Banker Trojan Targeting Indonesian and Vietnamese Android Users
Since approximately August 2024, a group has been targeting Indonesian and Vietnamese Android users with banking trojans disguised as legitimate payment and government identity applications. The operators exhibit distinct domain registration patterns, often reusing TLS certificates and grouping domains to resolve to the same IP addresses, with a strong operational focus during Eastern Asia’s daytime hours.
Details
The pattern was initially identified through the monitoring of suspicious site elements such as those associated to Google Play Store http.html:”VfPpkd-jY41G-V67aGc” that may suggest spoofed Play store websites for malware delivery.
icrossingappxyz[.]com
The page contains fake buttons for Google Play Store and App Store application downloads. Clicking the Google Play starts an on-page download progression bar and then prompts for a file store download location on device. The Apple App Store link was nonfunctional.
The site uses an obfuscation wrapper with Socket.IO library, which enables real-time, bidirectional communication with a server. This is highly abnormal for a download page. Instead of linking directly to a file download, when a user clicks the Android button, it initiates a WebSocket connection: socket.emit(‘startDownload’, …). The server responds by sending the .apk file back to the browser in many small chunks. The browser listens for these with “socket.on(‘chunk’, (chunk) => { chunks.push(chunk); });”. As the server sends data, it also sends progress messages (downloadProgress). The script uses these to update the on-screen progress bar, making the user believe a normal download is occurring. When the server sends the “downloadComplete” message, the script combines all the chunks in memory and sets the type to ‘application/vnd.android.package-archive’, the MIME type for an APK file. It then creates a temporary local URL for the file and creates an invisible <a> link, pointing to the temporary file URL and programmatically clicks it. This initiates a user download prompt from the browser.
The malicious site operators likely attempted to evade detection and hide their malware store through the elaborate download method. Network security and firewalls might be configured to block direct downloads of .apk files. However, by hiding the file transfer inside WebSocket traffic, it can often slip through undetected. Since there is no static URL pointing to the malicious file, automated security scanners that crawl websites looking for malicious links will not find it.
It is worth noting that some browsers correctly flagged these downloads as suspicious with download warning prompts such as the following:
IdentitasKependudukanDigital.apk
1f9253092c5a2abdb7bc3d93fccad85f23ce5bfde38377c792a242f045afcdb5
The file was detected as BankBot.Remo.1.origin, a previously closed source banking trojan that had its source code leaked on Russian-language forums in 2016. This has resulted in many variants.
Other much more commonplace malware delivery sites were also used such as the following spoof of M-Pajak, a tax payment app. It simply spoofs the Google App Store page and has a direct download URL to the malicious file stored on the server. Notably, the site used a mix of Thai, Vietnamese, Portuguese, and Indonesian language in the HTML code instead of dynamically inserting the correct language strings based on the visitor’s Accept-Language header or GeoIP. This suggests these are template files used by unsophisticated operators.
twmlwcs[.]cc
Download URL: https[:]//twmlwcs[.]cc/tax-app/M-Pajak.apk
M-Pajak.apk
SHA256 Hash: e9d3f6211d4ebbe0c5c564b234903fbf5a0dd3f531b518e13ef0dcc8bedc4a6d
The downloaded file is also a loader for BankBot and is configured with the following C2 domains:
saping.ynhqhu[.]com
aaping.ynhqhu[.]com
admin.congdichvucongdancuquocgia[.]cc
admin.outdoormovietheaters[.]com
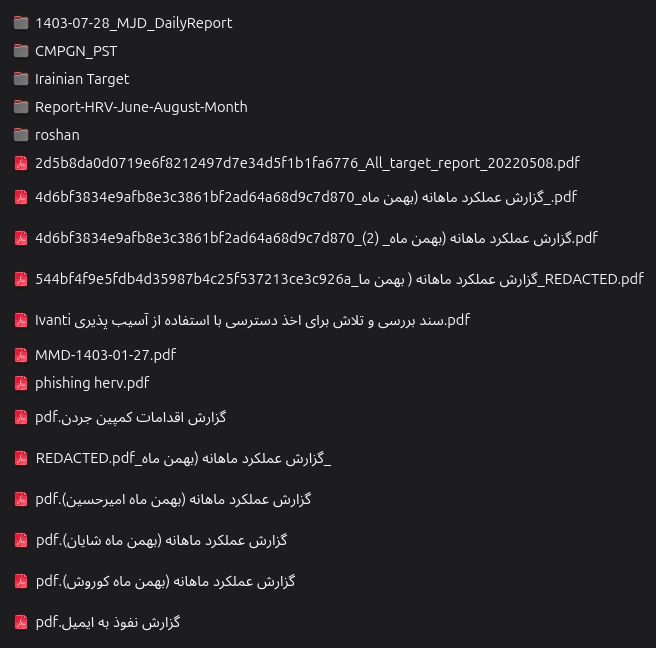
Of the over 100 domains identified in this activity for malware distribution, there were a very limited number of variations in the spoofed content used for delivery. There were slight variations as can be seen from the following sample screenshots in addition to following the fake verification trends that have become commonplace over the past year.
