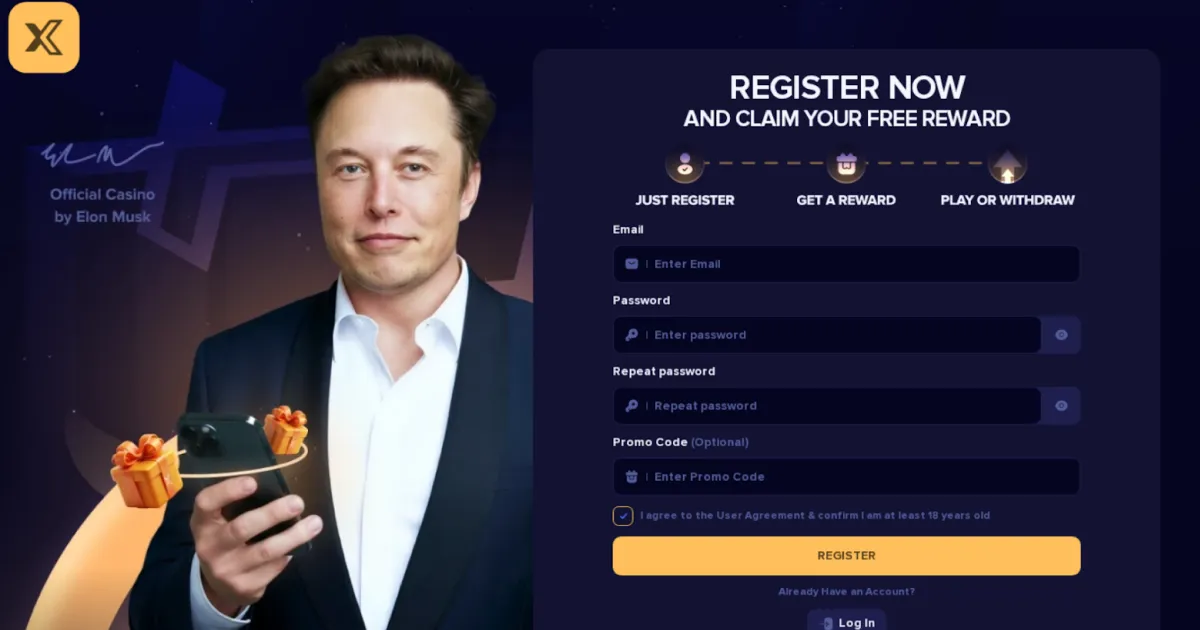
Before trying out your new year luck, be wary of online gambling apps and real money games. This report details an investigation into multiple clusters of dubious Android applications created in the past few weeks that are engaged in predatory gambling and real money gaming apps. Notably, these are not registered apps. They are intentionally misleading users into thinking they are legitimate and reputable through multiple tactics like spoofing the Google Play Store, creating fake reviews, generating fake public win declarations, and creating entire brands with marketing campaigns and broad distribution tactics. These clusters also attempt to evade detection and analysis by having post install code and configuration retrievals from actor controlled sites, which serve a dual purpose of distributing region specific content to users post installation.
The report is segmented into three distinct infrastructure clusters. Each cluster appears to target a general set of countries including Nigeria, India, Pakistan, and the Philippines. They also appear to have non-region specific user base targeting, including English, Portuguese, and Bengali speaking users. Despite the wide range of targets, the clusters share a common theme of mobile-focused gaming or gamified gambling apps to attract users for financial gain.
Details
The three clusters spoof the Google Play Store with fake app reviews and downloadable Android applications. Clusters 1 and 2 involve Android application delivery campaigns that utilize the Cocos2d game engine to obfuscate code setup,load external code and configuration details, and send device and user telemetry to actor controlled domains. These applications are distributed via hundreds of websites spoofing as Google Play Store installation pages with fake reviews. Search Engine Optimization (SEO) manipulation techniques are used to drive traffic to these sites.
Cluster 1: AA Game: Aviator
Approximately 180 domains since March, 2025,170 of which were first seen on 2025-12-14. They host nearly identical websites and serve primarily the same APK file with a few exceptions in older versions. The apps appear to feature crash-gambling mechanics, a style of game where users attempt to collect as much money as possible before the game crashes.
