How Lotus Blossom (G0030) compromised the Notepad++ update pipeline in a precision supply-chain espionage campaign targeting high-value organizations.

How Lotus Blossom (G0030) compromised the Notepad++ update pipeline in a precision supply-chain espionage campaign targeting high-value organizations.

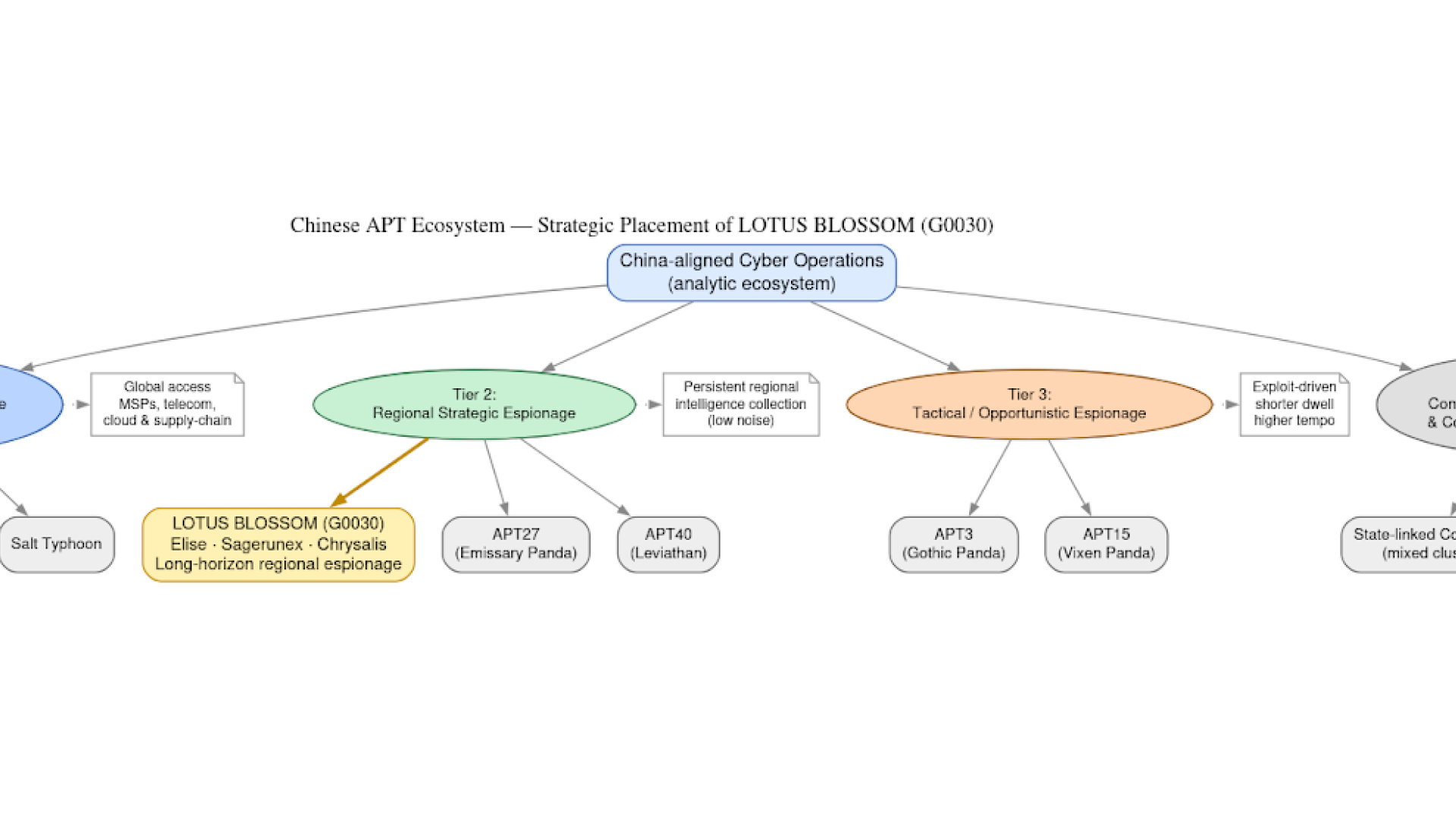
Leaked Knownsec documents reveal China’s cyberespionage ecosystem. Analyze TargetDB, GhostX, and 404 Lab’s role in global reconnaissance and critical infrastructure targeting.
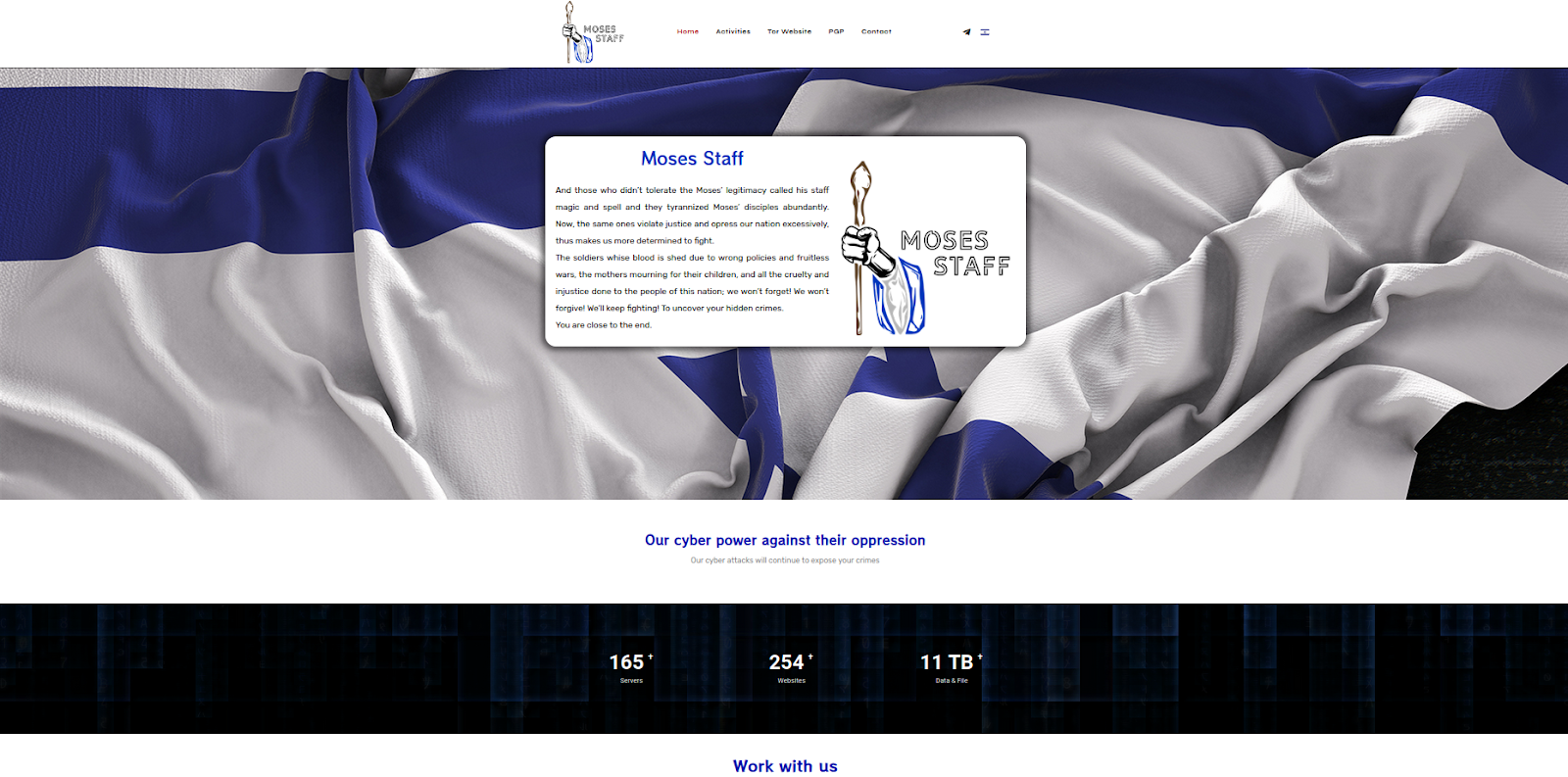
APT35/Charming Kitten's leaked documents expose the financial machinery behind state-sponsored hacking. Learn how bureaucracy, crypto micro-payments, and administrative ledgers sustain Iranian cyber operations and link them to Moses Staff.