The group also has a nice habit of keeping their malware in open web directories such as the following:
Open Index of dgpyynxzb[.]com
| BCA.apk | 0de69fad50b9e0800ba0120fe2b2f7ebb414e1ae335149a77dae3544b0a46139 |
| BCA mobile-8-5.apk | 68fb18d67bb2314ff70a0fb42e05c40463cceb9657c62682179e62809429ad99 |
| BRI-JR (1).apk | 9ada0f54f0eaa0349c63759172848fcb1dd123d892ece8d74002f96d6f095a43 |
| BRImo_0320SXZ_1 (1).apk | 0d36bb982c7b4d7b309f34653af7f5abe80b1503971d9832d617c5f6b35f362c |
| D-Bank Pro_0725_UU.apk | d47246c9bd4961f692cef6e3d8cdc5aa5f64e16946104cc9c194eb47077fd897 |
| Livin.apk | 4eb7a289af4ea7c65c4926e4b5e2c9ec3fb4d0b9cc425f704b7d1634c23a03a9 |
| MyBCA-8-5.apk | 680eb952cfff2fb39563abc6321851f4b7e6a8014d09ed2744465bcb192562ce |
| MY_BCA.apk | b847b228ed7993136b390bdd6c4afaadc7a441afabf28524bd236e002cf58d47 |
| OCBCmobileid_02202025AC.apk | f7a148d0da5bea32a823b27cf8c45e7532d5e0a964cc4a102fa006ea4ff7e64d |
| OCBC mobile Indonesia_02272025AC.apk | 90aa611b5a258d36220afad46aa52f7496dc11211999ea84e0e7182dc3476aa5 |
| WondrBNI727.apk | e433744f2372bc1ef925007f1f2a17509b4a498472d68c671bb8849265c61475 |
Open Index of ykkadm[.]icu
| 3fb8add8f3b3f6755c6f427c05cc3acc690yLYUy.apk | e29c4a157ac2e1a233f9a59e63cb203fd8eac0595c452d93ed9b72e264dbc8f9 |
| ACBONE01172025U.apk | 2386baafae215fee4c27b955dd6786a7d70d32e5d6eff54cfd8a1353d3d1b473 |
| KienlongBank01172025Ucompatible.apk | ec5b55d4829d043ed3998cc90f633fab5d37bcf5476c6b274eeba85b9f5baaa7 |
| NamABank01162025U.apk | 359a032427342b32bcd85a40e0f99496732f03bbce15aa0d8c92a2b9cfd493dc |
| SHBmobile_01232025U.apk | 14ce035b4bc33458612f3b692e9d9f3304e4eb0455c933452ec49d56549520c4 |
| VTB1212025.apk | 33939f391dab818e6bbda531f64280869adbaafc213c2f4773169f561c88f19f |
indiemusicacademi[.]com
Domain Registration Patterns
Over the past 12 months, the actor was observed using distinct domain registration patterns. This often included the reuse of TLS certificates on two domains and grouping multiple domains to resolve to the same IP addresses.
- ISP:
- Alibaba
- Scloud
- CloudFlare
- IP Country: SG, ID
- Common Website title and page:
- Identitas Kependudukan Digital- Apps on Google Play
- Server Type: nginx
- Nameserver:
- share-dns[.]net
- cloudflare[.]com
- SSL Issuer: R10, R11, WE1
- Registrar:
- Gname.com Pte. Ltd.
The most prolific registration patterns were the use of Alibaba ISP, Gname Registrar, and share-dns[.]net nameservers.
