Evolution of Infrastructure and AI-Powered Security Analysis
Summary
Since January 2025, DomainTools Investigations has been tracking a large cluster of malware delivery domains that’s been active since June 2023. We’ve published three reports on the cluster in the past 11 months, and in the latest Part III report in July 2025 we surmised that the cluster comprised over 2,800 domains. Since then, we’ve observed more than 1,900 additional malware delivery domains we suspect are tied to the same super cluster. This high volume of malware delivery domains makes for an excellent case study of AI facilitated analysis to take on the burden of website analysis, binary analysis and detection authoring.
This report provides updates on the cluster following Part III and introduces a new experimental approach to defensive hunting and tracking malware delivery clusters such as the one described through the deployment of agentic AI systems that enable analysis workflows at the scale and speed necessary to match threat actor operations. Using a combination of task based AI orchestrator and sub agents, one security researcher achieved a 10x improvement in analysis throughput (assuming the websites were resistant to traditional solutions) with agents tirelessly processing over 1,900 malware delivery websites in the time traditionally required for roughly 200-400 manual investigations.
At a glance, the threat actor continues to demonstrate remarkable persistence and scale in their malware delivery operations, maintaining a wide variation in infrastructure deployment, lure sites, and malware delivery, which consistently appears to be targeting Chinese-speaking users across the globe. Our analysis from May to November 2025 reveals notable operational evolution across distinct clustering patterns and continued spoofing of common software download websites as lures to deliver trojans and credential stealers. However, the same operational security weaknesses prevail in the form of highly leveraged SOA emails, tracking IDs for SEO manipulation, unique registrant names, and relatively unique infrastructure combinations. These factors allow for distinct campaigns to be linked together, forming the super cluster of approximately 5,000 malware delivery domains that has been active since 2023.
Sample of the malware delivery websites spoofing common application download pages:


Part 1: Campaign Evolution Analysis
1.1 Infrastructure Evolution
