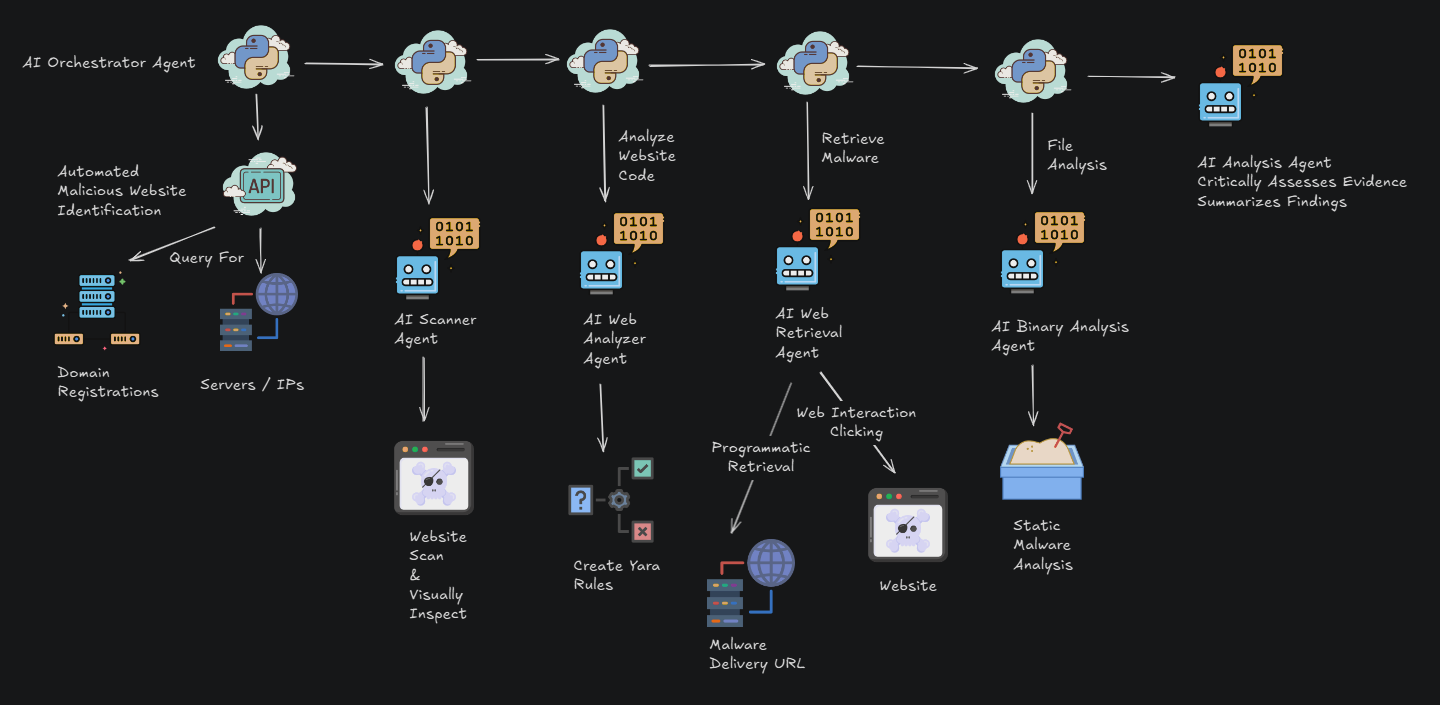
Newly Identified Domains Likely Linked to Continued Activity from PoisonSeed E-Crime Actor
DomainTools Investigations identified a set of malicious domains registered since 01 June 2025 likely linked to the ecrime actor publicly known as PoisonSeed. These domains primarily spoof the email platform SendGrid and are likely attempting to compromise enterprise credentials of SendGrid customers. They display fake Cloudflare CATPCHA interstitials to add legitimacy to malicious domains before redirecting targeted users to phishing pages. We did not identify specific targets, but public information indicates PoisonSeed’s historical target scope comprises cryptocurrency platforms and enterprise environments.
