A Profile of Iran’s Covert Cyber Strike Unit and Its Psychological Warfare Extension
Executive Summary
Intelligence Group 13, embedded within the Shahid Kaveh Cyber Group, represents one of the most operationally aggressive and ideologically fortified units within the Islamic Revolutionary Guard Corps (IRGC) cyber arsenal. Positioned at the confluence of tactical cyber-espionage, industrial sabotage, and psychological warfare, the group is uniquely equipped to respond to geopolitical escalations,particularly in light of the recent U.S. airstrikes targeting Iranian nuclear facilities, which have significantly heightened the risk of asymmetric retaliation.
As Iran faces intensified pressure and public calls for reprisal, it is assessed that it is increasingly likely that IRGC cyber divisions will be leveraged for retaliatory digital operations. Intelligence Group 13, already known for its history of intrusions into critical infrastructure, including U.S. water systems and Israeli control networks, now finds itself in a strategic posture to deliver retributive action through cyberspace. Whether through direct disruption, pre-positioned malware activation, or narrative defacement and psychological intimidation, the group's capabilities make it a prime tool for hybrid response, combining deniable technical aggression with symbolic messaging designed to project defiance and psychological impact.
Functioning under the umbrella of the IRGC’s broader cyber command, which includes the Electronic Warfare and Cyber Defense Organization (EWCD), the Intelligence Organization (IO), and Quds Force forces like Unit 300, Intelligence Group 13 is not an isolated cell but part of a highly coordinated ecosystem. Its online presence is reinforced by propaganda fronts such as CyberAveng3rs, a media arm that issues threats, amplifies operational claims, and disseminates defacement content through platforms like Telegram and Instagram. Together, these assets form a multi-domain influence architecture that allows Iran to execute cyber retaliation while shaping the narrative battlefield.
This report maps the hierarchy of Intelligence Group 13 within the IRGC, profiles its leadership, outlines its tradecraft and ideological underpinnings, and assesses the increased likelihood of its deployment in near-term retaliatory cyber operations.
Intelligence Team (Group) 13 تیم اطلاعاتی ۱۳
The group, (pronounced: Team-e Ettela'ati-ye Sizdah), takes its name from Mohammad Kaveh, an IRGC commander who was martyred during the Iran-Iraq War in 1986 at the age of 25. He led elite IRGC operations in Kurdistan and Western Iran and was viewed as a revolutionary model for sacrifice, bravery, and obedience. In keeping with the IRGC’s broader ideological tradition, the title “Shahid” (شهید), meaning martyr, is commonly affixed to the names of operational units, serving both as an homage to fallen commanders and a deliberate invocation of religious-nationalist symbolism. This naming convention reinforces the ideological continuity between the IRGC’s early revolutionary battles and its modern digital warfare initiatives. By invoking martyrdom, such units portray their operations not merely as tactical missions but as sacred continuations of a historical and spiritual struggle. The Shahid Kaveh Group draws directly from this legacy to infuse its cyber operations with ideological legitimacy and emotional resonance. The archived site kaveh313[.]lxb[.]ir hosted tributes, biographical stories, and hagiographic imagery that inform the spiritual framework for the group’s name and mission, blending religious devotion, revolutionary ethos, and digital militarism into a unified operational identity.

IRGC Cyber Command Hierarchy
The Islamic Revolutionary Guard Corps (IRGC) oversees a complex and multi-tiered cyber command architecture designed to fulfill distinct yet interconnected missions across domestic security, intelligence collection, and global offensive operations. This structure is deliberately compartmentalized, allowing the IRGC to conduct covert campaigns while maintaining plausible deniability through the use of proxy units, contractors, and front companies. At the core of this system is the Shahid Kaveh Group, an elite offensive cyber unit that operates with both ideological fervor and technical precision. Intelligence Group 13, its most active tactical team, is fully embedded within this command, drawing operational directives from a triad of IRGC oversight bodies:
- The Electronic Warfare and Cyber Defense Organization (EWCD), which coordinates cyber defense and internal sabotage capabilities,
- The Intelligence Organization (IO), responsible for domestic surveillance and strategic targeting intelligence, and
- The Quds Force (QF), which projects IRGC influence and cyber aggression abroad, particularly through specialized units like Unit 300 and Unit 600.
Together, these divisions provide the Shahid Kaveh Group,and by extension Intelligence Group 13, with the operational cover, intelligence feeds, and strategic alignment necessary to wage hybrid cyber warfare across physical and psychological domains.