At a high level, the actor's infrastructure has undergone an overall fragmented evolution with a few exceptions since our July 2025 report (Part III), which documented 2,800 domains created from January to May 2025. Current analysis indicates that approximately 1,900 additional domains have been created in the period from May 2025 to November 2025.
Initially, domain hosting infrastructure was highly consolidated prior to May 2025, but this gradually gave way to diversification in August. By November, the infrastructure fractured further into smaller, more fragmented clusters with a focus on localization and operational security improvements as well as leveraging domestic Chinese registrars and randomized domain naming patterns.
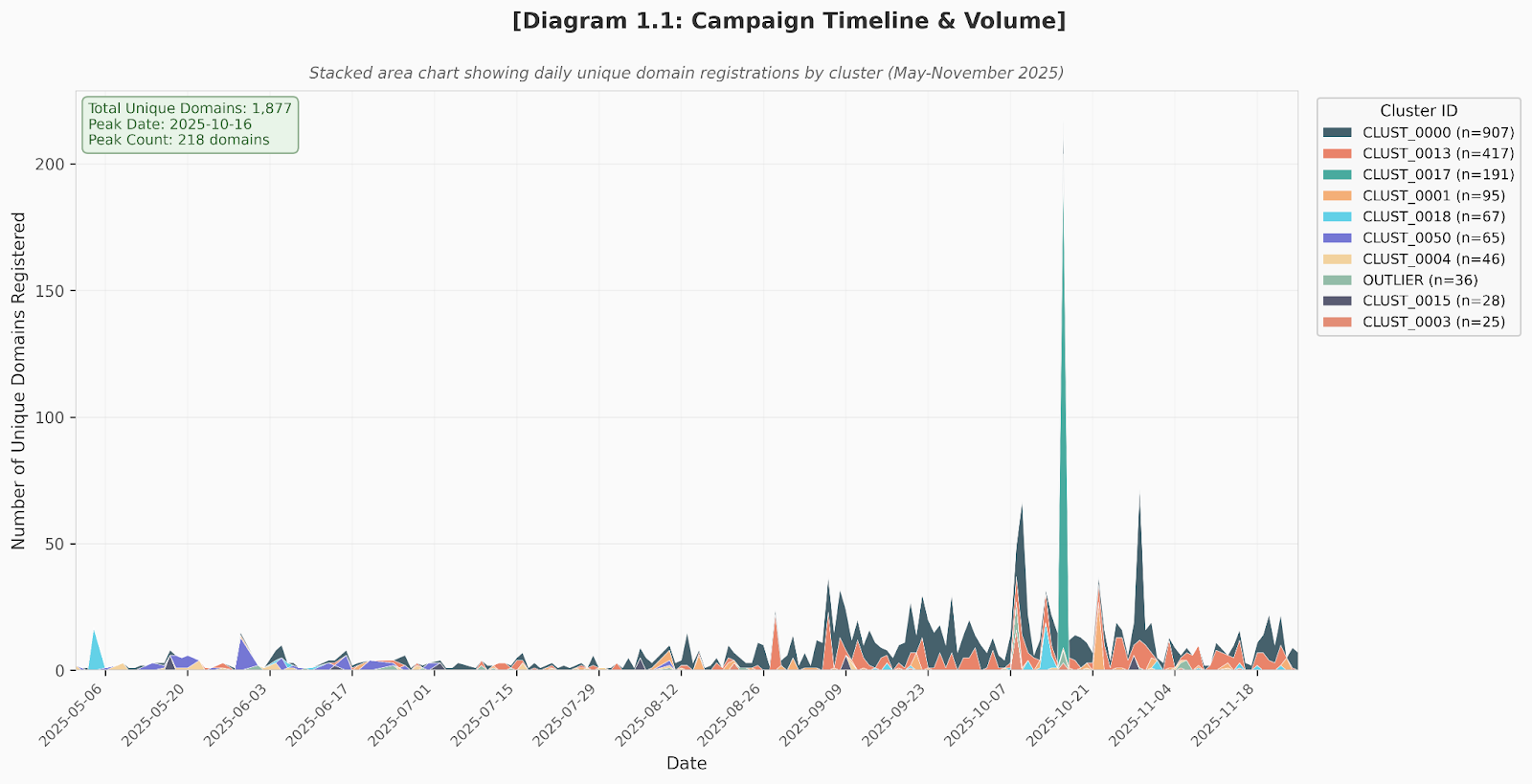
The infrastructure evolution appears to demonstrate distinct transitions with a particular surge in overall variability from August to November:
Consolidated (May-July 2025)
- Primary infrastructure: Alibaba Cloud Hong Kong
- Registrar: WebNIC (98% concentration)
- Focus: Chrome, Chinese VPN, and WPS Office spoofs
Diversified (August-September 2025)
- New targeting: Signal and Telegram messengers
- Domain clustering tightens (higher specificity scores)
Localization (October-November 2025)
- Majority use of Chinese domestic registrars
- 四川域趣网络科技有限公司 becomes primary registrar
- Random domain naming patterns emerge
- Possible OPSEC improvement attempts
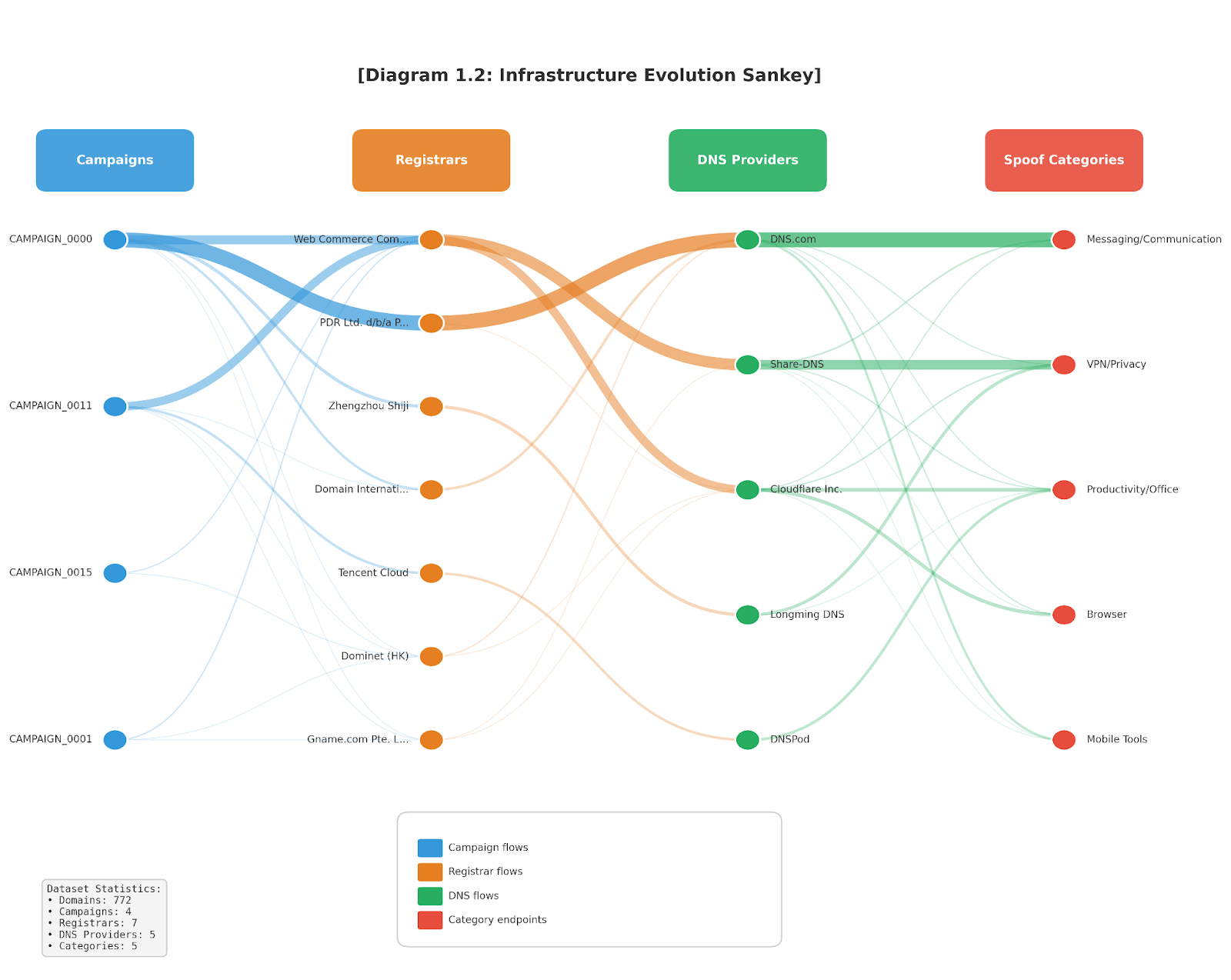
[Diagram 1.2: Infrastructure Evolution Sankey] Flow diagram showing: Campaigns → Registrars → ISPs → Countries
1.2 Campaign Comparison Matrix

1.3 Operational Adaptations
Comparing domain registration trends from January through June 2025 with June through November 2025, several adaptations emerged:
Infrastructure Resilience
- Reduced reliance on single ISPs (from 90% to 40% maximum concentration)
- Geographic distribution across 5 countries (previously 3)
- Registrar diversification: 8 unique registrars vs 3 previously
OPSEC Improvements
- Increased use of privacy protection services
- Shorter domain active lifespans (average 30 days vs 60 days)
Technical Evolution
- Enhanced anti-automation JavaScript (20+ unique evasion signatures)
- Multiple packer usage (VMProtect, ASPack, ASProtect, MPRESS)
- Certificate pinning in Cloudflare-hosted domains
Part 2: Technical Threat Analysis
2.1 Malware Delivery Evolution
Analysis of 2,393 domains reveals continued targeting of Chinese-speaking users through spoofing campaigns. The actor maintains their core tactic of mimicking legitimate software download sites while expanding their portfolio.
