Mapping Hidden Alliances in Russian-Affiliated Ransomware
Understanding the landscape of cyber threats, particularly Russian-affiliated ransomware, is a complex and evolving challenge. The traditional model of tracking distinct, unified ransomware groups is becoming increasingly difficult. In the "post-Conti era," ransomware has transformed into a marketplace of mutations. It's no longer about centralized operations but rather a fractured ecosystem where allegiances shift and connections are often hidden.
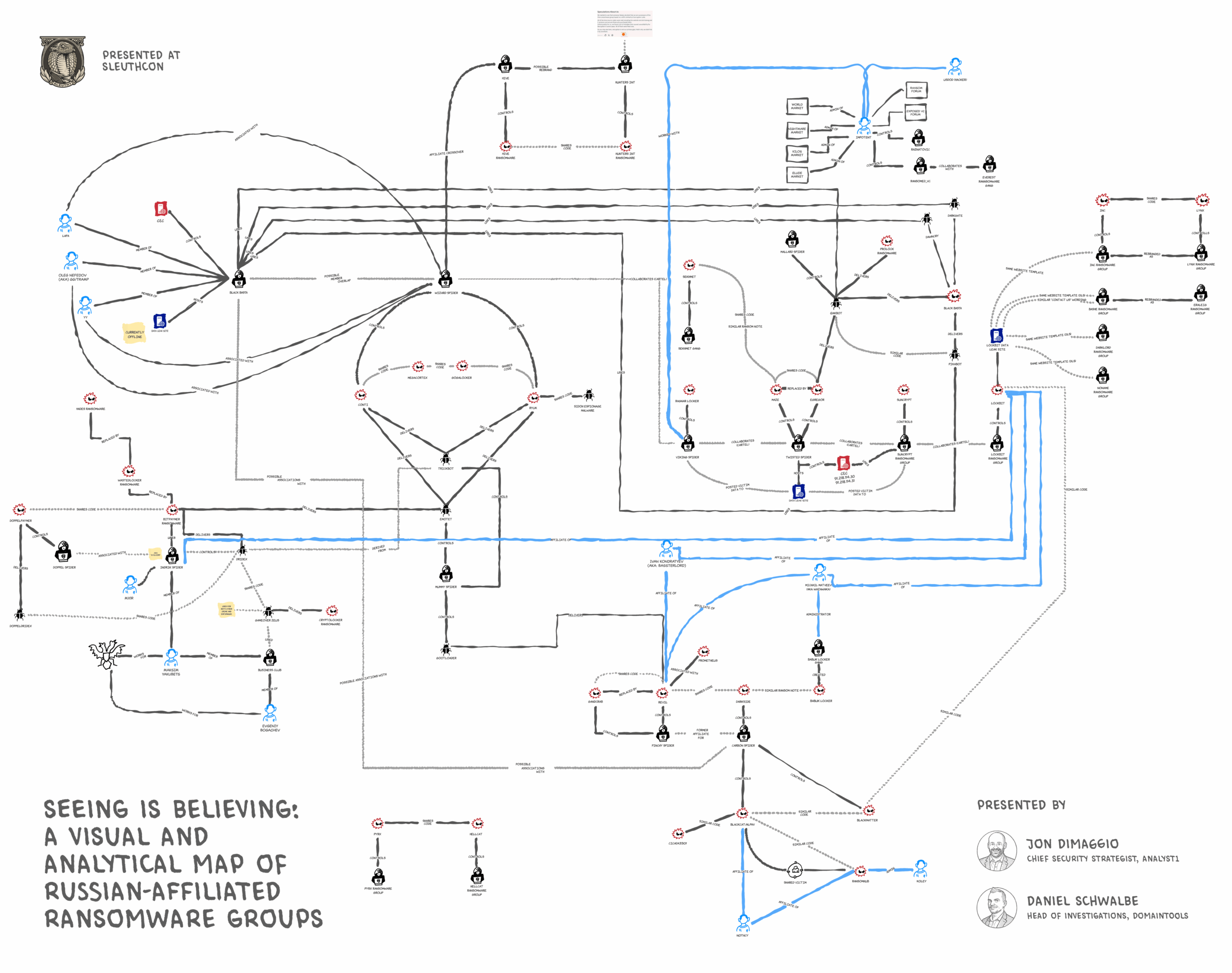
In order to develop a deeper understanding and help others in the community in the process, Jon DiMaggio at Analyst1, Scylla Intel, and the DomainTools Investigations Team dove into a research project that culminated into a detailed infographic called “A Visual and Analytical Map of Russian-affiliated Ransomware Groups.” This work follows previous research DomainTools undertook in tracking ransomware families and provides a visual representation of complex connections in this space.
