From Laptops to Laundromats: How DPRK IT Workers Infiltrated the Global Remote Economy
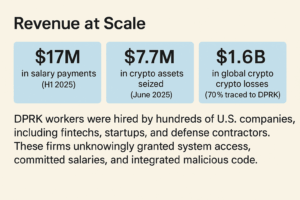
This report maps the entire ecosystem of a DPRK IT worker infiltration scheme: key actors, GitHub aliases, laundering flows, shell companies, fake domains, platform infiltration, wallet infrastructure, and global enablers. We also examine the national security implications of the scheme, as well as how lax corporate hiring standards allowed North Korean operatives not just to get paid, but to access critical infrastructure, intellectual property, and production code.