This research analyzes Proton66, a bulletproof hosting network enabling cybercrime operations, serving as a hub for aspiring cybercriminals. It focuses on threat actor, known as "Coquettte" and their ties to the Horrid hacking group, a loosely organized cybercriminal collective fostering amateur threat actors.
Bulletproof Hosting Networks and Proton66
While researching malicious domains hosted on Proton66, we stumbled upon an intriguing discovery—a fake cybersecurity website, cybersecureprotect[.]com, masquerading as a legitimate antivirus service. However, due to an operational security (OPSEC) failure, this domain left its entire malicious infrastructure exposed. This revelation led us down a rabbit hole into the operations of an emerging threat actor known as Coquettte—an amateur cybercriminal leveraging Proton66’s bulletproof hosting to distribute malware and engage in other illicit activities.

Proton66, a well-known Russian bulletproof hosting provider, has long been a haven for cybercriminals looking to operate with impunity. By investigating cybersecureprotect[.]com, we uncovered a larger network of malicious activity, including credential-stealing malware, keyloggers, and trojans, all distributed through Proton66’s infrastructure. Interestingly, Coquettte’s criminal ventures are not limited to malware. Investigators uncovered other projects operated by this actor that suggest a broad interest in illicit activities. One notable example is a website hosted at meth[.]to, which purports to distribute guides on the manufacture of Methamphetamine, C4/Semtex, flashbangs, napalm, and catalytic converter theft. While the site appears to contain detailed instructions, it remains unclear whether the content is genuinely intended as a resource for criminal activity or if it falls into the realm of dark humor, shock content, or trolling.
This analysis provides a detailed technical analysis of Coquettte’s malware infrastructure, including forensic insights into how their campaigns function, the threat posed by Proton66 as a cybercrime enabler, and a comprehensive list of indicators of compromise (IOCs) that security professionals can use to detect and mitigate related threats.
Proton66 as a Threat Actor Breeding Ground
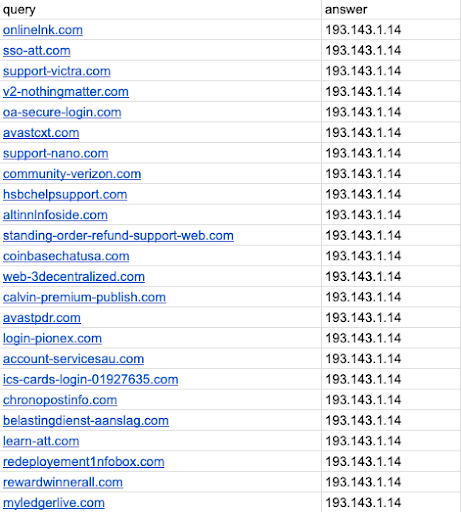
Proton66 is a Russian bulletproof hosting provider (Autonomous System AS198953) notorious for enabling cybercrime by ignoring abuse complaints. In a 2024 threat intelligence report by Intrinsec, researchers identified Proton66 as a key player in the bulletproof hosting arena, facilitating illicit online activities such as malware distribution and phishing campaigns. What sets Proton66 apart is its appeal to less-experienced threat actors; its services allow even amateur hackers to host malicious content with impunity. Many phishing and credential-harvesting sites on Proton66 impersonate major brands (e.g. AT&T, Netflix, GoDaddy, banks, crypto exchanges, and government portals) to steal user data. These operations often exhibit poor OPSEC, indicating the operators are relatively inexperienced.
Example of malicious domains:
Threat Actor “Coquettte” and Their Malware Infrastructure
One emerging threat actor thriving in the Proton66 ecosystem goes by the handle “Coquettte” (note the triple “t”). Coquettte appears to be an amateur cybercriminal leveraging Proton66’s services to deploy malware under the guise of legitimate software. Investigators first uncovered Coquettte’s activities through the domain cybersecureprotect[.]com, a fake cybersecurity product site hosted on Proton66. The website pretended to offer “CyberSecure Pro” antivirus software, but due to an OPSEC failure, its web directory was left publicly accessible – revealing the malicious files within.
