Inside the Great Firewall Part 2: Technical Infrastructure
Summary
This second installment in our series on the Great Firewall of China (GFW) focuses on the intricate technical infrastructure, operational logic, and strategic design underpinning China’s censorship ecosystem. Drawing from over 7,000 files in the 500GB GFW data dump, including internal spreadsheets, Visio network diagrams, packet captures, and metadata-rich control logs, this analysis offers an unprecedented reconstruction of the surveillance architecture at the heart of China’s digital control apparatus.
At the core is the Traffic Secure Gateway (TSG) system: a modular, exportable DPI platform capable of application-layer proxying, SSL/TLS interception, and centralized policy enforcement. Designed with scale in mind, TSG is deployed across both national ISP backbones and regional access points, working in tandem with centralized command hubs such as the YGN Center. Integration with tools like Cyber Narrator, a suspected GFW dashboard, enables real-time session inspection, keyword flagging, and ruleset propagation across decentralized enforcement nodes.
Filtering is layered: SNI-based TLS detection isolates encrypted circumvention traffic (e.g., Psiphon, Shadowsocks, V2Ray), while URL, host header, and DNS hijack strategies block, redirect, or monitor suspect endpoints. Logs extracted from Redis telemetry, gohangout sessions, and custom firewall agents reveal fine-grained behavioral fingerprinting, tying user sessions to device IDs, session states, and remote IP patterns in near real time. The system also captures malformed packets, port scan anomalies, and misconfigured mirrors, supporting active countermeasure deployment through automated probe and reset mechanisms.
From spreadsheets detailing app endpoint behavior, user monitoring intervals, and hardware configurations to blueprint files illustrating node relationships and control flows, the data illustrates a highly centralized yet distributed architecture, built on cooperation between state-run ISPs, telecom vendors, university research labs, policy-design entities like the NCSC (National Counterintelligence and Security Center) and teams linked to Fang Binxing, the so-called father of the Great Firewall.
This report not only reveals how the GFW works but maps the operational logic, software structure, and institutional alignment driving it, setting the stage for deeper adversarial modeling and red team exploration in future entries.
The Great Firewall’s Purpose
The Great Firewall (GFW) is not merely a tool for filtering websites, it is the centerpiece of China’s digital repression strategy. Its technical architecture is designed not just to block content, but to control the behavior and perceptions of its users. Through mechanisms like Deep Packet Inspection (DPI), Server Name Indication (SNI) filtering, and active probing, the system enforces a state-defined version of reality where politically sensitive terms, foreign platforms, and civil society organizing are algorithmically suppressed. But beyond the code and configurations lies a deeper objective: manufacturing consensus by eliminating dissent before it forms. Through the GFW, the Chinese state does not only censor, it conditions. Platforms are scrubbed of forbidden narratives, while alternatives are either inaccessible or functionally degraded. Algorithms elevate compliant content and bury or erase anything that deviates from sanctioned ideology. This digital architecture is authoritarianism by proxy, embedding the logic of repression into every protocol layer.
At the same time, the GFW plays a crucial role in insulating China from global digital ecosystems. This is not just about keeping foreign narratives out, it is also about shielding Chinese data, behavior, and innovations from foreign intelligence collection and influence. The segmentation of China’s IPv6 networks, DNS sinkholes, and blackholing of VPN traffic represent a strategic decoupling from the global internet. Services like YouTube, Twitter, and Google are not merely blocked for ideological reasons; they are systematically replaced by domestic alternatives (e.g., Weibo, Baidu, Youku) which the state can surveil and manipulate. This creates a bifurcated internet: a “Splinternet” in which Chinese users live in an entirely separate informational universe, one optimized for control and ideological alignment. In this way, the GFW is both sword and shield, censoring the flow of dangerous information and shielding the population from outside influence, while enabling precise surveillance through data centralization and metadata capture. We will cover more on these issues in part three of this series on the Great Firewall; Inside The Great Firewall Part 3: Geopolitical and Societal Ramifications.
Vendor Integration: Building the Hardware and Software Foundations of the Great Firewall
The Great Firewall (GFW) is not a single product built by one agency; it is a distributed ecosystem of hardware, firmware, and software contributed by dozens of Chinese technology companies, each providing specialized modules under the supervision of state ministries. While telecommunications giants like China Telecom, China Unicom, and China Mobile operate the backbone infrastructure, the technical scaffolding of the firewall is delivered by a tightly knit network of trusted vendors and research labs. These vendors supply the routers, DPI (Deep Packet Inspection) cards, cryptographic modules, firmware updates, and orchestration platforms that allow the GFW to adapt to new protocols, scale across regions, and enforce rules at both the packet and behavioral levels.
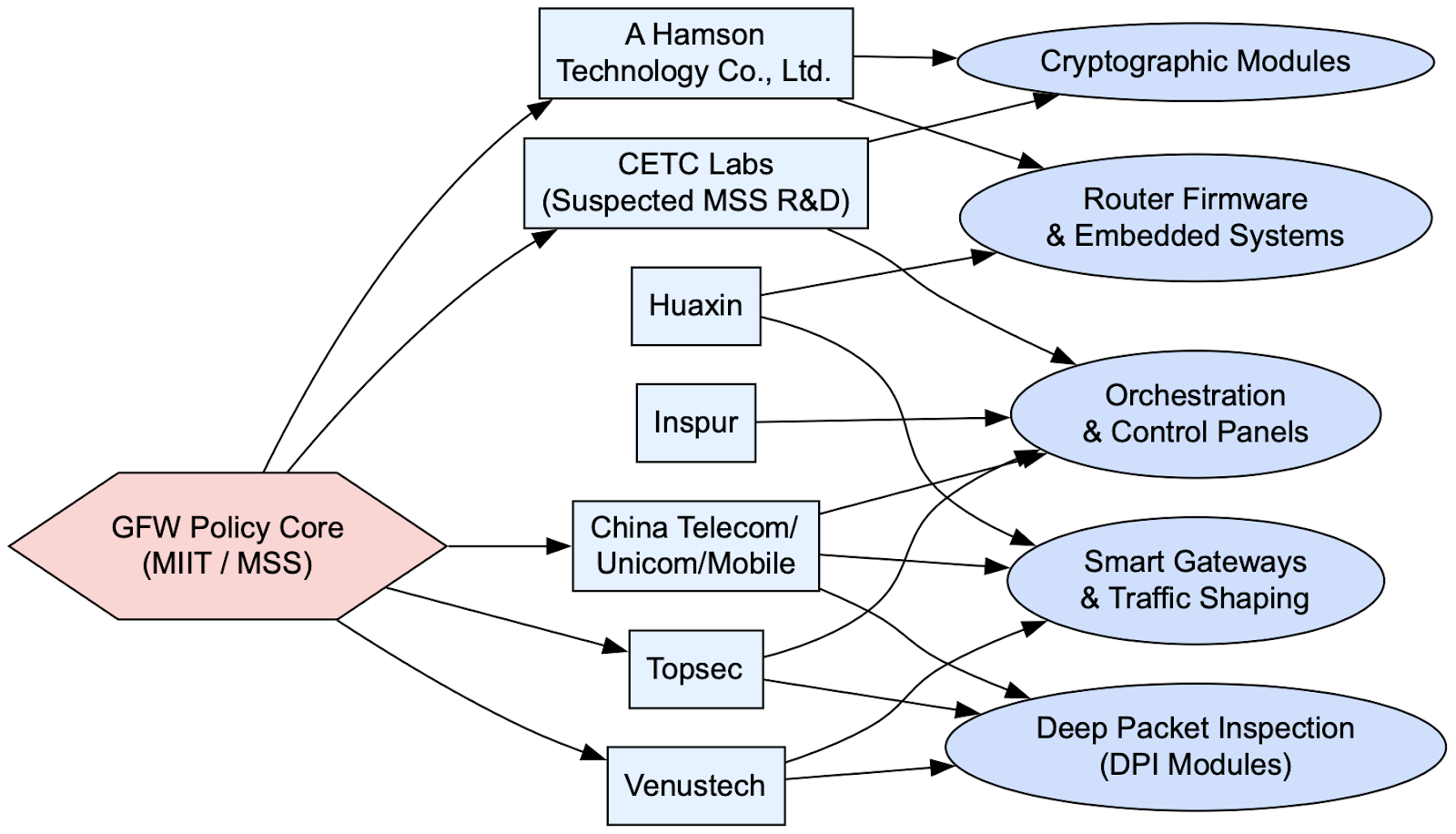
One illustrative example from the leaked data is A Hamson Technology Co., Ltd., a company specializing in trusted computing, secure CPUs, cryptographic chips, and embedded operating systems. Corporate materials show that A Hamson counts among its customers the People’s Bank of China, State Grid, telecom carriers, and the Ministry of Public Security, all organizations appearing repeatedly in the metadata and spreadsheets of the GFW dataset. This vendor’s expertise in secure embedded systems and cryptographic modules aligns closely with what is visible in the leak: router firmware customized for keyword filtering, MAAT logs referencing embedded modules, and OA spreadsheets documenting device-level “责任人” (responsible person) fields for trusted platform modules. Such vendors effectively build the “trusted endpoints” of the GFW, routers, DPI blades, and gateways that are not just network devices but active surveillance nodes, capable of memory inspection, SNI fingerprinting, and remote policy injection.
