoice, a supervisor who confirmed the payment, and a system that measures operational tempo in euros, not ideology.
By uniting the visible fury of Moses Staff’s leaks with the quiet paperwork of Charming Kitten’s ledgers, Episode 4 shows how Tehran’s cyber theatre truly operates. It is a play in two acts: the spectacle of resistance on the front stage, and the hum of bureaucracy behind the curtain, where compliance, logistics, and finance keep the revolution online.
Moses Staff Victimology:
For Iran’s cyber apparatus, Moses Staff represents not just a hacking group but a psychological weapon forged for the long war with Israel, a digital insurgency cloaked in ideology and bureaucracy. Between 2021 and 2025, the group’s victim set reads like a cross-section of the Israeli state itself: soldiers, defense engineers, municipal employees, lawyers, and IT administrators, all woven into the same web of exposure. The data shows an operation built to mirror Iran’s doctrine of asymmetric warfare, one where humiliation and disruption can achieve what direct confrontation cannot. Moses Staff’s leaks are not random; they’re curated performances designed to erode trust, advertise reach, and export Tehran’s revolutionary narrative into the digital domain.
The victimology reveals a disciplined targeting strategy. At the top are the institutions that define Israeli power, its military, intelligence services, and defense contractors. Leaks from IDF personnel files and infrastructure maps are as much about psychological warfare as intelligence gain, meant to demonstrate vulnerability in the most sacred strata of the state. Below that tier sit the defense industries, Rafael, ZAHAL suppliers, and Mossad-linked contractors, raided for R&D data, internal communications, and resumes that can feed Iran’s own weapons programs or counterintelligence matrices. The campaign widens further to the civilian layer: the Israel Electric Corporation, small municipalities, and local law firms. These targets serve dual purposes, reconnaissance for future disruption and manipulation of public sentiment. By breaching cloud providers and IT service firms like UST Global Israel, Moses Staff extends reach laterally, turning trusted intermediaries into unwitting vectors.
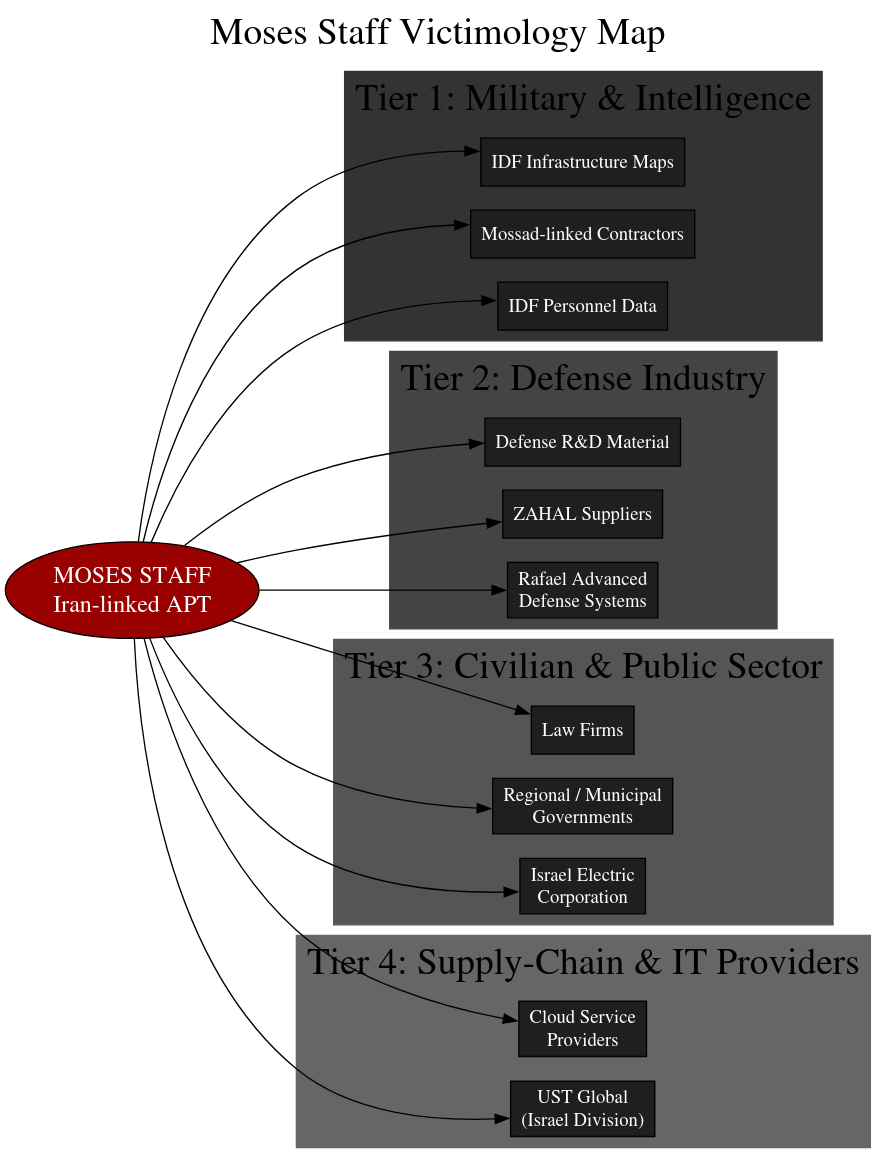
Each compromise serves a strategic function within Iran’s broader playbook. The leaks and defacements broadcast messages of defiance, ‘we see you, we can touch you, and your secrets are ours.’ The exposure of Mossad contractors undermines recruitment, the leaks from law firms plant doubt about client confidentiality, and the focus on infrastructure mapping telegraphs a latent capacity for sabotage. None of this is random opportunism; it’s statecraft through spreadsheets and stolen archives. The operations echo the IRGC’s longstanding emphasis on soft power projection and psychological warfare: destabilize morale, complicate defense logistics, and inject fear into the bureaucratic machinery of governance. What emerges from the Moses Staff campaign is a template for twenty-first century conflict; non-kinetic information operations (IOs) act as extensions of Iran’s regional struggle, executed not with missiles but with leaks, defacements, and the quiet precision of digital attrition.