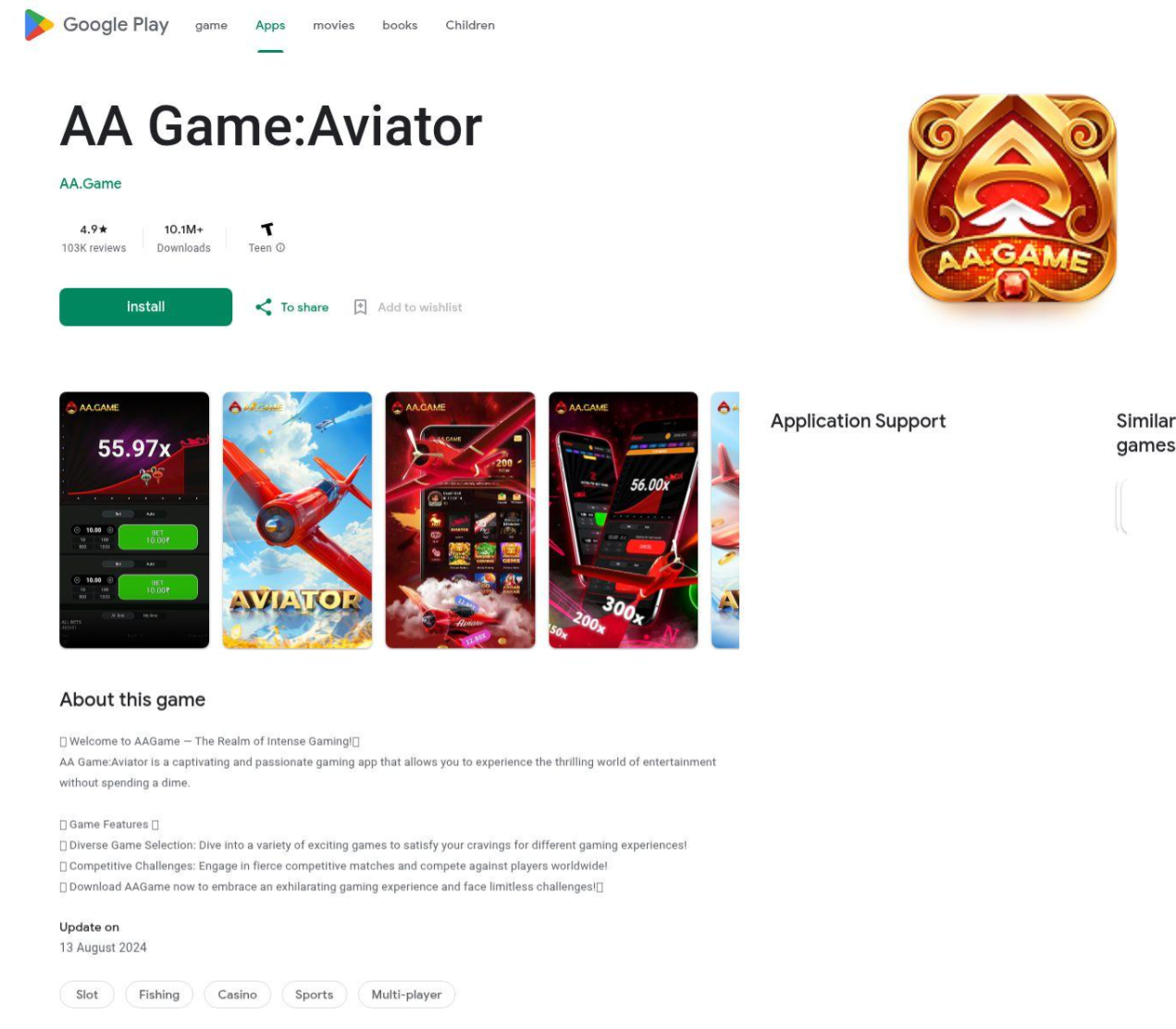
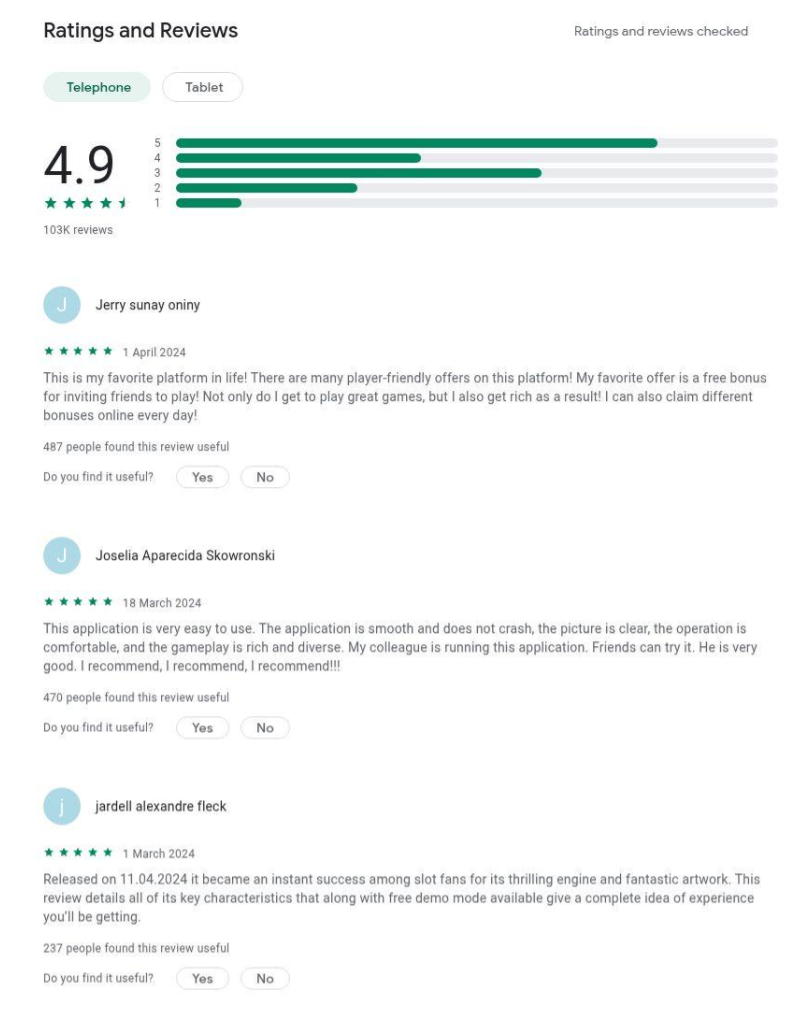
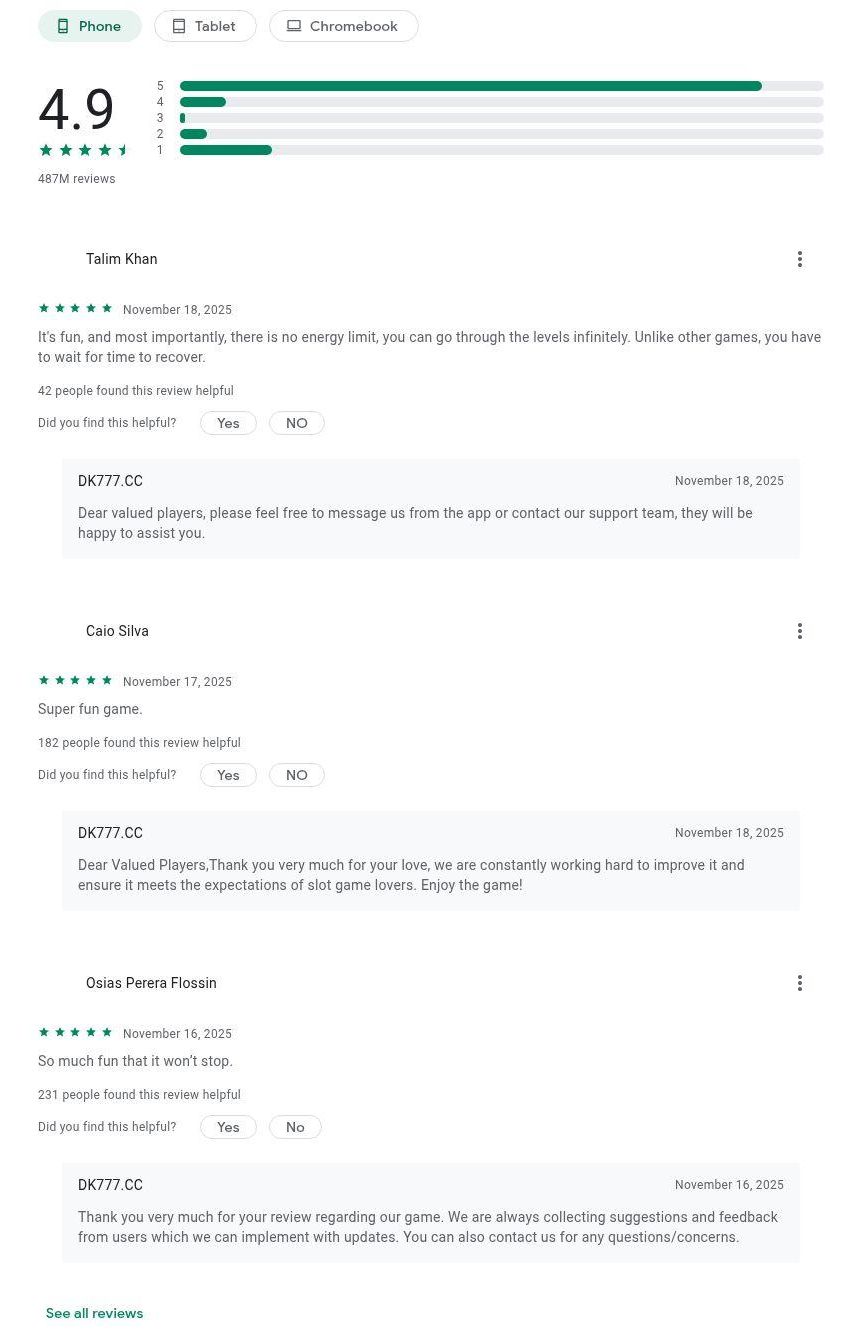
The reviews are clearly fake. They are hardcoded into the HTML, there are multiple identical reviews under different names, and they all share the exact same review id such as “data-review-id="13dc2fa2-4acc-4923-8a55-be2f20d1841a". In a real database, every review has a unique ID. Here, the scammers just copied and pasted the same HTML template.
