Security Research
for the Community
Recently Added

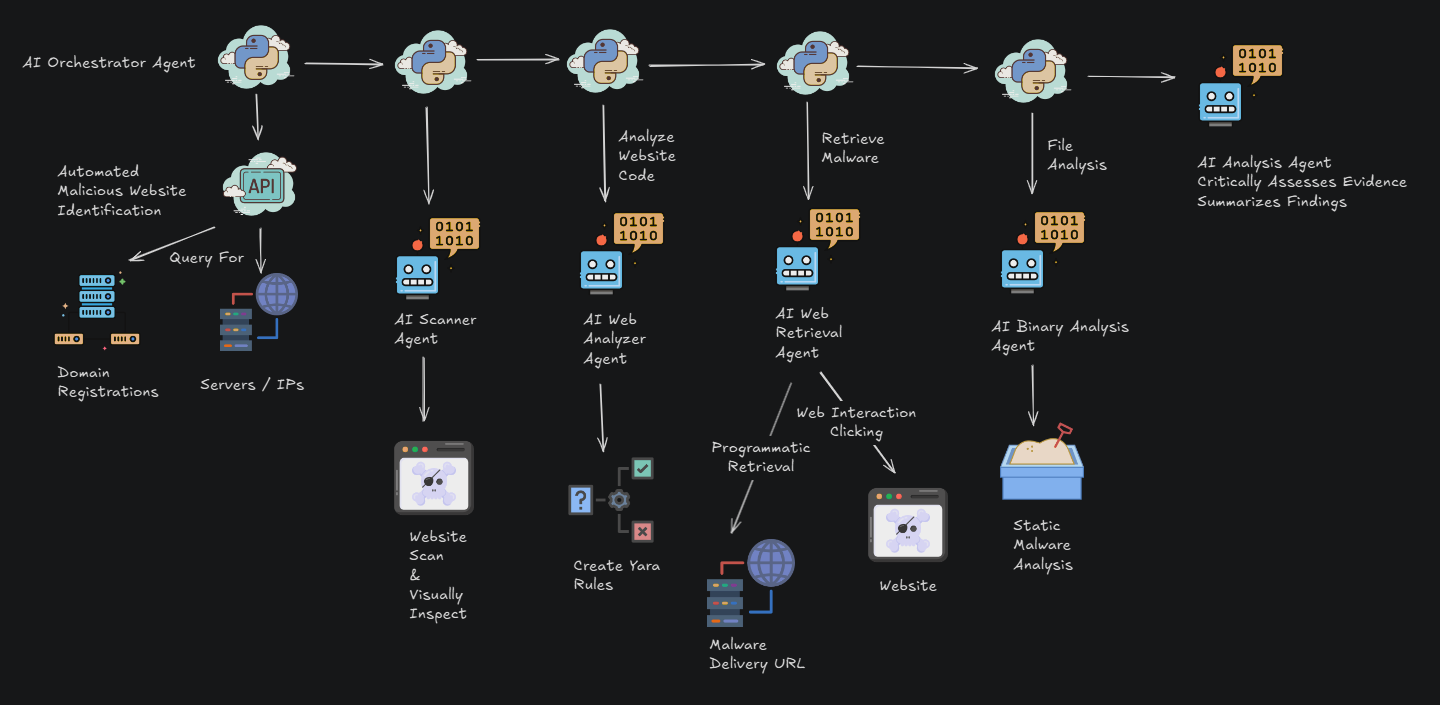
Leaked Knownsec documents reveal China’s cyberespionage ecosystem. Analyze TargetDB, GhostX, and 404 Lab’s role in global reconnaissance and critical infrastructure targeting.