IRGC Moses Staff Motives: Political and Operational Motives
Moses Staff’s activity fits squarely within Iran’s long-standing doctrine of using cyber power as an instrument of asymmetric statecraft: not to match an adversary blow for blow, but to exploit vulnerabilities, gather intelligence, and exert political pressure without kinetic escalation. Analysts have repeatedly observed Tehran prioritizing disruption, information operations, and psychological effects over outright destructive campaigns, a posture that leverages lower-cost, deniable operations to punch above Iran’s conventional weight (CSIS).
Politically, the leaks, shaming posts, and public data dumps perform several simultaneous functions. They undermine confidence in Israeli institutions, signal capability to domestic and regional audiences, and provide tangible propaganda for allied proxies. Publicly exposing IDF personnel, defense-industry documents, and contractor records is designed to erode morale, complicate recruitment, and broadcast Tehran’s reach, all while avoiding direct military confrontation. This blend of intelligence collection and public humiliation is consistent with Iranian playbooks that combine cyber espionage with psychological operations (SentinelOne).
Operationally, Moses Staff’s target set and methods indicate pragmatic, goal-oriented priorities: collect military and R&D data to inform countermeasures and procurement; map critical-infrastructure networks for later disruption; and pivot through IT service providers to expand access and persistence. The group’s focus on Israeli government, defense, utilities, and support firms points to a layered campaign that values both immediate intelligence yields and the option to escalate to operational sabotage if the political calculus demands (MITRE ATT&CK).
Economically and bureaucratically, these campaigns are run like a government program, producing different incentives and tradeoffs: consistency, traceable procurement and staffing, and an emphasis on service continuity (renewals, vetted resellers, repeatable toolchains) rather than opportunistic monetization. In practice, that means operations are resilient and persistent but also bound by the limitations and inefficiencies of state logistics, which can produce predictable patterns for defenders to track (Sekoia.io Blog).
Taken together, the political objective is coercive image-making and long-term attrition; the operational objective is to create persistent, actionable intelligence and latent disruption options. Moses Staff’s strikes are therefore best understood as a non-kinetic extension of Iran’s regional strategy: to degrade adversary cohesion, buy strategic advantage in intelligence, and shape the information environment without crossing thresholds that would invite overt military retaliation (secalliance.com).
Infrastructure Footprints: Domain Ecosystem and Operational Purpose
The domain ecosystem uncovered in the dump reflects the familiar operational grammar of Iranian threat actors: disposable brands, thematic cover identities, and parallel infrastructure branches tailored to function, mission, and deniability. Rather than a single monolithic C2 cluster, the operators distribute their presence across loosely coupled domains that mimic recruitment agencies, talent portals, religious fronts, job boards, and generic operational shells. The result is an environment where each hostname appears mundane in isolation, yet collectively they form a coherent operational lattice aligned with Tehran’s playbook for cyber operations, influence campaigns, and access maintenance.
The most explicit cluster centers on Moses Staff, whose public-facing leak infrastructure has repeatedly cycled through domains such as moses-staff.io, moses-staff.to, and moses-staff.se. These domains serve as the group’s broadcast layer: data-leak sites, intimidation platforms, and staging points for propaganda distribution. The existence of multiple TLD variants underscores a resilience strategy; when one domain is seized or blocked, the narrative continues uninterrupted via a sibling domain. Certificates, TOR mirrors, and cloud-based mirrors found in the dump suggest a deliberate redundancy model: a propaganda architecture hardened by duplication rather than stealth.
A second cluster revolves around bbmovements.com, which appears tied to earlier Iranian influence operations masquerading as grassroots civic activism. In the dump, it sits adjacent to VPS and ISP management notes, pointing to a broader role than mere messaging: it likely served as a multi-use façade capable of hosting recruitment funnels, persona emails, and low-grade operational staging. This pattern mirrors other IRGC and Ministry of Intelligence (MOIS) information operations, where social-movement branding is blended with technical infrastructure to blur attribution and intent.
