September is coming to a close, and with it, the sun bids adieu to Seattle (my home base) for another six months or so. Anybody who has lived here for more than a couple of years can recognize the exact day it happens. It’s a different date every year, but it’s unmistakable! In just 24 hours, it goes from pleasantly sunny, low 70s weather (low 20s C for my international friends) to min-50s (mid-teens in C) and rain. Summer is over, and the grey gloom returns to give birth to the Pumpkin Spice Latte. That day was yesterday 😕
But it’s not all bad. With less available daylight, we give ourselves permission to spend more time inside, and that means more time for research! If you are a returning reader, welcome back! If you are a new reader, what you are about to read is news from our group of researchers and analysts, where they provide their expertise in investigating, mitigating, and preventing Domain and DNS based attacks.
My team has been on a tear this month, we've published new research on Salt Typhoon, an advanced Chinese APT, and we've analyzed the massive Kimsuky leak, giving us a rare look into a North Korean threat actor's playbook. We also identified new activity from the PoisonSeed e-crime group, and uncovered a banking trojan targeting Android users in Southeast Asia. Let's get you up to speed!
Hot off the Presses
Inside Salt Typhoon: China’s State-Corporate Advanced Persistent Threat
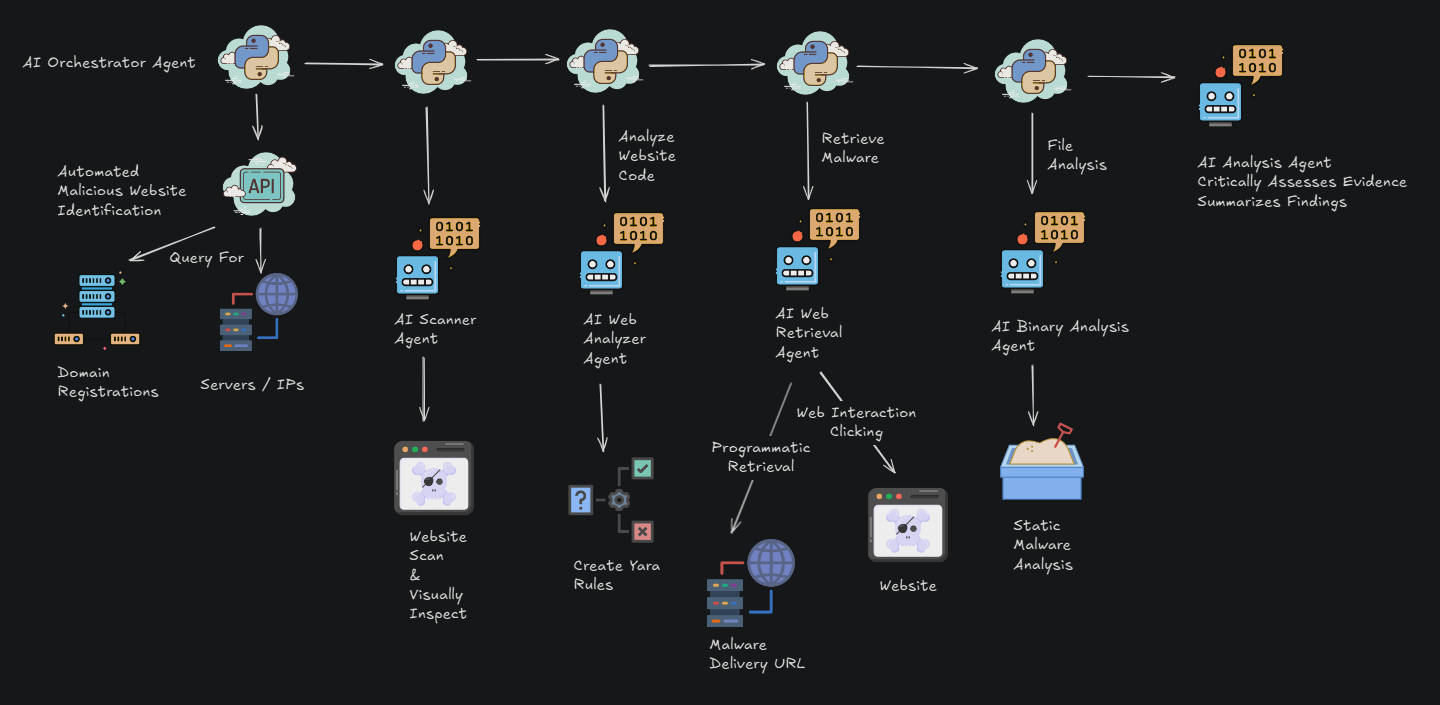
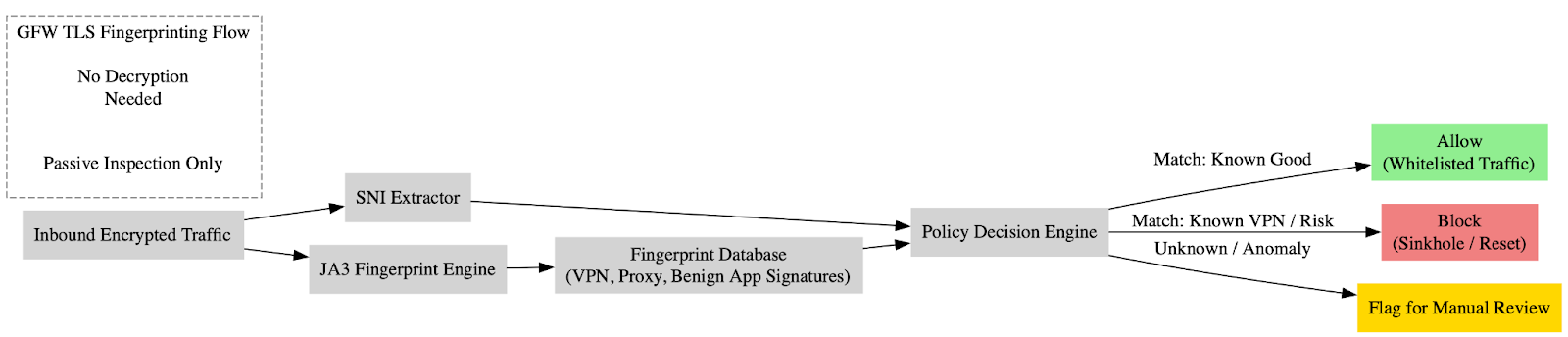
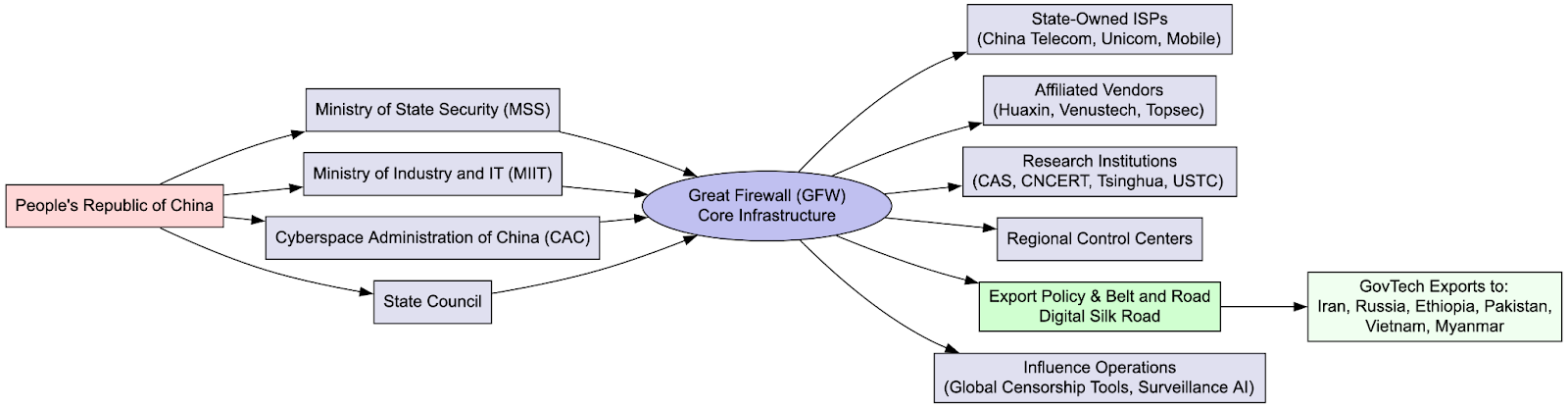
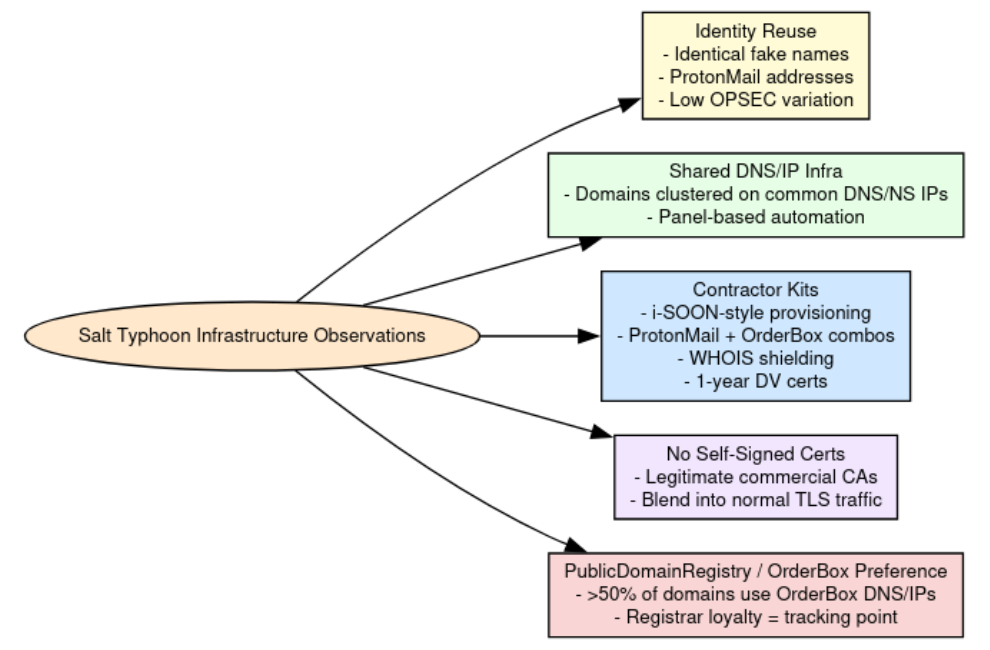
Less than a week ago (25 September), we published research that maps Salt Typhoon’s infrastructure and operational profiles. The APT linked to the PRC’s Ministry of State Security has a targeting profile that spans the U.S., U.K., Taiwan, and the E.U., with confirmed breaches in at least a dozen U.S. telecom firms, multiple state National Guard networks, and allied communications providers. The research covers known intelligence and operational profiles, links to other entities within the PRC’s cyber espionage apparatus, and a deep dive into the infrastructure and behavioral patterns uncovered by our researchers.
Salt Typhoon has demonstrated sophisticated spycraft in exploiting network edge devices, maintaining long-dwell persistence via firmware/rootkit implants, harvesting data from telecom providers, and using plausibly deniable contractor infrastructure to obscure attribution. Our research provides crucial intelligence for attribution, detection, and threat modeling of the observed activity.