“Aviator” games are also commonly used themes for unregulated, illegal gambling crash style games. The example app above uses terms like “Get Rich”, and has fake reviews like “I also get rich as a result!” and “Because I made more money than you can imagine!". Legitimate apps on the Play Store are strictly regulated; Google does not allow apps to promise that you will "get rich." These are social engineering tactics used to play on people's desire for easy money.
Brief details of connective tissue
Baidu Tracking ID: 49521a05cd400ce694691ca2cfd38453
IP ISP: Defender Cloud International LLC
Registrar:
- Metaregistrar BV
- Bangning Digital Technology Co.,Ltd
Name Server Domain: share-dns[.]net, share-dns[.]com
Server Type: nginx
SSL Hashes
- bc1f466a2c1c4b885adac674e39e8fe22d26d4a5
- b9e8c8b5ddba6935c82fd5e192e4171d005b0d8c
- 134a16bfde5eb4d3908a53aa9a18a50c7b129c29
Website Title: AA Game:Aviator - Apps on Google Play
AA: Aviator Application
AAGame-new523y.apk
3860ffaa621b26c742dcfce52b916ddad6f7f4056045a0fadaf3434fc978c9ad
6da17544754706b86042b1646b6ae7101b549f539b69c5be5b68594cd9cfa969
83332d680ed84f222a5b9f2085b4fa9523e98c80d65eeecde6d4cb65d3075110
32a7c4a4dc4b14988adfa65a1c5d55df2ca39852c5e7aa61187df306436f58d7
india-aagame-7000003.apk