[Diagram 2.1: Domain Naming Word Cloud] Word clouds showing naming patterns by campaign
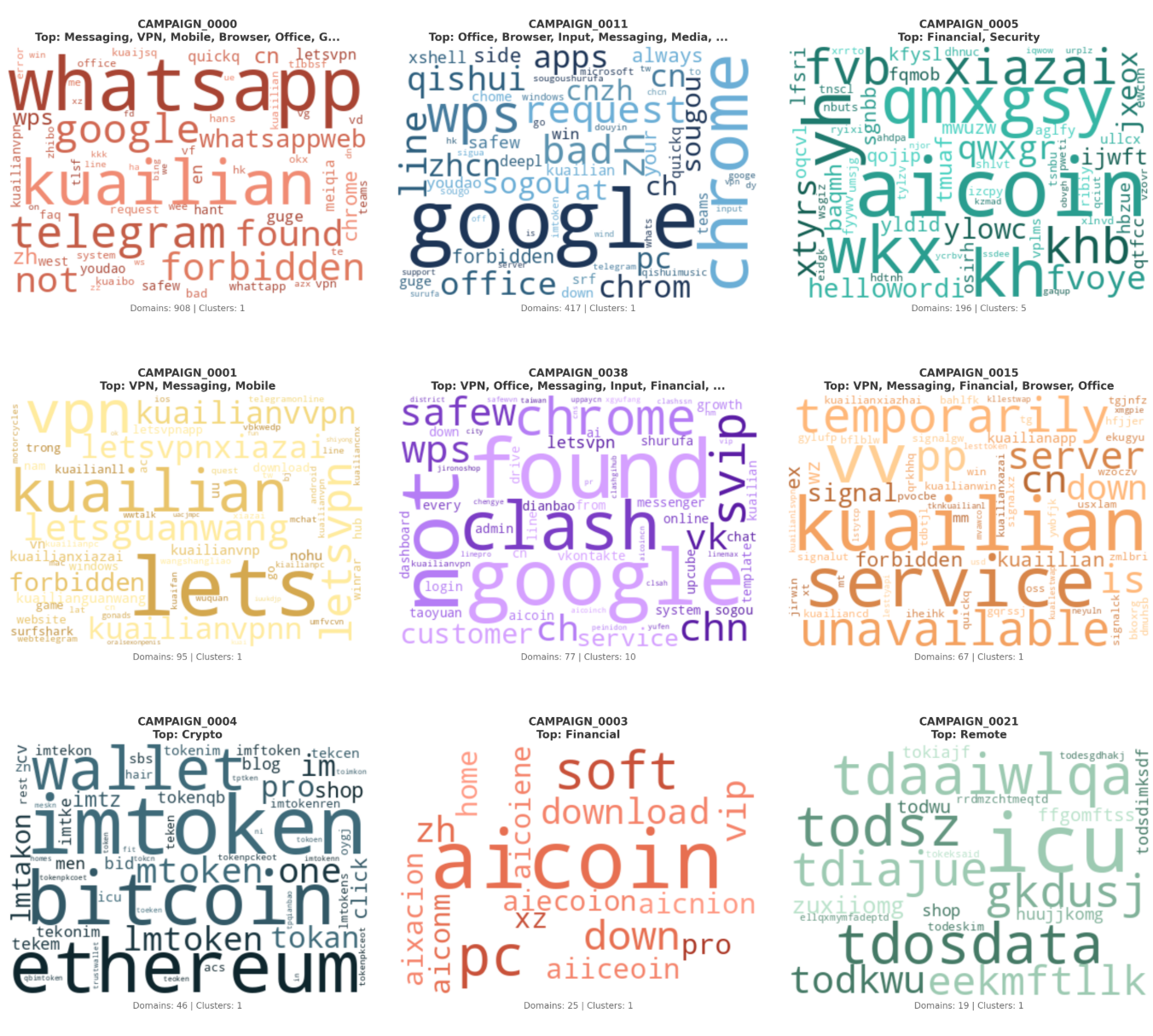
Patterns in Spoofed Application Categories
Communication Tools (391 domains, 24.2%)
- WhatsApp variants: 243 domains
- Pattern: xx-whatsapp[.]com[.]cn, whatsapp-xx[.]com[.]cn
- Examples: dk-whatsapp[.]com[.]cn, whatsapp-us[.]com[.]cn, ph-whatsapp[.]com[.]cn
- WhatsApp Web: 34 domains
- Pattern: web-*-whatsapp[.]com[.]cn, app-*-whatsapp[.]com[.]cn
- Examples: web-apc-whatsapp[.]com[.]cn, app-hs-whatsapp[.]com[.]cn
VPN Services (363 domains, 22.4%)
- LetsVPN/Kuailian (快连): 129 domains
- Pattern: kuailian*[.]com[.]cn, kuaillian-xx[.]com[.]cn
- Examples: kuailianwq[.]com[.]cn, kuailianod[.]com[.]cn, kuaillian-rd[.]com[.]cn
- Kuailian variants: 43 domains
- Pattern: xx-kuailian[.]top, kuailian*-kuailian[.]top
- Examples: vd-kuailian[.]top, kuailian3-kuailian[.]top
Productivity Software (229 domains, 14.2%)
- Google (search/services): 148 domains
- Pattern: cn-*-google[.]com[.]cn, zh-*-google[.]cn, web-*-google[.]cn
- Examples: cn-app-google[.]com[.]cn, zh-cn-google[.]cn, web-gg-google[.]com[.]cn
- Youdao (translation/dict): 19 domains
- Examples: youdao-youd[.]com[.]cn, web-youdao[.]com[.]cn
- WPS Office: 18 domains
- Pattern: wps-office-*[.]com[.]cn, wps-*[.]com[.]cn
- Examples: wps-office-cnzh[.]com[.]cn, wps-jinshan[.]com[.]cn
Web Browsers (109 domains, 6.7%)
- Chrome: 53 domains
- Pattern: guge-*[.]com[.]cn, chrome-*[.]com[.]cn
- Examples: guge-cn[.]com[.]cn, guge-chrome-app[.]com[.]cn, chrome-cnzh[.]com[.]cn
Cryptocurrency Tools (54 domains, 3.3%)
- ImToken: 38 domains
- Multi-TLD strategy: .com, .org, .top, .xyz, .shop, .click
- Examples: imtz1[.]xyz, mtoken[.]shop, imtoken-im[.]click
Financial/Trading Platforms (51 domains, 3.2%)
- AICoin: 27 domains (extensive infrastructure)
- Multi-TLD strategy: .com, .org, .biz, .vip
- Examples: aiiceoin[.]com, xz-aicoin[.]com, aicoin-zh[.]org
- AICoin Download variants: 11 domains
- Examples: us-aicoin[.]com, aicoin-xz[.]com, home-aicoin[.]com
Input Methods & Translation (43 domains, 2.7%)
- Sogou Input: 15 domains
- Pattern: *-sougoushurufa[.], *-sogou[.], sogou-*[.]