Heatmaps showing the domain registration (left) and first seen DNS requests (right) with the time of day (UTC) over the year.
With the heatmaps for both domain registration and first seen DNS resolutions showing a visually similar grouping, it can also be observed that the delta relative to the domain registrations and first seen DNS requests averaged 10.5 hours over the year. This suggests the domains may be consistently operationalized quickly after registration though not nearly as rapidly as other more prominent cyber crime groups.
The time data shows a strong grouping around eastern Asia’s daytime hours, as is expected with the likely focus on targeting Indonesian and Vietnamese mobile users. It may also suggest the operators are working during the same times, if not also located in the same region.
Conclusion
The malicious operators employed some methodologies to bypass network security that might block direct downloads and prevent static URL-based security scanners from detecting the malicious files. However, it is worth noting that some browsers correctly flag these downloads as suspicious, displaying warning prompts to users and serving as a crucial line of defense for end users. Additionally, several commonplace methodologies employed prominently by less sophisticated financially-motivated groups such as spoofing Google Play Store allow for the identification of these spoofed malware delivery sites. The consistent use of Alibaba ISP, Gname Registrar, and share-dns[.]net nameservers across their operations provides a clear footprint of their infrastructure. While some spoofed sites, like twmlwcs[.]cc, show mixed language code possibly indicating template use by less sophisticated elements, the overall campaign exhibits a coordinated approach to malware delivery. Overall it is likely financially motivated and suspected of being operated by a group in the same region.
IOCs
Domains (see them on our Github as well)
| asdrjswer678[.]com asociaciondehotelesdemexico[.]com bocongan-congdichvucong[.]com bps-ikd[.]com bpsikd[.]com brightter-efg[.]com brightter-ysl[.]com capnhat-etvn[.]cc capnhatdulieu-et[.]com care-ind[.]cc chinhphutt[.]com cong-dich-vu-cong-quoc-gia[.]com cong-dichvucong[.]com congdichvu[.]cc congdichvu[.]vip congdichvucong-bocongan[.]com congdichvucong-quocgia-dvc[.]com congdichvucong-quocgia[.]com congdichvucong[.]cc congdichvucongbocongan[.]com congdichvucongdancuquocgia[.]cc congdichvucongdancuquocgia[.]com congdichvucongquocgia[.]com coring-ind-care[.]cc coring-ind-care[.]com cpvn-eta[.]cc cski-evn[.]cc dich-vu-cong[.]com dichvucong-dvc-quocgia[.]cc dichvucong-qg[.]com dichvucong-quoc-gia[.]com dichvucong-quocgia[.]cc dichvucong-quocgia[.]com dichvucongquocgia[.]com dichvuquocgia[.]com dichvuquocgia[.]org digital-idn[.]com dirjenpajak-caring-idn[.]com dirjenpajak-idn-caring[.]com djp-idn-pajak[.]cc djp-mpajak-idn[.]cc djp-mpajak-idn[.]cyou djp-mpajak-idn[.]top djpcare-mpajak-idn[.]cc djpcare-mpajak-idn[.]com djpcareloop[.]top down-loadmpajakidn[.]com download-djpidn[.]com download-idnpajak[.]com downloaddjpidn[.]com downloadmpajakidn[.]com downloadmpajakidn[.]vip downloadpajak[.]cc dulieu-etvn[.]cc dvc-chinhphu[.]com