Command Structure – Known Figures
The leadership behind Intelligence Group 13 reflects a blend of strategic IRGC command, operational direction, and industrial integration. At the top sits Hamidreza Lashgarian, a senior IRGC cyber official with confirmed affiliations to both the Electronic Warfare and Cyber Defense Organization (EWCD) and Quds Force Unit 300. Lashgarian is widely regarded as the supervisory figure behind the Shahid Kaveh Group, providing overarching guidance on both ideological framing and operational tempo. Beneath him, Reza Salarvand serves as the direct commander of Intelligence Group 13, identified in dissident leaks as the group’s tactical leader and field-level coordinator. Salarvand’s role includes managing target selection, overseeing cyber intrusion campaigns, and aligning Team 13’s actions with IRGC strategic objectives. Supporting these military units is Mohammad Bagher Shirinkar, a key figure embedded in EWCD-linked contractor firms. Shirinkar plays a critical role in bridging the IRGC’s internal operations with its broader technical ecosystem, facilitating tool development, subcontractor oversight, and deniable operational capabilities through civilian-facing fronts.
IRGC High-Level Hierarchy

Placement of Intelligence Group 13 Within IRGC Cyber Org
Intelligence Group 13 functions as the operational spearhead of the Shahid Kaveh Group, a hybrid entity positioned at the intersection of the IRGC’s cyber warfare and Quds Force portfolios. This structural alignment gives Team 13 a unique dual mandate: to execute precision cyber intrusions with military-grade sophistication while simultaneously engaging in psychological and ideological warfare. As a tactical APT (Advanced Persistent Threat) cell, the unit specializes in cyber reconnaissance, disruptive sabotage of critical infrastructure, and the deployment of malware designed to pre-position effects across adversarial networks. Its proximity to both IRGC Electronic Warfare and Cyber Defense (EWCD) and external-facing Quds Force units enables Intelligence Group 13 to operate with both deep access and strategic reach, making it a central instrument of Iran’s asymmetric cyber doctrine.
Internal Chain of Command

Technical Mission and Tactics
The strategic mandate of Intelligence Group 13 centers on disrupting critical infrastructure and shaping adversarial perceptions through covert digital operations. The unit has demonstrated a specific focus on targeting industrial control systems (ICS), including Unitronics PLCs, Israeli electrical grids, U.S. water treatment facilities, and fuel distribution systems, all selected for their high-impact potential and symbolic value. Their campaigns often involve pre-positioning malware, embedding implants within target environments well in advance of activation to enable dormant or timed sabotage. Complementing these efforts is an aggressive intelligence collection posture, relying on phishing, credential theft, and OSINT harvesting to support intrusion planning and post-access operations. Crucially, Team 13 integrates psychological warfare into its strategy, disseminating screenshots, leaks, and taunting messages through propaganda arms like CyberAveng3rs to generate fear, confusion, and reputational damage in tandem with technical effects.
Disinformation & Propaganda: The Role of CyberAveng3rs Patriotic Hacker Wing
CyberAveng3rs serves as the psychological warfare and influence operations extension of Intelligence Group 13, functioning not as an independent actor but as a deliberately constructed propaganda arm embedded within Iran’s cyber doctrine. Rather than remaining in the shadows like traditional APTs, Team 13 leverages CyberAveng3rs to publicize and amplify the psychological impact of its technical operations,turning covert intrusions into open spectacles of defiance. Through Telegram channels, Instagram accounts,and diaspora-linked echo networks, CyberAveng3rs publishes defacement screenshots, malware control panel captures, and operational taunts directed at Western and Israeli infrastructure targets. These narratives are often laced with religious-nationalist motifs, martyr quotes, and anti-Zionist rhetoric, reinforcing the IRGC’s ideological messaging. CyberAveng3rs is not merely reactive; it issues pre-attack warnings, brags post-operation, and threatens future campaigns, making it a key instrument for intimidation, distraction, and symbolic escalation. By fusing information operations with hacking campaigns, it enhances the IRGC’s ability to wage cognitive warfare alongside technical compromise.