9a7495bb56e05389c00e4702a53eed6d946d265b20be766c92ef15e00d69ca6b
A defining characteristic of these applications is the use of the Cocos2d framework. In this model, the Android Java layer (DEX) acts as a minimal host for a native C++ engine (libcocos.so), which in turn executes encrypted, compiled JavaScript code.
Although some of the analyzed application’s code paths and text suggested they were targeting Nigerian based users, there were also samples focused on the Indian rupee (INR). Though remnants of what could be past regional targeting were observed, it's unclear if a specific user base is currently being targeted in this cluster.
Analysis of an older development variant of the Android application revealed a module called hall_marqueen. This module is hard-coded to generate fake withdrawal notifications, creating the illusion of a highly active and profitable user base:
code JavaScript
downloadcontent_copy
expand_less
setHallLabelText() {
let e = "";
// 5% chance of a "realistic" name, 95% chance of a generic "UserXXXXX"
if (p.instance.getIntRandom(0, 20) > 19)
e = p.instance.getRandomName();
else {
let t = p.instance.getIntRandom(0, 3e5).toString();
while (t.length < 5) t = "0" + t;
e = "User" + t;
}
// Randomized fake withdrawal amounts
let t = ["100", "200", "500", "1000", "5000", "10000", "20000"];
const n = Math.floor(Math.random() * t.length);
return e + " successfully withdraws ₹" + t[n];
}Cluster 2: DK777
Cluster 2 is a more generalized gambling Android app delivery. Sixteen domains registered on the same day host similar websites spoofing the Google Play store to deliver the same APK file. The application "DK777" features slots and multi-game halls, with visual assets emphasizing "big wins" and "jackpots”. The application also uses a Cocos2d framework with a more complex range of obfuscation techniques, including over 1,000 obfuscated files within the application’s classes dex file and 50+ encrypted JSC files. Multiple presumably actor-controlled sites with backups were identified that are used to send device telemetry and retrieve additional configuration and code for execution. Some of the configurations were set to use the Pakistani rupee. Languages in the apps included English, Portuguese, and Bengali.
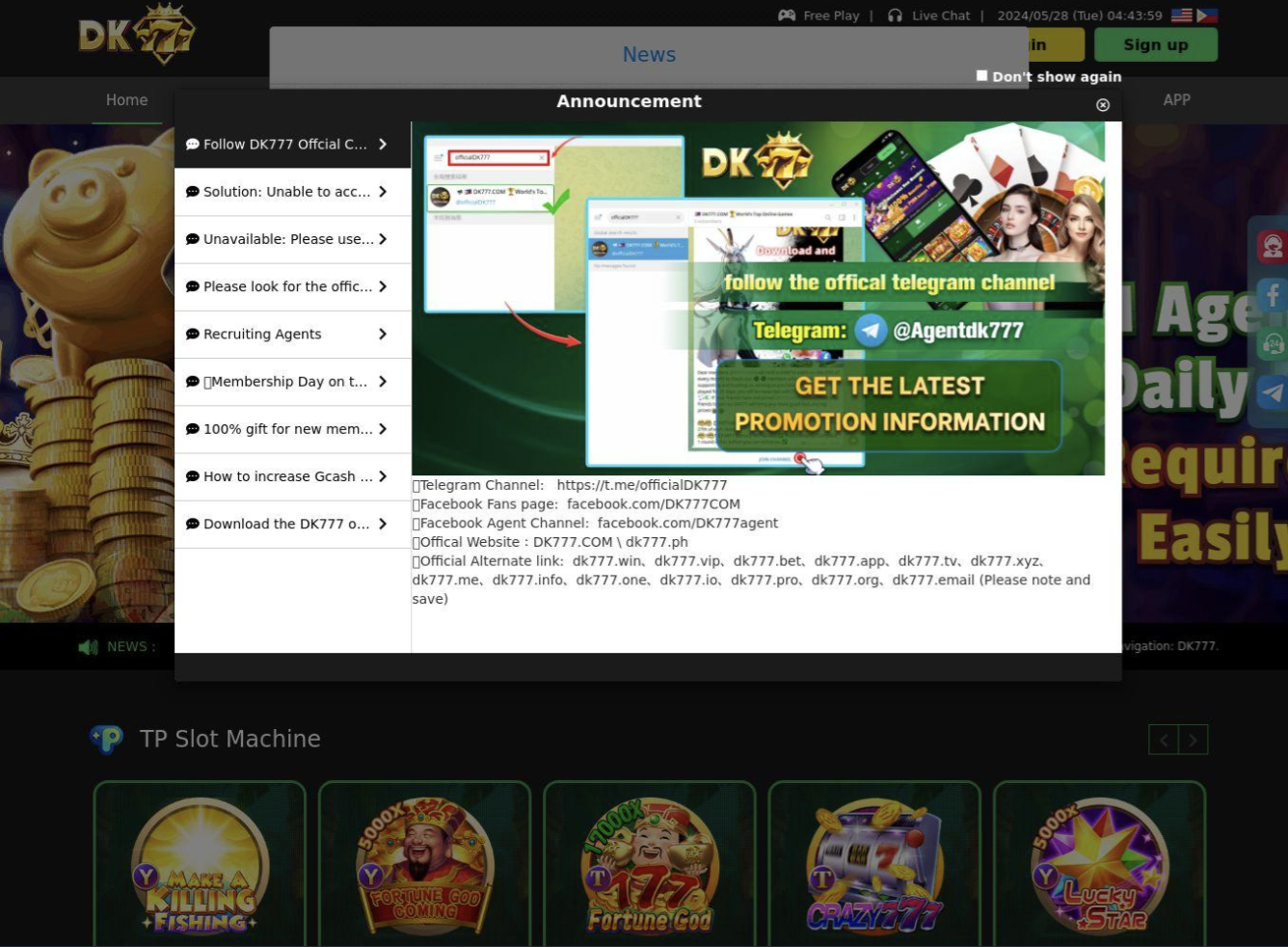
Initial delivery domains spoof the Google Play Store for DK777 Android app delivery, including the following:
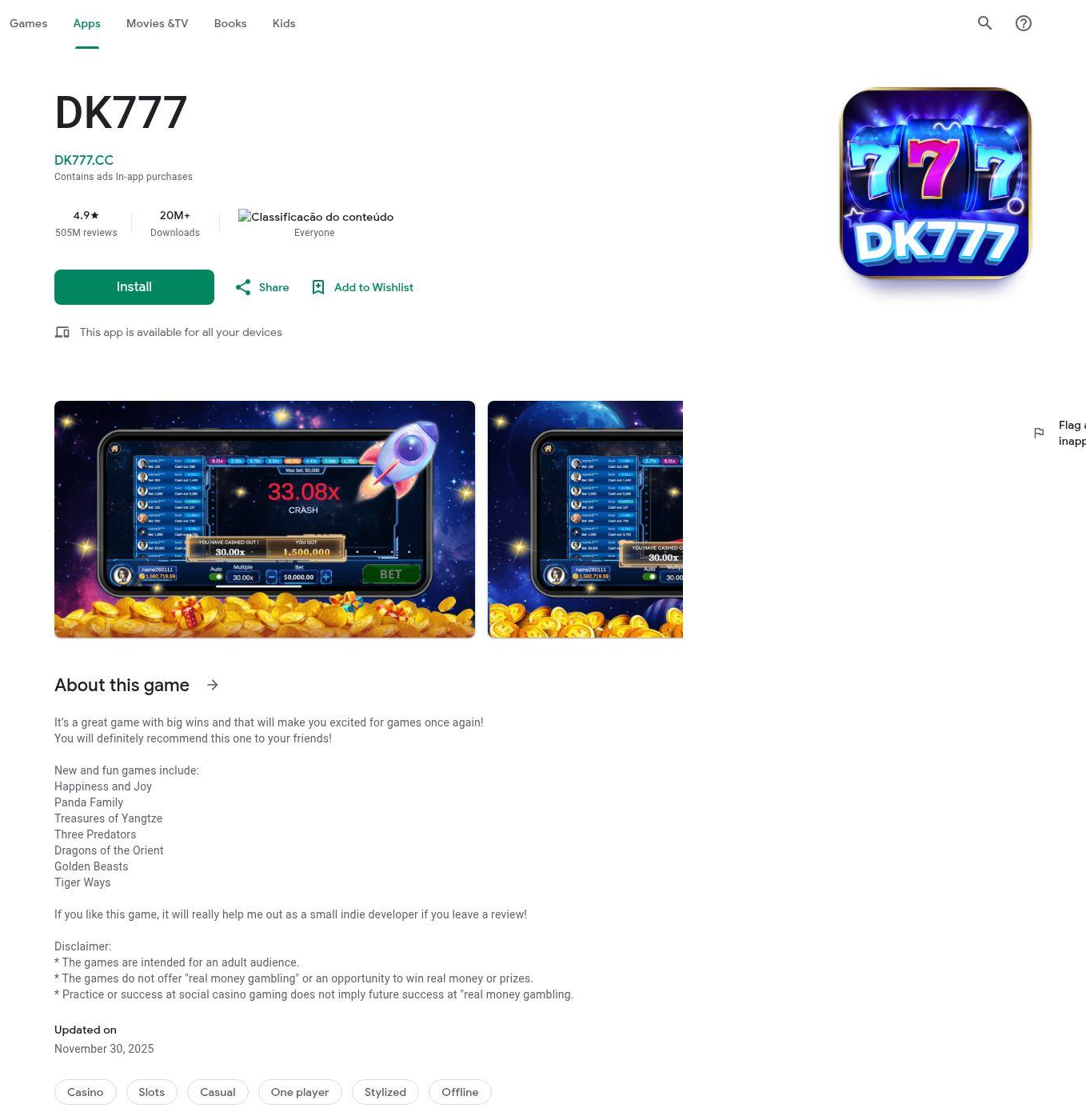
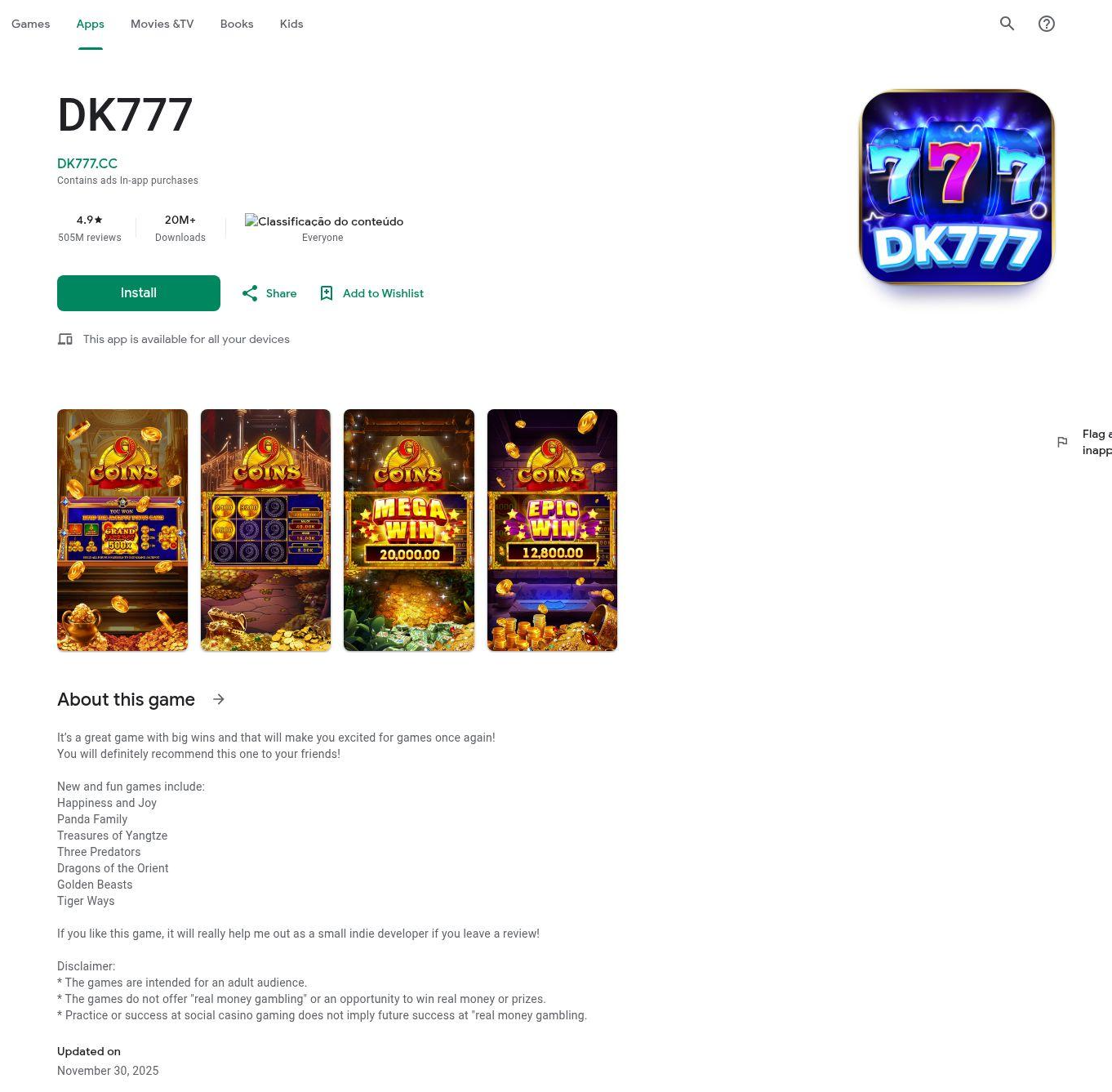
Brief details of connective tissue
ISP: CloudFlare Inc.