dvc-dichvucong[.]com dvc-quocgia[.]cc dvc-quocgia[.]com dvc-quocgia[.]net dvc-quocgia[.]org dvcdichvucong[.]com dvcqg[.]cc dvcqg[.]org dvcqg[.]vip dvcquocgia[.]com dvcvn-congdichvucongquocgia[.]cc dvcvn-dichvucongquoccgla[.]online dvcvn-dichvucongquocgla[.]online dvcvn-dichvucongquocglaa[.]online dvcvn-dichvucongquoocgla[.]online dvcvn-trungtamdulieu[.]com dxgjsgw[.]com e-djp[.]com e-ikd[.]com e-pajak[.]cc etx-dongbodulieu[.]com evn-ctdl[.]cc fbpsikd[.]click hdgjgw[.]com hosodongbo-etvn[.]cc hsgjsgw[.]com i-djp-pajak[.]com icrossingappxyz[.]com id-djp-dl[.]com id-ektp[.]com id-pemerintah[.]com idmpajak[.]com idn-digital[.]com idn-dirjenpajak-caring[.]cc idn-dirjenpajak-caring[.]com idn-pajak-djp[.]cc idn-pajak-djp[.]top idngov[.]com idnpajak[.]com idnpajakdownload[.]com iheartusnf6[.]com ikddigital[.]online ind-ikddps[.]cc ind-ikddps[.]online ind-ikddpzs[.]online ind-ikddpzz[.]online indiemusicacademi[.]com japavest[.]com japfunds[.]com jfjygw[.]com keelvari1[.]cc m-djp-download[.]com m-pajak[.]cc m-pajak[.]vip mpajak-djp-idn[.]cc mpajak-djp-idn[.]top mpajak-djp-idn[.]vip mpajak-idn-download[.]cc mpajak[.]cc onlinedjp[.]com onlinepajak[.]cc outshine-byd[.]com outshine-ryg[.]com outshine-sem[.]com pa-jak[.]org pajakdownload[.]com pemerimtahx[.]com pemerintah[.]cc phatnguoicsgt[.]com registerktp[.]com registerktp[.]online toptraditional[.]com topunfortunately[.]com topviolent[.]com ttcskhdl[.]cc twmlwcs[.]cc vietnamchinhphu[.]org vncirclek[.]com vndichvucongtructuyen[.]com ykkadm[.]icu ynhqhu[.]com |
Sha256 Hashes
| 0b7f4c3be1d0b0f0b53495ff33e8c4b22adf122e01f8c72d705c489a975fe498a9358048b5f6e8e7c4b47bebd41991f9e33ccea6e9eb88d1c33dc6079ceb06b6d4937d30853932bc0bf840bac79121e027ec7078395ec2c50d6392f1fed528f11f9253092c5a2abdb7bc3d93fccad85f23ce5bfde38377c792a242f045afcdb54be32b6417ee32b9da0b81e487f9e26503bd7086d95a4fb5fd8dd8ac1f328e5ddb0c223bc08108694e8185e0d8bcd32684e56ba251fb63a544c7eff2932580799e38cc89cf22ff8f5a566c2069702dd89f55bc3f8a3caf96f0d9327256bdc791e29c4a157ac2e1a233f9a59e63cb203fd8eac0595c452d93ed9b72e264dbc8f92386baafae215fee4c27b955dd6786a7d70d32e5d6eff54cfd8a1353d3d1b473ec5b55d4829d043ed3998cc90f633fab5d37bcf5476c6b274eeba85b9f5baaa7e9d3f6211d4ebbe0c5c564b234903fbf5a0dd3f531b518e13ef0dcc8bedc4a6359a032427342b32bcd85a40e0f99496732f03bbce15aa0d8c92a2b9cfd493dc14ce035b4bc33458612f3b692e9d9f3304e4eb0455c933452ec49d56549520c433939f391dab818e6bbda531f64280869adbaafc213c2f4773169f561c88f19fe9d3f6211d4ebbe0c5c564b234903fbf5a0dd3f531b518e13ef0dcc8bedc4a6d0de69fad50b9e0800ba0120fe2b2f7ebb414e1ae335149a77dae3544b0a4613968fb18d67bb2314ff70a0fb42e05c40463cceb9657c62682179e62809429ad999ada0f54f0eaa0349c63759172848fcb1dd123d892ece8d74002f96d6f095a430d36bb982c7b4d7b309f34653af7f5abe80b1503971d9832d617c5f6b35f362cd47246c9bd4961f692cef6e3d8cdc5aa5f64e16946104cc9c194eb47077fd8974eb7a289af4ea7c65c4926e4b5e2c9ec3fb4d0b9cc425f704b7d1634c23a03a9680eb952cfff2fb39563abc6321851f4b7e6a8014d09ed2744465bcb192562ceb847b228ed7993136b390bdd6c4afaadc7a441afabf28524bd236e002cf58d47f7a148d0da5bea32a823b27cf8c45e7532d5e0a964cc4a102fa006ea4ff7e64d90aa611b5a258d36220afad46aa52f7496dc11211999ea84e0e7182dc3476aa5e433744f2372bc1ef925007f1f2a17509b4a498472d68c671bb8849265c61475 |