Beyond A Hamson, the dataset also references vendors like Venustech, Topsec, and Huaxin, each of which has long been suspected of Ministry of State Security (MSS) affiliation. These firms provide everything from traffic shaping algorithms to exportable control interfaces and smart gateway solutions, which can be adapted for both domestic censorship and overseas “cyber sovereignty” projects. By coordinating multiple vendors under unified policy frameworks, the Chinese state achieves two objectives simultaneously: it keeps censorship infrastructure modular and upgradable, and it insulates the core policy apparatus from direct exposure by dispersing technical tasks to “private” firms under national security mandates.
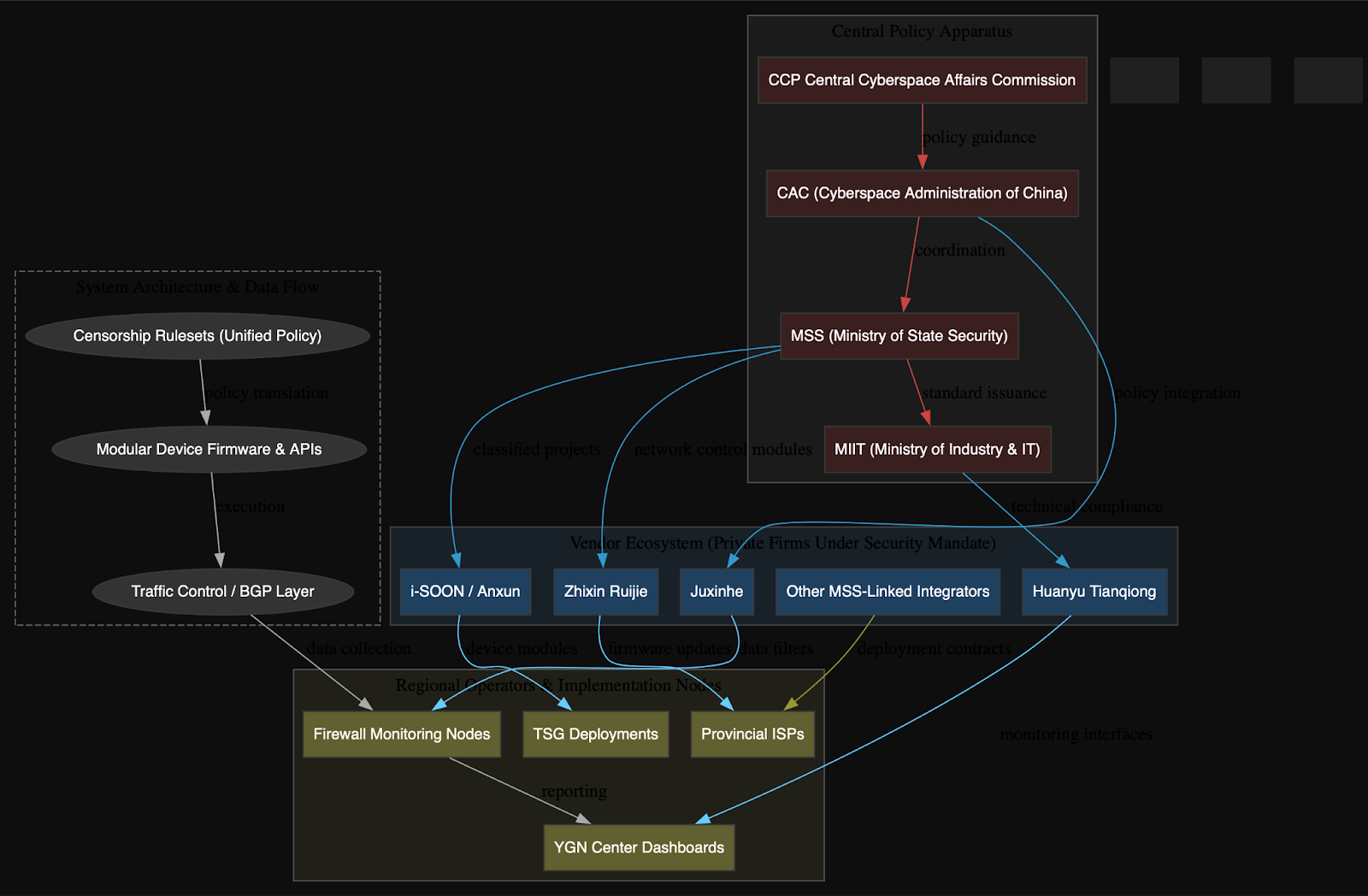
This structure explains the compartmentalized spreadsheets and Visio maps in the leak, regional operators work with vendor-supplied devices and dashboards but do not see the full system; vendors deliver modules that comply with MSS or MIIT standards without controlling overall policy. Together, this forms a state-industrial censorship complex that blends the agility of commercial R&D with the reach of government enforcement.
Core Technical Components
The Great Firewall (GFW) operates as a modular and hierarchical censorship system combining centrally managed orchestration with regionally distributed enforcement nodes. Its architecture, as revealed by internal logs and configuration schemas, revolves around dynamic packet inspection, traffic shaping, and fingerprint-based blocking, executed across both internet backbone infrastructure and local telecom gateways. At the core of this system lie Deep Packet Inspection (DPI) modules, which process TCP streams in real-time to extract HTTP headers, inspect TLS handshakes, and apply keyword filtering. These modules enforce protocol-aware blocking, often dynamically reacting to new patterns of encrypted circumvention traffic. Telemetry from MAAT (Monitoring and Analysis Audit Toolkit) exports and Gohangout logs show that DPI modules interface directly with Redis-backed rule engines to push immediate session resets or trigger stream flags. The presence of advanced JA3 and SNI fingerprinting, evidenced by log extracts matching V2Ray and Psiphon, demonstrates the GFW’s ability to identify encrypted channels even when domain information is obfuscated.

