SecuritySnack: Phishing Interviews
A malicious actor has created several domain masquerades of small companies posing as job boards, interview themes, and login pages since approximately August 2025. The activity appears to have two distinct objectives. The first is a credential harvesting scheme targeting ID.me accounts — the official identity provider for US government services like the IRS and SSA — which may then be exploited to facilitate financial fraud, including tax refund theft and fraudulent unemployment benefits. The second cluster focuses on malware delivery, tricking job seekers via fake Microsoft Teams meeting invites to download a malicious, unsigned variant of the remote access tool Connectwise. This gives the attacker access to the victim’s machine where they may conduct follow-on attacks.
Registration Commonalities
- Nameserver: namecheaphosting.com
- IP ISP: Namecheap Inc.
- Mail Server Domain
- privateemail.com
- jellyfish.systems
- SSL Issuer: Sectigo
- Registrar: NameCheap Inc.
- Server Type: Microsoft
ID.me Credential Harvesting
clock-towerrealty[.]org
apply-untide[.]rentals
The site purports to be a United Rentals Careers portal and uses legitimate links and site content loaded from the real site, jobs.unitedrentals[.]com.
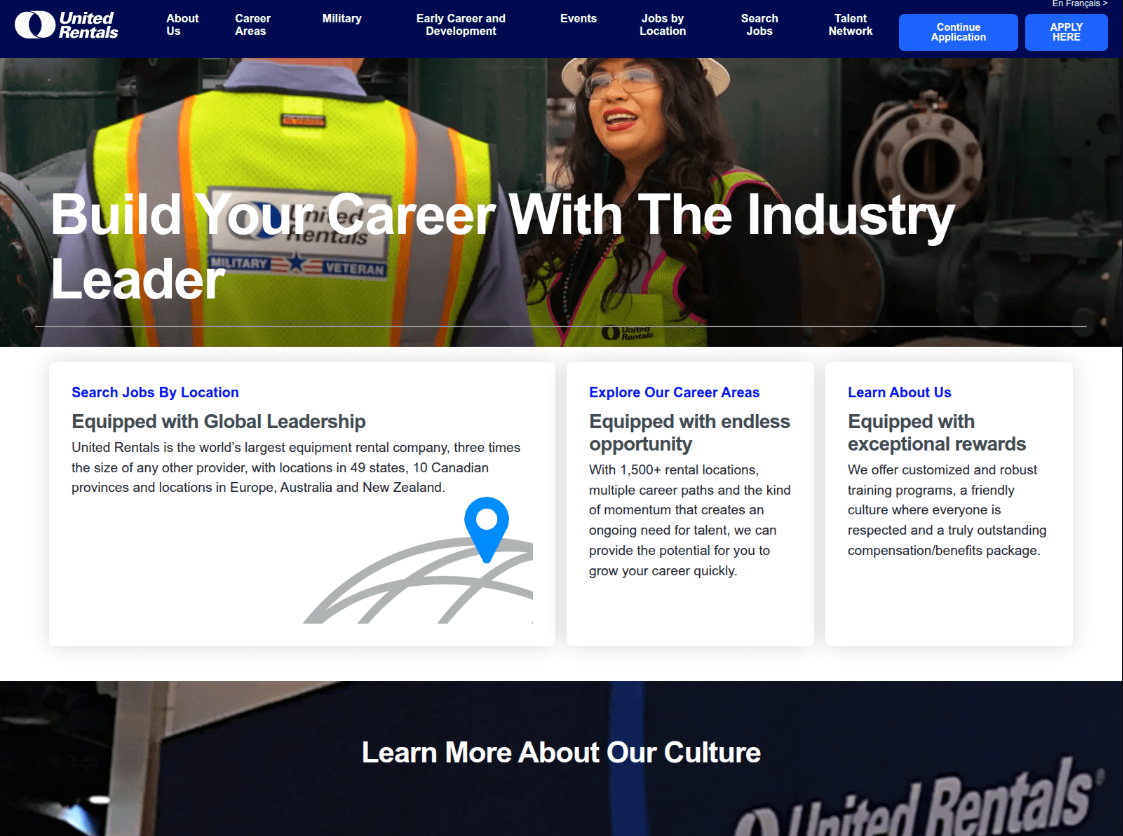
The two buttons on the top right for “Continue Application” and “APPLY HERE” direct to another actor owned domain, clock-towerrealty[.]org.
http[:]//clock-towerrealty[.]org/APPLY/?ff_landing=13 Continue Application
https[:]//clock-towerrealty[.]org/APPLY/?ff_landing=10 APPLY HERE
The code for clock-towerrealty[.]org contains a credential harvester designed to look like a legitimate corporate portal. This appears to be a brand spoof but not a website spoof of the real entity, Clock Tower Realty in Florida, USA.