Registrar:
- Metaregistrar BV
- Gname[.]com Pte. Ltd.
Name Server Domain: cloudflare[.]com
Website Title: DK777 – Apps on Google Play
All the initial delivery domains download the same APK.
DK777_1000.apk
7da0e56d4c0669647aec7ea3645b882b793d4de20ab14718d4d6698fe9b3b8a2
The app retrieves external code and configuration details from actor-controlled domains.
All six domains were registered the same day (2025-12-08) with similar registration and hosting configurations. Pivoting on these configurations revealed over 120 other domains dating back to as early as 2022-01 with similar gambling themes, including "192bet[.]com" and "pak111[.]com".

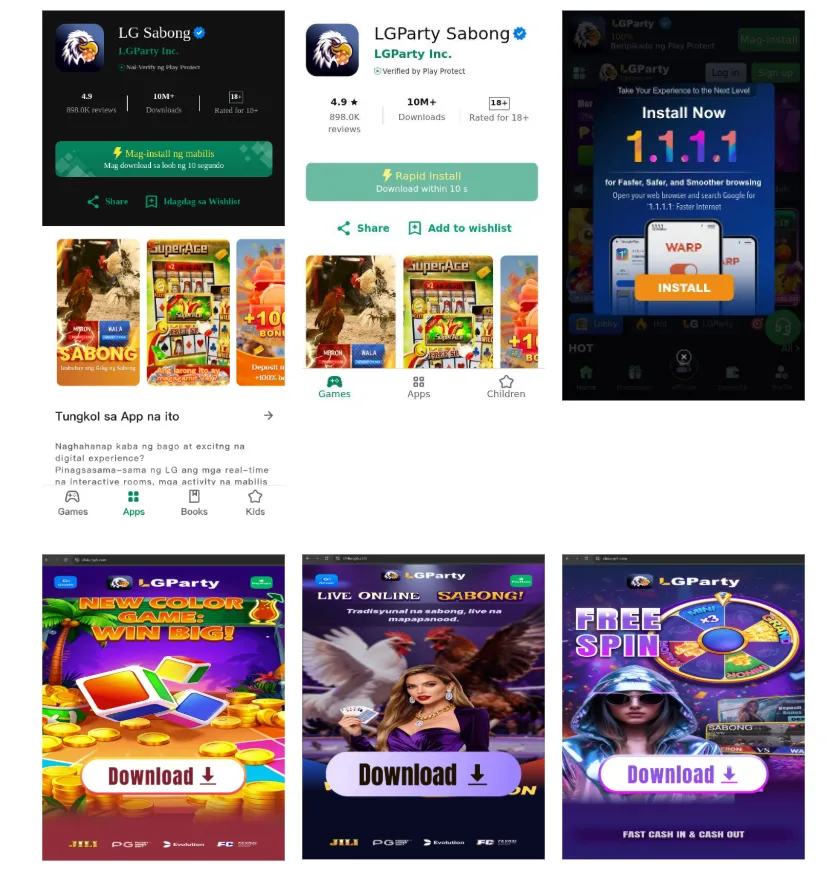
Cluster 3: LG Sabong
This cluster has approximately 196 domains. The bulk of registrations occurred between November and 2025-12 with related domains observed as early as 2025-05. The websites have aspects suggesting some localization for Filipino-speaking users. The nomenclature "Sabong" (cockfighting) suggests a focus on a culturally specific gambling market in the Philippines, while some variations of the randomized display images use the Filipino language.
Brief details of connective tissue
Google Tag Manager: GTM-M899ZXM
ISP: CloudFlare Inc.
Registrar: Dynadot Inc
Name Server Domain: cloudflare[.]com
Server Type: AliyunOSS
Website Title:
- LG - Apps
- LGParty - Apps
- LGParty - Apps on Google Play
The sites use a "Cloaking" or "Bridge Page" system typically used in the gambling industry to bypass ad platform restrictions (like Facebook or Google Ads).
The code does not build a real functional website with buttons and text. Instead, it renders a hardcoded "lgpartyShareLand" component, which are PNG images displayed as the site content. These images are randomly selected during page load from two arrays stored on an Aliyun (Alibaba Cloud) server. There are 12 different sets of images for "LGParty" and 9 sets for "LG111". This is likely done so that ad reviewers see different "innocent" versions of the page, making it harder for automated bots to flag the site as a gambling portal.Deceptive Asset URLs
- https[:]//static.lg1313abcwsx[.]com/googleInstall/lgparty_shareland_[1-12].png
- https[:]//static.lg1313abcwsx[.]com/site/ind/shareLand/page_[1-9].png
The images display download or install buttons, but the entire site is set up as an onClick event wrapper, which triggers a jumpHander function. The jumpHander does three things:
- Generates or retrieves a fbFingerId (Facebook Fingerprint ID) and stores it in the user’s localStorage
- Runs a Facebook Pixel event (PageView and ClickLand) to track that a "lead" clicked the ad.