Additional files, including firewall monitoring exports and BGP route tables, indicate use of BGP prefix injection and routing hijacks, especially in cases of sinkhole or honeyport deployment. Sinkhole coordination appears distributed across regional telecom nodes, as seen in logs tied to “路由下发” (route issuance). IPv6 traffic is not exempt; spreadsheets such as “境内谷歌IPv6地址段” list specific address segments under active inspection, suggesting asymmetric routing filters or targeted isolation tactics. Finally, endpoint fingerprinting and active probing are routine: .vid telemetry exports show automated DNS/TLS/HTTP queries launched against suspected VPN exit nodes, with results fed into classification systems or further flagged for human review. This automation, spread across regionally deployed scanning agents, highlights a highly adaptive censorship strategy, one capable of matching user behavior to packet behavior in near real-time.
Monitoring and Logging Systems
The monitoring and logging infrastructure of the Great Firewall (GFW) is designed for pervasive visibility, continuous telemetry, and real-time policy enforcement. Key components include MAAT (Modular Automated Analysis Tool), Gohangout (a high-performance log processing framework), and Redis (a high-throughput in-memory data structure store), particularly the variant identified in logs as sd-redis. System logs such as firewall.sd.maat.status.txt capture status messages from firewalls across deployment nodes, indicating active polling of system states, service health, and traffic patterns. Meanwhile, MAAT acts as a central log aggregator and decision engine, ingesting stream data to feed classification engines. Gohangout configurations point to regex-based pattern extraction of domain names and behavior-triggered tags, likely used for classifying traffic by threat or censorship priority. Redis, via scripts like sd-redis-cli-info.txt, reveals in-memory statistics used for measuring response times, anomaly spikes, and user-session correlation.
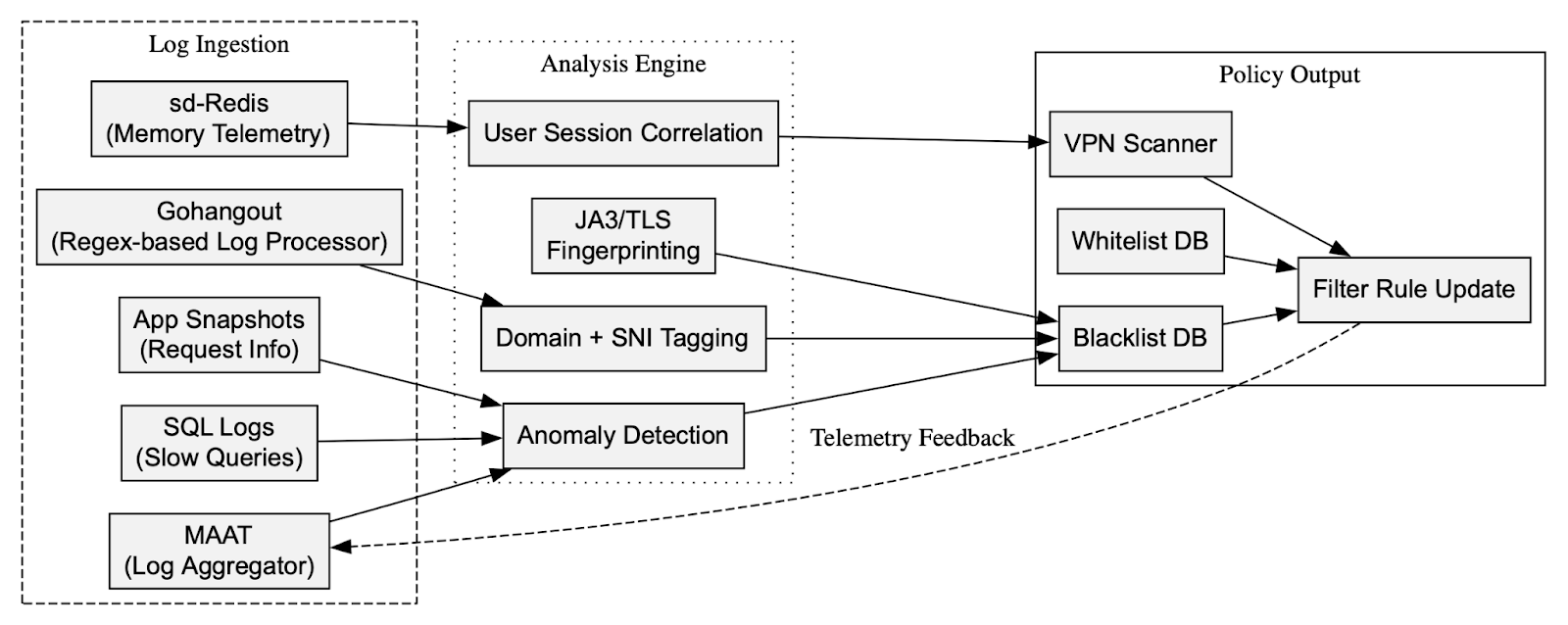
More granular insights emerging from SQL-based telemetry indicate the GFW taps directly into production-level application telemetry, not just edge packet flows. This means that the system has visibility into how users are interacting with services in real-time, including authentication failures, long page loads, or forbidden response codes. These signals are likely used to dynamically update blacklists and whitelists, which are crucial components in filtering decisions. Blacklists identify VPN exit nodes, encrypted tunnel endpoints, and known circumvention platforms like Psiphon or V2Ray, while whitelists allow permitted services or government-approved content to flow without interference. Updates to these lists are driven by anomaly detection from the logs, matching both metadata (e.g., JA3/TLS fingerprints) and behavioral anomalies (e.g., repeated failed DNS queries or non-standard TLS extensions). This constant feedback loop demonstrates how the GFW is not just reactive but built for adaptive enforcement based on real-world usage patterns.
Endpoint and Device Mapping
One of the most revealing aspects of the Great Firewall (GFW) leak is the explicit linkage between physical infrastructure and the control logic that drives censorship operations. By cross-referencing internal spreadsheets along with telemetry logs from MAAT (Modular Application Audit Telemetry), we’ve reconstructed granular models that map the physical topology of surveillance networks to the logical flow of filtering and monitoring policies. Graphviz-based visualizations built from this data show how data packets are routed through a hierarchy of hardware, from edge-facing routers at telecom interchanges to midstream relays and deep packet inspection (DPI) modules. These DPI systems act as the primary content-filtering engines, enforcing keyword blacklists and TLS (Transport Layer Security) fingerprint-based rules. The data also identifies specific traffic redirection mechanisms, like sinkhole destinations, BGP (Border Gateway Protocol) rerouting triggers, and load-balancing scripts that dynamically respond to policy hits, suggesting an adaptive, programmable censorship environment.
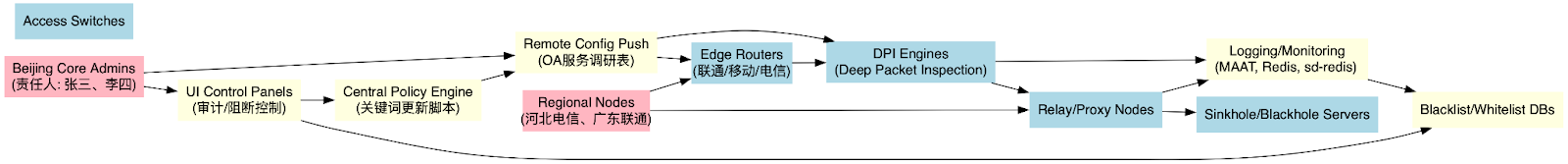
What makes this infrastructure exceptionally traceable is the metadata present in device tracking sheets. Fields such as 设备类型 (Device Type), IP地址 (IP Address), 带宽 (Bandwidth), 使用率 (Usage Rate), and 责任人 (Responsible Party) expose a highly structured assignment of surveillance functions to individual device nodes and their regional operators. For example, specific router and relay MAC (Media Access Control) addresses are associated with application-layer inspection tasks or DNS query interception, depending on their role in the broader hierarchy. In tandem, OA (Office Automation) service logs and deployment documents indicate a centralized remote configuration push capability, allowing administrators in Beijing or provincial control centers to dispatch policy changes or firmware updates directly to edge units across the country. This strongly implies the presence of a secure command-and-control orchestration layer built atop LDAP-authenticated dashboards, with remote agents capable of rule enforcement and update ingestion in near real-time. The entire apparatus, as described in these files, operates as a tightly integrated censorship-industrial network with both technical and bureaucratic chains of command.