The goal of this project was not simply attribution or listing individual groups. Instead, we set out to map hidden connections between criminal factions, going beyond just mapping "families" to understand the intricate relationships between them. The core focus was on identifying overlaps in human operators, code fragments, infrastructure, and TTPs (Tactics, Techniques, and Procedures).
The Creation Process: A "Spider-Out" Investigation
Creating this map required a deep dive into the operational realities of various ransomware actors. Our methodology involved performing a "spider-out" incremental investigation. We began with well-known groups like Conti, LockBit, and Evil Corp, then expanded our research outwards, following the threads of connection.
To gather the necessary information, we drew upon a variety of sources:
- OSINT (Open-Source Intelligence)
- Historic infrastructure data
- Proprietary threat intelligence
- HUMINT (Human Intelligence)
It's important to note that the analysis only includes publicly available information; nothing is revealed that could tip off adversaries.
Our analysis of these diverse data points helped isolate valuable signals from the surrounding noise. This included overlapping IP addresses, passive DNS records, shared certificates, web content, and delivery vectors used by different groups. These infrastructure overlaps imply potential resource pooling, bulletproof hosting, or affiliate-level reuse. We also analyzed code and TTP crossovers, such as the overlap between Black Basta and Qakbot or the use of legacy Trickbot infrastructure. The prevalence of shared tools like AnyDesk and Quick Assist also suggested common training, playbooks, or crossovers in operator organizations. And finally, we looked closely at the most important element, the people in these groups.
Visualizing the Overlaps: Human Capital and Operator Drift
Perhaps one of the most significant findings visualized in the infographic is the human overlap and operator drift. Our research uncovered instances of known individual actors migrating across different ransomware ecosystems. For example, sources indicate individuals like “Wazawaka” have been associated with multiple groups including REvil, Babuk, LockBit, Hive, and Conti. Similarly, "Bassterlord" moved from REvil to Avaddon, then to LockBit, and finally to Hive.
This phenomenon highlights a crucial insight: brand allegiance among these operators is weak, and human capital appears to be the primary asset, rather than specific malware strains. Operators adapt to market conditions, reorganize in response to takedowns, and trust relationships are critical. These individuals will choose to work with people they know regardless of the name of the organization. Indeed, rebranding in this context is a feature, not a bug. The infographic helps to visualize how these individuals move between groups, carrying their expertise and capabilities with them.
Key Takeaways from the Mapping:
The creation of this infographic reinforces several strategic takeaways:
- Reuse does not equal identity. Different groups may share code or have human overlap but are not the same entity.
- Group labeling is increasingly obsolete.
- The modern threat landscape is best understood by tracking clusters of activity, not just named groups, and focusing on similar activity rather than specific names.
This new perspective, visually represented in this infographic, is crucial for understanding how ransomware operations function today. Groups act like modules, specializing and adapting as the marketplace matures. They exhibit a separation of responsibilities, with distinct roles for negotiators, developers, infrastructure managers, and leadership. Sanctions evasion strategies, such as Evil Corp’s repeated rebranding paired with infrastructure reuse, prove that while names may change, capabilities endure.
Understanding these hidden alliances and overlaps is key to developing and maturing more effective disruption strategies. As a community, we need to evolve how we track actors and criminal brands, recognizing that shared infrastructure or website artifacts might serve as more stable "fingerprints" than group names.
The full infographic provides a comprehensive visual guide to these complex relationships. We believe this work offers a new lens through which to view and counter Russian-affiliated ransomware, emphasizing the need to understand the underlying ecosystem and human networks rather than just transient names and tools.
Related Content
APT35/Charming Kitten's leaked documents expose the financial machinery behind state-sponsored hacking. Learn how bureaucracy, crypto micro-payments, and administrative ledgers sustain Iranian cyber operations and link them to Moses Staff.