Several domains, such as tecret.com, cavinet[.]org, kanplus[.]org, termite[.]nu, and dreamy-jobs.com, show no preexisting footprint in public threat intelligence, which itself is revealing. These domains exhibit the hallmarks of internal-use operational infrastructure: short-lived, singly purposed, and designed to blend into the noisy churn of small business web presence. Their naming conventions track closely with CharmingKitten’s habitual use of career-themed, service-oriented, or vaguely technical branding, perfect for phishing lures, credential-harvesting portals, or as stand-ins for command-and-control endpoints disguised as SaaS tools. Historical WHOIS behavior from similar APT35 operations suggests these domains likely hosted cloned login portals for Microsoft, webmail, VPN, and cloud admin panels.
Another subset, including wazayif-halima[.]org, israel-talent[.]com, and israel-talent[.]xyz, reflects the APT’s long-running interest in targeting Israeli organizations through employment-themed social engineering. These domains mirror job-placement branding common to Israel’s tech and defense workforce, offering a credible lure surface for spear-phishing campaigns aimed at engineers, analysts, and corporate staff. In typical Charming Kitten fashion, the operators diversify across multiple TLDs, .com, .org, .xyz, to increase survivability and widen the radius of mis-typo capture for inbound victims.
The final layer consists of remnants of project-coded infrastructure, Abrahams Ax, kashef, and Bulgaria-based servers, that appear in the operators’ internal notes as hostnames, VPN exit nodes, or C2 pivots. While not domains themselves, the appearance of these labels alongside the real domains anchors the entire set within an organized procurement cycle: operators stand up a domain, bind it to a VPS host, wrap it in an alias persona, and log it in the operational spreadsheet. The repetition of this pattern across all domain families demonstrates that Charming Kitten does not innovate on infrastructure; it iterates. Domains are spun, burned, and replaced through a playbook that prioritizes administrative continuity over sophistication.
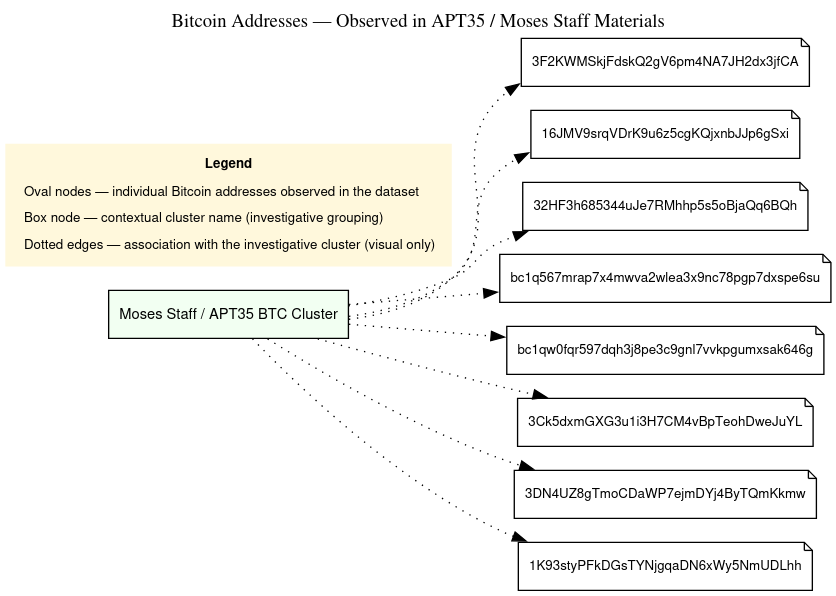
Bitcoin Wallets, Transactions, and Payments: What the Ledger Shows