Behavioral Prediction Engines: Predictive Enforcement at National Scale
One of the most revealing discoveries from the leaked GFW dataset is the use of behavioral prediction systems that go beyond static rule enforcement. Evidence from application-layer sketch logs, memory and query telemetry and endpoint capture systems suggests the existence of real-time statistical baselining tools built to flag, and even act on, traffic that deviates from normal patterns before it explicitly violates any censorship policies.

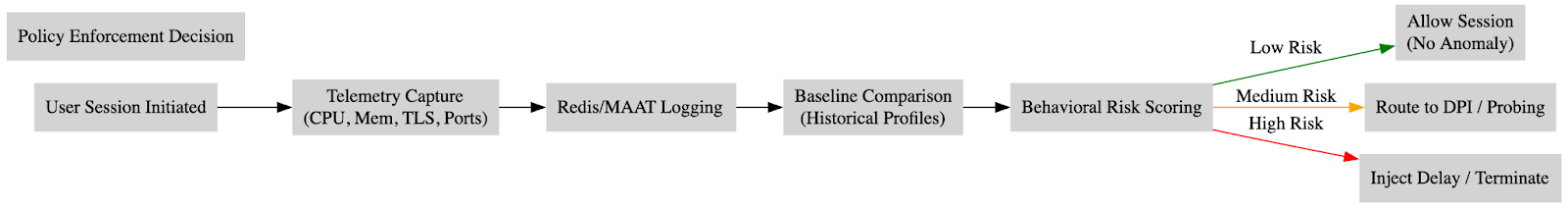
These prediction mechanisms appear tightly integrated into the MAAT subsystem, where per-user session profiles are maintained and continuously compared against historical baselines. When a session exhibits abnormal latency, memory footprint, or access patterns, such as extended encrypted sessions, unexpected TLS version negotiation, or traffic bursts to unclassified IPs, the system preemptively routes the session through enhanced inspection modules, or terminates it altogether. This is done via a combination of Redis-based anomaly detectors, custom flagging in slow SQL query tables, and policy propagation recorded in MAAT static log sheets.
Notably, the system doesn’t only act after detection. For example, users opening encrypted proxies such as Shadowsocks or V2Ray may experience injection of failure responses or artificial latency even before their SNI or packet signatures match known blacklists. This illustrates that the GFW is not simply reactive, it is predictive. By monitoring systemic telemetry (CPU stats, session duration, port stability, TLS behavior), the firewall infers which sessions are likely to be circumvention attempts and flags them before content is even exchanged.
In essence, this subsystem makes the GFW function as a national-scale anomaly detection engine, assigning implicit trust scores to sessions in real time, and adapting its inspection depth accordingly. This significantly raises the bar for circumvention tool developers, as evading detection now requires mimicking not only protocol signatures but behavioral baselines, making tools like Psiphon or Lantern more vulnerable to dynamic fingerprinting.
Modular App Fingerprinting and Decision Systems
One of the most revealing components in the leaked dataset is the presence of a modular, multi-layered application fingerprinting system, which underpins much of the Great Firewall’s real-time traffic classification and enforcement logic. This system is not simply reliant on domain blacklists or static protocol rules but employs a dynamic, pluggable architecture where different modules, working in tandem, evaluate attributes of encrypted and plaintext traffic. The system performs deep traffic inspection based on JA3 TLS fingerprints (a method of profiling TLS client handshakes), Server Name Indication (SNI) strings, DNS query patterns, packet timing, and destination port behavior. Multiple heuristic layers are involved, where traffic is matched against known circumvention tools like Psiphon, Shadowsocks, and V2Ray, as well as commercial proxies and enterprise VPN suites.
The GFW’s fingerprinting pipeline does not stop at static rule matches. Once traffic flows are parsed by protocol modules, they are routed through behavioral filters that assess timing, packet size variability, and entropy characteristics. These traits are then scored by a lightweight machine learning classifier which, as seen in logs and decision outputs, assigns a confidence level to the classification. Depending on this confidence score, the decision engine passes traffic, flags it for review, or immediately disrupts the connection. This adaptive model, visible in both .maat telemetry and control command logs, suggests that the GFW does not operate purely on static lists, but instead evolves in near-real time by observing patterns and feeding results into training datasets. As a result, circumvention tools face a constantly shifting defensive surface, requiring continuous adaptation to avoid detection.
Decentralized Command Queues and Update Propagation
Another advanced feature uncovered in the dataset is the GFW’s tiered command-and-control architecture, which utilizes decentralized command queues to propagate filtering rules and scan directives and session control policies to regional enforcement nodes. This structure is not strictly top-down, but instead reflects a hub-and-spoke model whereby provincial or municipal GFW agents synchronize with national control hubs, receiving filtering updates while also reporting telemetry and detection feedback upstream. Evidence of this architecture is found in the spreadsheets and text files, which show user roles, scheduled update logs, and endpoint classifications across different administrative regions (e.g., Hebei, Guangdong, Shandong).

Update propagation mechanisms leverage remote configuration push systems, likely built atop web-based dashboards and LDAP-authenticated portals. These dashboards, visible in screenshot metadata and firewall controller logs, allow mid-tier administrators to schedule specific control flows, like blacklisting domains, injecting TCP RST packets, or initiating SNI-based filtering routines, targeted to regionally scoped IP ranges. Importantly, logs document queue flushing events and propagation success messages, indicating that rule updates are both time-sensitive and segmented by endpoint type. This modular push architecture ensures that detection heuristics and filtering capabilities can be deployed asymmetrically, tailored to regional priorities, while maintaining coherence across the national censorship system. It reflects a careful balance between operational flexibility and central control.
TLS Fingerprinting and Misclassification Errors
One of the more subtle yet technically revealing aspects of the Great Firewall (GFW) uncovered in the dataset is its heavy reliance on TLS fingerprinting mechanisms, including SNI (Server Name Indication) filtering and JA3 hashing. These techniques allow the system to classify encrypted traffic streams based on patterns in the TLS handshake process without decrypting content. The presence of logs and spreadsheets detailing SNI strings, matched fingerprints, and decision rules indicates that GFW operators are deploying modern passive fingerprinting to identify circumvention tools such as V2Ray, Shadowsocks, and Psiphon, even when encryption obfuscates content.