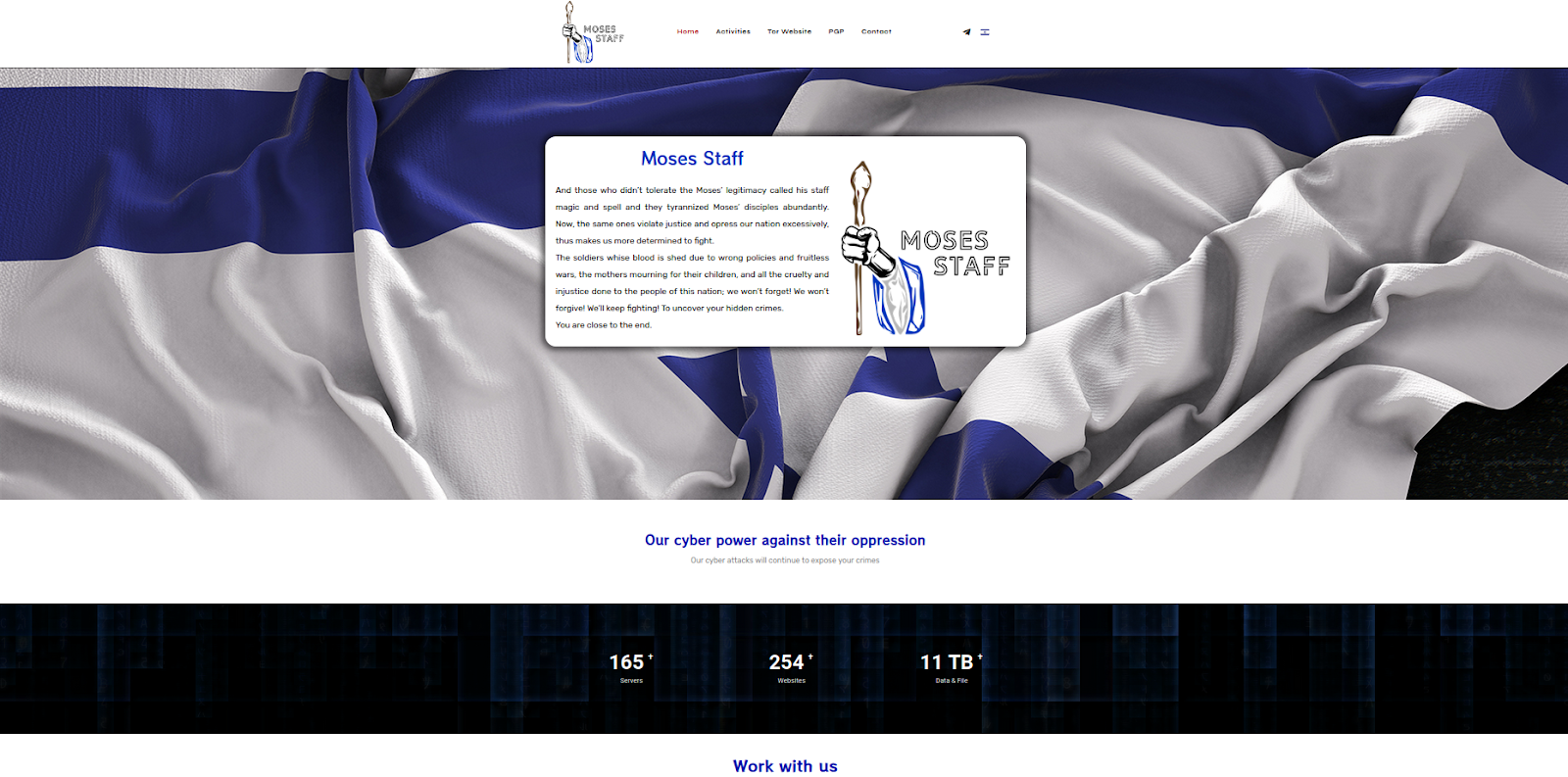
APT35/Charming Kitten's leaked documents expose the financial machinery behind state-sponsored hacking. Learn how bureaucracy, crypto micro-payments, and administrative ledgers sustain Iranian cyber operations and link them to Moses Staff.