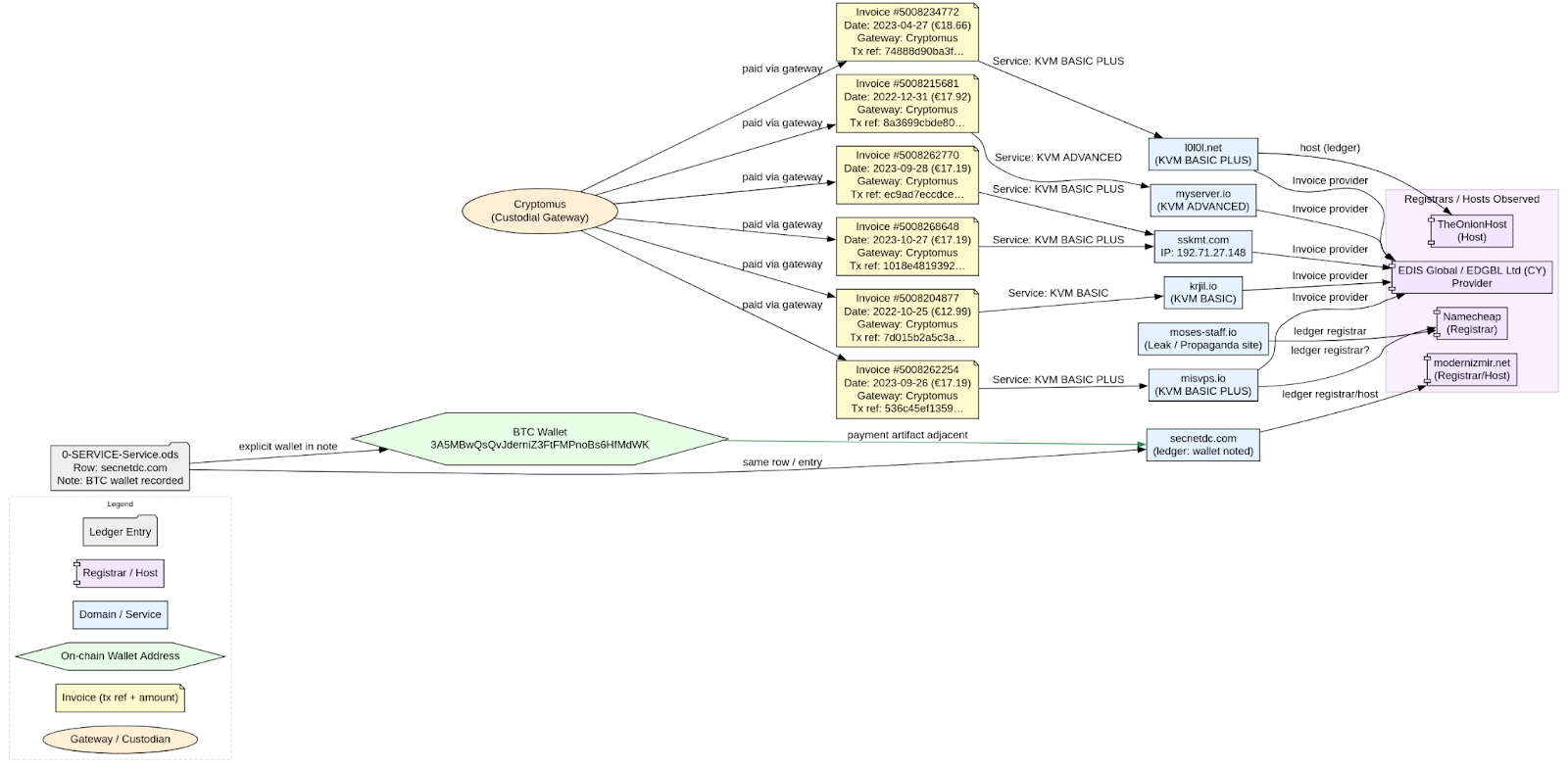
The financial layer in Episode 4 is striking for its simplicity: tiny, repeatable purchases funded via a crypto gate, recorded against obvious operational artifacts. When we shift focus from invoices and VPS to the on-chain fragments and address artifacts embedded in the ledger, three points stand out: small amounts, fragmented transaction provenance, and direct domain ties.
Wallets and Payments:
The network of wallets and transaction fragments aligns closely with the domains and services in use. Within the operational records, domains appear side by side with payment entries, forming a self-contained system of attribution. When an on-chain artifact, such as the address beginning with 3A5M, appears, it sits directly beside a corresponding hosting entry like secnetdc.com, creating a syntactic and functional pairing between cryptocurrency movement and specific infrastructure assets.
A second class of payment evidence emerges through Cryptomus transaction fragments. Though these fragments conceal the actual blockchain addresses, their repetition across multiple entries points to a common gateway and a stable set of receiving clusters. This consistency implies that crypto flows were routed through a single, reusable payment processor, maintaining continuity across purchases while obscuring direct traceability.
The financial behavior itself is telling: transactions are deliberately modest, typically between €12 and €18, suggesting micro-purchases calibrated to sustain long-term infrastructure while remaining invisible to financial compliance systems. Their scale minimizes AML or OFAC scrutiny and blends seamlessly with ordinary online commerce.
Taken together, the recurring use of the Cryptomus gateway and the EDIS reseller reveals a structured procurement method. Cryptocurrency payments are funneled into a limited number of merchant endpoints, while the ledger documents the dispersed operational footprint, domains, virtual servers, and service nodes. The isolated appearance of an explicit on-chain address signals occasional lapses in operational hygiene, providing a rare and valuable foothold for blockchain correlation and broader attribution.