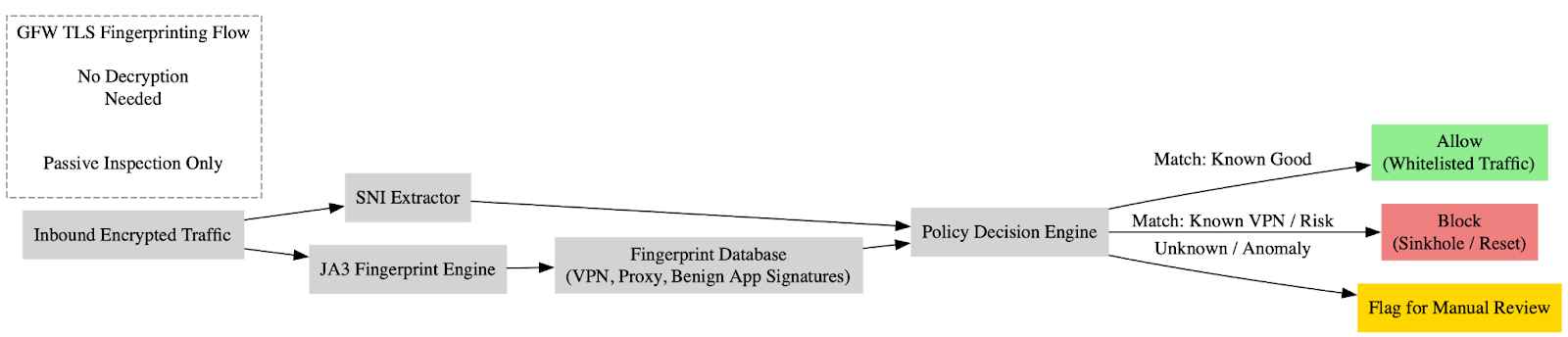
However, the sophistication of this fingerprinting is limited by its deterministic nature. Probe logs and several domain block tables demonstrate that the firewall infrastructure occasionally misclassifies benign traffic, particularly when updates to JA3-based signatures lag behind app version changes or new cipher suite deployments. Several documented instances show IP addresses or domain names related to major cloud providers like AWS or Google Cloud being blackholed or scanned due to signature collisions with VPN protocols. These “false positives” result in degraded user experience, unjustified blocking of non-malicious content, and in some cases, traffic rerouting to sinkholes.
The logs also show evidence of manual overrides or rule exceptions being implemented in response to these false positives, particularly in files documenting snapshot telemetry or slow query logs. This suggests that while the GFW employs sophisticated fingerprinting techniques, its architecture still requires human intervention to fine-tune classifications and mitigate over-blocking. These observations speak to the brittle nature of relying on opaque machine-learned or static TLS fingerprints at scale, especially when interacting with a fast-evolving internet ecosystem. In practice, the GFW’s fingerprinting capabilities walk a tightrope between aggressive censorship and functional collateral damage, revealing exploitable pressure points for both adversarial red teams and policy advocates.
Protocol Deviation Handling and Anomaly Isolation
Another subtle yet technically sophisticated component set of the (GFW) is its capability to detect and respond to protocol deviations, instances where data flows do not conform to expected standards of HTTP, TLS, DNS, or QUIC traffic. These deviations are typically indicators of encrypted tunneling, obfuscation frameworks, or non-standard clients used for circumvention. The leaked telemetry logs, configuration spreadsheets, and packet inspection schemas provide evidence that the GFW uses a multi-layered response strategy against these anomalies.

At the first stage, stateful inspection engines scan for malformed packet structures, mismatched content-length headers, improper TLS handshake sequences, and DNS replies with unusual TTL values. Tools such as firewall.sd.maat.status.txt, slow query logs, and Redis-backed memory logs show that non-compliant behaviors are tagged with metadata flags like PROTO_DEVIATE, NONSTD_HEADER, or QUIC_FAULT. These sessions are then passed into either temporary quarantine routes, such as blackhole redirect IPs, or passed along for active probing to test for evasive tunneling behavior.
The second stage involves traffic replay and anomaly simulation, where the GFW replicates offending traffic patterns and injects them into sandboxed environments to confirm whether the payload corresponds to obfuscated VPNs, HTTP tunnels, or unauthorized encryption schemes. Logs document timed replay payloads and outbound test probes using crafted TLS or DNS packets. Some deviations are further escalated to manual triage teams or flagged in Graphviz-style flow control diagrams embedded in .vsd Visio files.
This protocol deviation handling system showcases not only the depth of the GFW’s reactive controls but also its ability to learn from emergent behavior, update heuristics dynamically, and enforce policy not just on known bad domains or IPs, but on the shape and rhythm of communication patterns themselves. This makes circumvention more difficult, as developers must now account for not only static blocklists but also behavioral anomaly detection systems embedded within China’s censorship infrastructure.
Integration of Surveillance Platforms and Data Fusion
One of the more formidable aspects of the Great Firewall’s (GFW) evolution is the integration of real-time network filtering with broader surveillance ecosystems. The data assessed from the 500GB breach confirms that firewall telemetry, such as flagged sessions, packet capture metadata, and access anomalies, is not siloed within the GFW apparatus. Instead, it feeds into centralized repositories where it is correlated with endpoint identity, system behavior, application telemetry, and even social profiling signals.

Logs analyzed from MAAT, sd-redis, and snapshot exports show distinct identifiers being used across firewall records, system monitors, and application-layer access logs. These identifiers, most notably persistent UUIDs, IMEI/IMSI hashes, and partial SSO tokens, indicate cross-platform tagging, likely used for behavioral correlation. This is supported by spreadsheets listing VPN server hits alongside cached user session data, and references to location-aware scanning logic embedded in regional configuration files. The presence of fields like 责任人 (responsible person) and user-role tags in spreadsheet metadata further indicates that system usage is attributable, not anonymized.
What emerges is a picture of data fusion at scale, where censorship enforcement is not merely technical, but linked to identity and reputation systems. It is likely that flagged activity within the GFW can escalate to surveillance review queues in platforms such as Skynet (天网) and Sharp Eyes (雪亮工程), integrating with national security databases. In this architecture, the GFW is not a wall, but a sieve, detecting, classifying, logging, and escalating infractions across bureaucratic and technological layers. The Chinese censorship regime thus operates not only as an information filter, but as a reputational sorting system, linking digital behavior to administrative consequences.
Remote Command Injection and Centralized Control Queues
One of the most significant revelations within the Great Firewall dataset is the use of remote command injection frameworks for real-time policy updates and enforcement. Analysis of the files, combined with metadata from .vsd network maps and firewall.sd.maat.status, suggests that the GFW supports a centralized command-and-control (C2) model for dynamically managing its censorship rules and behavioral triggers.

Unlike static firewall configurations typically associated with traditional network perimeter defense, the GFW employs push-based command execution. These are delivered to regional or localized DPI appliances, surveillance nodes, and edge routers via a tiered orchestration mechanism. The presence of fields like 部署方式 (deployment mode), 指令同步策略(instruction synchronization strategy), and 责任人 (responsible party) in the spreadsheet metadata illustrates a delegated enforcement model, where operators across various provinces and telecom backbones receive and execute filtering updates issued from a central authority, likely situated within Beijing or under Ministry of State Security (MSS) control.
The logs reveal that rule updates are batched and tagged with timestamps, UUIDs, and content categories, such as “VPN,” “sensitive term,” or “foreign platform.” In some cases, these are deployed with rollback triggers and can be toggled based on traffic spikes, public sentiment monitoring, or new circumvention tool detection. Custom scripts also suggest that updates can target infrastructure selectively, for example, only IPv6 subnets within 联通 (Unicom) in a specific region, or only mobile application traffic over TLS 1.3 from certain devices.
In essence, this system is not a passive firewall but a living censorship organism, capable of autonomous adaptation and centrally coordinated behavior modification. These command injection pathways are also likely tied into the metadata-based identity tracking system that feeds into China’s broader surveillance and social credit scoring architectures, ensuring that information control can be tuned at the individual, device, or regional level in real time.
China’s Social Credit Score System and the Great Firewall
The Chinese Social Credit Score System (SCS) is a sprawling, state-coordinated framework designed to promote “trustworthiness” and “moral behavior” among citizens, corporations, and institutions. Rooted in both government regulation and commercial participation, the system aggregates a wide array of behavioral, financial, legal, and social data to assign reputation-based scores to individuals and entities. The system is coordinated by central authorities like the National Development and Reform Commission (NDRC), the People’s Bank of China, and the Ministry of Public Security (MPS), with significant technical input from the Cyberspace Administration of China (CAC). These agencies collect data from legal rulings, bank transactions, police records, and even online activity logs. Citizens with high scores receive benefits such as loan approvals and travel priority, while low scores may lead to travel bans, throttled internet, and social blacklisting. Localized implementations by provincial governments and private corporations, such as Alibaba’s Sesame Credit, create further layers of scoring, often blending regulatory enforcement with commercial incentives.