- Redirects the user’s browser to a new URL, often to open a "Google Play" style link or an "intent" (to force open the browser on Android) to a subdomain like: https://pllay-godgle.{actor domain}.com
In the redirect action, the system uses "Jump Links" to move the user from the "Bridge Page" (the fake UI) to the actual malicious payload.
var o = "https://pllay-godgle.".concat(location.hostname).concat(location.search);return "intent://".concat(e.replace(/^https?:\/\//, ""), "#Intent;scheme=").concat(a, ";package=com.android.chrome;end")The final goal is to force the installation of a "Waistcoat" APK. The script contains a utility function to trigger a silent download and communicates with a backend API at /x2/lg-waistcoat/delivery/. The term "waistcoat" (马甲包) is a Chinese industry term for "shell apps" or "wrapper apps" — fake apps used to hide gambling content inside an innocent-looking shell to get past Apple/Google app store reviewers.
APK Filename: Dynamically generated as LGParty.apk or LG111.apk depending on the site configuration.
Download URL Pattern: https://apk-[current-domain]/apks/[siteName].apk?_ts=[timestamp]
Execution Logic: The code creates a hidden anchor element (__apk_dl_anchor__), sets the download attribute, and programmatically clicks it:
function c() {
var e = "".concat(o.Z.siteName, ".apk"); // "LGParty.apk"
var a = "https://apk-".concat(location.host, "/apks/").concat(o.Z.siteName, ".apk");
var n = document.createElement("a");
n.id = "__apk_dl_anchor__";
n.href = a;
n.download = e;
n.click(); // Triggers immediate browser download
}The goal is likely application side-loading. Google Play Store policy is quite clear on gambling and real money apps. They must have licenses to operate and complete an application process to be approved among other requirements. Because Google Play Store bans or prevents unlicensed or fraudulent real-money and gambling apps, groups may use "Waistcoat" (shell) pages, images, and fake Play Store UIs to trick the user into downloading a "verified" file from the real Play Store while trying to avoid detection. Once the .apk is installed, the app likely shows an innocent game (like a flight sim or puzzle) until it connects to its server, which can then flip a switch to load in and show the actual illegal gambling interface. In the case of these clusters, the external code update functionality suggests they were or could be used in this manner but there were no identified apps currently in the legitimate Google Play Store.
Broader Outlook and Trend Analysis
The architecture observed here, specifically the Cocos2d native bridge combined with bytecode encryption, is a hallmark of "Shell" applications used in financial fraud. By separating the distribution (spoofed websites) from the logic (encrypted JavaScript), threat actors can pivot regional themes (India vs. Philippines) with minimal changes to the underlying technical framework. With Clusters 1 and 2, this appeared to be the case as the applications sent device telemetry to external servers, then retrieved and loaded configuration and code from those external actor-controlled domains at runtime. It is suspected that both clusters operated with regional and device profile-based configurations. These configurations also enable the actor to change the behavior of the application at any time to load in malicious code after installation.
While there is no direct attribution identified thus far, this pattern has previously been associated with professional syndicates operating out of Southeast Asia that manage high-volume gambling and investment scams.
The core strategy relies on delivering illegitimate applications that deceive users into trusting them. This is accomplished through various deceptive tactics, including the spoofing of the Google Play Store, the fabrication of social proof such as reviews and win declarations, and the establishment of dedicated brand identities with widespread distribution. A key feature of these operations is the attempt to evade analysis by utilizing post-installation code and configuration fetched from actor-controlled domains.
While the applications do not appear to be overtly malicious in nature, as with typical malware granting remote access to user’s devices or stealing credentials, these applications pose as gambling and real money games with no regulation, oversight, or legitimacy. They can and likely do manipulate the gambling app behaviors such as having rigged results or non randomized outcomes.
Security Advice and Conclusion
This campaign highlights the critical role of managed app stores in the mobile ecosystem.
- Sideloading Risks: The primary defense against these campaigns is avoiding APK installations from non-standard sources. These apps require sideloading specifically because their core logic — such as the fake marquee module — would be flagged by the automated and manual review processes of legitimate stores such as Google Play Store.
- Fabricated Social Proof: Users should be informed that download counts, ratings, and reviews on spoofed websites are cosmetic HTML elements and do not reflect the application's actual standing or security.
- Managed Environments: Organizations should leverage Managed Google Play or Mobile Device Management (MDM) solutions to restrict the installation of apps from untrusted sources, as the "hot-update" capabilities of these frameworks allow an app to change its behavior entirely after it has been installed.
IOCs
Cluster 1: AA Aviator Game
Cluster 2: DK777 Related Apps
Cluster 3: LG Sabong App