The Operational Collection Wallet: 1K93styPFkDGsTYNjgqaDN6xWy5NmUDLhh0
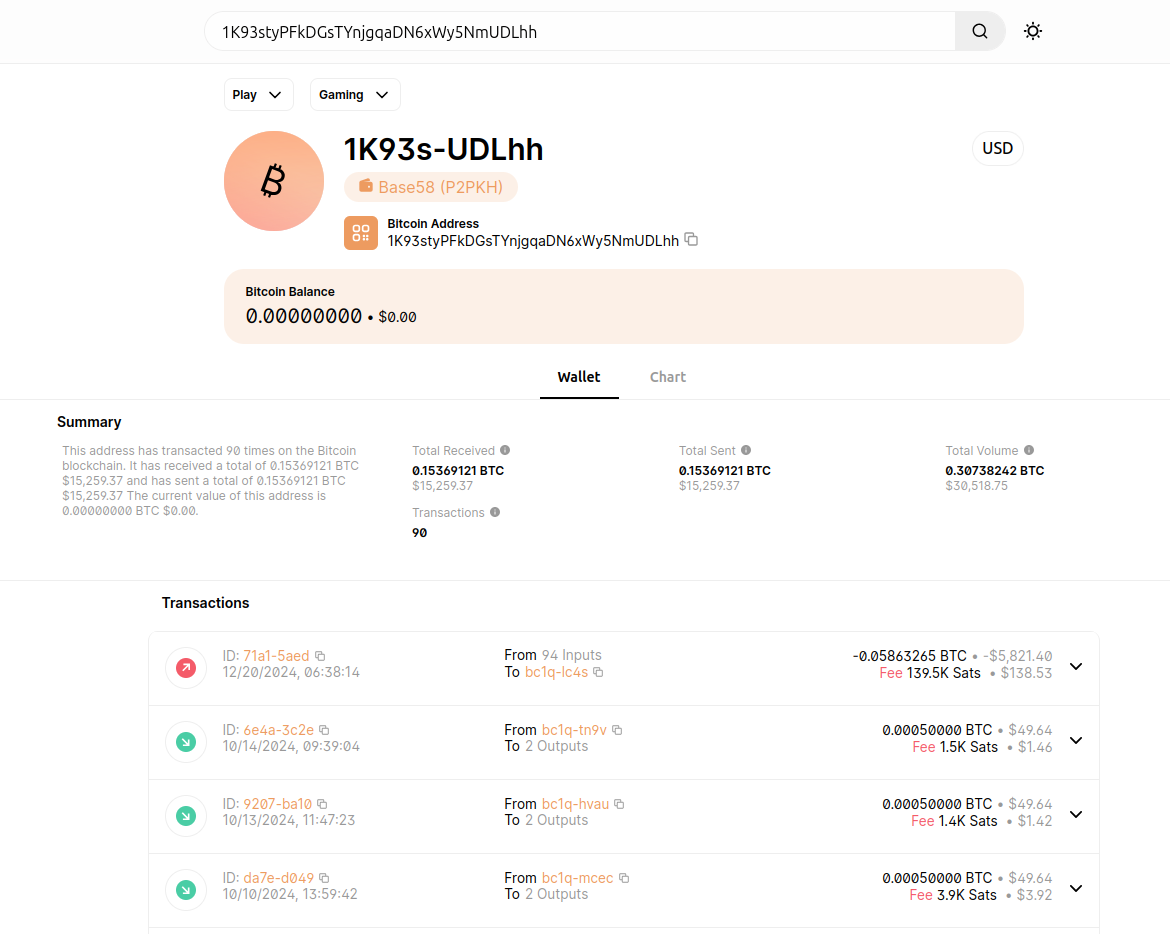
The above Bitcoin address, 1K93styPFkDGsTYNjgqaDN6xWy5NmUDLhh, is a central wallet that, according to the snapshot, transacted 90 times on-chain and received 0.15369121 BTC (displayed USD equivalent $15,259.37) before being fully emptied. The dashboard reports a total sent value identical to the total received (0.15369121 BTC), a total lifetime volume of 0.30738242 BTC (~$30,518.75), and a current on-chain balance of 0.00000000 BTC. That combination, many small transactions in, periodic consolidation and an ultimately zero balance, is a classic pattern for a service/collection wallet used to aggregate micro-payments and forward them onward.
Transaction-level indicators support that reading. The above image shows multiple incoming micro-payments of 0.0005 BTC (and similar small amounts) and at least one large consolidation spend (an outgoing TX of -0.05863265 BTC that lists 94 inputs) with a relatively large miner fee (the UI shows a fee of ~139.5k sats, displayed ≈ $138.53). Ninety total transactions with dozens of tiny inputs plus multi-input consolidation spends strongly suggest the wallet accumulated many small (Unspent Transaction Output’s typical of customer payments, routing from mixers, or automated payouts) UTXOs and then periodically consolidated or forwarded those funds in bulk.
Operational interpretation
- Role: collector/aggregation wallet for micro-payments (or small receipts) rather than a long-term cold storage or exchange custody address.
- Behavioral signals: repeated small inbound amounts (0.0005 BTC) indicate either automated service payments, funneling from many upstream payers, or staged outputs from a mixing service. The later consolidation with many inputs shows someone consolidated value — either to forward to a service/exchange or to obfuscate origin via coinjoins/mixers.
- Current state: emptied at snapshot time, meaning funds were forwarded elsewhere; those downstream hops are the logical next step to trace for attribution or cash-out points.
Operational Tradecraft: The Business of Operating an Intelligence Operation
The operational material in the dump turns what might seem like scattered activity into a clear and repeatable workflow. Each cycle begins with the creation of a ProtonMail persona, followed by the registration of a domain crafted for a specific campaign or cover purpose. Once the domain is secured, the operators purchase a low-cost VPS from a European reseller, pay through a cryptocurrency gateway, log the ticket number and credentials in the shared service ledger, and then deploy a phishing page or command server. Different aliases perform the steps, but the method never changes. What appears improvised from the outside is, in fact, a stable routine executed with bureaucratic discipline.