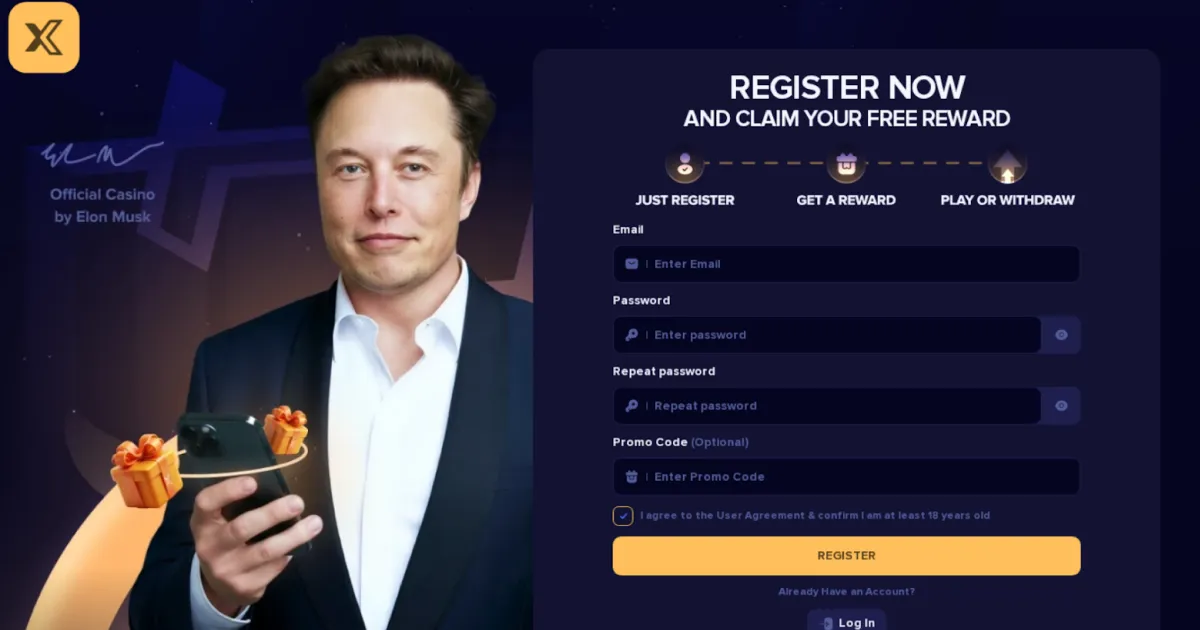
An analysis of an active cryptocurrency scam operation impersonating Trump, Musk, and Truth Social across 250+ domains — uncovering shared wallet infrastructure, on-chain laundering pipelines, and the tactics used to fake legitimacy.

Commentary followed by links to cybersecurity articles and resources that caught our interest internally.




How Lotus Blossom (G0030) compromised the Notepad++ update pipeline in a precision supply-chain espionage campaign targeting high-value organizations.

Leaked Knownsec documents reveal China’s cyberespionage ecosystem. Analyze TargetDB, GhostX, and 404 Lab’s role in global reconnaissance and critical infrastructure targeting.

APT35/Charming Kitten's leaked documents expose the financial machinery behind state-sponsored hacking. Learn how bureaucracy, crypto micro-payments, and administrative ledgers sustain Iranian cyber operations and link them to Moses Staff.

An analysis of an active cryptocurrency scam operation impersonating Trump, Musk, and Truth Social across 250+ domains — uncovering shared wallet infrastructure, on-chain laundering pipelines, and the tactics used to fake legitimacy.

Commentary followed by links to cybersecurity articles and resources that caught our interest internally.

Phishing campaign targets job seekers with fake career portals and interview invites, stealing ID.me credentials and deploying malware since August 2025.