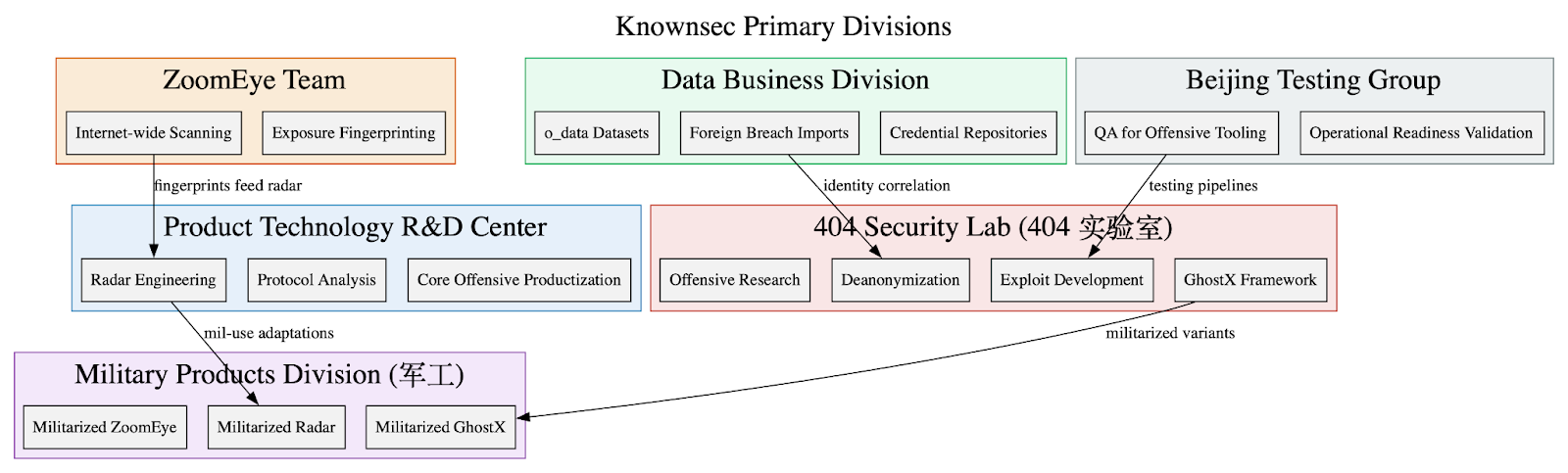
Inside the Kimsuky Leak: How the “Kim” Dump Exposed North Korea’s Credential Theft Playbook
DTI researchers broke down the “Kim” leak, mapping the full scope of the North Korean threat actor’s infrastructure from custom Linux rootkits to particular targets like PKI infrastructure and specific tools like NASM and ocrmypdf. Our analysis also found a strategic pivot to include Taiwanese developer and government networks, revealing a clear geographical expansion of North Korea's cyber interests.
The leak provides a unique opportunity to look directly into a DPRK threat actor’s playbook. Moreover, it gives analysts and defenders insight into the actor’s operational profile, including credential-focused intrusions targeting South Korean and Taiwanese networks, with a blending of Chinese-language tooling, infrastructure, and possible logistical support.
—-----
Newly Identified Domains Likely Linked to Continued Activity from PoisonSeed E-Crime Actor
DTI researchers identified a set of malicious domains likely linked to the e-crime group known as PoisonSeed. The identified domains spoofed the email sender platform SendGrid and used fake Cloudflare CAPTCHA pages to steal enterprise credentials, with similar tactics, techniques, and procedures (TTPs) as those historically tied to SCATTERED SPIDER.
While there is no definitive evidence of a direct link between PoisonSeed and SCATTERED SPIDER, the infrastructure identified as belonging to PoisonSeed highlights ongoing efforts by e-crime actors to use TTPs similar to SCATTERED SPIDER. These actors are likely continuing to leverage these TTPs to compromise enterprise credentials to facilitate a range of malicious activity.