Operator: Mr. Soul (Mr_Soulcy)
- Known handles:
- Instagram: Cyberaveng3rs
- Telegram: @CyberAveng3rs
- X @cyberaveng3rs
- Instagram: Cyberaveng3rs
- Notable content:
- Claimed the Aliquippa water system attack (PA, USA)
- Leaked Unitronics control panel screenshots
- Issued threats of “Operation IV” aimed at Israeli cybersecurity units
- Branded style includes martyr quotes, Islamic slogans, and ICS interfaces
- Claimed the Aliquippa water system attack (PA, USA)
Contractor and Front Company Ecosystem
The IRGC’s cyber operations rely heavily on a dense and evolving ecosystem of affiliated companies, some covertly managed through military intermediaries, others openly registered as “cyber defense,” “AI research,” or “IT solutions” firms. This web serves multiple strategic purposes. First, it allows the IRGC to outsource technical labor and scale operations without overexposing its formal personnel. Second, it provides plausible deniability, as these front firms can operate under civilian-facing banners while conducting state-directed offensive cyber activities. Third, it enables a rotating model of corporate obfuscation, where companies like Emen Net Pasargad are dissolved or sanctioned only to reappear under new names like Ayandeh Sazan Sepehr Aria, often with overlapping staff and clients. These firms are frequently staffed by IRGC veterans or relatives of high-ranking cyber officials, further blurring the lines between state, contractor, and covert operator.
This model closely parallels revelations from the i-SOON (安洵) data leak, which exposed how China’s Ministry of Public Security (MPS) and provincial security bureaus have long contracted out cyber operations to nominally private firms. Like the IRGC’s cyber complex, Chinese firms such as i-SOON and Chengdu 404 maintain the veneer of legitimate enterprise while developing spyware, managing fake persona farms, and carrying out state-sponsored intrusions. In both Iran and China, this hybrid public-private structure allows state entities to mask state cyber activity behind corporate fronts, maintain flexibility, and engage in offensive campaigns without bearing the full diplomatic cost.
Moreover, just as Iran’s firms like Cyberban Institute and Kavosh Center double as ideological and technical platforms, Chinese contractors often support both domestic surveillance and global espionage, engaging in infrastructure targeting, data exfiltration, and information control under the guise of national innovation. This convergence of state-backed ideology, cyber warfare, and privatized labor reveals a shared authoritarian blueprint: One in which cyber capabilities are cultivated through semi-privatized ecosystems designed to insulate command structures while enabling scalable, deniable aggression in the global digital theater.
Expanded Corporate Ecosystem Supporting IRGC Cyber Ops
The IRGC’s cyber capabilities rely not solely on military or intelligence personnel but on an expansive and deliberately obscured ecosystem of contracting companies, technical institutes, and shell entities that function as both operational extensions and recruitment/talent pipelines. These firms play a crucial role in sustaining the IRGC’s cyber warfare doctrine, developing malware, testing exploits, maintaining infrastructure, and providing a legal or commercial façade for offensive operations.
What makes these companies particularly effective, and elusive, is the way they straddle the boundary between legitimacy and subversion. Many of them present as cybersecurity vendors, AI startups, or educational technology labs, marketing themselves to civilian, academic, and even international clients. Behind the scenes, however, they serve as contractors for the IRGC’s Electronic Warfare and Cyber Defense Organization (EWCD), Intelligence Organization (IO), and Quds Force, executing tasks that range from infrastructure reconnaissance and SIGINT analysis to psychological warfare and influence ops.
This system is both resilient and adaptive. Companies are frequently rebranded, dissolved, or split into subsidiaries following public exposure or sanctions. For instance, Net Peygard Samavat, once exposed for its involvement in Iranian state cyber operations, later became Emen Net Pasargad, which itself was reconstituted as Ayandeh Sazan Sepehr Aria. Despite their changing names and corporate registrations, these entities retain the same personnel, mission scope, and government sponsors, effectively outlasting sanction regimes and Western takedown efforts.

Moreover, the personnel who operate these firms often rotate between IRGC intelligence positions, academic research roles, and private-sector leadership, creating a feedback loop where state doctrine, technical innovation, and civilian infrastructure become interwoven. This also creates a recruitment channel: Young developers and engineers are often brought into these companies under the banner of patriotic service or career opportunity, then quietly integrated into national-level cyber missions.
In effect, these firms function as force multipliers for Iran’s cyber program. They provide scalability, deniability, and a legal buffer between the Iranian state and its digital aggression. As international scrutiny tightens, the IRGC is likely to continue leaning on these corporate proxies to advance technical capability while avoiding direct attribution,mirroring similar models seen in China (e.g., i-SOON) and Russia (e.g., contractors like NTC Vulkan).
Below is a detailed examination of these key companies and their connections.