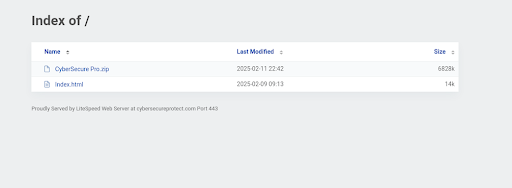
The directory contained a compressed zip file (CyberSecure Pro.zip) of a Windows Installer - CyberSecurePro.msi, which is actually the malware droppers rather than security software. When executed, the install reaches out to two hard coded URLs: cia[.]tf and quitarlosi[.], downloads a second-stage payload and drops additional executables from the threat actor controlled servers.
Analysis of the retrieved payload revealed that it was flagged as Rugmi (also known as Penguish or associated with the Amadey loader) – a modular malware loader commonly used by cybercriminals to deploy various secondary payloads such as infostealers, trojans, and ransomware. The specific SHA-256 hash of the Rugmi-infected installer was:
a07c9275d2628f6dee9271452a66683831d21367a63cdb61ade0fac55f3ed9ff (CyberSecure Pro[.]zip).
Execution Flow of the Malware:
- Compressed Archive: CyberSecure Pro[.]zip (SHA-256: a07c9275d2628f6dee9271452a66683831d21367a63cdb61ade0fac55f3ed9ff)
- Windows Installer Dropper: CyberSecure Pro.msi (SHA-256: 5558b04220e017f2a69fd88c575ec9450bde361049e42fd67501a0f89ba21834)
- Dropped Files: Upon execution, the .msi file extracts additional payloads, including:
- CyberSecureV.exe (SHA-256: 0983d99e87d9300d4a1b54c08d9a365160e406e4cd681bfd6ef82052d932a5b4) and stapelia.exe (SHA-256: 1487a4f637a68a5b1dadc379e770431d591421218818164add86c02853a433aa) – Identified as Trojan.Rugmi/Penguish, a loader trojan used to deliver infostealers such as Lumma Stealer, Vidar, RecordBreaker, and Rescoms.
- Configuration scripts and batch files to maintain persistence and execute additional payloads.
Trojan.Rugmi/Penguish’s Role in the Attack:
Rugmi/Penguish is a malware loader designed for stealthy payload delivery. It typically:
- Fetches additional malware (infostealers, trojans) from attacker-controlled servers.
- Evolves its delivery tactics, often used in conjunction with cracked software or fake security products.
- Uses obfuscation techniques to bypass antivirus detection.
- Communicates with C2 servers, like cia[.]tf, to receive commands and drop additional payloads.
Coquettte’s personal website, coquettte[.]com, provided additional insights into their online presence. The site, hosted on AWS, at one point displayed a message stating “18 years old software engineer, pursuing a degree in Comp Sci.” This suggests that Coquettte is a young individual, possibly a student, which aligns with the amateurish mistakes (like the open directory) in their cybercrime endeavors.
Further investigation revealed that the cia[.]tf domain, which was used as a malware command-and-control (C2) server, was registered with the email address root[@]coquettte[.]com. This direct link confirmed that Coquettte not only operated cybersecureprotect[.]com as a malware distribution hub, but also controlled cia[.]tf, which facilitated the downloading and execution of malware payloads. By analyzing registration records and domain relations, researchers identified additional infrastructure linked to Coquettte, indicating a broader cybercriminal operation that leveraged Proton66’s bulletproof hosting to persist despite takedown efforts.
Additional Malicious Activities by Coquettte
Interestingly, Coquettte’s criminal ventures are not limited to malware. Investigators uncovered other projects operated by this actor that suggests a broad interest in illicit activities. One notable example is a website hosted at meth[.]to – which, as the name implies, contains how-to guides for illegal substances and weapons.

The site allegedly provides (unverified) recipes and instructions for manufacturing methamphetamine, making explosives like C4/Semtex, constructing improvised devices (e.g. flashbangs, napalm), and even guides on catalytic converter theft. In essence, it functions as an illicit knowledge base or black-market tutorial site. The presence of such content indicates Coquettte (or their associates) are dabbling in the darker corners of cybercrime beyond just malware – potentially trying to run or contribute to an underground marketplace or forum for criminal activities.