PoisonSeed tactics, techniques, and procedures (TTPs) bear similarities to those historically linked to SCATTERED SPIDER. There has been significant media reporting about SCATTERED SPIDER adversary in recent weeks due to high-profile compromises against retailers, grocery chains, insurance providers, and airlines across the U.S., the U.K. and Canada. Some of these compromises led to significant business disruption. We have no evidence to connect the recently identified domains to operations against companies within these sectors; however, potential links between these actors is notable given the impact of recent compromises.
New PoisonSeed Infrastructure
Industry reporting originally identified the PoisonSeed actor in April 2025. That report described PoisonSeed’s use of SendGrid phishing domains to facilitate cryptocurrency theft. In May 2025, the Mimecast Threat Research team published a blog describing similar activity in which an actor leveraged phishing campaigns impersonating service providers such as SendGrid to deliver fraudulent notifications to the providers’ users. The ultimate objective of these campaigns was to harvest enterprise credentials and use them to facilitate further phishing campaigns and lateral movement within targeted enterprise environments.
Mimecast reported that a key element of the phishing campaigns was the use of fake Cloudflare CAPTCHA interstitials. Specifically, these interstitial pages included fake Cloudflare Ray ID data. Additionally, domain registration and hosting patterns included:
- Domains registered via the NiceNIC International Group Co. registrar
- Domain names primarily containing references to SendGrid, as well as more generic digital services such as single sign-on (SSO) and login portals
- Hosting on IP addresses assigned to the provider Global-Data System IT Corporation (AS42624)
We identified 21 domains registered since 01 June 2025 that match the elements identified in the Mimecast blog post. The majority of these domains reference SendGrid, and those that do not were co-hosted on IP addresses alongside SendGrid-spoofing domains and referenced other, more generic digital services. Information from URLScan.io showed that several of these domains displayed fake Cloudflare CAPTCHA interstitials and contained fake Cloudflare Ray ID data consistent with public reporting.
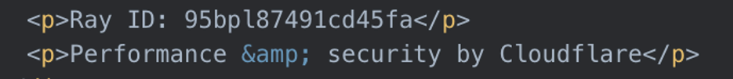
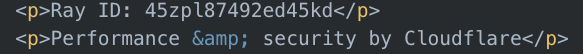
Table 1. PoisonSeed Domains Registered Since 1 June 2025
We have uploaded a list of several hundred domains identified with the same fingerprint to our Github for further research, analysis, and hunting.
Relationship to SCATTERED SPIDER
Mimecast’s blog attributed the malicious activity to SCATTERED SPIDER - an ecrime adversary engaged in financially-motivated activity since 2022 Our research indicates that the activity is likely attributable to the PoisonSeed actor based on use of the fake Cloudflare CAPTCHA interstitials and domain naming and registration similarities. However, it is plausible that PoisonSeed has historical or current connections to SCATTERED SPIDER.
The SCATTERED SPIDER adversary is linked to a diverse group of threat actors referred to as “The Com.” The adversary’s early operations typically combined smishing, SIM-swapping, and MFA push-notification fatigue to gain access to enterprise environments. However, the nature of a group like The Com has likely allowed SCATTERED SPIDER membership to change over time with new members bringing new skill sets such as advanced social engineering techniques aimed at companies’ IT helpdesks as well as ransomware affiliations. Additionally, former SCATTERED SPIDER operators may have left the group and continued to use some of the TTPs historically used by the adversary in new criminal operations.
It is plausible that similarities between PoisonSeed’s operations and those of SCATTERED SPIDER could be the result of PoisonSeed actors having a level of affiliation with the adversary itself or, more generally, with The Com collective. Additional research into PoisonSeed activity is necessary to more definitively establish this connection.
Assessment
The infrastructure identified in this blog highlights ongoing efforts by ecrime actors such as PoisonSeed to use tactics, techniques, and procedures (TTPs) historically similar to SCATTERED SPIDER. These actors are likely continuing to leverage these TTPs to compromise enterprise credentials to facilitate a range of malicious activity including phishing campaigns, cryptocurrency theft, data theft, and extortion.
Editor's note: Research for this article was conducted in July 2025, and conclusions are based on the information available at that time.
Related Content
APT35/Charming Kitten's leaked documents expose the financial machinery behind state-sponsored hacking. Learn how bureaucracy, crypto micro-payments, and administrative ledgers sustain Iranian cyber operations and link them to Moses Staff.