- Examples: cnzh-sougoushurufa[.]com[.]cn, app-sougoushurufa[.]com[.]cn, shurufa-sogou[.]top, shurufa-sogou[.]top, sogou-pc[.]cn
2.3 Binary Analysis Results
From workflow analysis data, we recovered and analyzed 47 unique binary samples across campaigns:
[Diagram 2.2: Binary Analysis Overview]
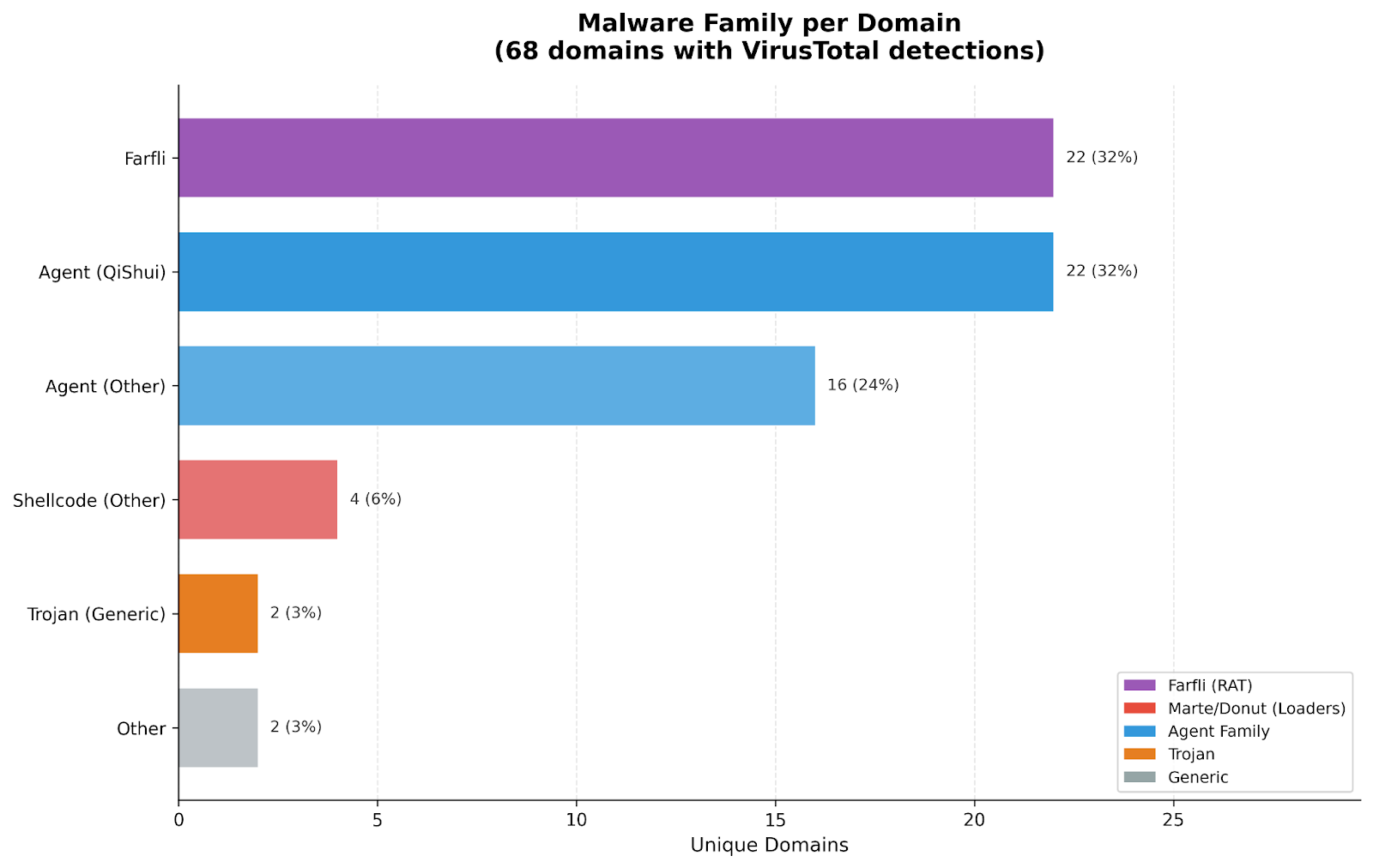
Malware Families Identified
Of the 1,900 domains processed, there were approximately 116 unique executables or archive files retrieved. In many cases, the same files were being delivered across multiple sites.
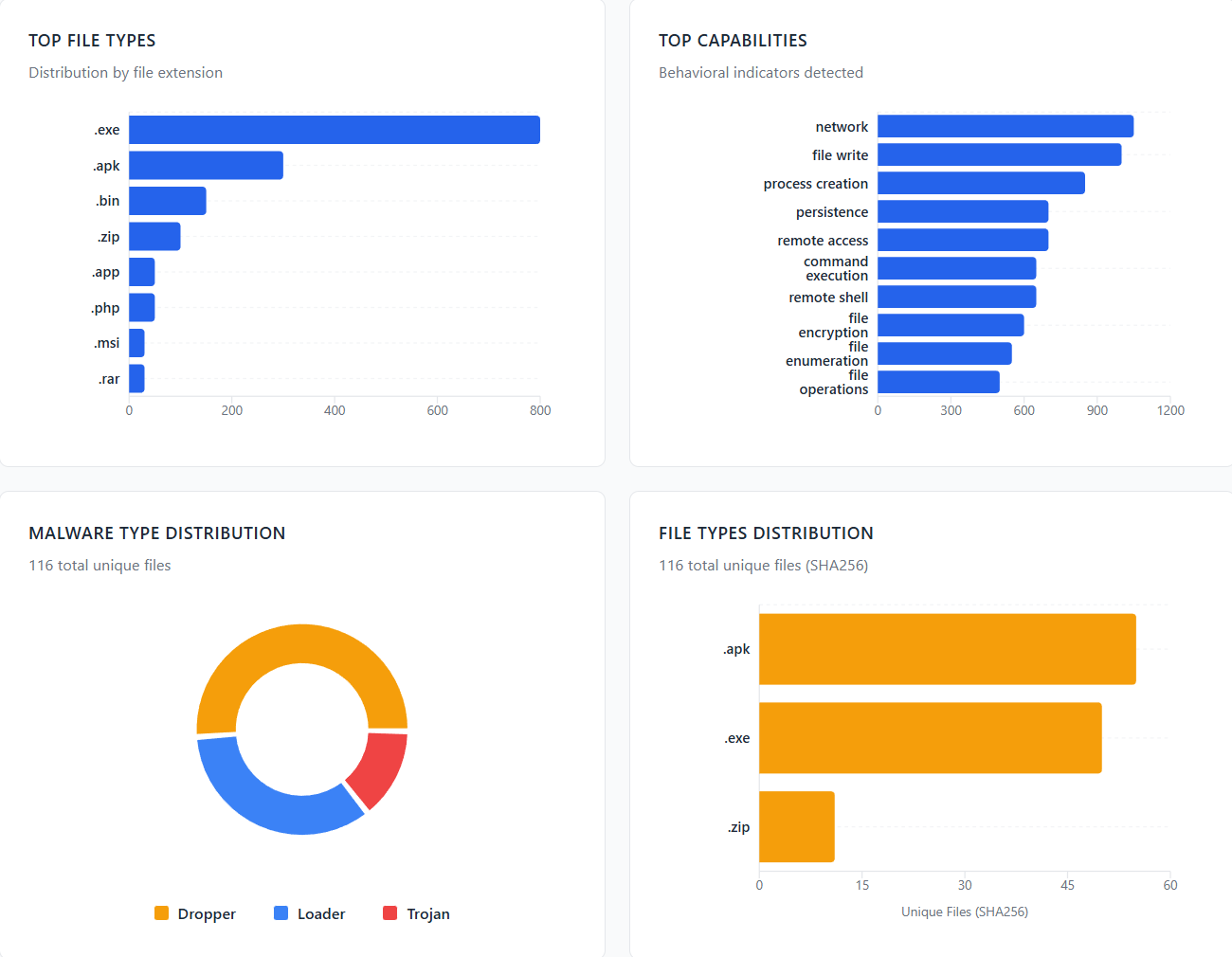
Several samples identified were detected in VirusTotal; however there was a relatively consistent pattern of having large