Shifts in alias or billing identity do not disrupt the choreography. A hosting purchase tied to “Maja Bosman” in December 2022 follows the same pattern as a purchase tied to “Levis Cross” in April 2023, with identical hosting tiers, vendors, price bands, and reliance on the same crypto payment rails. The consistency across time and personas shows that these are not isolated procurement events but templated cycles aligned with the rows preserved in the service ledger. The repeated use of EDIS Global in Cyprus as a hosting provider, combined with Cryptomus as the payment conduit, reveals a supply chain optimized for pseudonymous acquisitions. The operators gain anonymity, yet each transaction produces a traceable fragment that links the infrastructure back to the underlying workflow.
The ledger entries tie the entire system together. Domains such as sskmt[.]com and misvps[.]io were purchased using the same KVM BASIC PLUS hosting packages priced around seventeen euros per month, and the same price points, SKUs, and hosting strings appear throughout the spreadsheet. These recurring signatures allow investigators to follow a direct path from procurement to deployment, exposing an industrialized process in which inexpensive VPS instances are acquired in small units, paid for with micro-crypto amounts, cataloged in a shared sheet, and activated as persistent infrastructure for Charming Kitten and Moses Staff campaigns. The paperwork is not peripheral; it is the blueprint of the operation, revealing the workflow, the dependencies, and the pressure points where the infrastructure can be disrupted.
Operational Tradecraft: Creation and Use of Aliases and Email Addresses
The group’s operational tradecraft is clearest in the way it manufactures and discards identities. Each alias exists only long enough to perform a single task such as registering a domain, submitting a support ticket, or purchasing hosting. These personas are not cultivated, expanded, or reused. They are burned immediately after use, leaving only a fleeting entry in a provider’s logs. Historical WHOIS patterns confirm this discipline. While the domains are registered privately, the surrounding metadata shows that none of the names or ProtonMail addresses reappear in earlier domain ownership records, public forums, credential dumps, or any other online history. Each identity is created for the lifespan of a single procurement event and then abandoned.
The names themselves follow a deliberate aesthetic. Some resemble Israeli contractors, others Russian freelancers, American small business owners, or European students. This diversity helps the operators blend into the global background noise of hosting and domain purchases. ProtonMail provides the perfect backbone for this approach because it is widely used across regions where these personas would plausibly exist. Each alias receives a fresh ProtonMail address formatted to look like an ordinary personal account, active only long enough to complete registration tasks or answer provider messages. The absence of recurrence across the broader internet reflects a tightly controlled identity-lifecycle model.
This strategy creates airtight compartmentalization. A persona used for one domain is never used for another, and no name ever appears across different clusters of hosts or campaigns. To hosting providers, the activity looks like a scattered set of unrelated customers making small purchases. To an investigator with access to the internal ledgers, the pattern resolves into a single workflow: routine creation of ProtonMail inboxes, rapid procurement of low-cost infrastructure, strict one-time use of identities, and immediate disposal. The result is an identity management system engineered to eliminate persistent markers, frustrate long-term correlation, and make each procurement step appear isolated despite being part of a unified operational machine.
Disposable Identities and Their Intersection with Domains, Wallets, Timelines, and Ledger Patterns
The group’s disposable aliases only make sense when viewed alongside the four systems they touch: domain acquisition, cryptocurrency payments, campaign timing, and the shared service ledger. Each fabricated persona appears briefly at the junction of these pillars, completing a single procurement action before vanishing. While the names leave almost no independent footprint, the artifacts they generate across these other systems reveal how structured and interconnected the operation truly is.
The domain clusters form the first pattern. Each one consists of a small burst of registrations made within minutes or hours of each other, all protected by private WHOIS. Every cluster is assigned its own set of one-time identities, ensuring that no alias appears across separate groups of domains. The financial layer reinforces this structure. Even though payments are routed through Cryptomus, recurring transaction fragments and micro-payments align with specific hosting renewals and activation dates. These fragments persist long after the aliases are discarded, creating durable technical markers that link procurement events to infrastructure timelines.
The final coherence comes from the campaign chronology and the service ledger. Domains and VPS instances often sit dormant for weeks after being purchased, then activate shortly before a phishing campaign or intrusion attempt. This gap between procurement and use reduces exposure while keeping the workflow efficient. The ledger ties all of this together. It records hosting SKUs, timestamps, credentials, and reminders that match the payment logs and vendor records, proving that each alias is simply a single-use instrument within a unified operational system. Taken together, the four pillars show how the group balances anonymity with internal discipline: identities disappear instantly, but the infrastructure they trigger follows a consistent and well-documented lifecycle.
In this way, the group is able to create an appearance of scattered and unrelated activity across the internet while maintaining a very tight internal process. The aliases provide camouflage. The infrastructure tells the real story.


Why This All Matters
In the world of cyber threat intelligence, attention often fixates on the glamorous front end of intrusion, the zero-days, the implants, the command-and-control frameworks. But what the APT35 and Moses Staff leaks expose is the hidden half of cyberwarfare: the bureaucratic engine that funds, equips, and sustains it. These files strip away the mythology of elite operators and reveal a machine that runs on invoices, crypto payments, and shared spreadsheets. What makes this revelation significant isn’t just what Tehran is hacking, but how it keeps hacking, through systems of procurement, payment, and administration that mirror legitimate state accounting.