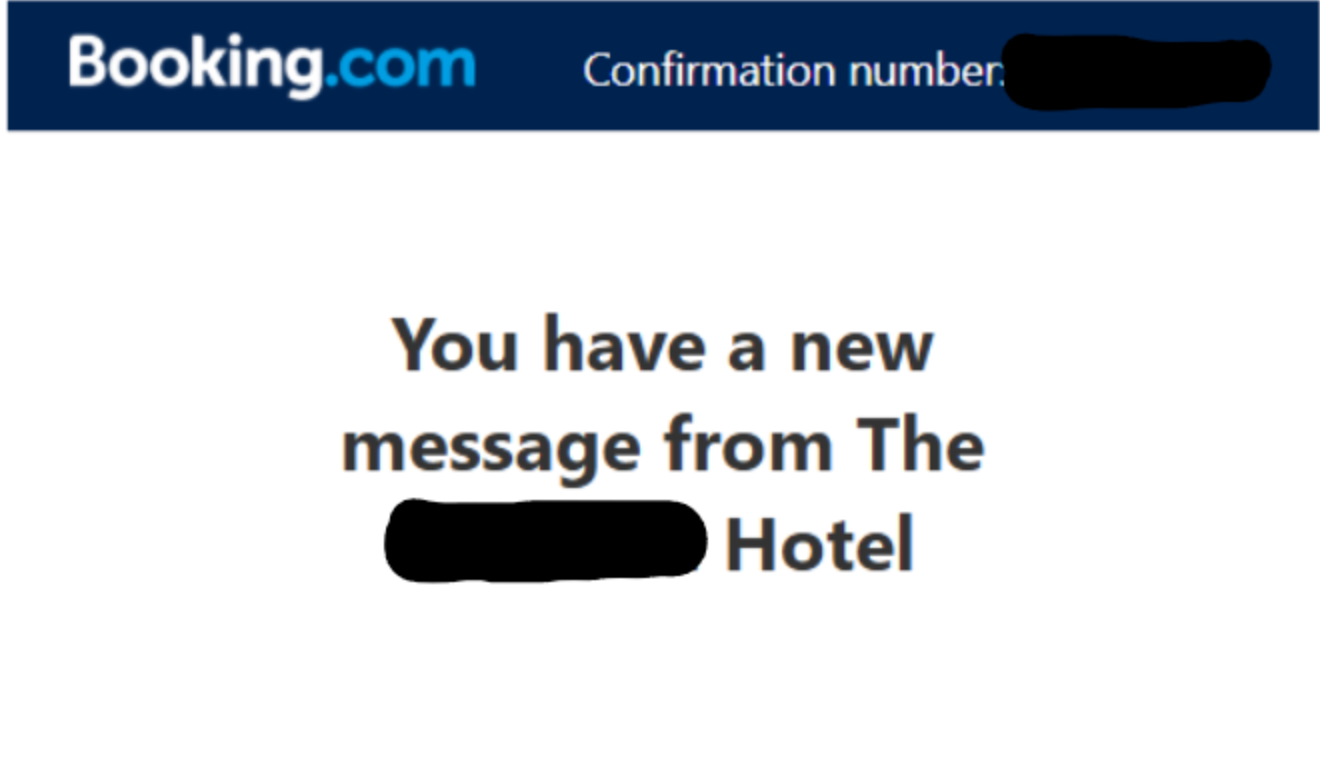
New B2B2C supply chain attack targets Booking.com customers. Attackers are compromising hotel accounts to send & "verify or cancel" phishing messages with dynamic booking data. Learn how to spot these fake domains and protect your payment info.


APT35/Charming Kitten's leaked documents expose the financial machinery behind state-sponsored hacking. Learn how bureaucracy, crypto micro-payments, and administrative ledgers sustain Iranian cyber operations and link them to Moses Staff.

New B2B2C supply chain attack targets Booking.com customers. Attackers are compromising hotel accounts to send & "verify or cancel" phishing messages with dynamic booking data. Learn how to spot these fake domains and protect your payment info.