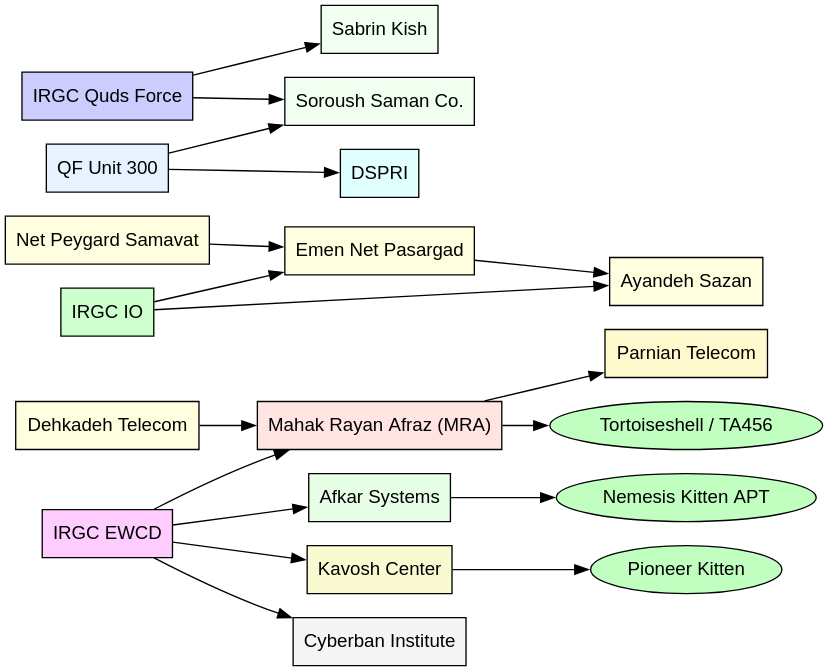
Core Contractor Entities and Their Functions
- Emen Net Pasargad (ایمننت پاسارگاد) – Once a flagship contractor for disinformation and foreign interference (e.g., impersonating the Proud Boys during the 2020 U.S. election). Dissolved in 2023. Sanctions Source
- Ayandeh Sazan Sepehr Aria (آریا سپهر سازان آینده) – A successor to Emen Net, continuing operations in information operations and malware development. Founded by Mohammad Bagher Shirinkar. Recorded Future
- Mahak Rayan Afraz (محک رایان افراز) – Specialized in AI and surveillance tooling, including:
- Hazm – Persian NLP engine
- Gol Rokh – Facial recognition platform
- Disbanded in mid-2023 amid U.S. pressure. Treasury
- Hazm – Persian NLP engine
- DSPRI (موسسه سنجش داده پیشرفته) – Linked to IRGC Quds Force Unit 300, DSPRI handles signal interception and encrypted traffic decryption, including battlefield deployments in Syria, Lebanon, and Iraq. Recorded Future, p. 14
- Sabrin Kish (شرکت صابرین کیش) – Developed sniffers and ICS tools sold to IRGC clients; also engaged in foreign contracts (e.g., deal with Iraq’s NSA head Faleh al-Fayyadh). Maintains financial and corporate overlap with IRGC Cooperative Foundation. Wikipedia
- Soroush Saman Co. (شرکت توسعه الکترونیکی و مخابراتی سروش سامان) – Supplied surveillance and tracking systems to Hezbollah, and built AI-based phone surveillance for Unit 300. [IntelliTimes coverage via Lab Dookhtegan]
- Afkar Systems (افکار سیستم) – Tied to Nemesis Kitten APT, allegedly led by Ahmad Khatibi Aghda. Operated through Center 2060 and Cyber Base 2000, both under EWCD’s umbrella. CISA Advisory
- Parnian Telecommunication (شرکت الکترونیکی و مخابراتی پرنیان) – Facilitates cyber workforce recruitment for IRGC and MRA-linked projects. Job ads call for infosec and penetration testing expertise. Recorded Future, p. 19
- Kavosh Center (مرکز کاوش) – Offensive R&D hub tied to the Shahid Kaveh Group. Led by IRGC affiliate “Shayan” (Malek Mohammadi Nejad). Possibly involved in TTP development and APT tool testing. Recorded Future
- Cyberban Institute (موسسه سایبربان) – Run by Mehdi Lashgarian, nephew of IRGC cyber leader Hamidreza Lashgarian. This front publishes ideological content, disinfo narratives, and tech analysis favorable to IRGC doctrine. Recorded Future, p. 22
Observations on Structure and Strategy
The structure and behavior of IRGC-affiliated cyber firms reveal a deliberate and adaptive operational model. Many of these companies engage in strategic rebranding, dissolving or renaming themselves after being sanctioned or exposed, Net Peygard reemerged as Emen Net, which later became Ayandeh Sazan, while Dehkadeh Telecom transitioned into Mahak Rayan Afraz, with a new identity likely forthcoming. These transitions help avoid regulatory scrutiny while maintaining operational continuity. Furthermore, interlocking leadership is a hallmark of the ecosystem: Figures such as Mohammad Bagher Shirinkar, Hamidreza Lashgarian, and Esmail Rahimi appear across multiple entities, indicating a centralized and tightly coordinated management structure. The ecosystem also supports technology transfer abroad, with tools and capabilities exported to IRGC-aligned actors in Iraq, Syria, and Lebanon, particularly via Quds Force Unit 300. Notably, these firms are often the technical and logistical backends for known APT groups. For example, Afkar Systems underpins Nemesis Kitten, Mahak Rayan Afraz has links to Tortoiseshell (TA456), and clusters tied to the Shahid Kaveh Group appear to support Pioneer Kitten operations.
