I know I’m not the only one that flinched when a Log4j vulnerability dropped on the Thursday before Christmas. That it’s only a 6.3 allowed me to breathe again, but only shallowly.
Long before security, I spent my days in a 911 dispatch room soloing emergency calls and coordinating the response. The overlaps between that and cyber incident response are many, but two are worth calling out today. The first is that both types of response require forming an elaborate mental map of the emergency. And the second is that both types of response aren’t embodied; you’re at a workstation, processing and integrating in real time, but without the ability to physically release the tension involved.
The lack of physical embodiment is one of the reasons 911 calls can stick with you. Recall down to the waver in someone’s voice or something you think you heard in the background can be excruciatingly intimate and precise; the slosh of water in a tub, or the bark of an unrelated dog. And anchored to the desk as you are, there is no way to work the tension out of your body at the time. You learn to sit with it, and in turn the memories sit with you.
Some cyber incident response scenarios play out similarly. We can thrive on the tension, we can perform in near-superhuman ways across parallel tasks of critical importance for an extended period of time, we can love the thrill of pressure and the satisfied exhaustion of knowing how we handled it. But it all takes a toll, and that toll can stick with you.
We ignored it for a long time in Emergency Services, and in some ways still do. But it also resulted in the establishment of mechanisms like Critical Incident Stress Debriefing, mutually supportive ways to blow off steam while acknowledging the incident, and more. Many of us working remote, though, struggle more because the work desk hangs around our neck like an albatross, and we toss it as far as possible once the work day ends. But the stress of those incidents isn’t dealt with, and the mental and physical fatigue make after-hours efforts seem impossible.
Gauge how you and your team handle incidents. Figure out if you leave the stress in your body, or if you can find a way to work it out. It’s even more critical maintenance than replacing spinning disks – because when your stress response systems start throwing errors, they’re much harder to resolve.
Take care of yourselves out there. Take care of each other. We are all we’ve got.
Podcasts
Cyberwire – Root access to the great firewall – DomainTools Head of Investigations Daniel Schwalbe interviewed on our Great Firewall series. Definitely worth a listen – just editing these pieces kept me up at night, given the impact of realizations about the technologies behind the Great Firewall.
Articles
Intezer – Tracing a Paper Werewolf campaign through AI-generated decoys and Excel XLLs – Excellent find by Intezer, accompanied by a good writeup from Reuters. Only read after your coffee and when you’re prepared for statements like “An XLL is a native Windows DLL that Excel loads as an add-in, allowing it to execute arbitrary code” because I was not ready.
Infoblox – Parked Domains Become Weapons with Direct Search Advertising – More great work with an accompanying writeup by Brian Krebs. Parked Domains continue to be one of the most common threats I see in day-to-day hunting, so it’s good to see research in this area.
DomainTools Investigations – The APT35 Dump Episode 4: Leaking The Backstage Pass To An Iranian Intelligence Operation – The next in our APT35/Charming Kitten series, with some of the strongest writing I’ve seen from our team yet. Several phrases are going to stick with me for a while, but especially “the banality of intrusion.” The depth and breadth of bureaucracy involved is sort of amazing compared to other models.
Greynoise Intelligence – React2Shell research – Greynoise has assembled a boatload of supplemental data on their github for folks defending against the React2Shell vulnerability, or those looking to hunt for exploiters. C2 IPs and domains, full payloads, hashes, and more. Lots of credit goes to Greynoise for providing this to the community.
Research Papers and Reports
GA Tech et al – From Concealment to Exposure – Understanding the Lifecycle and Infrastructure of APT domains – Some incredibly important points here as far as domains being aged, IP/DNS changes prior to public disclosure causing defender issues, a need for much longer log retention than most organizations consider, and more.
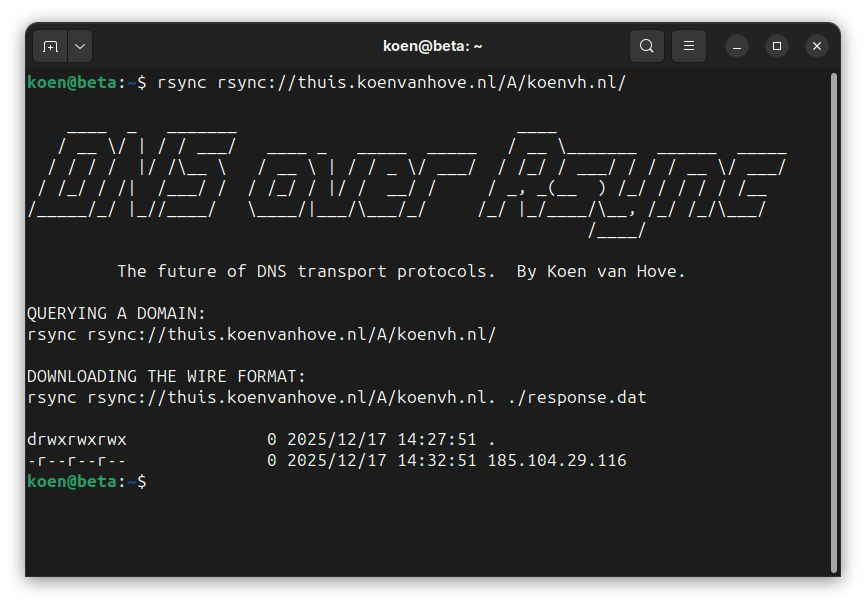
koenvh – DNS over rsync – Yes, you read that right. No, I won’t take it back, and you can’t make me. I saw it so you have to see it too, I don’t make the rules. It’s not the most cursed protocol I’ve ever seen, but it’s close.
Entertainment
The Onion – Study Finds 80% Of Americans Lack Social Connections To Pull Off Heist – Something tells me the readership for this list probably skews much further toward being able to crew a heist with their network, but that’s just a guess.