Each transaction tells a story of adaptation under constraint. With Iran’s access to global finance curtailed by sanctions, operators have built a parallel economy of intrusion: crypto gateways like Cryptomus and NowPayments act as anonymized intermediaries; small-scale European VPS resellers such as EDIS Global and Impreza Host become unwitting facilitators; and administrative ledgers track every euro spent as if it were a budget line in a ministry. The pattern reveals a sanctioned nation’s workaround, a form of gray-market logistics that turns the limitations of isolation into operational discipline. In this system, anonymity isn’t a byproduct of evasion; it’s a standardized function, designed to allow IO operations to persist without disruption.
By documenting the minutiae, the BTC addresses, the service tickets, the 12-euro hosting payments, this dump transforms our understanding of Iranian cyber capability. It’s not the product of rogue ingenuity but of institutional persistence, a bureaucratic adaptation of espionage to economic isolation. Cryptomus and similar payment rails effectively launder state funding into operational liquidity, while European resellers provide the legal and infrastructural scaffolding that make Tehran’s influence operations indistinguishable from ordinary e-commerce. In that sense, the lesson of these leaks is strategic: cyber power is not just built on code or exploits but on supply chains, accountants, and renewal schedules. The spreadsheet, not the malware, is what keeps Iranian operations online.
APPENDIX A: IOC’s
Operations Domains:
- bbmovements.com
- cavinet.org
- secnetdc.com
- tecret.com
- termite.nu
- dreamy-jobs.com
- wazayif-halima.org
- israel-talent.com
- israel-talent.xyz
- kanplus.org
MOSES STAFF DOMAINS:
- moses-staff.io
- moses-staff.se
- moses-staff.to
Recurring Hosting Providers:
- EDIS Global (Limassol, Cyprus) 57169
- CloudDNS nodes linked to moses-staff infrastructure AS203391
- “Server Samane” (internal operator label) AS16509
- Bulgaria-based VPS nodes (3CX / VPN / “Karaj” references) AS21340
Email Addresses and Cover Names:
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
Aliases:
- Maja Bosman
- Levis Cross
- Sheldon Bayer
- Edgar Evseev
- Mekhaeel Kalashnikova
- Shirley Bishop
- Clark Norman
- Julius Yermolayev
Bitcoin Wallets:
- 3F2KWMSkjFdskQ2gV6pm4NA7JH2dx3jfCA
- 16JMV9srqVDrK9u6z5cgKQjxnbJJp6gSxi
- 32HF3h685344uJe7RMhhp5s5oBjaQq6BQh
- bc1q567mrap7x4mwva2wlea3x9nc78pgp7dxspe6su
- bc1qw0fqr597dqh3j8pe3c9gnl7vvkpgumxsak646g
- 3Ck5dxmGXG3u1i3H7CM4vBpTeohDweJuYL
- 3DN4UZ8gTmoCDaWP7ejmDYj4ByTQmKkmwU
- 383j9rbvXyf4ZVaTPLPB1QfpkDJZfMEziG
- 3MCyrpDmEUAWjx5rg5L3uqcZDux6e9Ns78
- bc1qmasss9tj2wcyr8vyjajhn8qu9xr3g9hl0r0ne7
- 34bvn64Hn9rgwahJJVveh8xTgseLtY8KpJ
- bc1q2peh44qqjx9xg32xqfwzmrcrj42lean57vg6j4
- 3BMbdmfc9sKKEtX9EFKbxbS75xTuKEzRjF
- 35eL5XLnKWbpJPdQGULvqhQpNQEkBSPisN
- bc1qxjmw2lknnne5hr0c4va2fjx0kzc9la4vhuaqex
- 13Ue2i4Pombmd1NUGKgT8P1SCm8jw5F2Kj
- 1K93styPFkDGsTYnjgqaDN6xWy5NmUDLhh
- 19cChyRjku4zMKPr7PtkNSAdp9JE6AmiL2
- 1HcPgNVrb7RvYkaGSu286qz2WF5UVBPP1R
- 38Ai21L6mt7Qe2jnpxAZvjTLqKCYfjx9Am
- bc1qtf2a865s7ncxcsdcwee8yyyqjhhkk9nn7ww98q
- 32LvatxLwVfxpteiJc14HCyDDv2t2BRfj5
- 31we2wugu5z7Mc3irnmZu9H7rXPrEqsuTf
- 3Fv1X3we164eiBkme9wzHDU1iHpXuWcx8h
- bc1qfzke9vknxdvtm6yrkru3ddzfl74ducx7s6rke2
- 33PMgvq7HN8gdpd82WFCxKpVtsnSUWbLFx
- bc1q9a8k39xpxeflsetdw92mzd98kg7gpcwsm2malh
- bc1qpq0pk3xskqs70wg9werg3ypl8e255euzd5g4nq
- 391baZHDES5TvotnYSnWwqnyYDXf2taWWb
- 38SvFcEVRsfADhuxk7FS1p3TJfXYHewzGe
- bc1q7xk8vk2cttvz92xjh2r4tfry0964rvvedeqpls
- 17cHK7neWyAq1imHgjc6wKqoX3gqPcUx4N
IP Clusters:
- 128.199.237.132 – DigitalOcean (WordPress scanner patterns)
- 212.175.168.58 – Türk Telekom
- 212.12.178.178 – Nour Communication Co. Ltd, Saudi Arabia
- 1.235.222.140 – KRNIC (Korea)
- 109.125.132.66 – Pishgaman Tejarat Sayar DSL, Iran
- 83.96.77.227 – Fast Communication Co. Ltd, Kuwait
MITRE ATT&CK Technique Mapping
Aligned to Charming Kitten / Moses Staff Identity, Infrastructure, and Operational Tradecraft
TA0043 – Reconnaissance
T1595 – Active Scanning
Operators stage VPS nodes to probe target systems and deliver phishing infrastructure.