file downloads (100-250mb) from clusters. This likely prohibits most users from uploading to services like VirusTotal to scan the files without using the API.
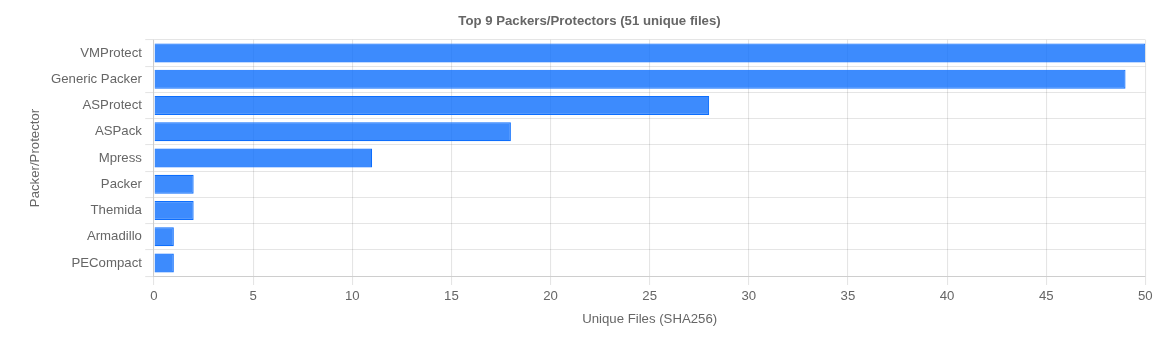
Other prominent patterns were protected files with VMPprotect or UPX and other packers of suspected droppers.
The experimental improvements to the website analysis and malware retrieval approach for research purposes provided additional insights into the malware delivery cluster: namely, that there is a relatively wide variation in the types of malware being delivered from relatively consistent web templates and relatively close clustering of domain management operations compared to previous findings