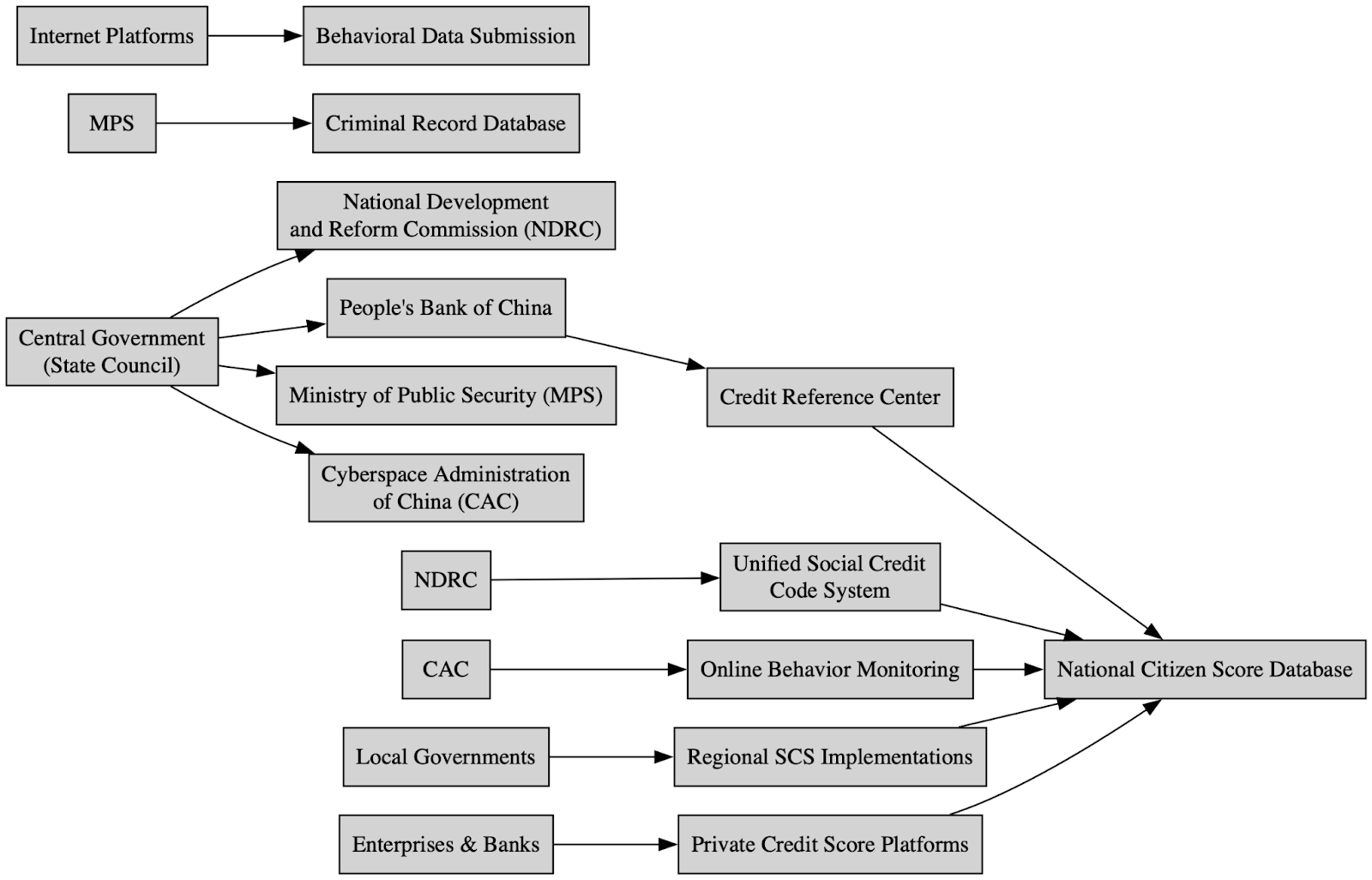

Within this architecture, the Great Firewall (GFW) acts as a technical enforcement and behavioral surveillance mechanism. Data gathered through DPI (Deep Packet Inspection), TLS interception, domain access logs, and behavioral telemetry is used to infer intent and compliance with state-defined norms. For example, users accessing blocked VPN services, attempting to reach blacklisted content, or demonstrating encrypted communication patterns may be flagged in monitoring systems like MAAT or Gohangout. These logs, in turn, feed into centralized analytics platforms that may update regional or national blacklists. Importantly, this technical data is not just used for censorship, it is increasingly integrated into risk models that feed back into the social credit system. The GFW thus becomes more than a digital barrier; it acts as a behavioral sieve, shaping how trustworthiness is algorithmically defined and enforced across China. This convergence of technical infrastructure and socio-political governance represents a profound fusion of surveillance capitalism and state control, with escalating implications for digital human rights.
Conclusion
The Great Firewall’s architecture is not a singular construct but a federated, modular system that reflects a deeply integrated model of scalable repression and technical precision. Rather than centralized omniscience, the system operates through layered enforcement, with real-time monitoring nodes deployed at key internet exchange points (IXPs), backbone service providers, and regional telecom branches. These nodes feed data into centralized analysis engines and regional control centers, where behavioral patterns, encrypted traffic markers, and protocol anomalies are processed through tools like MAAT, Gohangout, and customized Redis-backed monitoring agents. At the application layer, heuristics detect circumvention behavior , such as the use of Psiphon, V2Ray, or Shadowsocks, using techniques like SNI filtering, JA3 fingerprinting, and connection scheduling flags. DNS responses are spoofed or dropped depending on classification rules, while sessions may be hijacked or redirected via sinkholes and TCP reset injections. The underlying telemetry reveals how regional operators execute policies set by central authorities, supported by MSS-linked vendors providing firmware, DPI modules, and command-and-control dashboards.
Despite this sophistication, the leaked data exposed fault lines, including regionally misconfigured mirrors that unintentionally broadcast blacklist UUIDs, and BGP anomalies suggesting overly aggressive routing filters. These lapses highlight both the bureaucratic silos and technical brittleness of enforcing censorship at scale. Nonetheless, the architectural strategy is resilient: it favors redundancy, localized enforcement autonomy, and reactive filtering rather than static rulesets. What emerges is not just a firewall in the traditional sense, but a living ecosystem of algorithmic governance. The next phase of analysis will step beyond the command-line telemetry and log files to examine the broader implications, the geopolitical consequences of codified information suppression, and the mounting human cost of building a surveillance state at the scale of 1.4 billion people.