The malicious domain is using a cheaply registered WordPress site to trick job seekers into providing their email and password. Credentials being targeted are ID.me. If a scammer gets ID.me credentials, they could potentially perform unauthorized logins to steal tax refunds, apply for fraudulent unemployment benefits, or take over Social Security accounts.
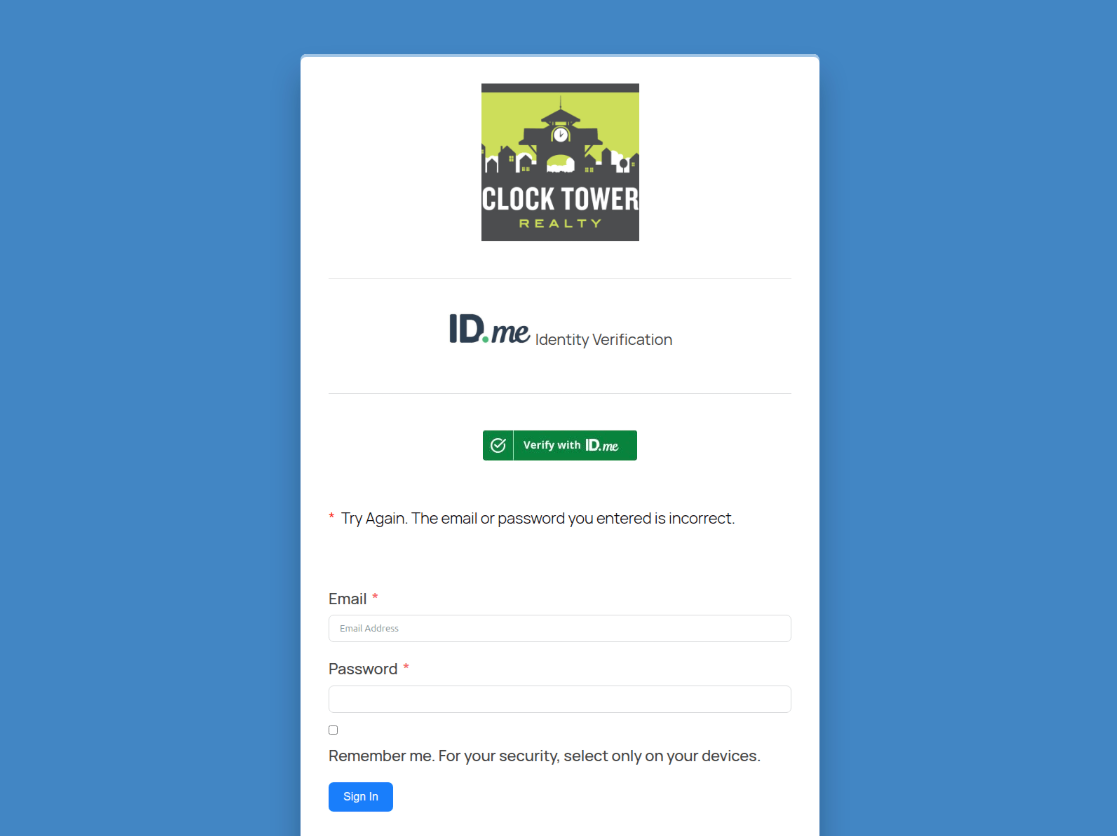
When a user clicks the "Sign In" button after entering their information, the data is sent to admin-ajax.php, suggesting the stolen credentials are being stored in the WordPress SQL database.
https[:]//clock-towerrealty[.]org/APPLY/wp-admin/admin-ajax.php
The site also has a preloaded error message loaded initially - a basic deception to trick users into entering credentials.
```
<p class="alert alert-error" role="alert">
<span style="color: #ff0000">* <span style="color: #000000">Try Again. </span></span>
<span style="color: #ff0000"><span style="color: #000000">The email or password you entered is incorrect.</span></span>
</p>
```This site, strangely, uses images with the following filenames:
- WhatsApp-Image-2026-01-16-at-12.23.50-PM-300x117.jpeg
- WhatsApp-Image-2026-01-16-at-12.25.04-PM.jpeg
These scammers may have taken screenshots of legitimate company logos and sent them via WhatsApp during the development of the scam, hence the file names “WhatsApp-Image”. Seeing "WhatsApp-Image" in a site's source code is a strong indicator that the site is fraudulent. Legitimate companies like United Rentals have dedicated IT departments.
The site is instrumented for marketing and behavior tracking using the Google Tag Manager (GTM) ID “GTM-T75PDC7R”,which appears on multiple other actor-controlled sites created between 2025-08 and 2026-01 that feature the same type of scam.