T1598 – Phishing for Information
Domains such as dreamy-jobs.com, israel-talent.com, and wazayif-halima.org are designed to lure specific industries for credential harvesting.
TA0001 – Initial Access
T1566 – Phishing
Job-themed, credential-harvest pages deployed on low-cost VPS nodes purchased through EDIS and Impreza Host.
T1078 – Valid Accounts
Harvested credentials fed into further access attempts, often timed shortly after domain activation.
TA0002 – Execution
T1204 – User Execution
Operators deploy phishing pages requiring victim interaction (login forms, document lures).
TA0003 – Persistence
T1098 – Account Manipulation
Use of harvested credentials to maintain foothold where applicable.
T1136 – Create Account
Single-purpose ProtonMail inboxes created for procurement (operational persistence at the infrastructure layer).
TA0004 – Privilege Escalation
(Not a focus of the dump, but implied in reference to Charming Kitten’s broader history of targeting Microsoft Exchange and Ivanti appliances.)
T1068 – Exploitation for Privilege Escalation
TA0005 – Defense Evasion
T1036 – Masquerading
Use of aliases that imitate Israeli, Russian, European, and American names; job-themed domains; fake recruitment brands.
T1070.004 – File Deletion
Use of single-use ProtonMail identities deleted or abandoned immediately after procurement.
T1112 – Modify Registry
(Not directly in the dump, but historically used in Moses Staff post-exploitation phases.)
T1027 – Obfuscated/Encrypted Files
TOR mirrors, private WHOIS, and encrypted communication channels.
T1564.003 – Hidden Artifacts: Disposable Email Identities
Strict one-time usage of procurement emails to prevent cross-cluster linkage.
TA0006 – Credential Access
T1056 – Input Capture
Credential-harvesting login portals deployed on purchased domains.
T1110 – Brute Force
Occasional activity against Israeli organizations (documented in public reporting of Moses Staff operations).
TA0007 – Discovery
T1087 – Account Discovery
Infrastructure scans for valid credentials through job-themed lures.
T1046 – Network Service Scanning
EDIS-hosted servers used to probe Israeli networks prior to planned intrusions.
TA0008 – Lateral Movement
T1021 – Remote Services
Use of harvested valid accounts through VPN portals and cloud dashboards.
TA0009 – Collection
T1530 – Data from Cloud Storage
Compromises of cloud/email providers in the civilian tier.
T1114 – Email Collection
Phished credentials provide mailbox access enabling data theft.
TA0011 – Command and Control
T1071 – Application Layer Protocol
C2 nodes hosted on low-tier VPS servers via HTTP(S).
T1105 – Ingress Tool Transfer
Payloads staged on purchased domains and KVM BASIC VPS instances.
T1568.002 – Dynamic DNS
Operators rotate hosts rapidly; CloudDNS references seen around Moses Staff mirrors.
TA0010 – Exfiltration
T1048 – Exfiltration Over Alternative Protocol
TOR mirrors used for anonymity during leaks.
T1567.002 – Exfiltration to Web Services
Leak sites operated under moses-staff.io, .se, .to.
TA0040 – Impact
T1491 – Defacement / Psychological Operations
Public leak sites intended to intimidate Israeli institutions.
T1485 – Data Destruction
Moses Staff’s destructive toolchain, already known in historical operations.
Supporting Operational Tradecraft Mappings
Identity Infrastructure Techniques
T1585.001 – Establish Accounts: Email Accounts
Single-use ProtonMail addresses for procurement.
T1583.003 – Domain Registration
Clusters of domains purchased for credential harvesting and campaign staging.
T1583.001 – Acquire Infrastructure: Virtual Private Servers
Routine procurement from EDIS, Impreza Host, Bulgarian VPS sellers.
T1586.002 – Compromise Accounts: Webmail
Credential theft from phishing operations.
Financial / Payment–Layer Techniques
T1586 – Obfuscation via Payment Providers
Cryptomus used to anonymize infrastructure transactions.
T1587 – Develop Capabilities
Infrastructure provisioning using micro-crypto payments in a repeatable pattern.
T1599 – Network Boundary Bridging
By paying through crypto and using global VPS hosting, operators evade regional filtering.