in January and May 2025. This suggests that this long lived cluster dating back to 2023 has been or is evolving into a service platform where end users might bring their own malware in attempts to lure targets of opportunity.
2.4 Geographic and Temporal Patterns
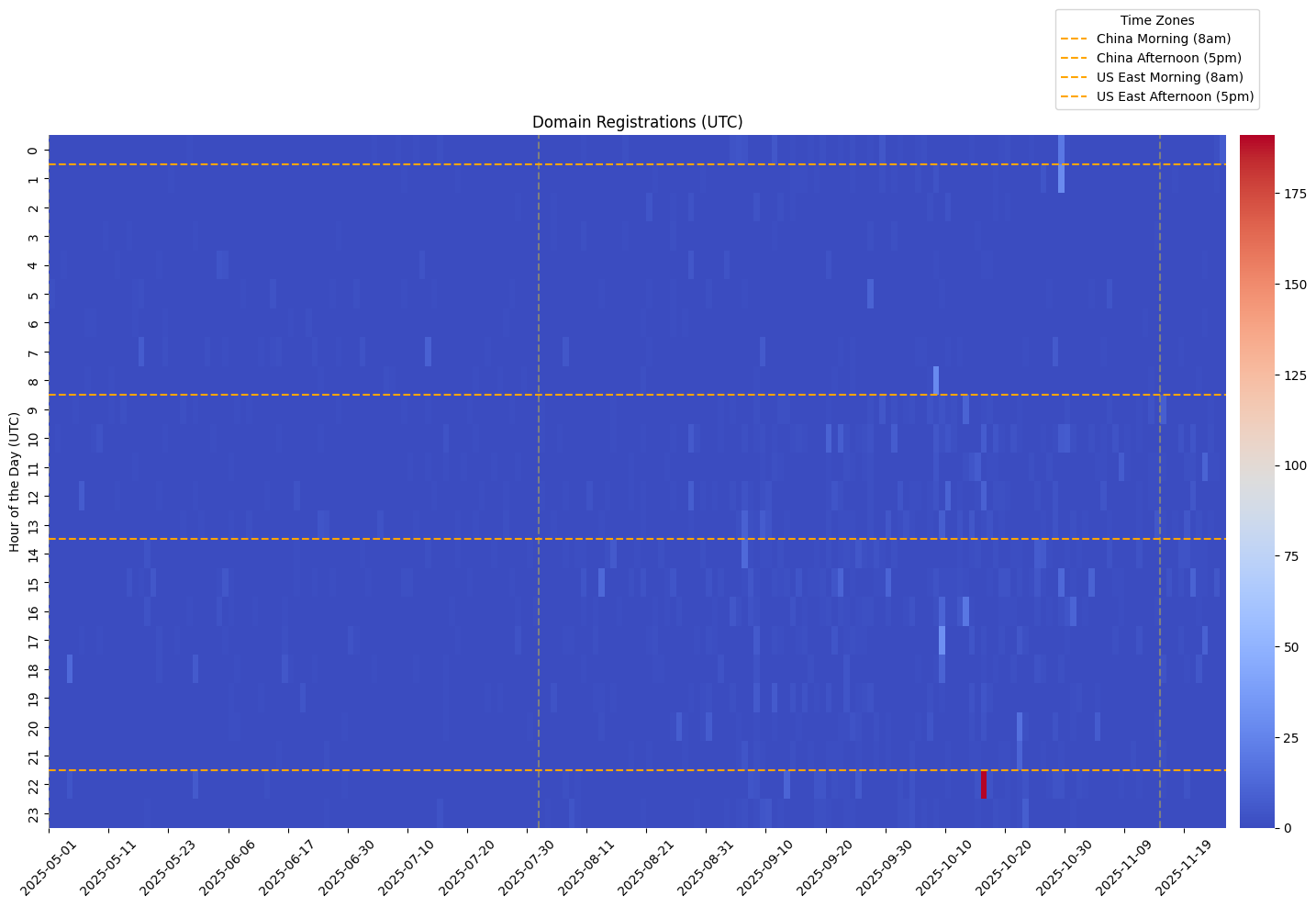
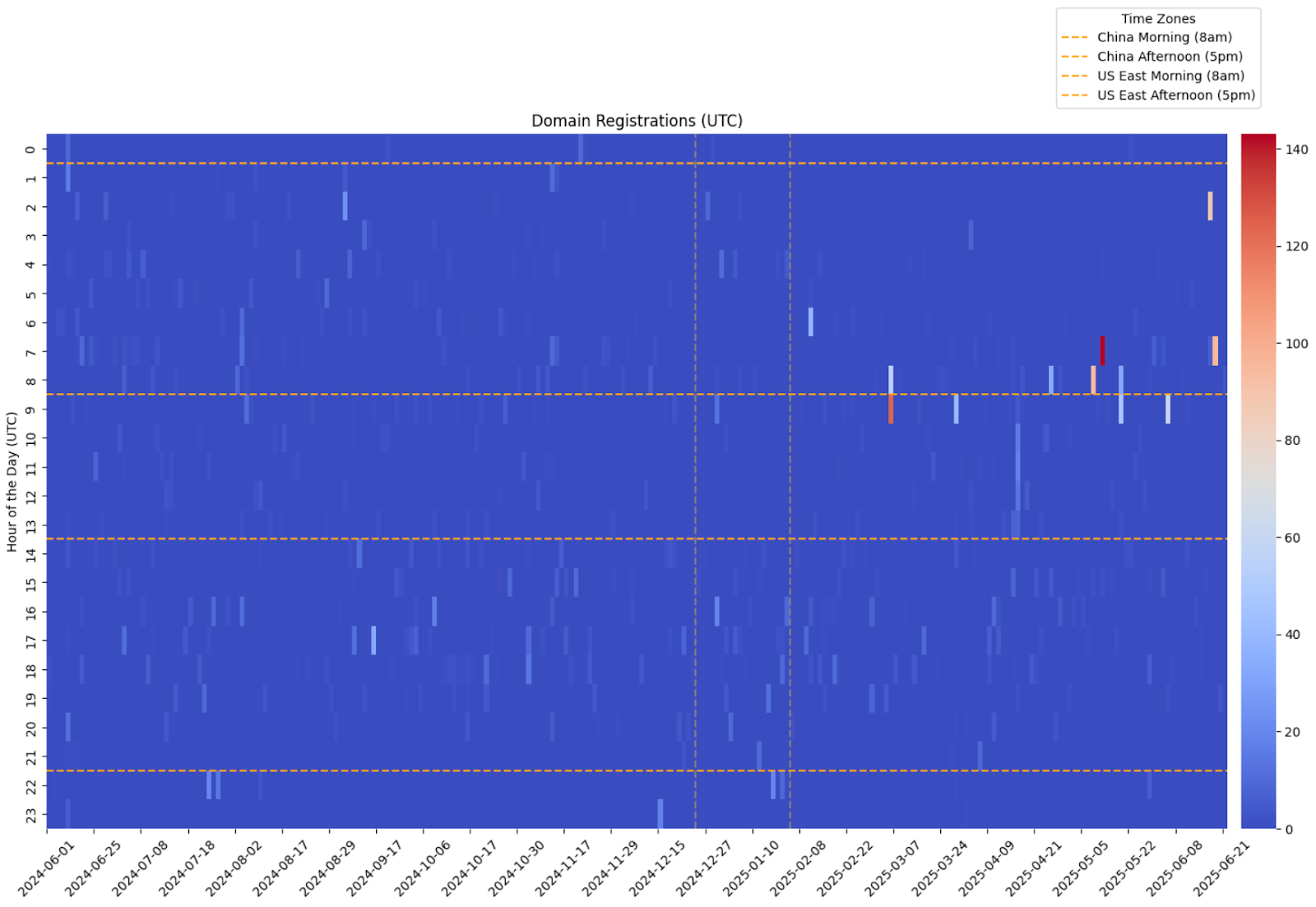
Prior investigations found that domain registration patterns largely aligned with East Asia business hours (8am-5pm UTC+8) in terms of overall volume, continued activity through US holidays but cessation before Chinese New Year, and approximately 40% weekend reductions. The recent data from May to November 2025 does not appear to corroborate similar findings.