Website Title: Careers | United Rentals
GTM-T75PDC7R
clock-towerrealty[.]org
apply-untide[.]rentals
from-unietd[.]rentals
frosm-unitde[.]rentals
from-united[.]rentals
forms-unitde[.]rentals
froms-united[.]rentals
Malware Delivery
Other domains suspected of being in an associated cluster of activity were also identified masquerading as legitimate small company brands with job interview meeting invites. However, these domains do not simply attempt to steal credentials through fake logon pages. Instead, they deliver a malicious Windows installation file that provides remote access to the compromised machine.
Initial phishing domain: mlcrsoftedge[.]com. The site itself purports to be and links to https[:]//lsxconstructions[.]com/, a seemingly legitimate construction company website, which was created 2025-02-01 and redirects to lsxconstruction[.]com.
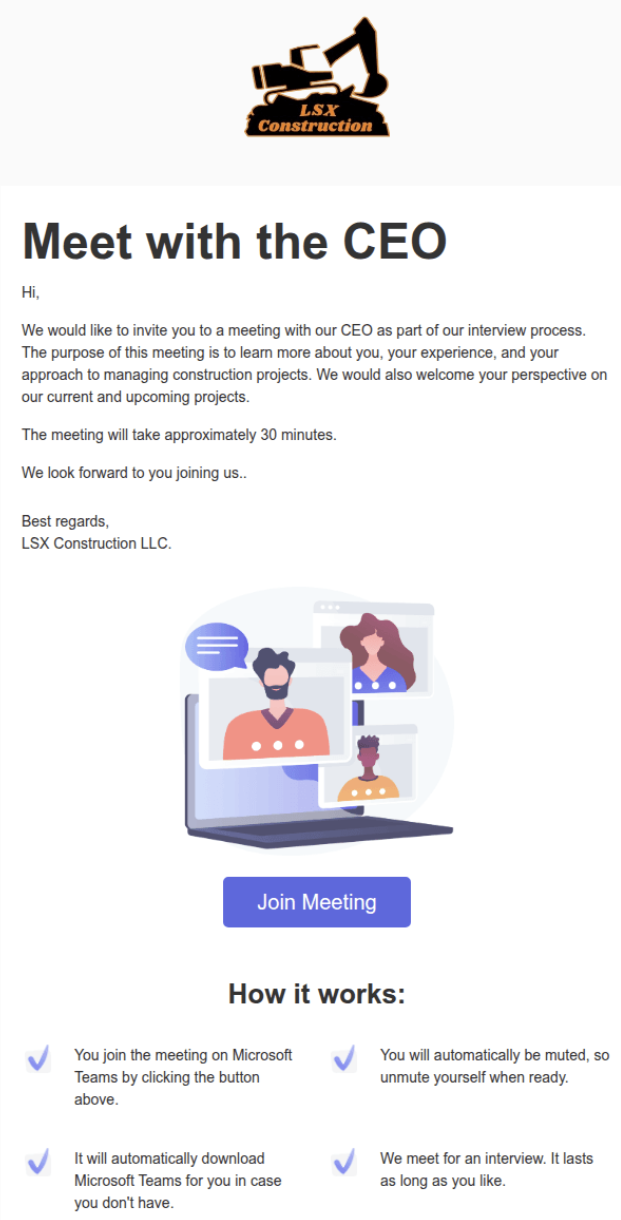
When users receive the meeting invite and click the "Join Meeting" button, they unknowingly initiate a download of a modified, unsigned installation file for Connectwise, a remote access tool.
https[:]//mlcrsoftedge[.]com/downloads/LSXCMeets.msi
LSXCMeets.msi
4107f8e0d6597866d4beb7c30718935353782dc7e199d3956fd10c8456383feb
Bundled files such as 7027b69ab6ebc9f3f7d2f6c800793fde2a057b76010d8cfd831cf440371b2b23 are linked to multiple reports of impersonation attacks and Connectwise phishing campaigns going back to 2025-04-23. The majority of the recent activity appears to have started around 2025-11.
Conclusion
The identified phishing activities use domain masquerades with a job theme and consist of two distinct attack types. One focuses on harvesting ID.me credentials, which are used to access government services (IRS, SSA, VA) and facilitate financial fraud. The second delivers a malicious, unsigned remote access tool (Connectwise) disguised as a Microsoft Teams link, resulting in system compromise. While there’s no definitive evidence the two clusters are linked to the same actor, the registration patterns, themes – specifically, masquerading as small companies – and timeframe appear highly correlative.
IOCs
mlcrsoftedge[.]com
clock-towerrealty[.]org
apply-untide[.]rentals
from-unietd[.]rentals
frosm-unitde[.]rentals
from-united[.]rentals
forms-unitde[.]rentals
froms-united[.]rentals
Sha256: 4107f8e0d6597866d4beb7c30718935353782dc7e199d3956fd10c8456383feb
Google Tag Manager: GTM-T75PDC7R
Related Content