APPENDIX: A File List
File list of dump translated from Mandarin
Network Research Report.docx
27712684_attachments_20220419-Zhang Qingfeng-Daily Communication Record.docx
695411_attachments_Phishing Website Detection System Manual.docx
105873423_attachments_20240423 Meeting Minutes – Feedback Version.docx
27712684_attachments_20220420-Wang Meiqi-Daily Communication Minutes.docx
695411_attachments_Appendix 1: University of Chinese Academy of Sciences Graduate Dissertation Midterm Report.docx
105873423_attachments_clearn.docx
27712684_attachments_20220420-Gao Yue-Daily Communication Minutes.docx
695452_attachments_A Method and Device for Multipath TCP Protocol Function Restriction.docx
105873423_attachments_MAAT Regularization Test.docx
27712684_attachments_April 2022 Meeting Minutes.docx
695452_attachments_Explanation on Voluntary Waiver of Remuneration for Work-Related Inventions and Creations (Template)_1.docx
105873423_attachments_MAAT Test String Regularization Test Report.docx
27716205_attachments_【Reference】Departmental Approval.docx
695452_attachments_Amplification of Reflection Attack Detection System Code.doc
105873423_attachments_MAAT Network Flow Processing Configuration Unified Description Framework – Learning Annotation Version.docx
27716205_attachments_Graduate Registration Form.doc
695452_attachments_Amplification of Reflection Attack Detection System Specification.docx
105873423_attachments_Memory Growth Problem Troubleshooting Report 20240326.docx
27716205_attachments_Attachment 1-1: Departmental Approval.docx
695452_attachments_Voluntary Waiver of Invention Benefits Statement (Template).docx
105873423_attachments_Blocking Status Query Program Abnormal Troubleshooting Process.docx
27716205_attachments_Attachment 16: Graduate Registration Form.docx
695452_attachments_Zou Yuting_University of Chinese Academy of Sciences Graduate Thesis Midterm Report.docx
105873423_attachments_Crash Information.docx
27716205_attachments_Attachment 1: Defense Application.doc
695452_attachments_Zou Yuting_University of Chinese Academy of Sciences Graduate Thesis Proposal.docx
105873423_attachments_Document Notes.docx
27716205_attachments_Attachment 21: Scientific Research Achievement Certification Template.docx
695452_attachments_Zou Yuting’s Graduation Remarks.docx
105873423_attachments_Source Code Notes.docx
27716205_attachments_Attachment 2: Revision Instructions for Dissertation Revisions after the Pre-Defense.docx
695502_attachments_Regulations on the Management of Mid-term Assessments for Dissertations of the Institute of Information Engineering, Chinese Academy of Sciences (Interim).doc
105873437_attachments_20240423 Meeting Minutes – Feedback Version.docx
27716205_attachments_Attachment 4: Pre-Defense Committee Member Review Form.docx
695502_attachments_Institute of Information Engineering Master’s Degree – Class of 2017 – Mid-term Assessment Registration Form – Shang Jingjing.doc
105873437_attachments_clearn.docx
27716205_attachments_Attachment 5: Doctoral Dissertation Pre-Defense Review Form.doc
695502_attachments_Institute of Information Engineering Master’s Degree – Class of 2017 – Thesis Proposal – Shang Jingjing_1.doc
105873437_attachments_MAAT Regular Expression Test.docx
27720755_attachments_Attachment 17: Guidance on Writing Standards for Graduate Degree Dissertations at University of Chinese Academy of Sciences.doc
695502_attachments_Institute of Information Engineering Master’s Degree – Class of 2017 – Thesis Proposal Registration Form – Shang Jingjing.doc
105873437_attachments_MAAT Test String Regular Expression Test Report.docx
27721697_attachments_Work Introduction.docx
695502_attachments_Government, Enterprise, and University Email System Security Measurement Report.docx
105873437_attachments_MAAT Network Flow Processing Configuration Unified Description Framework – Learning Annotation Version.docx
39127869_attachments_Offline Deployment SENTRY.docx
695502_attachments_Shucun Government Email System Security Measurement Report.docx
105873437_attachments_Memory Growth Troubleshooting Report 20240326.docx
39129077_attachments_OLP-BP User Manual (Dual-Fiber Bidirectional).doc
695502_attachments_Graduation Reflections.docx
105873437_attachments_Blocking Status Query Program Abnormal Troubleshooting Process.docx
39129077_attachments_Optical Protection Diversion Interoperability Instructions – Communication Instructions.docx
695502_attachments_Email Security Extension Protocol Application Analysis.docx
105873437_attachments_Crash Information.docx
39129436_attachments_Compilation Environment.docx
695502_attachments_Network Mail Service Detection System Manual.docx
105873437_attachments_Documentation Notes.docx
39129436_attachments_Video Recording.doc
695502_attachments_Design Documents.docx
105873437_attachments_Source Code Notes.docx
3.NMS Administrator Manual_V1.0_CH.docx
695502_attachments_Mail Repository Table.docx
106104952_attachments_Psiphon Phenomenon Analysis.docx
40.166 Crash Investigation Document.docx
695502_attachments_Mail Service Provider Reputation Assessment System Manual.docx
106105540_attachments_IP Traceability Report.docx
44990672_attachments_2022.04 Daily Communication Minutes.docx
695502_attachments_Email Service Provider Reputation Assessment System Source Code.docx
106105561_attachments_DPI Benchmark Test Plan.docx
44990672_attachments_20220507-Zhang Qingfeng-Daily Communication Record.docx
695502_attachments_Email System Advanced Features Description 20191022.docx
106106530_attachments_Lesson Plan and Answer Sheet.docx
44990672_attachments_20220520-Wang Meiqi-Daily Communication Minutes.docx
695678_attachments_BillGates, Mayday, and XorDDos Family Traffic Characteristics.docx
106106532_attachments_Fang Ban – Lesson Plan and Answer Sheet – Zhang Linkang.docx
44990672_attachments_20220520 – Gao Yue – Daily Communication Minutes.docx
695678_attachments_Kafka Setup Process.docx
106106535_attachments_Zhang Linkang – Lesson Plan and Answer Sheet.docx
44990672_attachments_April 2022 Meeting Minutes.docx
695678_attachments_Institute of Information Engineering Master’s Degree – Class of 2017 – Thesis Proposal Registration Form – Wang Yu.doc
106107220_attachments_Defense Record.docx
44990894_attachments_(Reference Template) Appendix 9: Revision Notes for the Dissertation after Review.docx
695678_attachments_Notice on Voluntary Waiver of Remuneration for Work-Related Inventions and Creations.docx
106107951_attachments_Defense Record.docx
44990894_attachments_Attachment 9: Revision Notes for the Dissertation After Review.docx
695678_attachments_Malicious Service IPv6 Address Discovery and Assessment System Manual.docx
106109482_attachments_Li Zhuo – Defense Opinion.docx
44992427_attachments_Resolution of the Second Research Laboratory Dissertation Defense – Reference Template (including PhD and Master’s) 2022.doc
695678_attachments_Malicious Service IPv6 Address Discovery and Assessment System Source Code.docx
106109964_attachments_Advantages of Upgrading_v2.doc
44992427_attachments_Attachment 14: Defense Committee Resolution and Voting Results (Reference Template).docx
695678_attachments_Graduation Reflections – Wang Yu.docx
106109964_attachments_Advantages of Text Upgrade.doc
44992427_attachments_Attachment 2: Defense Committee Resolution (Blank).docx
695678_attachments_Attachment 1: Midterm Report of Graduate Dissertation from University of Chinese Academy of Sciences – Wang Yu.docx
106109974_attachments_Kafka Component Parameters and Frequently Asked Questions.docx
47251516_attachments_2022.05 Daily Communication Minutes.docx
695678_attachments_Attachment 2: Midterm Assessment Registration Form for Graduate Dissertation from University of Chinese Academy of Sciences – Wang Yu.doc
106110644_attachments_Reflections on the Encrypted Video Content Recognition Test Invitational Competition – TikTok – Yang Chen.docx
47251516_attachments_20220601 – Zhang Qingfeng – Daily Communication Records.docx
695874_attachments_CMAF Research and Analysis.docx