[Diagram 2.3: Registration Timing Heatmap 2025-05 to 2025-11] Hour/day heatmap showing timezone working patterns
[Diagram 2.4: Registration Timing Heatmap 2024-06 to 2025-06] Hour/day heatmap showing timezone working patterns
Working Hours Analysis
Peak Activity
Primary Peak: UTC 22:00 (276 domains, 13.9%)
- Beijing: 06:00 (pre-business) | US East: 17:00 (end of day) | Moscow: 01:00 (night)
- Note: 191 of 276 domains (69%) came from a single Oct 16 bulk registration event
- This peak is anomalous for any standard timezone's business hours
Secondary Peak: UTC 15:00 (179 domains, 9.0%)
- Beijing: 23:00 (late night) | US East: 10:00 (morning) | Moscow: 18:00 (evening)
Weekend Activity
- Weekday/Weekend ratio: 3.26:1 (30% above expected 2.5:1 uniform ratio)
- Thursday anomalies: 26.1% of activity (expected ~14%)
Holidays:
Infrastructure Geography
It's important to note that domain registrations can be done via API and in this case may well be, meaning they could be registered at any arbitrary time. Similarly, the TLD and regional hosting providings are typically globally accessible. Though previous analysis of this cluster found that a strong pattern of domain registrations and first observed DNS traffic were common during East Asia working hours, that is no longer evident from the data. What can be still inferred is that the focus remains consistently on primarily targeting Chinese language users. This inference was amplified by the cluster’s record spike in malware delivery website configurations during the Chinese Mid-Autumn festival, suggesting the intentions of this cluster are or have been primarily targeting Chinese users.
Part 3: Agentic AI for Analysis
3.1 Architecture Overview
The game-changing capability in our analysis comes from the deployment of specialized AI agents that operate in coordinated workflows. Unlike traditional automated tools that follow rigid scripts, the agentic system demonstrates adaptive intelligence in analyzing threats.
[Diagram 3.1: Agent Orchestration Flow]

Two-Layer Agent System
Layer 1: Orchestration
- Receives analysis requests
- Coordinates specialized agents
- Synthesizes findings into threat intelligence
Layer 2: Specialized Analysis Agents
- ScannerAgent: Browser automation and traffic capture
- CodeAnalyzerAgent: JavaScript semantic analysis
- BinaryAnalyzerAgent: Multi-tool malware analysis
- YARAGeneratorAgent: Automated rule creation
3.2 AI-Powered Analysis Workflow
The power of agentic AI is best illustrated through an actual analysis sequence. Here's how the agents collaboratively investigated a suspicious domain:
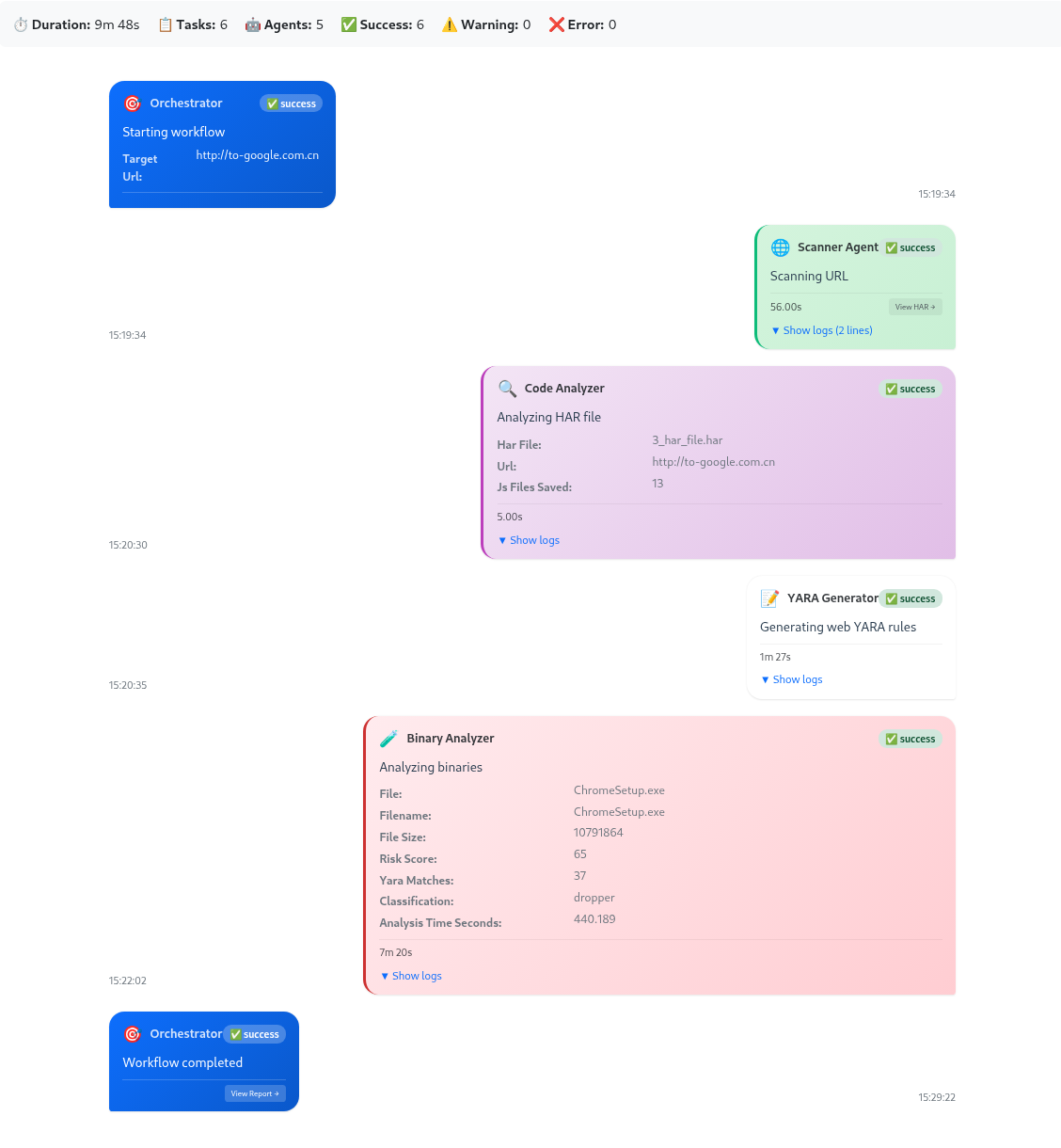
Sampling of the website code analyzer subagent looks for malicious characteristics, identifies malware delivery behaviors, and determines if Yara rules could be generated for any identified malicious code on the site. If so, they get tasked to and created by another subagent and are immediately put to use going into future analysis so the system can learn as it goes.