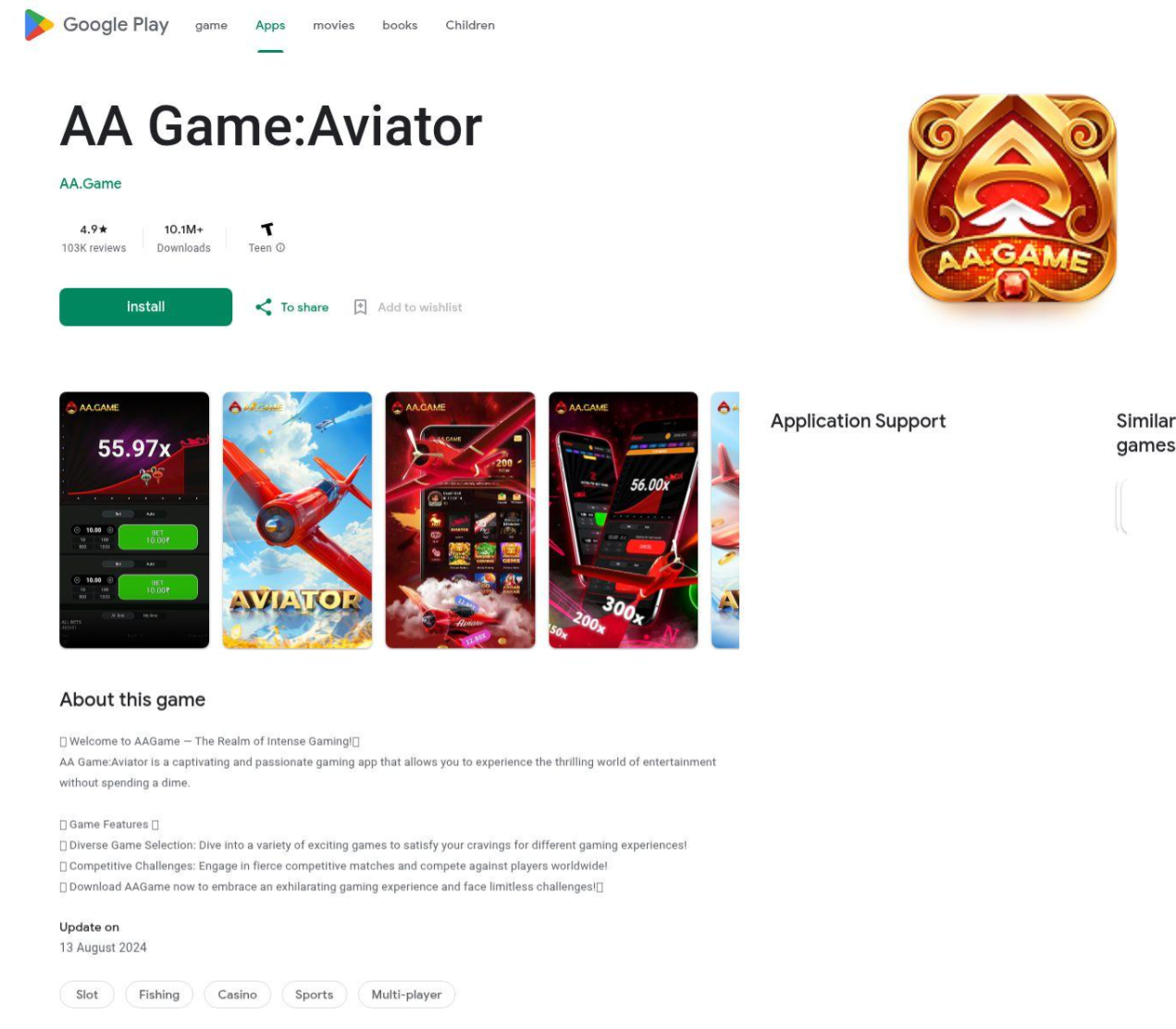
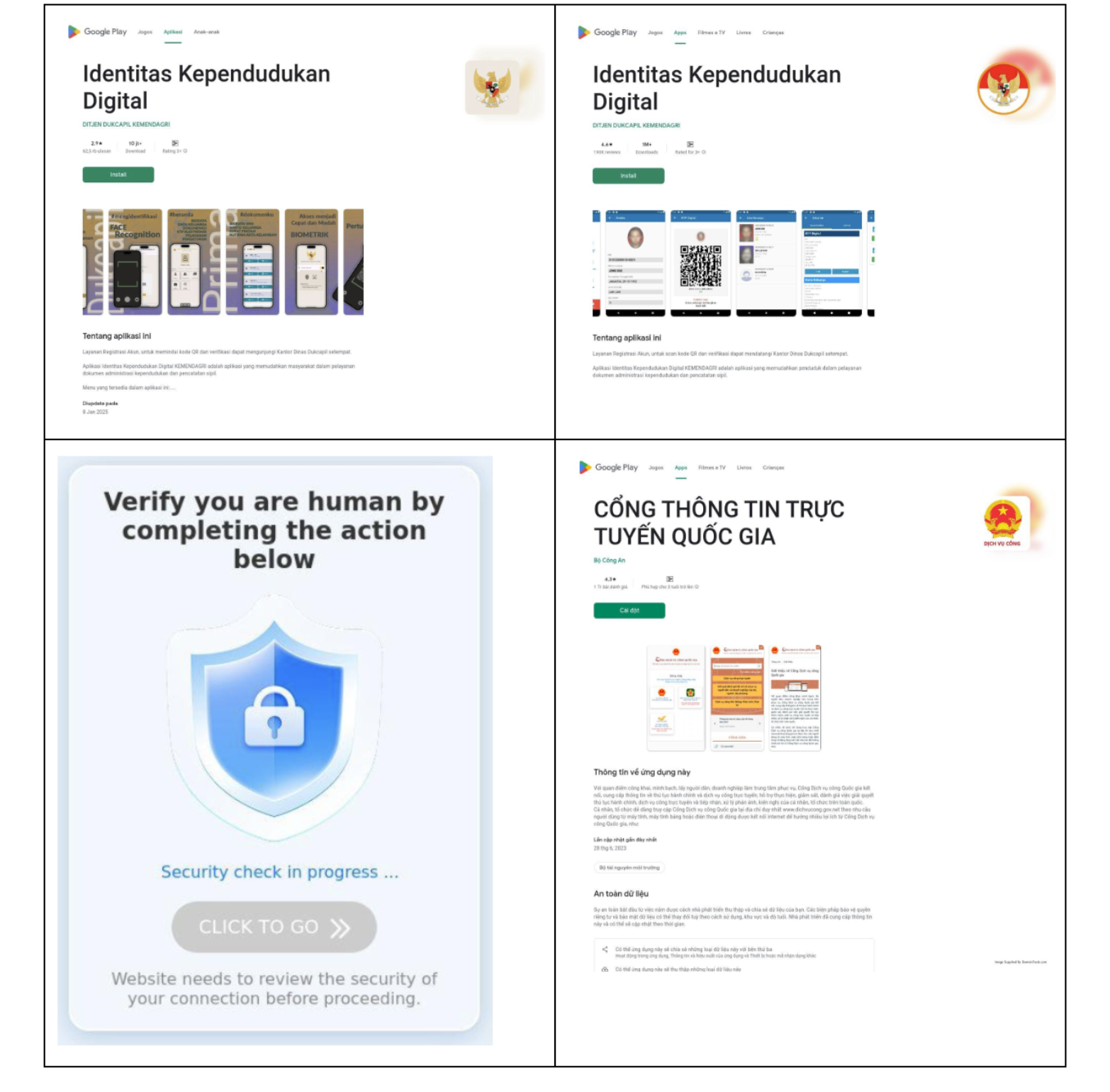
Banker Trojan Targeting Indonesian and Vietnamese Android Users
DTI researchers observed a threat actor spoofing trusted platforms like the Google Play Store to target Android users in Southeast Asia. The actor disguised their malware as legitimate payment and government identity applications to trick Indonesian and Vietnamese users into downloading malware linked to BankBot.Remo.1.origin, a previously closed source banking trojan that had its source code leaked on Russian-language forums in 2016.
—-----
What We’re Reading
With the arrival of fall, and back to school season in full swing, it got me thinking: Wouldn’t it be great if there were a scholastic book fair for cybersecurity? Well there isn’t, but there is my colleague Ian Campbell's monthly recommended reading list for September:
- The top article for the month: The Record - Ransomware gang takedowns causing explosion of new, smaller groups
- The top podcast for the month: Microsoft Threat Intelligence - Stopping Domain Impersonation with AI
- The top research for the month: arXiv - Large Language Models for Security Operations Centers: A Comprehensive Survey
📚Check out the full reading list here 📚
Where We’ll Be
- BSidesNOVA, Arlington, VA, 10-11 October
- GovWare, Singapore, 21-23 October
- TechNet Indo-Pacific, Honolulu, HI, 28-30 October
Final Thoughts
As always, thank you to my returning readers! If you’re new, I hope you found this newsletter informational, helpful, and worthy of sharing with your peers. And of course I hope you will keep coming back to read future editions!
We share this newsletter via email as well - if you’d prefer to get it to your inbox, sign up here.
If you missed last month's content, here are some quick links:
- From Laptops to Laundromats: How DPRK IT Workers Infiltrated the Global Remote Economy
- Hunting for Malware Networks
- SpyNote Malware Part 2
Thanks for reading - see you next month!
-Daniel