106110644_attachments_Competition Exchange – Zhang Xiyuan.docx
47251516_attachments_20220620-Wang Meiqi-Daily Communication Minutes.docx
695874_attachments_Regulations on the Management of Mid-term Assessments of Degree Thesis of the Institute of Information Engineering, Chinese Academy of Sciences (Interim).doc
106110644_attachments_Competition Replay_Tang Weitao_1.docx
47253181_attachments_2022-06-01 Pre-Application Kick-off Meeting and Technical Exchange Meeting.docx
695874_attachments_Institute of Information Engineering Master’s Degree – Class of 2017 – Mid-term Assessment Registration Form – Shang Jingjing.doc
106110644_attachments_Shenzhen Competition Replay_Cui Chenyang_1.docx
48042345_attachments_Spring Boot HTTPS.docx
695874_attachments_Institute of Information Engineering Master’s Class of 2017 – Project Proposal – Shang Jingjing.doc
106111885_attachments_User Manual.docx
49185937_attachments_20220620 – Wang Meiqi – Daily Communication Minutes.docx
695874_attachments_Institute of Information Engineering Master’s Class of 2017 – Project Proposal – Liu Youting.doc
106112252_attachments_CRDT Research.docx
49185937_attachments_2022.06 Daily Communication Minutes.docx
695874_attachments_Institute of Information Engineering Master’s Class of 2017 – Project Proposal Registration Form – Shang Jingjing.doc
106113119_attachments_qps Test bind9 vscoredns.docx
49185937_attachments_20220701-Zhang Qingfeng-Daily Communication Record.docx
695874_attachments_Institute of Information Engineering Master’s Degree-2017-Project Proposal Registration Form-Liu Youting.doc
106113320_attachments_Flink Troubleshooting Manual.doc
49185937_attachments_20220701-Wang Meiqi-Daily Communication Record.docx
695874_attachments_Government, Enterprise, and University Email System Security Measurement Report.docx
106113349_attachments_Apache Doris Configuration Items
106113349_attachments_Application Notes.docx
49185937_attachments_April 2022 Meeting Minutes.docx
695874_attachments_Shucun Government Email System Security Measurement Report.docx
106113365_attachments_Offline Deployment SENTRY.docx
49186474_attachments_20220715 – Gao Yue – Daily Communication Minutes.docx
695874_attachments_Graduation Reflections.docx
106113392_attachments_Optical Protection Diversion Interoperability Instructions – Communication Instructions.docx
49186474_attachments_20220715 – Zhang Qingfeng – Daily Communication Record.docx
695874_attachments_Email Security Extension Protocol Application Analysis.docx
106113394_attachments_Compilation Environment.docx
49186474_attachments_20220715 – Wang Meiqi – Daily Communication Record.docx
695874_attachments_Network Mail Service Detection System Manual.docx
106113399_attachments_Video Recording.doc
49186474_attachments_April 2022 Meeting Minutes.docx
695874_attachments_Design Documents.docx
106113405_attachments_NMS Administrator Manual_V1.0_CH.docx
49187953_attachments_20220801 – Gao Yue – Daily Communication Minutes.docx
695874_attachments_Mail Repository Table.docx
106113406_attachments_Psiphon Phenomenon Analysis.docx
49187953_attachments_20220801 – Zhang Qingfeng – Daily Communication Record.docx
695874_attachments_Mail Service Provider Reputation Assessment System Manual.docx
106113411_attachments_IP Traceability Report.docx
49187953_attachments_20220801 – Wang Meiqi – Daily Communication Record.docx
695874_attachments_Email Service Provider Reputation Assessment System Source Code.docx
106113416_attachments_DPI Benchmark Test Plan.docx
49187953_attachments_April 2022 Meeting Minutes.docx
695874_attachments_Email System Advanced Features Description 20191022.docx
106113421_attachments_Lesson Plan and Answer Sheet.docx
49189242_attachments_20220815 – Gao Yue – Daily Communication Minutes.docx
695874_attachments_BillGates, Mayday, and XorDDos Family Traffic Characteristics.docx
106113422_attachments_Fang Ban – Lesson Plan and Answer Sheet – Zhang Linkang.docx
49189242_attachments_20220815 – Zhang Qingfeng – Daily Communication Record.docx
695874_attachments_Kafka Setup Process.docx
106113423_attachments_Zhang Linkang – Lesson Plan and Answer Sheet.docx
49189242_attachments_20220815 – Wang Meiqi – Daily Communication Record.docx
695874_attachments_Institute of Information Engineering Master’s Degree – Class of 2017 – Thesis Proposal Registration Form – Wang Yu.doc
106113424_attachments_Defense Record.docx
49189242_attachments_April 2022 Meeting Minutes.docx
695874_attachments_Notice on Voluntary Waiver of Remuneration for Work-Related Inventions and Creations.docx
106113425_attachments_Defense Record.docx
49190679_attachments_20220901 – Gao Yue – Daily Communication Minutes.docx
695874_attachments_Malicious Service IPv6 Address Discovery and Assessment System Manual.docx
106113426_attachments_Li Zhuo – Defense Opinion.docx
49190679_attachments_20220901 – Zhang Qingfeng – Daily Communication Record.docx
695874_attachments_Malicious Service IPv6 Address Discovery and Assessment System Source Code.docx
106113427_attachments_Advantages of Upgrading_v2.doc
49190679_attachments_20220901 – Wang Meiqi – Daily Communication Record.docx
695874_attachments_Graduation Reflections – Wang Yu.docx
106113428_attachments_Advantages of Text Upgrade.doc
49190679_attachments_April 2022 Meeting Minutes.docx
695874_attachments_Attachment 1: Midterm Report of Graduate Dissertation from University of Chinese Academy of Sciences – Wang Yu.docx
106113429_attachments_Kafka Component Parameters and Frequently Asked Questions.docx
49192059_attachments_20220915 – Gao Yue – Daily Communication Minutes.docx
695874_attachments_Attachment 2: Midterm Assessment Registration Form for Graduate Dissertation from University of Chinese Academy of Sciences – Wang Yu.doc
106113430_attachments_Reflections on the Encrypted Video Content Recognition Test Invitational Competition – TikTok – Yang Chen.docx
49192059_attachments_20220915 – Zhang Qingfeng – Daily Communication Record.docx
695874_attachments_CMAF Research and Analysis.docx
106113431_attachments_Competition Exchange – Zhang Xiyuan.docx
49192059_attachments_20220915 – Wang Meiqi – Daily Communication Record.docx
695874_attachments_Regulations on the Management of Mid-term Assessments of Degree Thesis of the Institute of Information Engineering, Chinese Academy of Sciences (Interim).doc
106113432_attachments_Competition Replay_Tang Weitao_1.docx
49192059_attachments_April 2022 Meeting Minutes.docx
695874_attachments_Institute of Information Engineering Master’s Degree – Class of 2017 – Mid-term Assessment Registration Form – Shang Jingjing.doc
106113433_attachments_Shenzhen Competition Replay_Cui Chenyang_1.docx
49193421_attachments_20221001 – Gao Yue – Daily Communication Minutes.docx
695874_attachments_Institute of Information Engineering Master’s Class of 2017 – Project Proposal – Shang Jingjing.doc
106113434_attachments_User Manual.docx
49193421_attachments_20221001 – Zhang Qingfeng – Daily Communication Record.docx
695874_attachments_Institute of Information Engineering Master’s Class of 2017 – Project Proposal – Liu Youting.doc
106113435_attachments_CRDT Research.docx
49193421_attachments_20221001 – Wang Meiqi – Daily Communication Record.docx
695874_attachments_Institute of Information Engineering Master’s Class of 2017 – Project Proposal Registration Form – Shang Jingjing.doc
106113436_attachments_qps Test bind9 vscoredns.docx
49193421_attachments_April 2022 Meeting Minutes.docx
695874_attachments_Institute of Information Engineering Master’s Degree-2017-Project Proposal Registration Form-Liu Youting.doc
106113437_attachments_Flink Troubleshooting Manual.doc
49194719_attachments_20221015 – Gao Yue – Daily Communication Minutes.docx
695874_attachments_Government, Enterprise, and University Email System Security Measurement Report.docx
106113438_attachments_Application Notes.docx
49194719_attachments_20221015 – Zhang Qingfeng – Daily Communication Record.docx
695874_attachments_Shucun Government Email System Security Measurement Report.docx