Screenshot of the malware delivery website spoofing as a Google Chrome download site for Chinese language users:

Agent analysis summary of the website code, visual inspection, and network traffic analysis:
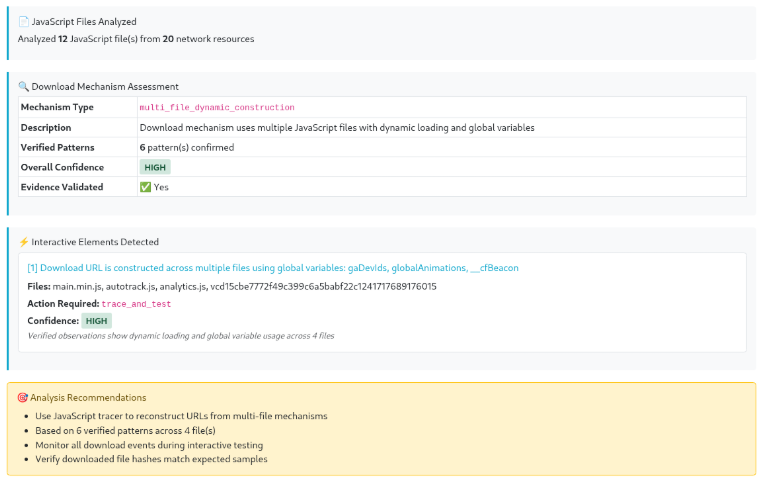
In a second example, the experimental AI service analyzed a gambling site that attempts to profile users and has anti-bot mechanisms to attempt to prevent scanners and web scrapers, and lacks a clear programmatic delivery mechanism. The screenshot below is of a download site for a purported online gambling mobile app. It serves an APK file that is packed and suspected of sideloading stealer malware.

Agentic code analysis of the site:
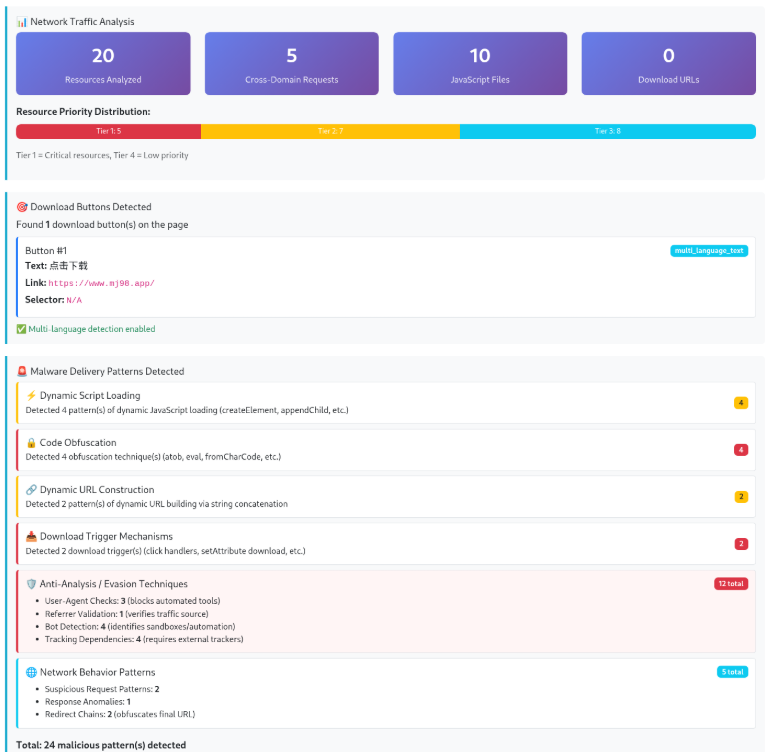
3.3 Scaling Defense with AI
The use of AI agents changes the economics of defense. In investigating malicious websites for example, the primary pain points for a human analyst can be determining the website characteristics to identify and retrieve malware and knowledge management to discern if similar site configurations have been observed before. The timing for a human analyst doesn’t scale to many websites or the many investigation avenues sometimes needed such as combining code and interactive analysis actions. Agents can run those same tools and action those same or similar interactions.
[Diagram 3.2: AI vs Manual Analysis Comparison]
Processing Transparency
It's important to note our actual performance metrics. During this experimentation phase we gave minimal system resources and allowed for 3 agent workers to process 1 domain each through the workflow at a time. These were their approximate completion time averages broken down by the core tasks within the analysis workflow. In one bulk processing run with 3 workers, 2,000 malware delivery domains were processed in approximately 10 hours.
- Average Processing Time: 1-10 minutes per domain
- Variance Factors:
- Simple static sites: ~1 minute
- Heavy JavaScript: ~3 minutes
- Binary download and analysis: ~5 minutes
- Parallel Processing: Up to 3 concurrent analyses
- Daily Throughput: 400 - 4,000 domains
Conclusion
The threat actor continues to demonstrate capabilities in maintaining large-scale malware distribution infrastructure targeting Chinese-speaking users. Through our analysis of approximately 1,900 domains from May to November 2025, we observed an evolution in their operational tradecraft, including infrastructure diversification, enhanced evasion techniques, and additional spoofed entities such as popular Chinese AI and entertainment apps.
This investigation experimented with AI-powered analysis. The deployment of specialized AI agents enabled full coverage in analysis throughput while maintaining relatively high precision; however, agentic detection authoring remained a persistent weak point that continues to require further refinement. This capability changed the defender's equation, enabling complex and dynamic analysis workflows to scale to the volume of a large malware delivery campaign.
Special recognition goes to the AI agents that processed thousands of domains tirelessly and consistently. However, we must acknowledge limitations in our analysis. Processing times of 1-10 minutes per domain, while revolutionary compared to manual analysis, still require substantial computational resources for internet-scale defense. Attribution confidence, while high for core clusters, relied on spoof themes and infrastructure patterns rather than incorporating website and binary characteristics into clustering parameters as well. Future work seeks to incorporate an increase in the learn-as-we-go approach to identify additional sites with common malware delivery and detection evasion characteristics as well as further efforts in binary analysis integration.
As we look forward, the cybersecurity landscape has found itself balancing on the scales of an AI-pervasive era where criminals and defenders alike might empower their roles.
The malware delivery campaign highlighted in this report provides insights into the scale of modern threats and an opportunity to show that with appropriate application of AI, defenders can keep pace.
Appendices
Appendix A: IOC List
A complete list of all domains, file URls, and hashes can be found on our GitHub.
Disclaimer: This report contains analysis of malicious infrastructure for defensive purposes. All malware samples and malicious domains should be handled with appropriate security controls. The processing times and performance metrics stated are estimates based on our specific infrastructure and may vary in different environments.
Registrant Emails
Trackers
SHA256 File Hashes
Download URLs
Domains