Affiliated or Associated Hacking Groups: Horrid[.]xyz and Other Connections

Further analysis of Coquettte’s infrastructure suggests potential ties to a broader hacking group or collective operating under the name “Horrid.” A domain linked to Coquettte, horrid[.]xyz, was registered by the same group and appears to be part of their extended ecosystem. Several other domains associated with their infrastructure include:
- terrorist[.]ovh
- meth[.]to
- meth[.]su
Both meth[.]to and meth[.]su hosted identical content, purporting to distribute guides on illicit activities, while terrorist[.]ovh was similarly structured. The pattern of overlapping infrastructure suggests that the individuals behind these sites may refer to themselves as “Horrid,” with Coquettte being an alias of one of the members rather than a lone actor.
Additionally, a Google Analytics tracker (G-RPK032CCFZ) embedded in some of their sites was linked across at least four domains, further confirming shared ownership:
- horrid[.]xyz
- terrorist[.]ovh
- meth[.]to
- meth[.]su
These interconnections reinforce the likelihood that “Horrid” operates as a small, loosely structured hacking collective rather than a single individual. The group's affiliation with multiple domains tied to cybercrime and illicit content suggests that it functions as an incubator for inspiring or amateur cybercriminals, providing resources and infrastructure to those looking to establish themselves in underground hacking circles.
Additional Online Presence and Linked Accounts
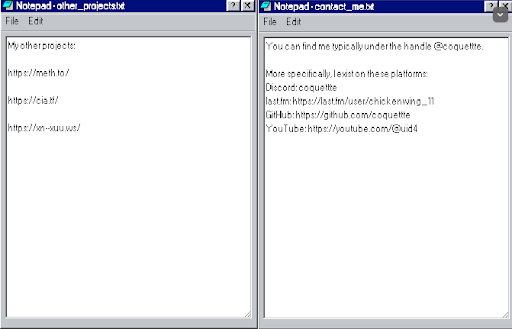
Beyond their own hosted infrastructure, Coquettte and their associates have left digital footprints across multiple platforms. Several of these accounts were referenced directly on coquettte[.]com in a file titled Contact_me.txt, listing the following links:
- GitHub: github[.]com/coquettte – Personal GitHub repository, potentially containing malware-related code or past projects.
- YouTube: youtube[.]com/@uid4 – (also has the alias “chickenwing_11”) Possible media or tutorial content associated with the group, which may serve to share tactics with aspiring cybercriminals.
- Last.fm Profile: last[.]fm/user/chickenwing_11 – While less directly relevant, this could be a personal account linked to the actor.
Additionally, some of their own infrastructure was self-referenced in Coquettte’s personal website (coquettte[.]com) in a file titled other_projects.txt, which listed:
- Meth[.]to: (https://meth[.]to/) – A site purporting to distribute guides on illicit activities.
- Cia[.]tf: (https://cia[.]tf/) – A malware hosting and C2 domain frequently observed in cybercriminal activities.
- Xn--xuu[.]ws: (https://xn--xuu[.]ws/) – A site that emulates a Linux terminal, which uses code from a community project mercurywork[.]shop, further linking their infrastructure to additional cyber-related projects.
The presence of direct self-references across multiple sites reinforces the interconnected nature of these domains, confirming a shared infrastructure between Horrid, Coquettte, and cia.tf. More importantly, these platforms appear to act as a launchpad for aspiring cybercriminals, giving them access to malware, hosting solutions, and potentially a network of like-minded individuals willing to collaborate on cyber threats.
Proton66 Cyber Threats: Vigilance Needed Against Emerging Malware and Amateur Actors
Proton66-based threats require vigilance on multiple fronts. While the individual threat actor “Coquettte” may be relatively amateur, the malware they deploy (stealers, keyloggers, etc.) can do serious damage if successful. The combination of a bulletproof hosting haven and accessible malware toolkits lowers the bar for entry into cybercrime, meaning even minor actors can pose a risk to organizations. By staying aware of the Proton66 network’s activities and aggressively monitoring for the IOCs and techniques detailed above, security teams can bolster their defenses against this breeding ground of emerging threats.
IOCs on GitHub
If the community has any additional input, please let us know.
https://github.com/DomainTools/SecuritySnacks/blob/main/2025/Proton66-Coquettte
Sign Up For DomainTools Investigations’ Newsletter for the Latest Research
Want more from DomainTools Investigations? Be sure to sign up for our monthly newsletter to get the latest research from the team – available on LinkedIn or email.