Operational Forecast and Strategic Implications
Intelligence Group 13 functions as the operational core of the IRGC’s cyber disruption strategy, a convergence point where technical sabotage, psychological warfare, and revolutionary ideology are seamlessly integrated. Operating under the umbrella of the Shahid Kaveh Group, Team 13 is not an independent or freelance actor but a disciplined tactical cell embedded in a broader, multi-layered command system overseen by IRGC EWCD, IO, and Quds Force divisions. Its mission is augmented through propaganda arms such as CyberAveng3rs, which act not only as amplifiers of defacement and intrusion campaigns but also as strategic influence assets projecting IRGC narratives into public and geopolitical consciousness.
The group’s tradecraft spans traditional APT techniques, such as credential harvesting, critical infrastructure penetration (e.g., Unitronics PLCs, fuel pump logic, and water treatment systems), and covert malware deployment (e.g., IOControl, Project Binder). Yet what sets Team 13 apart is its parallel investment in symbolic messaging, issuing threats via Telegram, leaking screenshots via Instagram handles like @mr.sul.ir, and invoking martyrdom and Islamic resistance to create a psychological echo chamber around each technical act.
This entire operation is scaffolded by a front company and contractor ecosystem designed to provide deniability, talent, infrastructure, and logistical support. These include Afkar Systems (linked to Nemesis Kitten), Mahak Rayan Afraz (associated with TA456), and Kavosh Center (supporting Pioneer Kitten), among others. These firms are part of a strategy of institutional layering and rebranding, allowing the IRGC to rotate through corporate identities while sustaining long-term capabilities. Rebranding paths such as Net Peygard → Emen Net → Ayandeh Sazan show how the IRGC evades sanctions without losing operational momentum.
Key Takeaways:
- Intelligence Group 13 is a deeply embedded extension of the IRGC’s strategic cyber doctrine,not an isolated threat actor.
- Psychological operations are prioritized on par with malware deployment, reflecting a dual mission of technical and perceptual warfare.
- The martyrdom framework (e.g., naming conventions like “Shahid Kaveh”) plays a pivotal role in unifying cyber actions with ideological legitimacy.
- The use of contractor ecosystems and front companies provides flexibility, plausible deniability, and continuity across sanctions and takedowns.
Risk Assessment:
Future campaigns by Intelligence Group 13 and its affiliates are likely to blend cyber-kinetic threats with narrative manipulation, targeting not just critical infrastructure but public perception and institutional trust. This includes:
- Threatening or disrupting civilian infrastructure in the U.S., Israel, and Gulf States
- Deploying psychological campaigns through channels like CyberAveng3rs, timed with physical intrusions
- Leveraging rebranded contractors to deliver tooling and intelligence capabilities both domestically and to proxy forces abroad (e.g., Hezbollah, PMF in Iraq)
Defending against this threat requires not only technical hardening but cognitive resilience, recognizing that the IRGC’s cyber ambitions are as much about controlling the story as they are about breaching the network.
Sign Up For DomainTools Investigations’ Newsletter for the Latest Research
Want more from DomainTools Investigations? Be sure to sign up for our monthly newsletter to get the latest research from the team – available on LinkedIn or email.